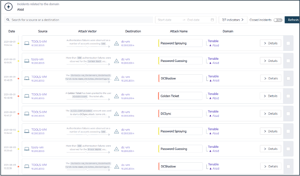
3 Tenable Identity Exposure Reviews

Tenable identity exposure formerly tenable.ad The Tenable.ad help us to find & mitigate the Vulnerabilities in AD before the attackers can exploit the Vulnerabilities. We can monitor in real time and we can run various tasks like threat hunting, detection, and incident response, etc. Review collected by and hosted on G2.com.
Basically it's a new product launch in the market and i found there is no lag in it. But still it could be cost efficient. Review collected by and hosted on G2.com.
Easy to deploy and great visibility to what's happening inside crucial system. Review collected by and hosted on G2.com.
Right now it serves the purpose and UI can be little improved. Review collected by and hosted on G2.com.
Easy to roll out,
SAAS efficiency, don't have to manage servers.
ability to monitor and detect exposure.
also recommends actions for every exposure. Review collected by and hosted on G2.com.
there are no major dislikes at the moment. only a small impact security score changes. Review collected by and hosted on G2.com.
There are not enough reviews of Tenable Identity Exposure for G2 to provide buying insight. Below are some alternatives with more reviews: