In a pinch of irony, the same week that the coronavirus was making headlines, it was announced that the first new computer virus in years was wreaking havoc in Europe, Russia, and India.
With millions of malware varieties circulating today, it’s not the most destructive form of malware in existence, but it is unique within the global threat landscape as the sole “computer virus” infecting systems today.
It’s a common misconception that malware and computer viruses are the same.
Malware vs. Computer Viruses
Malware refers to any software designed to disrupt computing environments, infect systems, steal data, or execute actions without the user’s approval. Viruses, still a form of malware, are unique in their ability to self replicate and spread entirely on their own, corrupting any files or data they interact with.
Unlike other malware that requires a hacker to execute commands, viruses act like a parasite, feeding off the computer and spreading whenever files are shared or connections are established across devices.
Today, there are more than one billion unique malware varieties in existence. According to AV-Test, an independent security research institute, nearly 30 million new malware variants discovered in 2020 alone.
The death of the computer virus
Computer viruses are the oldest form of malware, dating back more than 40 years. In the mid-2000s though, hackers appeared to abandon computer viruses for more sophisticated malware.
Modern computers and applications have evolved past the point of efficacy for most computer viruses. New systems are prebuilt with features that harden devices from infection and protect computers by preventing the virus from spreading without the user’s approval. Some malware variants including worms and ransomware are colloquially referred to as viruses, but they don’t have the same “living,” parasitic nature. The term “living” implies its reliance on a host for storage and execution. These viruses are typically attached to files, laying dormant until the host device opens the attachment, hence executing the virus.
Phishing, which is technically an action, not literal malware, has always been one of the easiest and most common ways for hackers to steal login credentials and other personal information, preying on the user’s trust.
| Related: What is Fileless Malware and How Do Attacks Occur? → |
Additionally, phishing techniques are great vehicles for spreading ransomware. When users open a malicious email attachment sent in a phishing attack, their device is instantly infected. In this scenario, the affected device locks down and the user sees a message demanding payment or ransom if they don’t wish to have their data deleted.
BotNets became huge as well once people realized how easy they are to build by infecting insecure smart devices. Once infected, thousands of devices working in unison collectively take down sites, applications, and networks. Fileless malware is one of the newest forms of malware, relying on a computer’s internal components to turn the system against itself. New threats like this continue to arise as hackers and institutional threat actors continue to see value in bypassing even the newest protection solutions.
The return of the “living” virus: Introducing “KBOT”
With the ability to disrupt systems, destroy files, and gain remote control of devices, the computer virus, “KBOT” has become the most widely-spread true “living” virus discovered in recent years.
The name KBOT was coined by threat researchers at Kaspersky Labs, who discovered the revitalized computer virus. The KBOT virus infects executable files with no chance of recovery and slows down computer systems by injecting code into system processes, enabling hackers to gain remote control over compromised systems.
KBOT is uniquely sophisticated for a computer virus. It infects all connected devices, adding dynamic, polymorphic code to files. Data is then encrypted on a virtual file system using the RC6 algorithm which hides the virus in plain sight. It can even download additional modules to harvest and transfer stolen information over a command-and-control server.
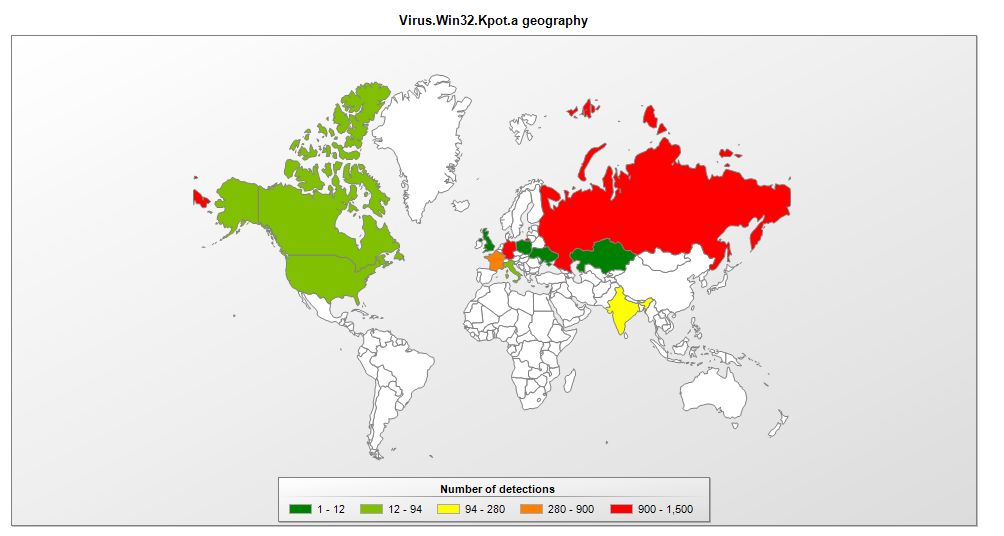 Image courtesy: Kaspersky Labs
Image courtesy: Kaspersky Labs
Evolution of malware protection
While KBOT is an interesting anomaly within the threat landscape, it’s not the top priority of most cutting-edge malware protection technologies. Anti-malware, antivirus, and advanced threat protection (ATP) solutions continue to evolve mirroring the threats around them.
Some time ago, antivirus advanced past local endpoint virus protection. Companies can no longer afford the risks of adding antivirus software to a device and assuming it’s protected. Luckily, the newest solutions are designed to protect against even more sophisticated malware capable of infecting all kinds of devices, networks, applications, and websites.
Endpoint security is the original and likely the most common use case of antivirus software today, but modern businesses must secure a lot more than endpoints alone. Cloud environments, websites, and applications all require unique protection. With the newest malware varieties, specifically fileless malware, companies have prioritized detection technology over protection.
Cloud workload protection platforms have emerged as the most effective way to protect data and workloads running on cloud services. These workload-centric tools help protect cloud environments by automating and providing continuous protection, compliance, and visibility.
The rapid evolution of malware has made it clear that it is unmanageable to prevent every single threat from a target. Instead, it would be more effective to keep baseline protection while adding continuous monitoring capabilities to automatically respond to threats as they arise.
If you’re looking for one of these solutions, check out our endpoint detection and response (EDR) and security orchestration, automation, and response (SOAR) categories.
Antivirus should remain a core component of a business’ virus protection plan. G2’s best free antivirus rankings outline the top products that can help businesses secure their systems with free solutions. Still, new threats require new technologies. Stay up to date on the newest security technologies with G2’s 2020 technology trends for cybersecurity.
Quer aprender mais sobre Provedores de Serviços de Segurança de Endpoint? Explore os produtos de Serviços de Segurança de Endpoint.

Aaron Walker
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.
