Cloud File Security Software Resources
Articles, Discussions, and Reports to expand your knowledge on Cloud File Security Software
Resource pages are designed to give you a cross-section of information we have on specific categories. You'll find articles from our experts, discussions from users like you, and reports from industry data.
Cloud File Security Software Articles
How To Tell if Your Phone Is Hacked and What To Do
If you’ve noticed your phone acting strangely–apps crashing, battery draining faster than usual, or unfamiliar pop-ups–it’s natural to wonder "is my phone hacked?"
by Holly Landis
What Is Cloud Security? Understanding the Basics of Cloud
When a business decides to move its data into the cloud, there is always the underlying question of security.
by Mara Calvello
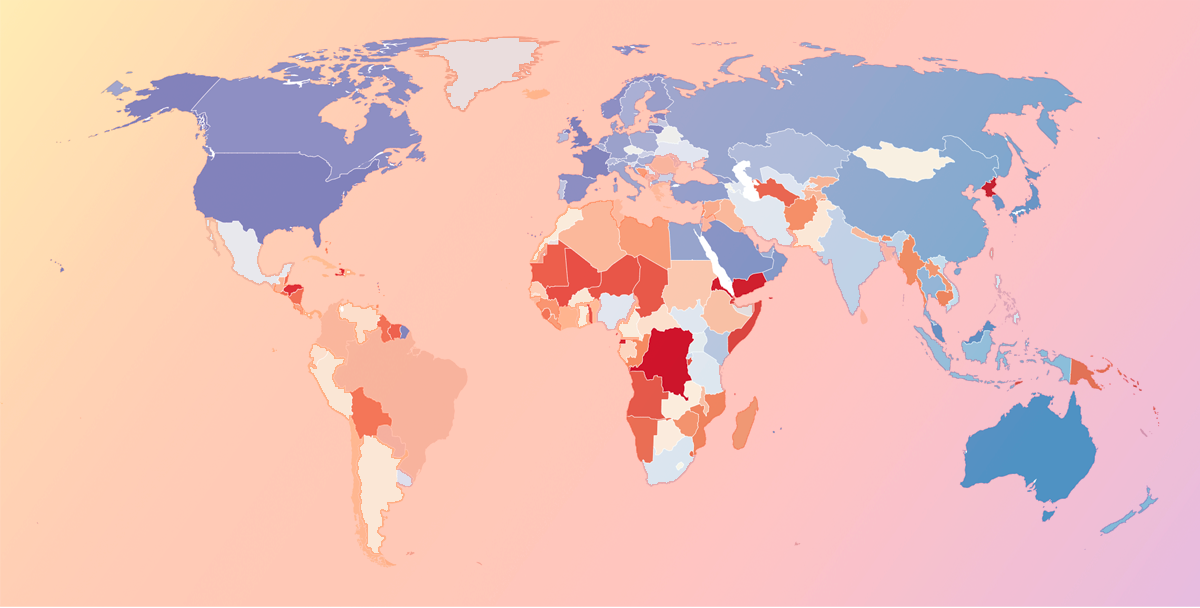
National Cybersecurity and Popular Products Across the World
In a digital age, data security is a top priority, but it can be difficult to know who exactly is responsible for securing sensitive information. While companies may feel they have sufficiently secured their own data, those that utilize SaaS vendors in their business put their sensitive information and business data in the hands of these vendors, who store it in the cloud or on-premises at their location.
There are a number of security considerations and variables a business should keep in mind, especially related to cloud security. But it's helpful to remember one simple question when considering vendors or evaluating current protection efforts: Does the country housing my data care about security?
Countries that do have taken action to protect personal and business data stored in their country or region. Other efforts to protect personal information include enforcing security standards, developing national cybersecurity strategies, and providing public awareness campaigns, among others. Countries that received lower scores have done less to ensure businesses are protecting data and require less transparency between data collectors and individuals.
In a globalized world, servers could be housed in any number of countries other than the one your business or a software vendor operates in. Still, it should be considered a potential red flag if vendors operate out of extremely vulnerable geographical regions.
Every year, the International Telecommunication Union (ITU) releases the results of a worldwide security survey titled the United Nations Global Cybersecurity Index (CGI). The index provides an overall security rating based on a number of factors related to legislative, organizational, technical, capacity building, and international cooperation.
by Aaron Walker
Cloud File Security Software Discussions
0
Question on: Microsoft Defender for Cloud Apps
What is Microsoft Defender for Cloud Apps used for?What is Microsoft Defender for Cloud Apps used for?
High level it's a CASB solution to manage shadow IT, but it has many capabilities including some DLP and posture management.
0
Question on: Avanan Cloud Email Security
What are the different types of email security?What are the different types of email security?
Email security is crucial when it comes to protecting our data privacy from cyber attacks and security breaches.
We can implement multiple layers of security enhancements to preserve our customer-sensitive information.
1. SPF implementation - Sender Policy Framework effectively enables the owners of the domain to scrutinize which servers are authorized to send emails & verify its authenticity.
2. Malware scanner utilities - It is helpful to scan our email attachments & associated links for malicious & suspicious contents to stop it from entering into our system.
3. Content Filtering Policies - They are used when we need to report or block emails containing sensitive elements & offensive contexts. Its also used to preserve our security standards and to prevent any data leakages.
Several types of email security measures that can be implemented to protect against various threats. Here are some of the most common types of email security:
Antivirus/Anti-malware: This type of security software scans incoming and outgoing emails for viruses and other malware, such as Trojan horses, spyware, and ransomware.
Spam filters: These filters are used to block unwanted and unsolicited emails, also known as spam, from reaching the inbox. They are designed to identify and block emails with suspicious content or from unknown senders.
Content filters: These filters are used to monitor email content for specific keywords or phrases that may indicate a security threat, such as credit card numbers, social security numbers, or other sensitive information.
Encryption: Email encryption is a security measure that protects the confidentiality of email messages by scrambling the content of the message so that only the intended recipient can read it.
Authentication: Email authentication is the process of verifying the identity of the sender of an email message. Common email authentication methods include SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting and Conformance).
Two-factor authentication (2FA): 2FA is an additional layer of security that requires users to provide two forms of identification to access their email account, such as a password and a security token or biometric identification.
By implementing one or more of these email security measures, businesses can help protect against a range of email-based threats, including phishing attacks, malware, spam, and data breaches.
Cloud File Security Software Reports
Mid-Market Grid® Report for Cloud File Security
Winter 2025
G2 Report: Grid® Report
Grid® Report for Cloud File Security
Winter 2025
G2 Report: Grid® Report
Enterprise Grid® Report for Cloud File Security
Winter 2025
G2 Report: Grid® Report
Momentum Grid® Report for Cloud File Security
Winter 2025
G2 Report: Momentum Grid® Report
Small-Business Grid® Report for Cloud File Security
Winter 2025
G2 Report: Grid® Report
Enterprise Grid® Report for Cloud File Security
Fall 2024
G2 Report: Grid® Report
Small-Business Grid® Report for Cloud File Security
Fall 2024
G2 Report: Grid® Report
Mid-Market Grid® Report for Cloud File Security
Fall 2024
G2 Report: Grid® Report
Grid® Report for Cloud File Security
Fall 2024
G2 Report: Grid® Report
Momentum Grid® Report for Cloud File Security
Fall 2024
G2 Report: Momentum Grid® Report