Humans are predictable. Sometimes, so are their passwords.
Anyone who has known or observed you can predict the passwords you’re likely to use. Take a moment and think, what password do you currently have?
Does it not involve your name, pet name, or the name of a loved one, coupled with a birth date and united by an elegant special character?
The nod simply means your user account is vulnerable to a cyber attack more than you may think.
You’ll need a dual-factor authentication, like validating your identity with a one-time password (OTP) on your phone, push notification, security token, and others in addition to standard password systems. When you work in an organization, the need for two-factor authentication rises exponentially, as a single compromised account can put the organization’s cybersecurity at risk.
Understanding two-factor authentication (2FA)
Two-factor authentication is the process of confirming one’s identity through two different challenges, using something you already know, have, or contain. In two-factor authentication, one test can be to fill in the username and password. The next challenge can be to verify the identity by tapping on a push notification, entering an OTP shared via email, text message, phone call, or other channels.
Some organizations carry two-factor authentication using the security keys, following the FIDO U2F guidelines. 2FA helps you address vulnerabilities of a standard password-only approach of authentication and makes it more secure.
It helps you keep your accounts safe by enclosing them within two security layers, where it gets tricky to log in unless the identity is verified.
Quer aprender mais sobre Software de Autenticação Multifator (MFA)? Explore os produtos de Autenticação Multifator (MFA).
The difference between 2FA and MFA
The notable difference between two-factor authentication and multi-factor authentication (MFA) is the number of factors that the authentication process uses to check your identity.
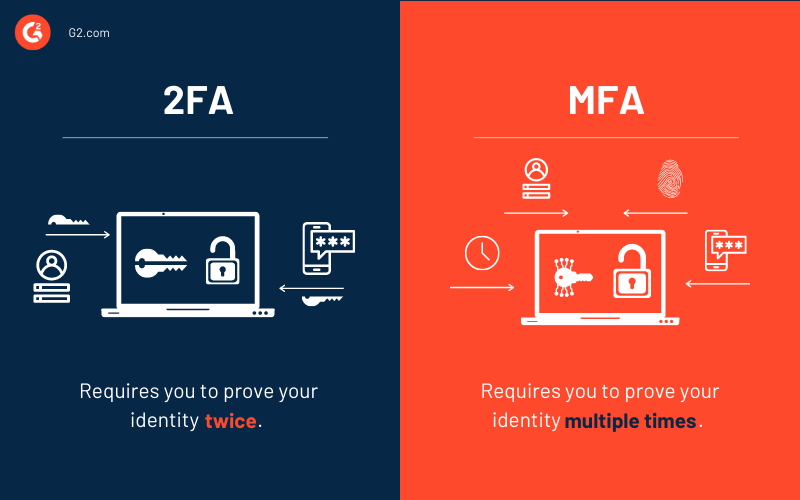
As the name suggests, 2FA challenges you to prove your identity twice, whereas MFA tests your identity with multiple factors like biometric, face recognition, time, location, and several others.
MFA is triggered when the two-step verification fails or suspicious activity is detected in the user behavior. Businesses can also use multi-factor authentication to secure sensitive information or most critical applications and services.
A step toward risk-based authentication (RBA)
Identity thefts or threats to information security are dynamic. You never know what the attacker is attempting to do or the methods they're using to penetrate user accounts. To cope with such threats, your authentication process must adopt an intelligent practice of identifying unusual or suspicious behavior in real-time and respond to that based on the risk it entails.
The risk-based authentication process presses on the above ideology by encouraging organizations to adopt intelligent multi-factor authentication processes. RBA systems analyze several authentication factors in real time and assign a risk score to a user’s request. Based on the risk score, authentication is permitted to specific systems that fall within the risk threshold.
If the risk score is above the threshold, the RBA software will prompt users to prove their identities with additional authentication factors or debar them from accessing the network.
Conclusively, two-factor authentication is closely related to multi-factor authentication as it combines any number of authentication factors to validate someone’s identity.
How does 2FA work?
Let‘s break down the 2FA process or two-step verification process into granular steps:
- A site or an application prompts you to log in.
- You’re expected to enter what you know, which is the first step in 2FA. Generally, it involves entering a username and password.
- Once you enter the combination of username and password, the site’s server finds and validates your identity.
- For passwordless authentication processes, the website generates a unique security key. The security key is processed by the authentication service provider and is validated by the website’s server.
- Once the first step of authentication is over, you’ll initiate the second step. The second step can take various forms, primarily associated with something you have, like a mobile phone.
- You’ll enter the one-time code generated in step 5, click on a push notification delivered by an identity provider, or insert a universal second factor (U2F) security token to verify your identity.
- When you’ve completed both the steps in authentication, you can access your account.
Why do you need two-factor authentication?
Cyber attackers have the technological expertise to test billions of password combinations in a short period. Considering the evolving threat landscape, passwords are no longer self-sufficient to defend your user account from unauthorized access.
Brute force attacks or social engineering attempts stage a consistent threat to penetrate your accounts and benefit from your sensitive information.
You need to establish layers of security defenses around your user accounts to protect them from rising threats. One way to do this is by adopting a multi-factor authentication process in your organization, where two-factor authentication is a part of it.
Two-factor authentication keeps attackers at bay, even when they've successfully penetrated through elements of your single factor authentication: username and password. Since the second factor is generally something you have, it’s difficult for a cybercriminal to lay their hands on it, resulting in better account protection.
Common authentication factors
You can pair traditional passwords with various authentication factors: a knowledge factor, a possession factor, inherent factor or time, and location factor. When you couple authentication factors together with standard passwords, it empowers your systems to protect user credentials in a better way. Organizations leverage multi-factor authentication (MFA) software to equip their technology with such capabilities.
Different categories of authentication factors:
- Knowledge factor: It’s a shared secret that you already know and can use to validate your identity. It can be a password, personal identification number (pin), or any other information which rests solely in your care.
- Possession factor: It’s an entity that you have. It can be a security token, an identity card, or a digital device to approve authentication requests.
- Inherent factor: These factors associate themselves with the user’s physical presence and verify them with biometric, facial, or voice recognition challenges.
- Time factor: It controls user logins based on time. If the login is within set time boundaries, it’s permitted, otherwise not.
- Location factor: It interrogates the user's trusted devices for location. If the login attempt is made from a predefined location, it’s allowed, otherwise debarred.
The authentication factors listed above keep user accounts secure and protected from intrusions. The first three are usually adopted in organizations moving toward 2FA standards. Organizations of diverse dimensions can stack more authentication factors if they need to actualize astronomical protection of user accounts.
Let’s dive into the details of common authentication factors in 2FA that organizations use.
1. Short message service (SMS)
People are no strangers to mobile phones today. You use it daily for various services like SMS, calling, gaming, and so on. Similarly, you can use SMS to pass the second challenge in two-factor authentication.
When you fill in your number in the authentication system, you’ll receive a one-time password (OTP), and after validating it, you’ll gain access to your account. Typically, verifying people’s identities with an OTP has become a common practice now. It’s a feasible and less problematic way for sure, but at the same time, it has its bitter sides.
A mobile number is a personally identifiable information (PII) that can compromise your privacy. Also, if your cell phone is dead, logging into a system will get unambiguously troublesome. But these are some challenges you can deal with as their chances of impacting you are less compared to a security breach.
2. Authenticator application
Authenticator applications use a secret key to generate verification codes on a mobile device to facilitate authentication. It’s another type of phone-based authentication that companies use for 2FA.
Organizations that leverage authenticator apps provide a QR code to the user, which they can scan to verify it with the secret key stored locally on their device. Once it’s verified, the device generates a code, which changes after periodic time intervals. You can enter this code to prove your identity and gain access to your account.
The technology fueling this type of authentication in 2FA is a time-based one-time password (TOTP) and is a part of open authentication (OATH) architecture.
The prime benefit of using an authenticator application is that, even if your device isn't connected to a mobile network, you can still verify your identity as the secret key is stored locally. However, if your device is stolen or lost, it’ll be tricky to gain access to your account.
3. Push-based authentication
In push-based authentication systems, you get a prompt on your mobile device to confirm if you are logging into your account. Many authentication software vendors provide this capability to the user, where you have to scan a QR code once to register your device with the account.
Following that, you’ll get a push notification for all your subsequent logins, and when you validate it, you can have seamless access to your account and applications.
Companies prefer using push-based authentication in 2FA as it stages resistance to phishing attacks and man-in-the-middle (MITM) attacks. It’s difficult for an attacker to trick into exposing the code or filling it in a malicious website.
4. Security keys powered by U2F
Security keys are physical devices such as a small USB, NFC, or Bluetooth. These devices follow the universal second factor (U2F) protocols set by FIDO Alliance.
Using such devices for two-factor authentication will involve:
- Registering these devices with your account
- Connecting the device with your system on subsequent logins
- Tapping “allow” on the device if requested in the authentication process
Security keys are considered to be phishing-proof and are intelligently built from a privacy perspective.
5. Email-based 2FA
Email is another channel that you can use to get past the second-factor challenge in 2FA. Email-based two-factor authentication will help you tighten the screws of single factor authentication (SFA), which were easily broken by credential stuffing or brute force attacks.
Users generally provide their email address to authentication providers to get updates and password reset. Email-based 2FA won’t risk your privacy, as there is no need to give a phone number or other personally identifiable information, and email is already registered.
The only place where an email-based 2FA can surprise you is when an attacker penetrates your email instead of your account. And next, they reset your account password using the email account and gain unauthorized access.
Top 5 multi-factor authentication software solutions
Multi-factor authentication software secures users’ accounts by challenging them to prove their identity in two or more ways before accessing their accounts. It enables them to add extra layers of security to traditional single-factor authentication and addresses vulnerabilities of password-based logins.
Businesses use multi-factor authentication to confirm the identity of users before they access privileged information. Not only does it restrict access from unapproved parties, but it also helps companies to prevent internal theft and data loss.
To qualify for inclusion in the MFA software list, a product must:
- Support secondary authentication methods such as OTPs, software tokens, hardware tokens, biometric factors, mobile push, and more
- Prompt the user to authenticate
- Allow for triggered MFA for new devices and users
* Below are the five leading multi-factor authentication software from G2's Winter 2021 Grid® Report. Some reviews may be edited for clarity.
1. Duo Security
Duo Security enhances your security by protecting your environments and applications with multi-factor authentication. Duo’s solution requires users to carry their mobile phones with the Duo Mobile app installed in them.
The mobile app is available for Android, iPhones, and wearables like the Apple Watch. Duo Security strongly suggests using push or U2F as a second authentication factor as they are most secure and can protect against MITM attacks.
What users like:
“Duo 2FA was the best function we placed all over the business. I can quickly stable links, and we can handle end-user connectivity quite effectively with Duo Push. A wide-ranging business plan will be in the making, applying 2FA to all of our everyday product uses. This can be rendered quite straightforward when utilizing the Duo 2FA defense, and it will be dead on accurate to use as shown by testing."
- Duo Security Review, Alessandra M.
What users dislike:
“We have nothing really bad to limit with respect to this software, we have used it for a long time in our company, and the only problem that arose was difficulties with the configuration. But once it is done, everything works very well.”
- Duo Security Review, Carlos C.
2. Google Authenticator
Google Authenticator is a software-based authenticator by Google that implements two-step verification services using the HMAC-based One-time Password algorithm and Time-based One-time Password Algorithm for authenticating users of software applications.
What users like:
“Google Authenticator is a mobile application whose task is to generate unique codes that allow you to sign in to accounts on various sites that we use. With Google Authenticator and its two-step verification when you sign in, we can prevent the theft of our data.
Double authentication with this application allows us to verify a given login not only with the password we set ourselves but also with an exclusively generated code on the phone in the Google Authenticator application. The interface of the application is very transparent, and the application is available for Android and IOS.”
- Google Authenticator Review, Matthieu B.
What users dislike:
“The only drawback of Google Authenticator is that this application is not compatible with all sites, although the number of compatible sites is continuously improving.”
- Google Authenticator Review, Jeremey F.
3. LastPass
LastPass protects your accounts with the second piece of information before users are given access to their accounts. It provides its authenticator application and allows users to integrate with various third-party applications, software, and USB tokens.
The LastPass Authenticator enables users to experience one-tap authentication for iOS, Android, and Windows phones.
What user like:
“With LastPass, I have to know just one password to access all my accounts. Every site, username, and password is stored securely and can be automatically populated when using the browser extension and logged in. It's also great for agencies that need to share access among a team. When an employee leaves, their LastPass access is deactivated, and they no longer can get to any of your company's accounts. It's easy to use, easy to maintain, and easy to ensure you and your employees can get to what they need.
I have a personal account for my own information, and I'm also a member of a business account, which can be linked to access everything at once. LastPass also has excellent organization tools to tag credentials and credit cards to a client folder. Information is easily searchable and findable in the system.
I love that it detects when a password has changed and prompts you to update the record stored in LastPass. Super helpful! We've been using LastPass for years without any problems, with full confidence that our credential data is secure and easy to access for those who need it.”
- LastPass Review, Jackie B.
What users dislike:
“Managing many accounts with LastPass isn't easy because every connection is logged in and concludes with a substantial selection of accounts. If you've to clean up thoroughly, it could be tough.”
- LastPass Review, Hameed S.
4. Authy
Authy’s MFA solution empowers you to defeat cybercriminals and avoid account takeovers with more robust security. Authy’s authenticator app is simple to set up and brings the future of strong authentication to the convenience of your device.
What users like:
“Nowadays, a password is not enough; it is insufficient in the face of so much computer insecurity; that is why the Two-factor authentication apps are more than necessary. Authy combines two elements; security and style. I like the interface since it integrates all the icons of the accounts that we keep.
Its interface has the characteristics that I consider essential in any app that is not complex to use and that its use is intuitive. It stands out from other similar apps. What I like most about this app is that if I change the smartphone, all my accounts’ migration is not a headache like in other apps. Just install Authy and log in with my phone number and mail. Another outstanding feature is that I can allow the use of multi-device.”
- Authy Review, Marta L.
What users dislike:
“Authy doesn't have a desktop version, which means that it can only be obtained and used from the mobile device, and to carry out any type of transaction with it, it is necessary to have it on top with one. A point that remains because it limits the time when carrying out an operation.”
- Authy Review, Tyler A.
5. Ping Identity
Ping Identity offers identity solutions that address your unique challenges, needs, and environment. It optimizes account security and convenience with various authentication factors, enabling enterprises to balance security and user experience for workforce, customer, and partner identity types with several cloud deployment options, including identity-as-a-service (IDaaS), containerized software, and more.
What users like:
“Ping utilizes open standards that help increase its interoperability with other applications. This use of open standards and overall stability makes it an excellent platform to base user authentication. The provided upgrade utility makes upgrades easy to perform. The professional services group from Ping have also been excellent and have been a true partner during implementation and other additional projects.”
- Ping Identity Review, Anthony S.
What users dislike:
“The UI/UX leaves a little to be desired; navigating the process of configuring your application or accomplishing support tasks can be a bit difficult. The documentation is decent, and support is always willing to help.
Notifications and events would be nice to have (certifications expiring, etc.).
A more "logical" view on Connections and Applications would be instrumental when dealing with multiple applications with different connections.”
- Ping Identity Review, Tyler A.
Keep user accounts shielded against unauthorized access
Two-factor authentication doubles up your security of user accounts by challenging the user to prove their identities twice and validates that the user is actually who they claim to be.
Keep your accounts secure while providing a superior login experience to your users.
Want to enhance the user experience further? Learn more about single sign-on and how it makes authentication simple.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.

