Consider how much of your life takes place on a computer or a mobile device.
You check your email, log into your social media accounts, and enter your credit card number after some online shopping. Every time we share sensitive data like passwords and banking information online, it becomes increasingly important to find ways to strengthen our online cybersecurity efforts.
Each and every one of our digital accounts is at risk for a breach, which is why it’s crucial to add an extra level of protection with multi-factor authentication (MFA) software.
What is multi-factor authentication (MFA)?
Multi-factor authentication is an authentication method that requires the user to present two or more pieces of evidence to gain access and log in to an account. The user will only be granted access after entering this information. Examples of evidence can include a phone number, an email address, or the answer to a security question.
Additional layers of security in the log-in process provide peace of mind that your personal information will stay protected and out of the wrong hands.
MFA vs. 2FA
Multi-factor authentication and two-factor authentication are both security measures that provide an additional layer of protection to your online accounts beyond just a username and password. While MFA combines any number of authentication factors to verify someone’s online identity, the most common type is 2FA.
2FA or 2-step verification requires two forms of verification before granting access to an account or system. Typical implementations include receiving a code via SMS, using a mobile app like Google Authenticator, voice-based authentication, or employing hardware tokens. Although more secure than a single password, 2FA can still be vulnerable to certain attacks, such as SIM swapping or phishing.
MFA goes beyond 2FA by adding additional layers of security. A failed two-step authentication process or suspicious user behavior may trigger it. MFA often combines different factors, such as a password, a biometric scan, and a security question. This type of additional security measures may be required when accessing more important files or sensitive data, such as health or financial records.
Want to learn more about Multi-Factor Authentication (MFA) Software? Explore Multi-Factor Authentication (MFA) products.
Importance of multi-factor authentication
Today, MFA is considered an essential feature in several IAM software categories today, including:
- Single-sign on software
- Privileged access management (PAM) software
- Cloud identity and access management (CIAM) software
- Cloud directory services
- Identity governance and access control tools
These IAM solutions integrate MFA to bolster security, minimize unauthorized access risks, and comply with various regulatory requirements.
While some feel like this process is a minor inconvenience, or it takes too long to set up, it’s worth it in the long run to have a higher level of security. Every other day we hear about accounts and records being compromised worldwide. MFA can help prevent this.
The ultimate goal of MFA is to create a line of defense between your information and hackers. MFA makes it much more difficult for unauthorized people to gain access. While they may know your password, they won’t be able to recreate a second authentication factor (your fingerprint, a text code, an answer to a security question).
In the past, MFA systems implemented just a two-factor authentication but with the increasing number of cyberattacks, people are resorting to using two or more factors for additional layers of protection. Although we cannot prevent all online crime, taking simple steps like using 2FA or MFA can massively reduce the chance of hacking.
If MFA is available, you should use it –especially when it comes to your most sensitive information such as your financial accounts, health records, and your primary email address.
Related: Interested in taking your security efforts even further? Browse our list of the best cybersecurity software providers that protect against hacking, viruses, and other threats.
How does multi-factor authentication work?
It’s important to note that there are two main types of multi-factor authentication.
- Application MFA: The authentication process that activates when a user attempts to gain access to one or more applications.
- Device MFA: The authentication process that immediately activates MFA at the point of login to a system.
Although they are separate processes, MFA is basically the same for both types. When a user tries to gain access to something (phone, laptop, server, etc.), they are met with multi-factor authentication and forced to enter two or more authentication factors. If the factors are deemed correct by a core identity provider (IdP), they will be granted access.
One of the most asked-for authentication factors is your phone number. Usually, with MFA, you enter your username and password upon login and then a unique code that is sent via text message.
This proves that you remember both your username and password, but also that you are in possession of your smartphone, which is “registered” as a device to receive these types of codes.
Multi-factor authentication methods
An authentication factor is a category of credentials to identify verification. When these factors are used in MFA, every additional factor increases the certainty that the person attempting to access the account is who or what they declared to be.
Your credentials fall into three different categories:
- Knowledge: Something only the user knows, such as their password or pin number.
- Possession: Something only the user has, such as a smartphone or a hardware token.
- Inherence: Something that is only of that user, such as their fingerprint or their voice.
For example, when logging into a banking app on a smartphone, the app texts the user a code to type in before they can access their account. This method of MFA falls under the “something you know” category, as it’s a PIN number the user has to enter before they are able to fully connect to their online bank account.

The Discover Card app takes it one step further by asking for “something you are” upon login – a fingerprint.
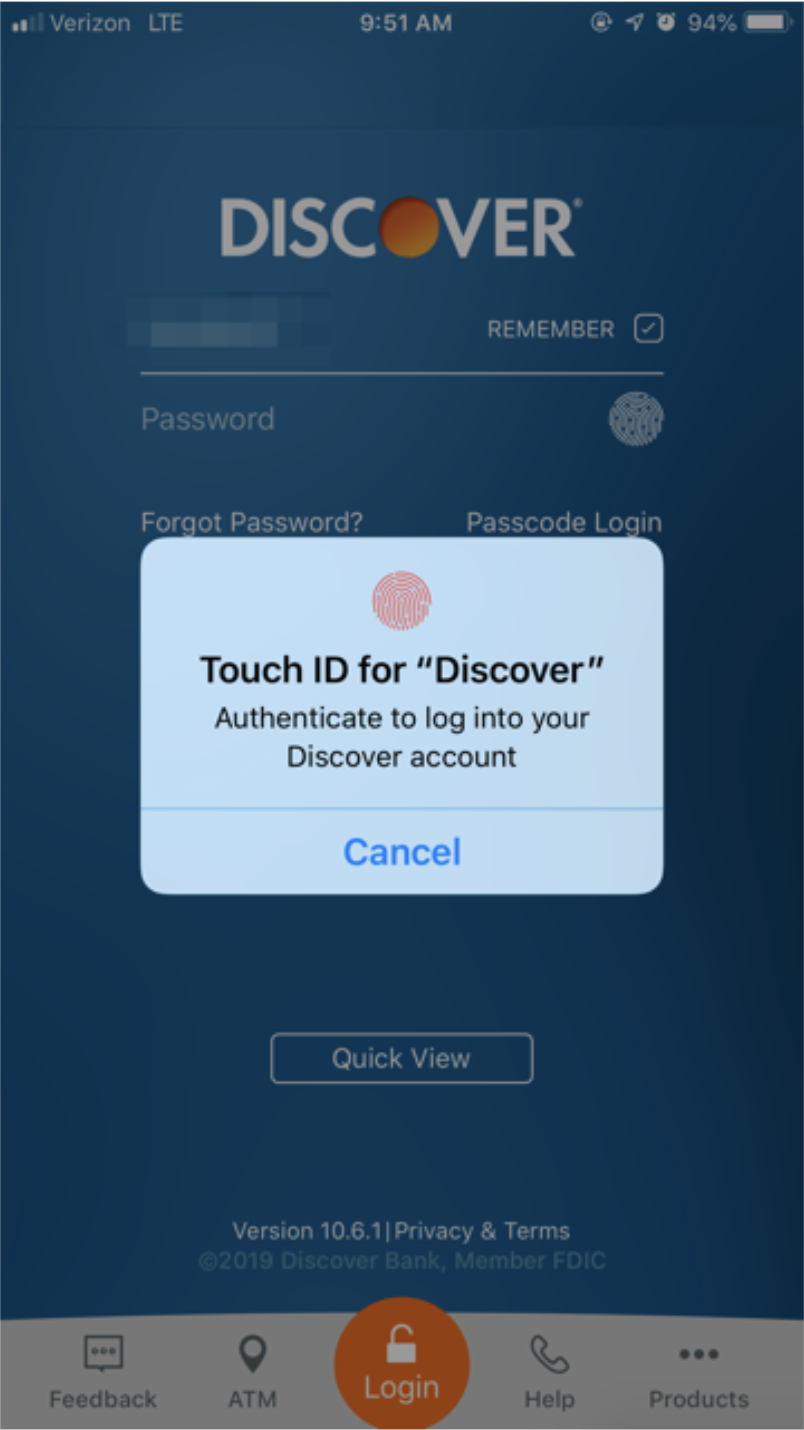
Or, think about when you go to the gas station to fill up your tank. After you swipe your credit card, the machine at the pump asks that you enter in your zip code. This would fall under “something you know” and is an older type of MFA.
Adaptive authentication
More current authentication factors consider the context of the login behavior.
For example, the system may recognize that a hacker is signing in from a strange location thousands of miles away, or notice that a new device is attempting to access your account. The system also takes note of the time you attempt login and the type of network you are accessing. If any of these factors appear out of the ordinary, adaptive authentication will be triggered.
Adaptive authentication leverages artificial intelligence and machine learning to note any strange logins on your account. Any atypical behavior (logging in from a new location or at odd hours) will make the system send out additional verifications such as facial ID or email codes.
Over time, adaptive authentication will learn the patterns of the user and eventually stop requiring them to verify their identity if they begin to frequent a new location or use a new device more and more.
Tip: Don't get your cybersecurity terms mixed up. Multi-factor authentication is a form of risk-based authentication, but they are not the same thing.
Types of multi-factor authentication
You may only use two or three types of multi-factor authentication when accessing online accounts, but did you know that there are a number of different types?
Email codes
These codes will be sent to the user requesting access through email. Receiving a code through your email is one of the most common types of MFA and can be a good option if your phone is lost, stolen, or simply in another room.
Text tokens
A text token is identical to an email code, just through a different means of communication. Receiving text tokens is an easy option to implement and can be used by virtually anyone.
After you enter your username and password, a one-time password (OTP) in the form of a pin number will be sent to your phone. The number acts as the second authentication factor and is entered on the next page/screen.
Biometric verification
Biometric verification can be anything from fingerprint identification to facial recognition. Users with smart devices or computers can take advantage of this technology to further strengthen their online protection.
Using biometric verification is usually less of a hassle than a one-time password and can make MFA a breeze rather than a burden.
Hardware tokens
While the previous three types of MFA have been virtual, a hardware token is physical. This token is considered one of the most secure methods of MFA but can be more expensive.
Many companies will offer hardware tokens to their highest-value users in order to keep them as a customer. Typically, a hardware token is the best option to protect things like your banking, insurance, and investment information.
Users will insert the token into the device or computer to access information. If they want to access information on a mobile device, they may need a USB or USB-C “dongle”.
The only downside? You have to keep track of where the token is, and if you misplace it or forget it at home, you won’t be able to access your accounts.
Security questions
You’ve probably come across security questions when setting up your bank account or school portal. Security questions are static and are considered a type of knowledge-based authentication (KBA). As you set up an account, you may be asked to set a security question.
Some example security questions are:
- What was the name of your first pet?
- What street did you grow up on?
- What is your mother’s maiden name?
- What was your childhood nickname?
When accessing your account, you will enter your username and password and then be asked to provide an answer to the security question. Stronger versions of KBA (called dynamic KBA) are generated in real-time based on records such as recent transactions and credit history.
Although security questions are a common form of multi-factor authentication, they can be compromised easily. If someone does enough online investigating through your social media accounts, they may be able to piece together some of the answers to your questions.
Other multi-factor authentication examples can include:
- Retina or iris scanning
- One time smartphone application codes
- Behavioral analysis
- USB devices, badges, other physical devices
The more types of multi-factor authentication you have implemented, the more secure your sensitive data becomes. Even if a hacker has access to two out of three types, they will still be unable to move forward and your MFA process will have been proven successful.
MFA security
Just how secure is multi-factor authentication? Security ultimately depends on dedication. If you’re willing to take the time to enter multiple authentication factors in to access your account, you may lose a minute of your day, but you’ll be better protected in the long run.
Additionally, trickier passwords (especially a variety of tricky passwords) are your best bet when it comes to account security. If you’re looking to beef up your MFA process, you can do any of the following:
- Ask your bank to implement multi-factor authentication.
- Try to avoid authenticating your identity through social verification as they are at most risk to be hacked.
- Do your research on which MFA methods will work best for you.
Achieving 100% security will never happen, but if you’re proactive with your online security, even the smartest hackers won’t be able to steal your personal information.
Benefits of multi-factor authentication
Nowadays, people expect multi-factor authentication to be apart of any account setup. It’s been integrated into the modern customer service experience and is now the standard for basic online security.
People love MFA because:
- It provides a higher level of protection than just a username and password.
- Users may feel more valued by companies that use MFA.
- MFA can connect with single sign-on software and give users a more simplified and secure login process.
At the end of the day, it’s only getting more dangerous to keep confidential information online or in the cloud. The rise of multi-factor authentication has eased the minds of customers and companies alike and has significantly strengthened overall protection against unauthorized users.
Two is better than one
And three is even better...at least when it comes to your security efforts. More and more websites, services, and apps are taking advantage of two, or even three, factor authentication as an added layer of protection.
The next time you sign up for an account, make sure you take the extra few minutes to set up MFA and protect all of your sensitive data.
Want to learn more about hacking? Discover how spear phishing works and how you can protect yourself from being an easy target.
This article was originally published in 2020. It has been updated with new information.

Alexa Drake
Alexa is a former content associate at G2. Born and raised in Chicago, she went to Columbia College Chicago and entered the world of all things event marketing and social media. In her free time, she likes being outside with her dog, creating playlists, and dabbling in Illustrator. (she/her/hers)
