Sensitive data needs protection.
Encryption helps safeguard sensitive data that organizations store, transmit, or use by converting them into incomprehensible forms.
Companies need to be aware of their data and its location. Some organizations use sensitive data discovery tools to find information so that no data is left exposed. Encryption tools then transform this data into ciphertext (random sequence of characters generated through mathematical calculations), making it inaccessible for unauthorized users.
What is encryption?
Encryption is the process of protecting actual data or information by converting it into a secret code. Anyone trying to access encrypted data would need an encryption key to decode it.
A cryptographic (or encryption) key is a set of mathematical values that are mutually agreed upon by a sender and a receiver. It ensures that the data is only available to people who have the authority to access it. Businesses use encryption key management software to centralize all keys and protect them from unauthorized access. It's used to monitor encryption keys and control their availability to users as it can risk data security when in the wrong hands.
The encryption process involves the conversion of plaintext into ciphertext, which is unintelligible. Ciphertext at times might appear to be a random sequence, but there is logic in its core.
Organizations need to maintain secure encryption with a complex key, making it challenging and less profitable for attackers to crack. They can use encryption software to maintain data integrity and confidentiality while reducing the liability if the data gets exposed or breached.
Why is encryption important?
Modern businesses work with ample personal data of their clients and employees. Protecting this data becomes a responsibility to maintain a business' reputation and avoid legal penalties. Encryption helps companies store and transmit data securely while keeping integrity and confidentiality intact.
Encryption serves data security in many ways:
- Authentication: Public key encryption verifies that the website's owner has the private key listed in a Transport Layer Security (TSL) certificate. It provides confidence to users that they are connecting to a genuine website.
- Integrity: Encryption ensures that unauthorized users don't tamper with the data in transmission or storage. It proves that information is not changed while flowing from the source to a recipient.
- Confidentiality: Encryption encodes data and prevents it from being exposed. It blocks malicious attackers or any unauthorized entity from accessing the data at rest or in transmission.
- Security: Encryption ensures information security even when the devices are stolen or misplaced. It helps businesses prevent data breaches and allows secure communication where parties can exchange information without a security risk.
- Regulations: Encryption helps organizations comply with several industry standards that gauge data security with paramount importance. For example, Payment Card Industry Data Security Standard (PCI DSS) or Health Insurance Portability and Accountability Act (HIPAA).
Data security is at the core of modern technology that works with several related entities. Encryption ensures that sensitive information shared between these entities isn't prone to leakage or exposure, making it an essential part of any good data security program.
Want to learn more about Encryption Software? Explore Encryption products.
How does encryption work?
Encryption uses several algorithms to decode data. For example, a message, "My name is Steve" would be encoded to a ciphertext, like "fweji2j320wfeoi93dfs". When it's sent to a recipient, they'd require an encryption key to decode the message.
Here are a few essential terms to help understand encryption:
- Encryption algorithm: An algorithm, also known as a cipher, is a set of rules that an encryption process follows. It includes key length, features, and functionalities that ensure effective encryption.
- Decryption: A process of converting ciphertext to plaintext.
- Encryption key: A randomized sequence of characters that are used to encrypt or decrypt data. Typically, private keys are 128 bits or 256 bits, and public keys are 2048 bits.
Encryption works at the core of Hypertext Transfer Protocol Secure (HTTPS) to maintain secure communication between a user and a server over a network. HTTPS uses TLS encryption protocol, which has superseded Secure Sockets Layer (SSL) in recent years.
Tip: Any website that follows HTTPS will have https:// in the URL instead of http://. You can find a secured lock symbol in your browser's address bar when you connect with a website.
Symmetric vs. asymmetric encryption
The main difference between symmetric and asymmetric encryption lies in the usage of encryption keys.
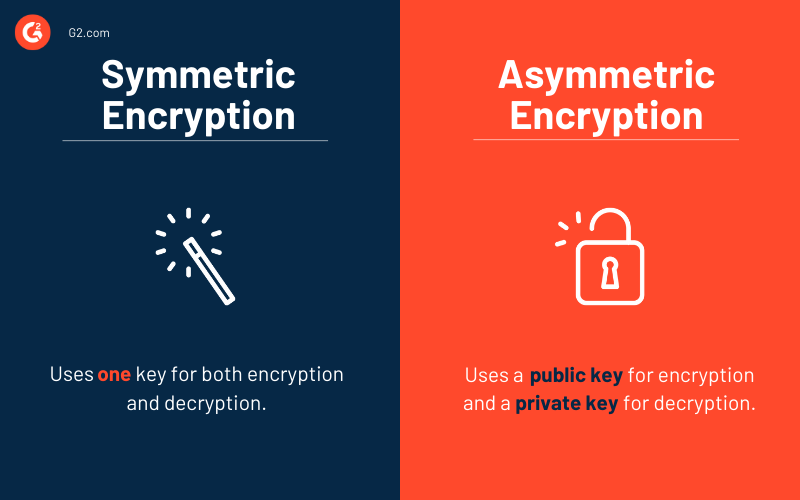
Symmetric encryption uses one key for both encryption and decryption. It acts as a shared secret that allows parties to encrypt or decrypt information. Symmetric encryption algorithms are less complex and comparatively faster to execute, making them a preferred choice for carrying bulk data transmission.
Symmetric encryption algorithms involve using block ciphers or stream ciphers. For example, the advanced encryption standard (AES) uses a block size of 128-bits (or 192, 256-bits), where the number of bits is encrypted as one unit.
Key exhaustion (using one key many times) is one issue that hampers symmetric encryption. In the absence of proper key hierarchy and effective key rotation, there can be information leakage that attackers can exploit to recreate a secret key. Examples of symmetric encryption include RC4, DES, 3DES, and more.
Asymmetric encryption, also known as public-key cryptography or public-key encryption, uses a pair of encryption keys: a public key and a private key.
A public key is used to encrypt a message and is accessible to everyone. Conversely, a private key is used to decrypt a message, and it's only shared with the key's initiator to maintain privacy. Both the keys are mathematically related, but you cannot derive a private key from a public key.
Asymmetric encryption is more complicated and time consuming, but it offers robust security compared to symmetric encryption. The length of keys in asymmetric encryption is comparatively larger. For example, Rivest–Shamir–Adleman (RSA) key can be 2048-bit. There are various other asymmetric encryption algorithms like Diffie-Hellman, Elliptic curve cryptography, and more.
List of encryption algorithms
Encryption algorithms use different key sizes, complexities, and methods to encrypt and decrypt a message. Here are a few common encryption algorithms.
AES
Advanced encryption standard (AES), also known as Rijndael, is a trusted cipher approved by the US National Security Agency (NSA) for protecting sensitive information. It falls under symmetric encryption, where one key is used for both encrypting and decrypting data.
AES encryption is facilitated by keys of different lengths that have several possible combinations.
There are three commonly used AES encryption key lengths:
-
128-bit with 3.4 x 10³⁸ combinations
-
192-bit with 6.2 x 10⁵⁷ combinations
-
256-bit with 1.1 x 10⁷⁷ combinations
AES 256-bit encryption is typically used in places where there's a need for more robust security. Even though there are multiple key lengths available in which AES 256 encryption is the strongest, using it everywhere might not be wise. For example, an app employing AES 256-bit encryption will drain your mobile battery faster than an app that uses AES 128-bit encryption.
Triple DES
Triple Data Encryption Standard (3DES) applies block cipher algorithms three times to each data block, ensuring stronger security. DES originally came with a 64-bit block and a 56-bit encryption key, making it less secure due to the short key length. 3DES was introduced to provide enhanced security with 3 x 56-bit encryption key length, where the security typically falls to 112-bit. The three keys in 3DES are k1, k2, and k3, which encrypt data three times.
3DES was the encryption of choice in the 1990s, but with the introduction of more secure encryption standards like AES, it’s been pushed to the backburner.
SNOW
SNOW is a word-based stream cipher that works on 32-bit words and 128-bit and 256-bit encryption keys. There isn't any intellectual property or other restrictions associated with the SNOW encryption algorithm. It has a short initiation phase and a remarkable performance on 32-bit processors and hardware.
There are three versions of the SNOW encryption algorithm:
-
SNOW 1.0 was used in the eSTREAM project, a project organized by the EU Encrypt network to identify new ciphers for widespread adoption.
-
SNOW 2.0 is a stream cipher chosen for International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) standard ISO/IEC 18033-4.
-
SNOW 3G was selected as a stream cipher for 3GPP encryption algorithms, UAE2 and UIA2.
Diffie-Hellman key exchange
Diffie-Hellman key exchange is a renowned development in public-key cryptography that allows two parties to create a shared key and use it for secure communication over an insecure channel. The parties involved haven't previously met.
The goal of the Diffie-Hellman key exchange is to securely establish shared secrets that you can use to derive keys. Then, with the use of these keys, you can transmit information in a protected manner.
RSA
Rivest–Shamir–Adleman (RSA) is a type of asymmetric encryption that finds its use in modern computers. The RSA encryption algorithm emanates from the idea that finding factors of a large composite number is a complex task.
It involves a public key and a private key, where the private key is a secret and cannot be easily calculated from a public key. RSA encryption is commonly used with other encryption schemes or digital signatures. It's not generally used to encrypt a complete message due to its inefficiency and resource-heavy structure.
Elliptic curve cryptography
Elliptic curve cryptography (ECC) leverages the mathematics of elliptic curves to generate key pairs for public-key encryption. It's gaining popularity as an alternative to RSA due to its smaller key size and the ability to maintain security.
ECC creates keys that are trickier to crack as they're based on how elliptic curves are structured algebraically over finite fields. In contrast to RSA, ECC encryption is quicker and uses less memory. Even though ECC provides greater security for a particular key length, it's not easy to securely implement compared to RSA. It has a steeper learning curve and takes longer to produce actionable results.
Quantum key distribution
Quantum key distribution (QKD) uses quantum mechanics while implementing a cryptographic protocol that enables two parties to establish a random shared key and have secure communication.
The security aspect of Quantum key distribution lies in the foundations of quantum mechanics rather than how difficult it is to crack a mathematical function. But the main drawback of using QKD is that it relies on a prior exchange of a symmetric key or public key. If there has been an exchange, parties can establish secure communication by AES without using quantum key distribution.
Parties can use Quantum key distribution to establish and distribute a key and then use another encryption algorithm like AES to encrypt or decrypt a message.
Blowfish
The Blowfish encryption algorithm is a symmetric block (64-bit) cipher that uses keys of variable lengths ranging from 32-bit to 448-bit. It's an unpatented and license-free encryption algorithm that everyone can use for free.
Bruce Schneier, an American cryptographer, designed Blowfish in 1993. It displayed a remarkable encryption rate and strong defense against cryptanalysis. However, AES has been a prominent encryption algorithm in the industry, and Schneier recommends Twofish for modern applications.
The major weakness that Blowfish cipher had was its vulnerability to birthday attacks (in contexts like HTTPS) due to its 64-bit block size. In 2016, the SWEET32 attack demonstrated how hackers could recover plaintext by performing birthday attacks against ciphers with 68-bit block size.
Did you know? A birthday attack is a cryptographic attack that leverages mathematics behind a birthday problem in probability theory to abuse communication between two parties.
Twofish
Twofish is a symmetric encryption algorithm that uses a block size of 128-bits and key sizes up to 256 bits. It was introduced in 1988 by Bruce Schneier and the extended Twofish team. For 128-bit keys, Twofish was slower than AES but was comparatively faster for 256-bit key sizes.
Twofish was created as a highly flexible algorithm that allows several layers of performance tradeoffs. It depended on encryption speed, memory usage, key setup, hardware gate count, and various other parameters. This encryption algorithm can be used by anyone for free and isn't patented by publishers.
Types of encryption
Different types of encryption are suitable for users based on their particular use cases, infrastructure, and various other parameters.
Here are a few common types of encryption:
- Encryption as a service (EaaS) provides a way for users that lack resources to manage encryption themselves, enabling them to comply with regulations and secure data in multi-tenant environments.
- Bring your own encryption (BYOE) fits cloud service users who want to manage their encryption software and keys.
- Cloud storage encryption is facilitated by cloud service providers who encrypt data using algorithms and store them.
- Deniable encryption allows encrypted text to decrypt in two or more ways based on the encryption key that a party uses.
- Column-level encryption is suitable for database encryption where each cell in a particular column can be accessed using the same password.
- Field-level encryption manages the encryption of data on a particular field of a webpage. For example, encrypting social security numbers or credit card numbers, etc.
- End-to-end encryption (E2EE) ensures that unauthorized users cannot intercept communications between two parties. It uses an encrypted communication circuit where the client software encrypts the message, and the recipient decrypts the message when it reaches them.
- Full-disk encryption (FDE) works at a hardware level and converts all data on a disk into an incomprehensible form that a party can only access with an authentication key.
- Network-level encryption is implemented through Internet Protocol Security (IPSec) that ensures secure communications at the network transfer layer.
- Link-level encryption ensures that the data is encrypted when transmitted from a host and decrypted when it reaches the following link or a relay point. Data is encrypted again when it leaves for the next link or relay point.
- Hypertext Transfer Protocol Secure ensures encryption of every content that a web server sends and verifies whether a public key certificate is installed.
- Homomorphic encryption converts data into ciphertext that can be processed, allowing users to conduct complex operations on encrypted data.
Benefits of encryption
Encryption technology helps you protect your data. It's as old as the art of communication itself. Egyptians used to hide inscriptions’ true meanings with nonstandard hieroglyphs back in 1900 BC, and the same ideology runs parallel while securing data in modern age encryption. It offers various benefits to users and provides the much-needed assurance that their data is safe and secure.
It ensures data confidentiality and integrity while storing or transmitting data over networks, enabling businesses to prove compliance with various regulatory standards. For example, PCI DSS compliance requires a merchant to encrypt a client's card details at rest and in transmission.
50%
of organizations have an overall encryption strategy applied consistently across the entire enterprise in 2021.
Source: Ponemon Institute
Moreover, encryption protects sensitive data that includes personal information while ensuring privacy and anonymity. It safeguards your customers' data from being exposed to malicious hackers or surveillance government agencies.
Challenges of encryption
Encryption is a beneficial asset for businesses in ensuring data security. Still, it's one part of several security solutions that together constitute an organization's cybersecurity program. There are many challenges organizations encounter when implementing encryption mechanisms.
The weakest link to an organization's cybersecurity is a human. Even though encryption ensures security mathematically, a user might disable it due to its complexities or share decryption keys in an insecure manner.
Being a single unit in a business' security arsenal, encryption is often paired with security solutions like endpoint security software, SIEM software, and various others. These tools can provide a blurred sense of security, but they open wide security gaps if not properly integrated and managed. Businesses must ensure that encryption and other security tools are correctly configured and are consistently active.
Top 5 encryption software
Encryption software converts normal data into a scrambled and unreadable form that ensures its confidentiality and integrity for data at rest, in transmission, or in use. Businesses use encryption software to regulate personally identifiable information (PII), personal health information (PHI), or payment card industry (PCI) data.
To qualify for inclusion in the Encryption software list, a product must:
- Protect files and data using the ciphertext
- Encrypts either data at rest, data in transmission, or data in use
- Enables user to select and manage files their encryption settings
* Below are the five leading encryption software from G2's Summer 2021 Grid® Report. Some reviews may be edited for clarity.
1. Progress MOVEit
Progress MOVEit is a securely managed file transfer software for sensitive data that leverages its workflow automation capabilities to administer tasks. It helps companies consolidate costs and management while keeping a documented audit trail. Businesses use Progress MOVEit to meet internal and external regulatory compliance requirements.
What users like:
"Ease of use, it's much easier than other tools for the end-user. It is convenient when working with clients as they can comfortably walk through the process. We have had very little back and forth with customers' ability to use it that helps both the parties save on time. We have a broad spectrum of clients with different technical skills, so an easy-to-use tool is a must for our purposes.
Also, information security was the primary driver in choosing a tool, and MOVEit meets those requirements. In today's world, it's essential to have a security-first perspective, which resonates with MOVEit that offers an effortless way to set multiple functions like single sign-on and various others."
- Progress MOVEit Review, James H.
What users dislike:
"I have not come across anything that I do not like about the MOVEit platform. Of course, there is a greater cost component than more rudimentary scripting and file processing methods, but you get what you pay for. This product is well worth the cost."
- Progress MOVEit Review, Brandon R.
2. Microsoft Bitlocker
Microsoft Bitlocker safeguards documents and passwords by encrypting all data in a particular drive. By default, it uses an AES encryption algorithm in cipher box chaining or XTS mode with a 128-bit or 256-bit encryption key.
What users like:
"It is exciting because BitLocker has given security that excels in the way of making multiple changes of the files; it helps me to keep up with the work but with the confidence that certain items are encrypted. The interface is very intuitive and has given a lot of resolution benefits."
- Microsoft Bitlocker Review, Rachel E.
What users dislike:
"Sometimes, the encryption can affect pc performance. It might cause some old systems to slow down and lag."
- Microsoft Bitlocker Review, Akib H.
3. Kaspersky Endpoint Security
Kaspersky Endpoint Security performs full-disk encryption to prevent data leakages via the loss of a device. It also offers file-level encryption that protects files transferred in untrusted channels, and Crypto disk stores user data in an encrypted form within a separate file.
What users like:
"Kaspersky Endpoint security is a great protector for network systems. It works well as an antivirus guard. It takes immediate reactions and solves the threats. It provides encryption for many purposes like email, messaging, text documents, etc. This software provides its management service with backup, recovery, and file management with monitoring the activities to protect from unnecessary threats."
- Kaspersky Endpoint Security Review, Arandi M.
What users dislike:
"It has tricky methods of installation for some operating systems. It should also provide spam filtering features. Features for detecting threats and malware in emails can be improvised. Kaspersky Endpoint Security should update some of its encryption features. It has a complex process to renew its subscription that can be simplified, and it occasionally requires new updates."
- Kaspersky Endpoint Security Review, Victoria E.
4. Tor
Tor allows users to communicate anonymously with each other on the Internet with its second-generation onion routing. It follows multi-layered encryption, where the traffic is relayed and encrypted three times as it passes over the Tor network.
What users like:
"Tor is a best-secured browser for anonymous browsing. Its installation process is straightforward, and no need for specified requirements to run this browser. Also, it has a user-friendly interface which helps to understand the features that it has. My most favorite attribute of the Tor browser is how it changes IP addresses periodically. We can make it manual for changing browsing by location or county.
Tor Browser bypasses government blocked websites, and also it can facilitate deep and dark browsing. With multiple layers of privacy protection, we can ensure our data."
- Tor Review, Madusanka B.
What users dislike:
"The main disadvantage of the Tor browser is we can't localize websites with our current location. And also, startup time and browsing time are very high. Some plug-ins and other privacy features are difficult to understand for beginners."
- Tor Review, Tharek J.
5. FileVault
FileVault secures Mac's hard disk using XTS-AES 128 block cipher technology with a 256-bit encryption key and comes with Mac OS X 10.3 and later. Once FileVault is enabled on a Mac, all existing data will be encrypted and any new and changed data will be automatically locked down and password protected on boot to prevent unauthorized access.
What users like:
"FileVault is a highly secure encryption system for all types of files and can run on any Apple device. It's easy to use, and you can protect any file, folder, image, document, or what you want with high-level encryption. You do not need to be a genius to use it. Anyone can protect their information with this application in the simplest way, without complications. Moreover, other data protection applications are complicated, and you must be a computer professional to use it."
- FileVault Review, Ronald K S.
What users dislike:
"There are no cons to this program that I have encountered. You could say that turning off FileVault seems to take longer to process fully. However, this seems somewhat logical to happen."
- FileVault Review, Jan P.
Keep sensitive data safe
Use encryption software to transform data into an unintelligible format, not to help malicious hackers exploit it. Even though it's a complex process and can pose some challenges in implementation, it's still worth having at the forefront of your business' security plan.
Learn more about information security and its importance to protect data, avoid financial loss and reputational loss, and maintain compliance.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
