Pas un jour ne passe sans que nous n'accédions à Internet d'une manière ou d'une autre.
Que ce soit pour faire des achats en ligne, accéder à notre service de streaming préféré ou publier sur les réseaux sociaux, cela fait désormais partie intégrante de notre quotidien.
En raison de cette utilisation intensive et de cette dépendance à Internet, nous sommes très vulnérables aux cyberattaques. Heureusement, la navigation sur Internet est rendue plus intelligente et plus sûre grâce à un réseau privé virtuel (VPN).
Qu'est-ce qu'un VPN ?
Un réseau privé virtuel ou VPN crée une connexion sécurisée à un autre réseau via Internet. Cela permet d'envoyer et de recevoir des données de manière sécurisée sur des réseaux partagés ou publics sur divers appareils, offrant aux utilisateurs une confidentialité et un anonymat accrus lors de la navigation sur Internet.
Selon IBM, le coût moyen d'une violation de données aux États-Unis s'élève à 9,44 millions de dollars.
En raison de l'augmentation de la cybercriminalité, il n'a jamais été aussi important de garantir la confidentialité de nos données. Utiliser un VPN procure une tranquillité d'esprit lorsque vous devez accéder au réseau de votre entreprise à distance, masquer votre adresse de protocole Internet (IP), ou simplement vous assurer que votre présence en ligne reste non publique. Plongeons plus profondément dans ce qu'est un VPN et ce qu'il fait.
À quoi sert un VPN ?
Il existe de nombreuses situations dans lesquelles un VPN peut être utile. Par exemple, une entreprise protège toutes ses données en les stockant dans un réseau privé.
Cela se fait généralement sur un serveur, un ordinateur réel ou un service hébergé dans le cloud. Étant donné que les données de l'entreprise doivent être sécurisées, le réseau utilisé doit être privé.
Si une entreprise dispose d'une équipe de travailleurs à distance ou d'employés qui voyagent souvent, un VPN étend ce réseau privé, le rendant virtuel et lui permettant d'être accessible de n'importe où.
Cela permet à ces employés de rejoindre le réseau en toute sécurité en utilisant des connexions VPN. Utiliser un VPN signifie que tout cela peut être fait en toute sécurité en continuant à garder toutes les données de l'entreprise privées.
Pour bien comprendre un VPN, il suffit de décomposer son nom.
- Virtuel : Lors de l'utilisation d'un VPN, un utilisateur aura une connexion privée directement à n'importe quel site Web, ou à un autre ordinateur ou appareil connecté à celui-ci.
- Privé : Toutes les visites de sites Web ou toute autre activité en ligne, comme le streaming de divertissement, sont strictement entre l'utilisateur et le site Web visité.
- Réseau : Un utilisateur de VPN a accès à un réseau spécifique au sein du serveur VPN, qui englobe un emplacement spécifique.
Vous voulez en savoir plus sur Logiciel VPN d'entreprise ? Découvrez les produits VPN d'entreprise.
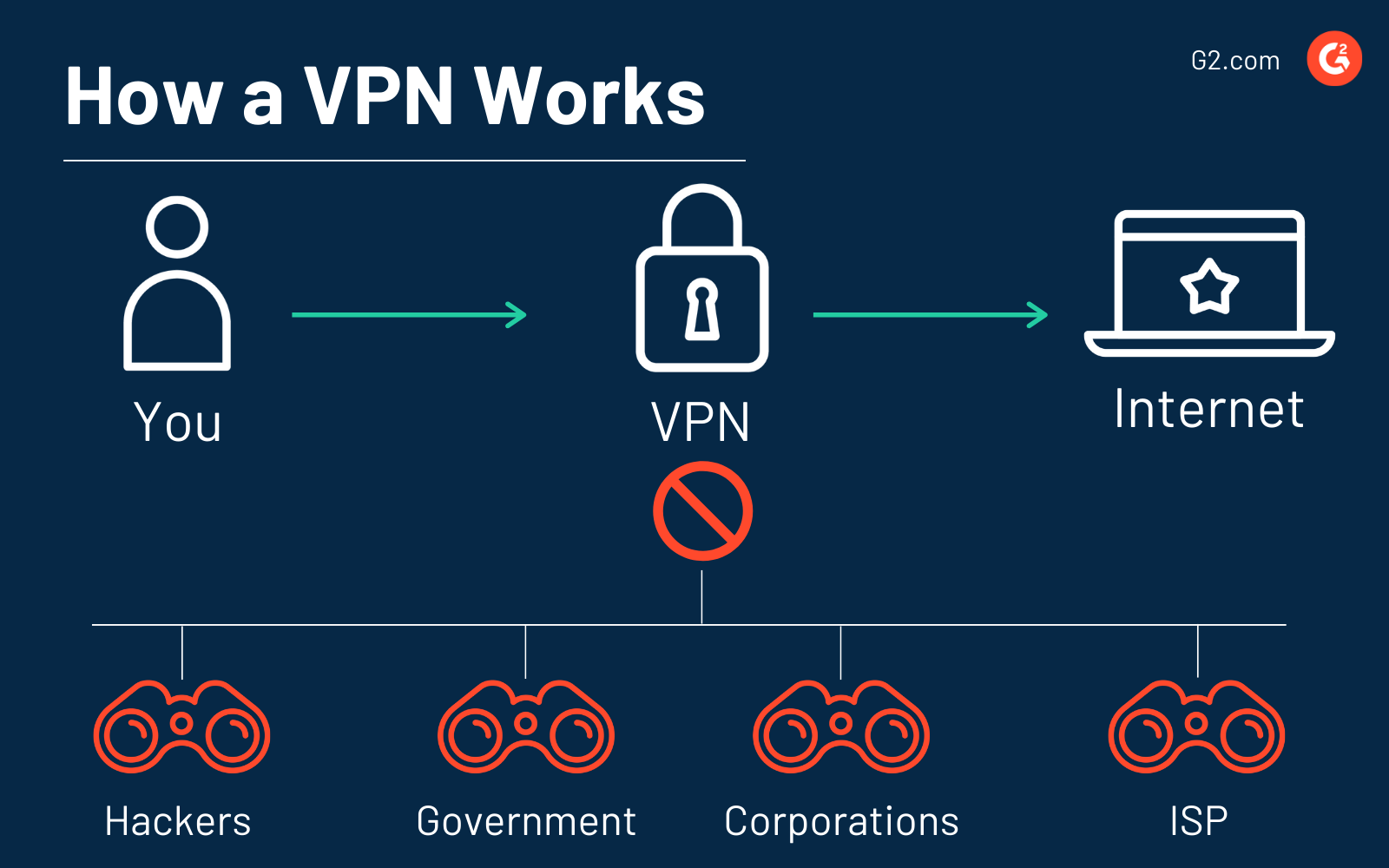
Comment fonctionne un VPN ?
Lorsque vous n'utilisez pas de VPN et que vous accédez à un site Web sur Internet, votre fournisseur d'accès Internet (FAI) vous redirige vers le site Web que vous souhaitez visiter. Tout votre trafic Internet passe par les serveurs de votre FAI, ce qui signifie qu'ils peuvent voir et enregistrer tout ce que vous faites en ligne.
Lorsque vous utilisez un VPN, il redirige votre trafic Internet via un serveur distant configuré. Ensuite, le VPN masque votre adresse IP et crypte toutes les données que vous envoyez ou recevez.
Le VPN agit comme un intermédiaire lorsque vous vous connectez à Internet — il masque votre adresse IP et protège vos informations personnelles. Si quelqu'un essayait d'intercepter les données, comme un pirate ou quelqu'un essayant de voler votre identité, les données ne seraient pas lisibles, ressemblant essentiellement à du charabia.
Cela se fait en créant un tunnel sécurisé qui protège la connexion de votre appareil à Internet. Le tunnel est cité en authentifiant d'abord l'appareil avec un serveur VPN.
Ensuite, le serveur applique un niveau de protection supplémentaire, appelé protocole de cryptage, à toutes les données échangées entre l'appareil et la destination.
Avant que vos données n'atteignent leur destination, toutes vos informations sensibles sont divisées en paquets. Pour une protection supplémentaire, le VPN prend chaque paquet de données et l'enferme dans un paquet extérieur, qui est ensuite crypté par un processus appelé encapsulation.
Ce paquet supplémentaire garde toutes les données sensibles sécurisées lors du transfert de l'appareil à la destination à l'intérieur du tunnel.
Une fois que les données sont arrivées en toute sécurité à leur destination, le processus de décryptage peut commencer.
Il est important de se rappeler que lorsque le paquet de données atteint la destination, il arrivera avec une nouvelle adresse IP fournie par le VPN. Pour cette raison, si vous vous connectez à un serveur dans un autre pays, il semblera que vous naviguez depuis ce pays.
Comment fonctionne le cryptage VPN
Le cryptage cache des informations qui ne peuvent être lues sans un mot de passe spécifique, connu sous le nom de clé. Cette clé est utilisée pour déchiffrer le code complexe dans lequel les données personnelles sont transformées.
Les seuls détenteurs de cette clé sont votre appareil et le serveur VPN. Le processus de décryptage de ces données, connu sous le nom de décryptage, est la manière dont les informations sont rendues à nouveau lisibles grâce à l'application de la clé.
Le processus de cryptage VPN se fait en trois étapes :
- Une fois qu'une connexion est établie au sein du VPN, vos données sont encodées dans un tunnel sécurisé, les rendant illisibles lorsqu'elles voyagent de votre appareil au serveur VPN.
- Votre appareil est maintenant considéré comme étant sur le même réseau que le VPN, donc l'adresse IP utilisée est celle des serveurs du fournisseur de VPN.
- Vous pouvez naviguer sur Internet comme bon vous semble, accéder à une variété de sites Web et de solutions logicielles, car le VPN protège vos informations personnelles.
Le cryptage est utilisé dans plus que les VPN. Par exemple, pensez à toutes les fois où vous entrez votre numéro de carte de crédit lors de vos achats sur un site Web sécurisé. Votre numéro de carte de crédit et toutes vos autres informations privées sont cryptés, les rendant illisibles jusqu'à ce qu'elles atteignent leur destination finale. Dans ce cas, la destination finale serait le site Web sur lequel vous achetez.
Grâce au processus de cryptage, un VPN peut cacher avec succès des éléments tels que :
- Votre historique de navigation et votre activité sur le Web
- Votre adresse IP
- Votre localisation
- Vos données sur un appareil
Pourquoi utiliser un VPN ?
À ce stade, vous vous demandez peut-être si un VPN vaut la peine d'être utilisé et quels sont les avantages d'utiliser un VPN en premier lieu. Il y a de nombreux avantages et raisons pour lesquelles les gens se tournent constamment vers les VPN. Décomposons-les.
Pour changer une adresse IP
Votre adresse IP fonctionne comme votre numéro de téléphone ou votre adresse personnelle dans le sens où elle indique aux sites Web où vous êtes et comment se connecter à votre appareil. Lorsque vous utilisez un VPN, il vous fournit une nouvelle adresse IP, de sorte que tout votre trafic semblera provenir d'ailleurs.
Pour rester en sécurité lors de l'utilisation du WiFi public
Il n'est pas rare de se rendre à la bibliothèque la plus proche ou au café avec votre appareil et de rejoindre le WiFi public. Nous le faisons tout le temps -- mais les pirates aussi.
Tout ce dont ils ont besoin, c'est d'un équipement simple et ils peuvent avoir accès à vos noms d'utilisateur et mots de passe lorsqu'ils passent par un point WiFi partagé. Utiliser un VPN crypte ces informations, les rendant illisibles pour un pirate.
Pour bloquer le suivi en ligne
Combien de fois avez-vous cherché une nouvelle paire de chaussures en ligne pour voir une publicité pour ces mêmes chaussures sur un autre site Web cinq minutes plus tard ? Ou peut-être avez-vous acheté en ligne des grenouillères pour le nouveau-né de votre meilleur ami, pour être montré des publicités pour des vêtements pour bébé pendant les six mois suivants.
Ça nous est tous arrivé, mais lorsque vous utilisez un VPN, vous pouvez empêcher les annonceurs d'envahir votre vie privée en ligne en ciblant votre adresse IP pour des publicités. En cryptant votre trafic et en remplaçant votre adresse IP, vous évitez de laisser une empreinte en ligne qu'un FAI ou une agence tierce peut suivre.
Pour voyager en toute sécurité
Que vous voyagiez pour le travail ou que vous souhaitiez vérifier les choses pendant vos vacances, vous pouvez constater que vous ne faites pas confiance au WiFi de votre hôtel.
Grâce au cryptage VPN, vous pouvez vérifier vos e-mails en toute sécurité, réserver un nouveau vol pour rentrer chez vous ou transférer de l'argent sur votre compte bancaire. Cela signifie que vous pouvez accéder à la fois au réseau de votre entreprise pour accéder aux documents de travail et à votre réseau domestique, peu importe à quelle distance vous vous trouvez.
Pour télécharger des fichiers
Que vous vouliez l'admettre ou non, un VPN sera utile lors du téléchargement de fichiers en utilisant BitTorrent, qui est un protocole de communication pour le partage de fichiers peer-to-peer pour distribuer des données et des fichiers sur Internet.
Le peer-to-peer est l'une des méthodes les plus rapides et les plus efficaces pour partager de grands ensembles de données sur un réseau. Néanmoins, de nombreux FAI découragent les utilisateurs d'Internet de ce type de partage de fichiers.
Si votre FAI rend quelque chose comme BitTorrent extrêmement lent, vous pouvez choisir de l'utiliser via un VPN, permettant un accès à des vitesses plus rapides et un partage facile.
Pour éviter la censure sur Internet
Si vous vous retrouvez à voyager dans un pays étranger, un VPN peut vous aider à contourner la censure sur Internet et à accéder à des services qui peuvent être bloqués. Par exemple, la Chine bloque certaines plateformes de médias sociaux, comme Facebook. Si vous vous retrouvez en vacances là-bas, vous pourriez également perdre l'accès à certains sites Web.
Étant donné qu'un VPN peut changer votre adresse IP pour qu'il semble que vous êtes situé ailleurs, vous pouvez vous connecter à un serveur VPN dans votre pays d'origine, vous permettant d'accéder à tous vos sites Web préférés.
Conseil : Découvrez si l'utilisation d'un VPN est légale dans le pays où vous vivez ou dans le pays où vous allez voyager.
Types de VPN
Il existe essentiellement deux types de VPN que vous pouvez utiliser. Celui que vous choisissez dépendra de l'utilisation que vous ferez du VPN.
1. VPN d'accès à distance
Un VPN d'accès à distance permet à un utilisateur de se connecter à un réseau privé et d'accéder à tous ses services et ressources tout en étant complètement à distance.
La connexion créée entre l'utilisateur et le réseau privé se fait via Internet, permettant à la connexion d'être complètement privée et sécurisée. Ce type de VPN est généralement utile à la fois pour les utilisateurs à domicile et les utilisateurs professionnels.
Par exemple, un utilisateur à domicile utilise généralement un VPN pour contourner les restrictions régionales sur Internet et accéder à des sites Web bloqués. Un employé d'une entreprise qui travaille actuellement à distance peut utiliser un VPN pour se connecter au réseau de son entreprise, lui permettant d'accéder à des fichiers et des ressources sur un réseau privé.
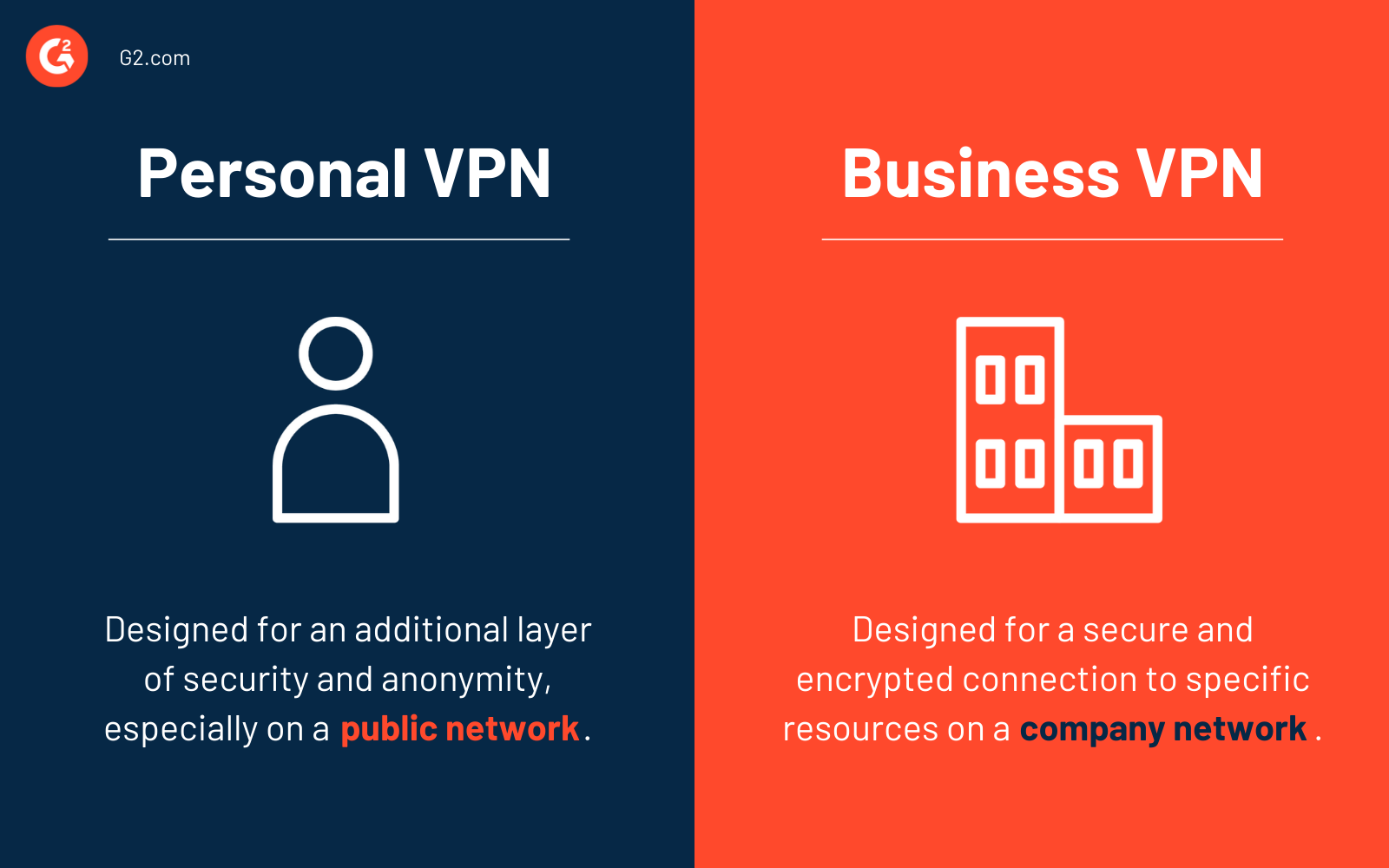
VPN personnel vs VPN d'entreprise
Il est important de noter qu'il existe quelques différences clés entre un VPN personnel et un VPN d'entreprise.
Comme son nom l'indique, un VPN personnel est celui que vous utiliseriez à la maison ou pour des affaires personnelles. Par exemple, vous utiliseriez un VPN personnel lorsque vous utilisez un réseau WiFi public. Il en va de même si vous essayez d'accéder à une vidéo YouTube géo-restreinte.
Un VPN d'entreprise, parfois aussi appelé VPN d'entreprise, offre aux employés d'une organisation spécifique la possibilité d'utiliser une connexion sécurisée de bout en bout cryptée pour accéder aux ressources cloud sur un réseau d'entreprise.
2. VPN site-à-site
Un VPN site-à-site, également appelé VPN routeur-à-routeur, est principalement utilisé par les grandes entreprises ou organisations qui ont des bureaux à différents endroits. Cela permet à ces entreprises de connecter le réseau d'un bureau à celui d'un autre bureau.
Pensez à cela comme un pont imaginaire entre les deux réseaux qui les connecte à Internet tout en restant une connexion sécurisée et privée.
Dans les VPN site-à-site, il existe deux façons de procéder :
- VPN basé sur l'intranet : Lorsque plusieurs bureaux de la même entreprise sont connectés à l'aide d'un VPN site-à-site.
- VPN basé sur l'extranet : Lorsque des entreprises utilisent des VPN site-à-site pour se connecter au bureau d'une autre entreprise.
Lorsqu'un VPN site-à-site est utilisé, un routeur agit comme le client VPN, et un autre routeur est utilisé comme serveur VPN puisque ce type est basé sur la communication routeur-à-routeur. Lorsque l'authentification est terminée entre les deux routeurs, la communication peut commencer.
Comment choisir le bon VPN
Il ne fait aucun doute que le marché des VPN est saturé d'options, alors lors du choix d'un logiciel VPN, posez-vous ces questions :
- Pourquoi avez-vous besoin d'un VPN ? Cherchez-vous à sécuriser votre domicile ou votre lieu de travail ? Quel type d'activités en ligne allez-vous faire qui nécessitent un VPN ? Regarder des films en streaming ? Travailler en ligne en voyageant ?
- Quelles qualités recherchez-vous dans un VPN ?Le VPN devra-t-il prendre en charge plus d'une connexion ? Voulez-vous de la vitesse ? De l'anonymat ? Un meilleur cryptage ?
- Quels outils VPN ont ces éléments sur ma liste de souhaits ?Éliminez les options qui ne peuvent pas vous fournir ce dont vous avez besoin. Notez particulièrement le protocole VPN - il déterminera les niveaux de cryptage et de sécurité.
- Quel est votre budget ?Voyez ce que vous pouvez vous permettre. Plus un VPN a de capacités, plus il sera généralement cher.
Protocoles VPN
Les deux types de VPN sont basés sur six protocoles de sécurité VPN différents. Chaque protocole VPN offre aux utilisateurs différentes fonctionnalités et niveaux de sécurité en fonction de leurs besoins.
- Internet Protocol Security : Également connu sous le nom d'IPSec, ce protocole est utilisé pour sécuriser toutes les communications Internet sur un réseau IP. Cela se fait en authentifiant la session et en cryptant chaque paquet de données pendant la connexion. Ce protocole peut être utilisé en conjonction avec d'autres pour augmenter la sécurité.
- Layer 2 Tunneling Protocol : L2TP est un protocole de tunneling qui est généralement combiné avec IPSec pour créer une connexion VPN extrêmement sécurisée. Cela se fait en construisant un tunnel entre deux points de connexion L2TP et le protocole IPSec pour crypter les données et protéger la communication entre le tunnel.
- Point-to-Point Tunneling Protocol : PPTP est l'un des protocoles VPN les plus couramment utilisés. Il construit un tunnel et enferme le paquet de données. Il utilise un protocole point-à-point (PPP) pour crypter les données entre la connexion.
- Secure Socket Layer et Transport Layer Security : SSL et TLS créent une connexion VPN spécifique où le navigateur Web agit comme le client, et l'accès de l'utilisateur est restreint à certaines applications au lieu de l'ensemble du réseau. Ce protocole est principalement utilisé par les sites Web de commerce en ligne et les fournisseurs de services.
- OpenVPN : OpenVPN utilise un protocole de sécurité personnalisé basé sur les protocoles SSL et TLS. C'est un VPN open-source qui est utile pour créer des connexions point-à-point et site-à-site.
- Secure Shell : SSH crée un tunnel VPN où le transfert de données a lieu, garantissant que le tunnel est correctement crypté. Ce protocole transfère les données d'un port local sur un serveur distant via le tunnel crypté.
Meilleur logiciel VPN
Bien que différents services en ligne comme Proxy vous permettent de masquer votre adresse IP et de rediriger le trafic Internet, les VPN offrent un ensemble complet pour garantir une sécurité et une confidentialité supplémentaires.
Que vous utilisiez Internet pour faire des achats en ligne ou accéder aux ressources de votre entreprise en tant que travailleur à distance, laissez un VPN s'occuper de réduire tout risque de violation de données ou de poursuite éventuelle qui pourrait en découler.
Pour être inclus dans notre catégorie de logiciels VPN, un produit doit :
- Utiliser des systèmes de cryptage et de sécurité pour connecter des appareils à des réseaux privés.
- Restreindre l'accès aux réseaux privés et aux données sensibles exclusivement pour le personnel autorisé.
- Identifier le trafic réseau au niveau du paquet pour encoder les données sensibles.
- Utiliser des protocoles de tunneling pour acheminer les connexions vers des réseaux sûrs.
* Ci-dessous figurent les 10 principaux logiciels VPN du rapport Grid® de l'hiver 2023 de G2. Certains avis peuvent être modifiés pour plus de clarté.
1. NordVPN
NordVPN aide les entreprises à sécuriser leur réseau et leurs connexions Internet en ajoutant une couche de protection supplémentaire pour sécuriser toutes les communications. Grâce à un cryptage fort appliqué à tout le trafic entrant et sortant, aucun tiers ne peut accéder aux informations confidentielles.
Ce que les utilisateurs aiment :
« Fournissant la meilleure passerelle sécurisée, NordVPN a parcouru un long chemin pour nous permettre de nous sentir libres à l'ère des problèmes de confiance. Il ne fournit pas seulement une politique de non-journalisation, mais il offre également une protection totale lors de la navigation sur Internet. Un compte peut être utilisé pour de nombreux appareils à des fins de protection. Avec un forfait très raisonnable, il donne accès à chaque version différente de contenu géo-bloqué et élargit les vues. »
- Avis NordVPN, Jeremy P., 7 avril 2020
Ce que les utilisateurs n'aiment pas :
« De temps en temps, j'ai observé quelques problèmes de connectivité avec certains serveurs. De plus, les plans tarifaires de NordVPN peuvent être plus chers que ceux d'autres fournisseurs de VPN, ce qui semble être un peu problématique pour moi. »
- Avis NordVPN, Abhijeet S., 22 mars 2023
2. Absolute Secure Access
Absolute Secure Access est un VPN d'entreprise qui permet aux utilisateurs d'accéder en toute sécurité à des ressources cruciales dans un cloud public et de sécuriser les informations confidentielles. La suite logicielle comprend trois produits, Absolute VPN pour sécuriser les données en mouvement, Absolute ZTNA pour éloigner les utilisateurs non autorisés, et Absolute Insights pour surveiller et améliorer l'expérience de travail à distance.
Ce que les utilisateurs aiment :
« Absolute Secure Access facilite vraiment l'accès de nos utilisateurs aux ressources professionnelles sur le terrain. La plupart de nos utilisateurs surveillent continuellement les systèmes professionnels et ont besoin d'une communication constante avec ces systèmes. Absolute Secure Access rend ce processus fluide et sans frustration. »
- Avis Absolute Secure Access, Micheal W., 9 février 2023
Ce que les utilisateurs n'aiment pas :
« La courbe d'apprentissage initiale est un peu écrasante, mais je suggère de suivre leur excellent cours de certification qui vous permettra de créer des politiques en un rien de temps ! »
- Avis Absolute Secure Access, Mike S., 10 février 2023
3. pfSense
pfSense est un logiciel de pare-feu et de routage open-source. Basé sur le système d'exploitation FreeBSD, cette solution de sécurité réseau est idéale pour un usage personnel et professionnel. Il dispose d'une interface utilisateur basée sur le Web et de plusieurs fonctionnalités telles que la traduction d'adresses réseau (NAT), la protection contre l'usurpation, le blocage d'applications, le cryptage SSL, la prise en charge multilingue, et plus encore, ce qui lui donne un avantage sur d'autres solutions commerciales.
Ce que les utilisateurs aiment :
« La puissance et la flexibilité que pfSense apporte à votre réseau sont exceptionnelles. La capacité VPN intégrée signifie que se connecter à mon réseau depuis l'extérieur est facile et ne nécessite pas de matériel supplémentaire. Le contrôle complet sur la façon dont les paquets circulent vers et depuis Internet, et même à travers les réseaux locaux ; signifie que j'ai un contrôle qui me permet de garder mon réseau fonctionnant efficacement et en toute sécurité. Si vous êtes habitué à traiter uniquement avec le matériel que votre fournisseur vous donne, pfSense est un pas en avant significatif. »
- Avis pfSense, Jay M., 26 février 2023
Ce que les utilisateurs n'aiment pas :
« Le principal inconvénient pour moi est qu'il faut un peu de temps pour se familiariser et se sentir à l'aise avec l'outil, mais même cela est une petite critique car c'est vrai pour toute technologie. Étant donné que la documentation est robuste et librement disponible, le seul coût est le temps qu'il faut pour la lire et la comprendre. »
- Avis pfSense, Dorian D., 20 mars 2023
4. ExpressVPN
ExpressVPN offre aux utilisateurs un VPN facile à utiliser et à haute vitesse qui est ultra-sécurisé. De plus, avec une configuration instantanée et une bande passante illimitée sur jusqu'à cinq appareils, vous pouvez être sûr d'être protégé contre les attaquants.
Ce que les utilisateurs aiment :
« Il est facile de se connecter et il fonctionne en arrière-plan, ne causant aucun ralentissement de la vitesse Internet. Il s'allume tout seul, donc vous n'avez même pas besoin d'y penser après l'avoir installé. »
- Avis ExpressVPN, Angeline H., 20 mai 2022
Ce que les utilisateurs n'aiment pas :
« Parfois, il y a des problèmes de connexion avec la version pour ordinateur portable. Cela se produit lorsque l'ordinateur portable "s'endort". Le VPN a alors du mal à se reconnecter et doit parfois être "réparé" en utilisant la fonction Ajouter/Supprimer des applications dans Windows. »
- Avis ExpressVPN, John S., 5 juillet 2022
5. Perimeter 81
Perimeter 81 est un service de sécurité cloud-native qui permet aux organisations d'accéder en toute sécurité aux ressources, de gérer les réseaux et de réduire le risque de violations de données. Le logiciel propose une gamme de fonctionnalités telles que l'authentification multi-facteurs, le filtrage Web, la protection automatique du Wi-Fi et la gestion des identités pour une expérience cyber-sécurisée.
Ce que les utilisateurs aiment :
« Interface simple et intuitive qui est facile à utiliser. Même un utilisateur novice et quelqu'un qui n'est pas bien versé dans la sécurité cloud peut facilement gérer son compte. »
- Avis Perimeter 81, Himanshu D., 14 novembre 2022
Ce que les utilisateurs n'aiment pas :
« Parfois, j'essaie de me connecter à un réseau externe et cela ne me permet pas, je dois redémarrer la machine et ensuite je peux me connecter à des réseaux externes via Perimeter 81. »
- Avis Perimeter 81, Ronald B., 24 mai 2022
6. ProtonVPN
ProtonVPN est conçu avec la sécurité comme principal objectif. Il envoie le trafic Internet à travers un tunnel crypté, de sorte que les mots de passe et les données confidentielles restent en sécurité même lorsqu'ils sont utilisés sur une connexion Internet publique ou non fiable.
Ce que les utilisateurs aiment :
« Facile à utiliser, tunneling VPN sécurisé d'une entreprise de confidentialité réputée avec un modèle commercial compréhensible qui s'aligne sur ses utilisateurs. Offre toujours une option gratuite pour protéger tout le monde et aussi pour démontrer comment le produit fonctionne. »
- Avis ProtonVPN, Richard P. 10 juin 2022
Ce que les utilisateurs n'aiment pas :
« Il n'y a pas beaucoup d'inconvénients à ProtonVPN ; cependant, les plans payants sont un peu chers sur le marché actuel. La fonctionnalité manquante la plus importante est le tunneling fractionné, où nous ne pouvons pas sélectionner quelles applications utiliser le VPN et lesquelles ne pas utiliser. »
- Avis ProtonVPN, Srivatsa V., 6 mars 2023
7. OpenVPN Access Server
OpenVPN offre aux utilisateurs des solutions VPN flexibles pour sécuriser leurs communications de données, que ce soit pour la confidentialité sur Internet, l'accès à distance pour les employés, la sécurisation de l'IoT ou la mise en réseau des centres de données cloud.
Ce que les utilisateurs aiment :
« J'aime qu'il ait des mises à jour fréquentes. L'installation et la configuration sont simples et assez intuitives. Il y a beaucoup de documentation disponible pour aider en cours de route. Il est livré avec quelques licences gratuites pour un usage personnel, donc cela satisfait mes besoins. Il a un installateur côté client très facile intégré au serveur. »
- Avis OpenVPN, Rajat H., 7 mars 2023
Ce que les utilisateurs n'aiment pas :
« Parfois, les profils client/employé expirent ou cessent de fonctionner sans raison. C'est très facile à réparer, mais cela cause encore une petite gêne de temps en temps. À part cela, rien ne se démarque. »
- Avis OpenVPN, Wyatt H., 13 mai 2022
8. NordLayer
NordLayer, anciennement connu sous le nom de NordVPN teams, est une solution de sécurité d'accès réseau basée sur le cloud. Elle offre aux entreprises plusieurs fonctionnalités telles que l'authentification à deux facteurs (2FA), la connexion unique (SSO), la connexion automatique et la détection des appareils jailbreakés pour garder les activités professionnelles à l'abri des regards indiscrets. L'application est disponible en téléchargement pour Windows, Mac, Android, iOS et Linux.
Ce que les utilisateurs aiment :
« NordLayer était facile à configurer et à gérer pour mon équipe. Nous avions besoin à la fois de la sécurité d'un VPN et d'une IP statique pour toute l'équipe, et NordLayer nous offre les deux à un prix qui est en ligne avec la concurrence. »
- Avis NordLayer, Steve K., 23 février 2023
Ce que les utilisateurs n'aiment pas :
« Parfois, certains des serveurs auxquels vous vous connectez seront lents, peut-être qu'ils ont de nombreux utilisateurs connectés ou beaucoup de données passant par ce serveur, mais une reconnexion rapide résout le problème. »
- Avis NordLayer, Michael M., 23 février 2023
9. Check Point IPsec VPN
Check Point IPsec VPN propose plus de 60 services de sécurité innovants pour prévenir les cyberattaques méga multi-vecteurs. Ils ont une gamme d'options pour les petites, moyennes et différentes tailles d'entreprises.
Ce que les utilisateurs aiment :
« Check Point est une plateforme VPN solide avec une optimisation matérielle et logicielle et des capacités d'administration exceptionnelles. Avec des fonctionnalités croisées telles que l'accélération matérielle et l'ASIC, cela rend cette solution parfaite pour une sécurité de haut niveau au niveau des banques d'entreprise. »
- Avis Check Point IPsec VPN, Jose A., 27 mai 2022
Ce que les utilisateurs n'aiment pas :
« Il faut utiliser beaucoup de commandes de débogage pour résoudre complètement certains problèmes. »
- Avis Check Point IPsec VPN, Ozan D., 20 juillet 2022
10. Twingate
Twingate est une solution d'accès à distance sécurisée, basée sur le modèle moderne de réseau de confiance zéro. Il utilise quatre composants, à savoir le contrôleur, les clients, les connecteurs et les relais pour garantir que seuls les utilisateurs autorisés ont accès aux ressources.
Ce que les utilisateurs aiment :
« Twingate suit un modèle de sécurité de confiance zéro dans lequel les implémentations sont effectuées avec les privilèges d'accès les plus bas pour notre plateforme client. Il ne permet pas à une seule ressource de prendre en charge la gestion du trafic de manière indépendante pour prévenir les violations de réseau et fonctionne avec des stratégies de distribution de nœuds. Nous pouvons réguler l'autorisation d'accès des utilisateurs en mettant en œuvre des étapes d'approbation pour la prise de décision sensible et les améliorations de visibilité. »
- Avis Twingate, Rithika G., 16 mars 2022
Ce que les utilisateurs n'aiment pas :
« Il y avait quelques étapes dont nous n'étions pas au courant au début et naviguer dans la documentation n'était pas toujours intuitif. En particulier, la configuration des noms d'hôte/adresses non-FQDN et sur le domaine (AD) via Twingate était quelque chose à apprendre et n'avait pas de moyen facile à configurer. De plus, les mises à jour du client avec des utilisateurs non administrateurs sont plutôt maladroites. Je finis généralement par télécharger à nouveau le fichier d'installation au lieu d'utiliser la fonctionnalité de mise à jour intégrée. »
- Avis Twingate, Bryan V., 7 juin 2022
Chaque mouvement que vous faites, ils vous observeront
Il n'y a jamais eu de meilleur moment pour protéger votre droit à la vie privée en ligne, et utiliser un VPN est un excellent point de départ. Peu importe où vous accédez à Internet, et ce que vous avez envie de faire, un VPN peut garantir que personne ne regarde et que vos données sont gardées à l'abri des regards indiscrets.
Faites le pas suivant et apprenez comment configurer un VPN pour que votre identité et vos données restent sécurisées.
Cet article a été publié à l'origine en 2019. Le contenu a été mis à jour avec de nouvelles informations.

Mara Calvello
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes content highlighting G2 newsroom events and customer marketing case studies, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.
