Fileless malware attacks are on the rise as more hackers use it to disguise their nefarious activities. These threats leverage a computer’s existing, whitelisted applications and computing power against itself. This is what security professionals refer to as “live off the land” threats.
Fileless malware is an advanced, persistent threat that comes in the form of sneaky, signatureless attacks that can turn a computer against itself and compromise systems to steal information. This leaves no trace for security professionals to perform a forensic analysis to root out the cause.
Detections of fileless malware this year increased 265% compared to 2018’s first half, according to Trend Micro’s 2019 Midyear Security Roundup. The report also found that the most common uses of fileless malware came in the form of cryptocurrency mining malware, ransomware, and banking trojans.
What is fileless malware?
Typical malware must be executed to facilitate an attack. Fileless malware does not require any file downloads and leaves no signature, making them significantly more difficult to investigate and remediate.
What is fileless malware?
Fileless malware is a memory-based malicious software component that lives in random access memory (RAM). Fileless attacks utilize built-in components of an operating system to turn a computer against itself.
Hackers utilize fileless malware by injecting malicious code, scripts, or libraries into documents and web pages. This code is referred to as LOLBins, or living-off-the-land binaries, and helps hackers automate attacks on penetration testing and administrative software.
LOLBins utilize whitelisted, legitimate software applications that exist on the targeted device, but use them with malicious intent. Commonly abused tools include PowerShell, PsExec, or Windows Management Instrumentation (WMI).
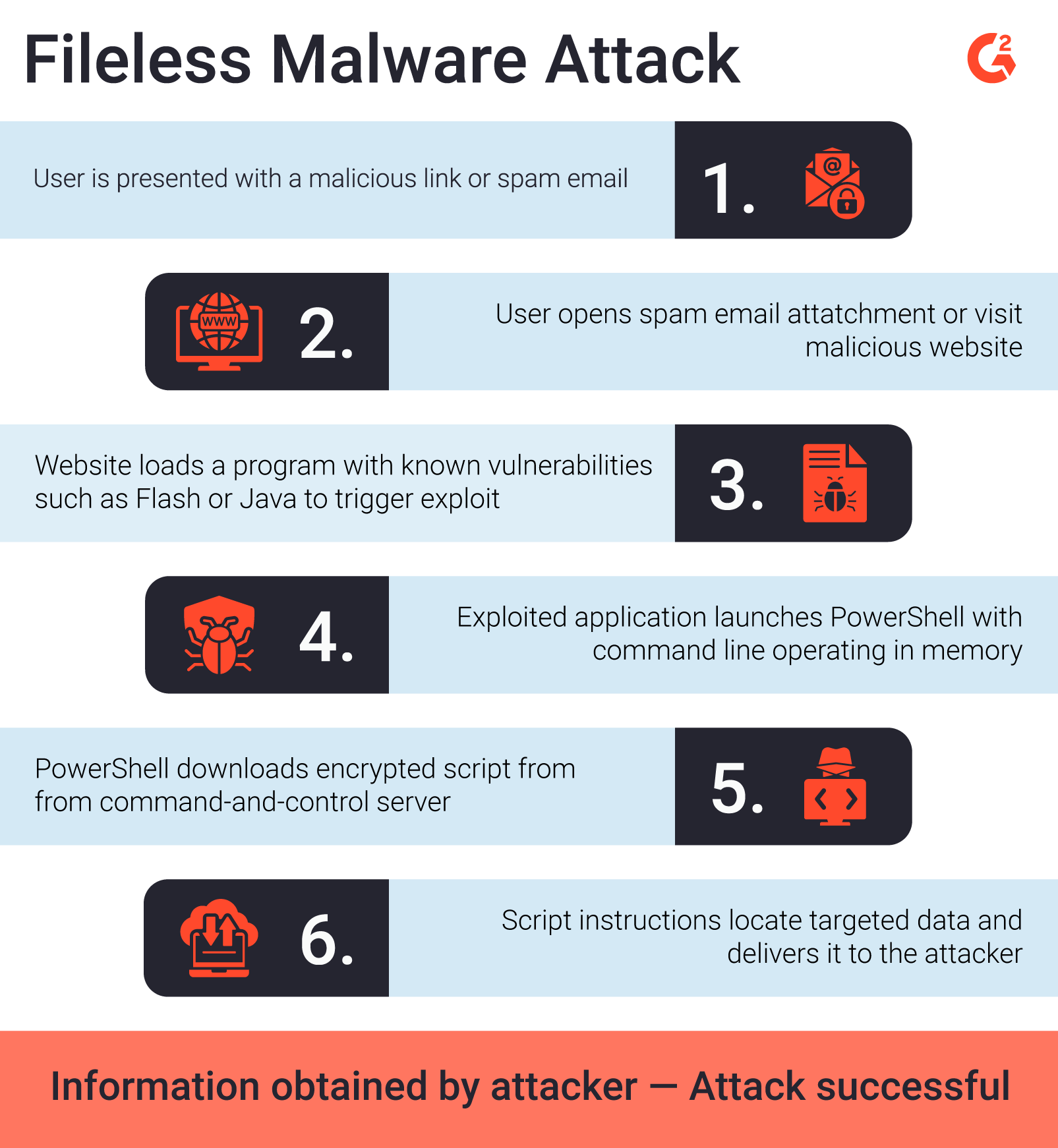
Hackers insert binaries, scripts, and libraries into everyday documents and deliver them to their target via email. Alternatively, they store LOLBins within the HTML of a web page. Once opened, the script triggers a series of tasks that operate and launch administrative tools that start conducting malicious activities in memory. These activities might include deploying ransomware, exfiltrating sensitive information, or connecting to a remote server to download and execute a malicious payload.
A few notable cases of fileless malware attacks include 2018’s banking trojan that infected more than 100,000 computers in two months, a number of ransomware attacks targeting hospitals in 2019, as well as a series of fake Adobe Flash update requests containing malware. Two of the highest profile attacks include the 2016 hack of the Democratic National Committee (DNC) and 2017’s Equifax data breach.
Types of fileless malware
Document-based — Macros stored in innocent-looking documents are one of the most common ways to facilitate an attack. Macros are designed to automate actions to save people time. While these are incredibly useful for many, hackers can easily hide a macro that contains an executable script in one of these documents.
For example, in a professional setting, it is not uncommon for an employee to receive a Microsoft Excel spreadsheet from one of their peers. It can be easy for an attacker to send a malicious Excel spreadsheet with a macro designed to run Powershell and automate tasks like downloading a malicious paywall.
Web-based — Attacks stemming from malicious online sites function a bit differently. Web-based attacks utilize a myriad of scripting languages executable through a web page, the most common is JavaScript. According to a 2018 Stack Overflow survey of more than 100,000 developers, about 72% of developers use JavaScript.
In this scenario, a web page loads, executes, and runs a JavaScript command to open PowerShell and trigger a number of actions. PowerShell will launch and follow the script commands which might include connecting to a remote server and extracting sensitive information or downloads and executes malicious files.
Why are fileless attacks becoming more common?
Trusted applications — Because fileless malware relies on trusted, legitimate applications, there are few ways to prevent against it. Rather than downloading files, which typically requires admin approval, the malicious script piggybacks off the native application. These tools are hijacked by the attacker.
Using legitimate tools allows these processes to occur in memory as opposed to the computer’s hard drive. This leaves no trace of the attack, operating in RAM solely. This allows the attack to operate in secret and hide malware within RAM where it’s undetectable by traditional antivirus software.
In-memory operation — There are a few attack-side benefits to operating executing commands in memory, but the most obvious is antivirus evasion. Antivirus software typically focuses on scanning downloads or newly-installed applications. Fileless malware requires neither action, causing most antivirus tools to miss the attack.
Another benefit is the lack of attention resulting from failed detection. This allows hackers to hide malware in places most security tools can’t access. In some cases, in-memory operation lets malware continue to run when a device is powered down.
Potentially OS agnostic — While Windows systems are more susceptible to fileless attacks, Mac and Linux systems may also be susceptible. Because fileless malware relies on whatever tools are native to a computer, the device’s operating system might become irrelevant.
Attacks may result from a script opened on a Mac computer or run commands from a remote server. These instances are far less common than Windows-based fileless attacks, but could operate similarly using Mac and Linux-native administrative tools in theory.
How to protect against fileless malware
Some security professionals argue that fileless malware is undetectable in real time. But, nothing is completely undetectable. The most commonly accepted solution to protect against fileless malware is implementing an endpoint detection and response (EDR) solution.
These tools combine the functionality of traditional antivirus and endpoint protection solutions with anomaly detection and threat remediation capabilities. If an endpoint device is attempting to communicate outside a specified network or a user downloads a file containing a malicious script, the EDR solution detects and resolves the issue from its source.
User and entity behavior analytics (UEBA) are an emerging market of security solutions that utilizes machine learning to develop a baseline of typical activities and behaviors performed by a user. If the system notices abnormal activities or requests from a strange device or location, security teams will be alerted. In addition to preventing fileless attacks, UEBA is capable of detecting insider threats, compromised accounts, and data breaches.
Additionally, if you’re running a Windows machine, it would be wise to disable PowerShell and WMI unless you’ve opened them manually. Unless you’re using Macros in Microsoft Excel or Word, it may also benefit you to disable Macros for those applications.
Other than technical solutions, security awareness training can help companies educate employees on how to identify spam emails and malicious websites. Check out our security awareness training software category to find the tools your team needs to educate your staff and protect your business.
Want to learn more about Machine Learning Software? Explore Machine Learning products.

Aaron Walker
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.