Top Rated Webroot Business Endpoint Protection Alternatives
I use both the Home and Business versions of this product, so I get to see both sides of this product. I will mostly focus on the business product in this review, as they both share similar protection but the business product gets more features.
I love the speed of the product, along with how lightweight it is on your computer. It does not interfere with the PC's speed too much, unlike other AVs. It is easy to install and forget about, as it silently works away in the background. I have used it for years, and I haven't had any issues with false positives. This product working in tandem with their DNS protection provides a great corporate experience as you can control what websites people can go on, you can add websites to a blacklist or a whitelist if you wish to make exceptions.
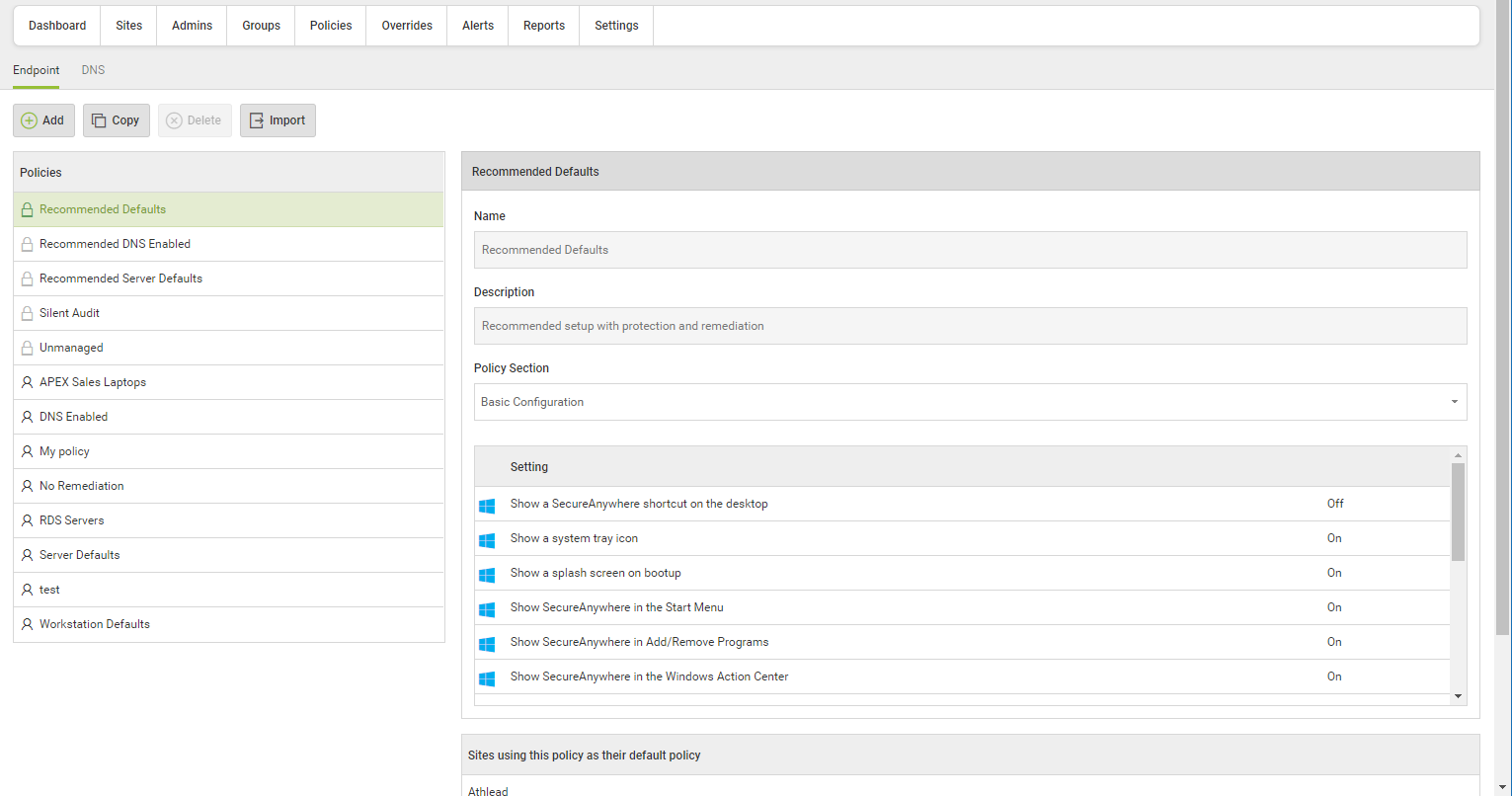
The business management portal works nicely and allows you configure all the options Webroot gives you in its program and being able to control it all centrally is a big bonus too, stopping end users messing with it. Review collected by and hosted on G2.com.
The things I dislike about Webroot are: The interface for the program itself is old looking, it could do with a design refresh. The Identity Protection system has broken Chrome/Edge in the past, multiple times, which has caused many frustrating problems on our end and for the customer, it has not been a problem for about a year now, but has been an annoyance for a couple of years.
Other than those main problems, I cannot think of anything major with what is wrong with webroot. Review collected by and hosted on G2.com.
Video Reviews
524 out of 525 Total Reviews for Webroot Business Endpoint Protection
Overall Review Sentiment for Webroot Business Endpoint Protection
Log in to view review sentiment.
The feature we like most is the integration with our RMM solution. Review collected by and hosted on G2.com.
It's good at the basics and integrates well with our other products but I don't feel like this is the highest level of protection you can get. Review collected by and hosted on G2.com.

It integrates well for automated deployment with Atera.
Agents are responsiove witin 30 seconds to changes made ont he console Review collected by and hosted on G2.com.
I have used many endpoint products and there isnt much I can say from myh experience that is negative. If I had to say something, the console could use a UX person to clean it up a bit, but honnistly tis not bad. Review collected by and hosted on G2.com.

The management console is very user friendly, allowing for a very granular management of endpoints Review collected by and hosted on G2.com.
The product has essentially become ineffective as the threat landscape has evolved, OpenText (who purchased Webroot, has not expended any resources to bring the product into effectiveness against the current threats Review collected by and hosted on G2.com.

I like how easy to use is.
easy to install Review collected by and hosted on G2.com.
sometimes it didn't work fine with macOS devices.
I would like to have an online chat. Review collected by and hosted on G2.com.
Works with Datto very well, you can set alerts to create tickets if it's not installed/updated/detects something.
You can set Datto to install it as soon as Datto installs as well to save you some time.
I've not needed to work with their support much but when I have they've been very thorough. Review collected by and hosted on G2.com.
Not many features and trying to whitelist apps/IP's can be a bigger task than you want it to be. Review collected by and hosted on G2.com.

The price is right for smaller companys. Review collected by and hosted on G2.com.
I dont like that its hard to remove from cleints computers. Review collected by and hosted on G2.com.
It is working well and simple to use. We have many computers that we trust to Webroot Review collected by and hosted on G2.com.
There are some tricky parts that make it difficult to work with and use properly. Learning curve Review collected by and hosted on G2.com.
Being able to remotely set anti-virus scans is a great help Review collected by and hosted on G2.com.
When the UI changed I was not to fond of the layout Review collected by and hosted on G2.com.

Webroot does not drain system resources like other protection suites I have used before. Somehow it still delivers better protection as well. It really is the whole package. Review collected by and hosted on G2.com.
I genuinely cannot think of anything - i really can't. I actually just asked my colleague as well in case I was missing something obvious and he gave the same answer. Review collected by and hosted on G2.com.
Webroot Endpoint Protection is a cloud-based endpoint security solution designed to protect businesses from various types of cyber threats such as viruses, malware, phishing attacks, and other online security risks. It is a lightweight solution that uses a predictive AI and machine learning to protect endpoints against known and unknown threats in real-time.
One of the strengths of Webroot Endpoint Protection is its fast scanning and detection capabilities. It is designed to work silently in the background without slowing down the computer or interrupting the user's workflow. It can quickly detect and block malicious activities before they can cause any damage to the system.
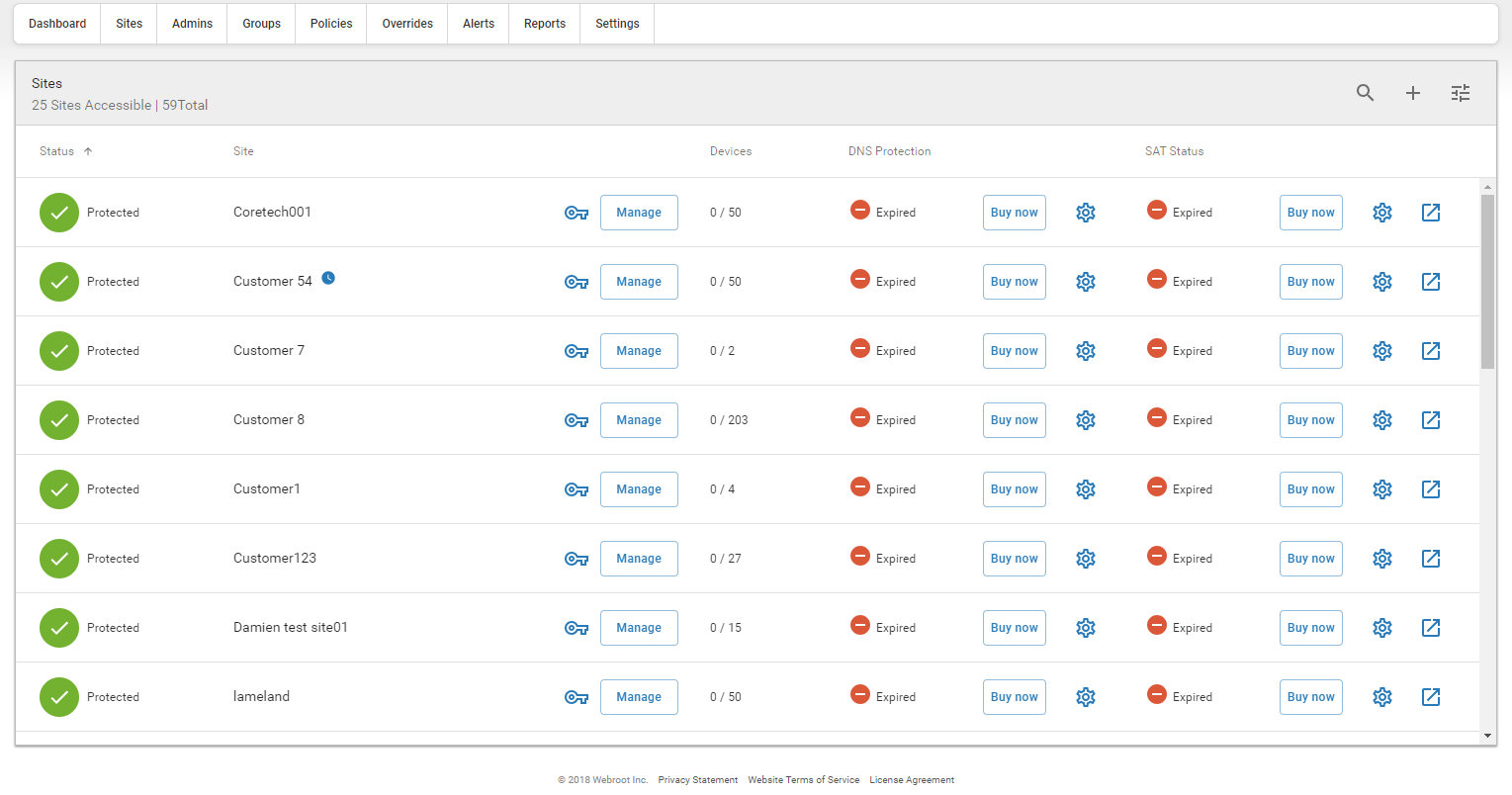
Another advantage of Webroot Endpoint Protection is its cloud-based management console. It allows administrators to manage and monitor the security of endpoints from a single dashboard, making it easy to deploy and manage the solution across multiple devices and locations.
Webroot Endpoint Protection also offers various features such as firewall protection, web filtering, and real-time threat intelligence that help keep endpoints secure from online threats. The solution is also compatible with different operating systems, making it an ideal choice for businesses with mixed environments. Review collected by and hosted on G2.com.
One potential negative aspect of using Webroot Endpoint Security is its heavy reliance on cloud-based technology. Although this can be an advantage in terms of scalability and management, it can also be a disadvantage for businesses with limited internet connectivity or those who prefer to keep their data on-premises for security or compliance reasons. Review collected by and hosted on G2.com.