When it comes to keeping your computer and all of your files safe, there is only so much you can do on your own.
You can make sure it has a strong password and even use multi-factor authentication to log into certain programs, but these methods only go so far. To ensure maximum network security, your system needs to be utilizing a firewall to keep unwanted visitors out of your private network and away from your personal information.
Not sure what a firewall is or if one is already in use on your network? Keep reading to find out!
Firewalls defined
Before we can learn everything there is to know about firewalls, let’s first define what they are.
What is a firewall?
A firewall is a network security system that monitors and controls incoming and outgoing traffic based on preset security parameters.
For over 25 years, firewalls have been the first line of defense in network security. The actual term firewall is a metaphor that we use to compare a type of physical barrier put in place to limit the damage that a fire can cause, with a virtual barrier limiting the damage that a cyberattack can cause.

Related: Looking for a greater understanding of what’s going on in your network?Check out the best free network monitoring software, according to real user reviews.
How do firewalls work?
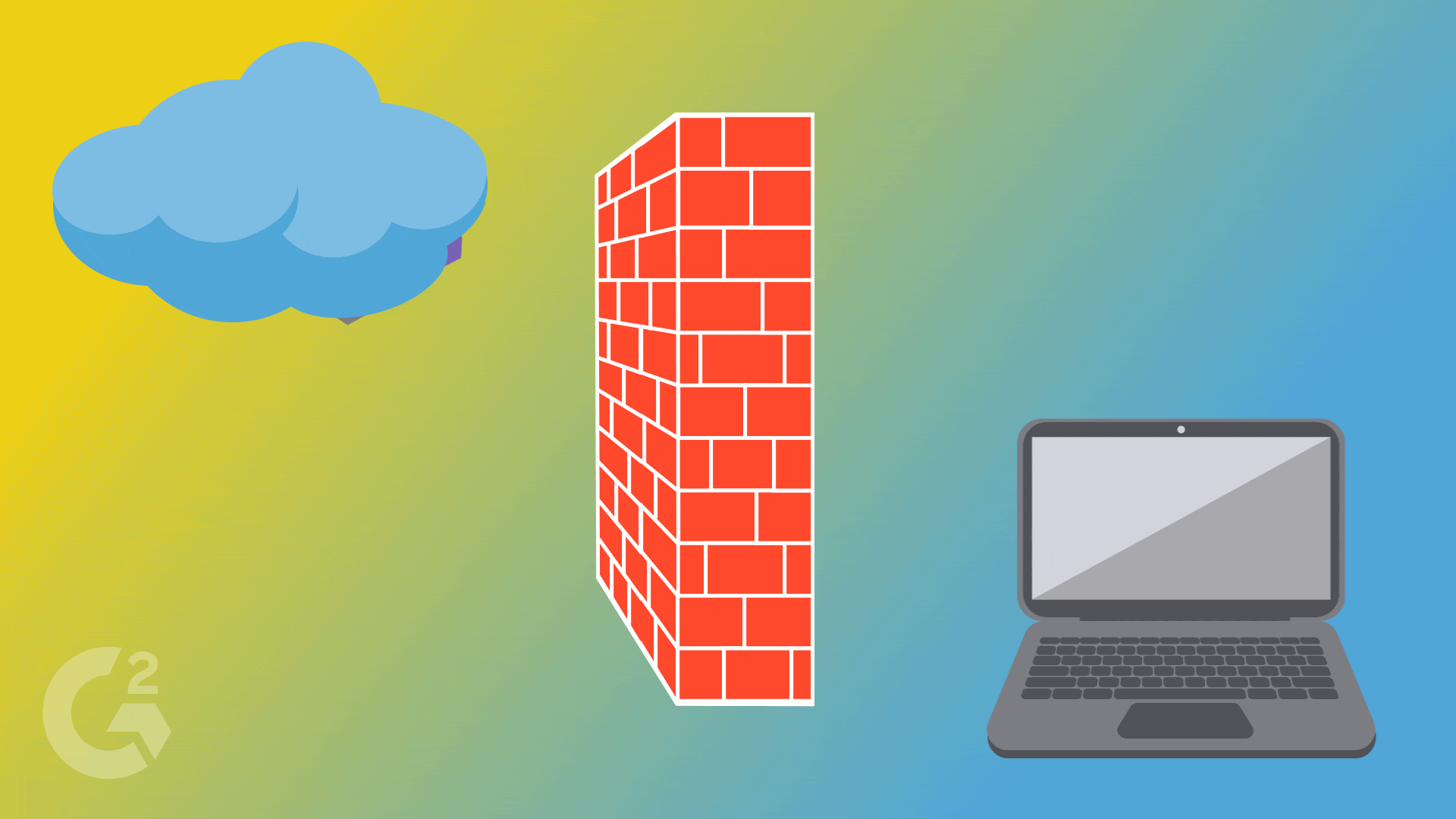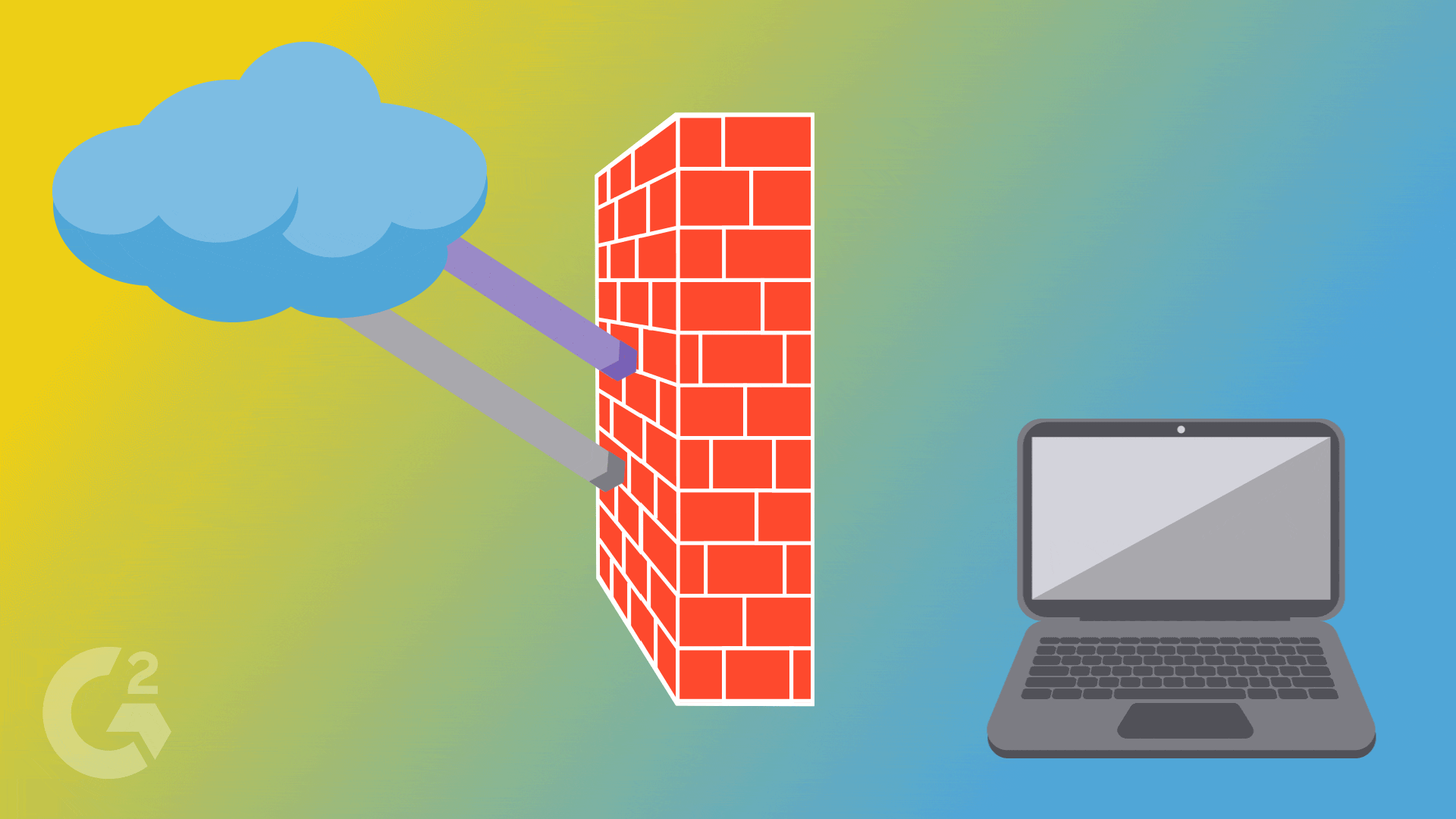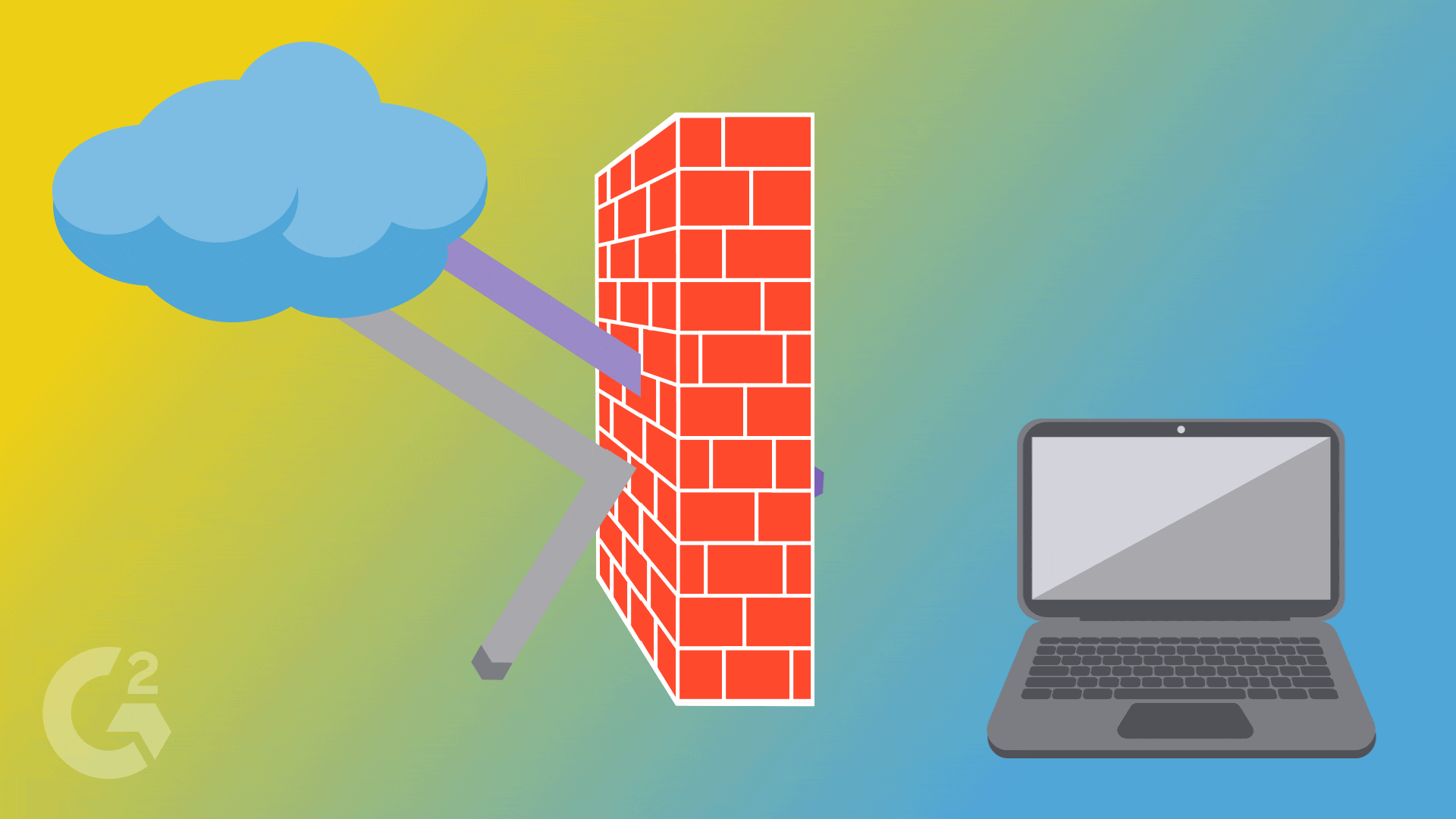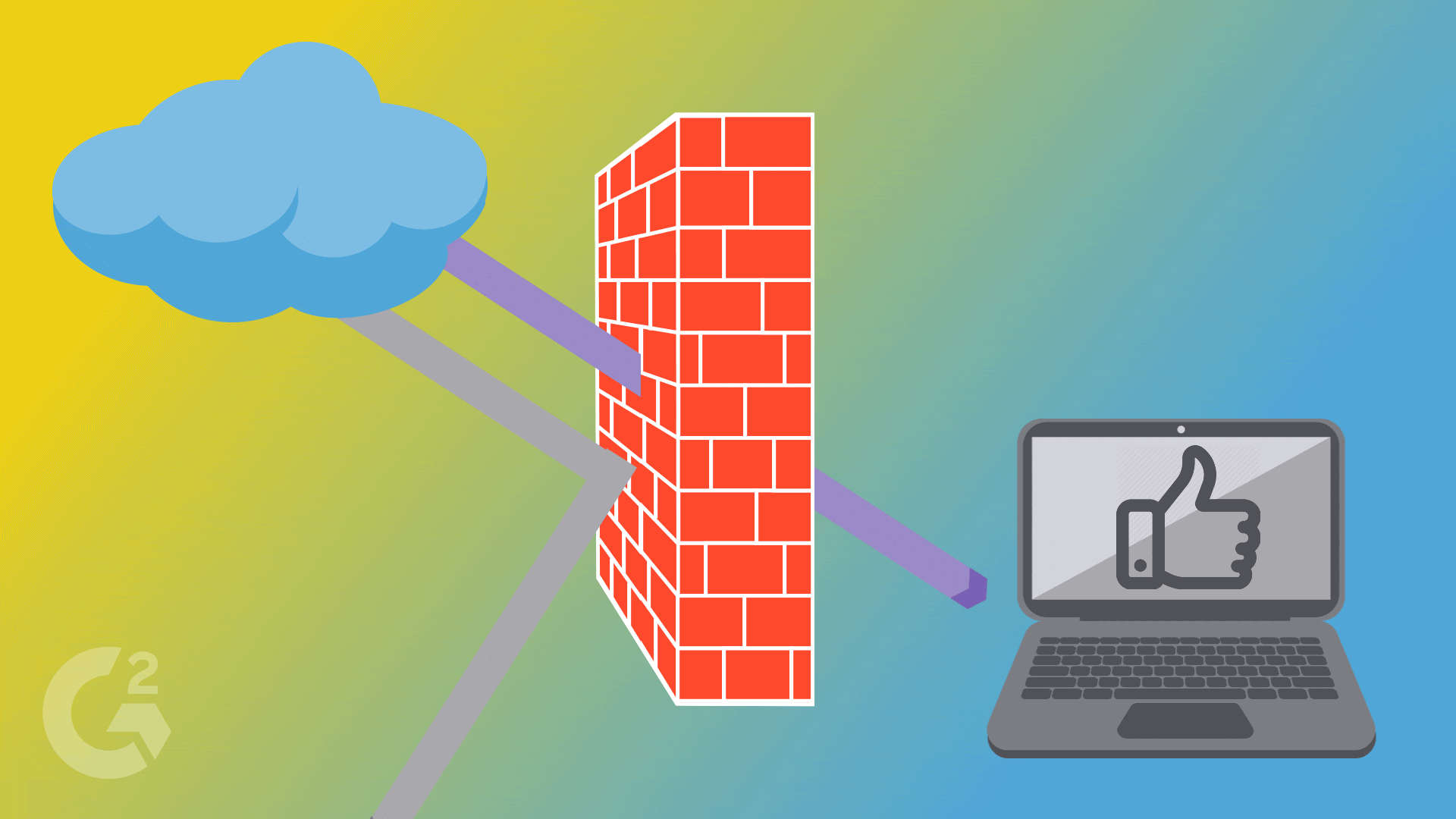
Firewalls establish a barrier between secured and controlled networks, whether they are trusted or untrusted, like the Internet. Using a wall of code, a firewall works to isolate your computer from the Internet while inspecting the data packet as it arrives on either side of the firewall. Then, it determines where it should be allowed to pass or be blocked.
Tip: A data packet is a small unit of data routed between an origin and a destination on the Internet.
The incoming traffic is analyzed based on preset rules and is carefully filtered from unsecured or malicious sources to prevent an attack.
Though they sound complex, they’re relatively easy to install and setup, depending on which firewall software you decide to use.
Related: If you aren't sure which firewall software you should be using, check out this exclusive roundup from G2!
At the very least, the firewall is responsible for checking the source and destination IP address on all packets, while filtering out packets sent from a malicious source.
Want to learn more about Firewall Software? Explore Firewall Software products.
Types of firewalls
Firewalls can either be software or hardware, depending on the type, but it’s best to utilize both. The software version of a firewall is installed onto a computer to regulate traffic through port numbers and applications. A hardware version of a firewall is a piece of equipment installed between the network and the gateway.
Related: Learn more about the differences between hardware and software!
In addition to software and hardware versions of firewalls, some types focus on varying types of cyber security.
Proxy firewall
A proxy firewall is a gateway from one network to another for a specific application. These provide additional functionality, such as content caching and enhanced security, as they prevent connections from outside the network.
Proxy firewalls filter traffic at the application as it acts as an intermediary between the two end systems. An advantage of using a proxy firewall is that any machines outside of the network being protected can collect only specific information about the network since they are never directly connected to it.
Stateful inspection firewall
Stateful inspection firewalls are often thought of as a “traditional” firewall as it allows or blocks traffic based on state, port, and protocol. These firewalls work to monitor all activity from the moment a connection is opened until it’s fully closed.
Next-generation firewall
Next-generation firewalls (NGFW) utilize traditional firewall technology and combine it with other functionality, like encrypted traffic inspection, intrusion prevention systems, cloud-delivered threat intelligence, antivirus software, and more.
These block modern threats, such as advanced malware and application-layer attacks, and can detect them within seconds, allowing a user to take action fast and avoid as much harm as possible.
Related: Interested in making a career change? Check out these 8 in-demand cyber security jobs.
Unified threat management firewall
A unified threat management (UTM) firewall combines the functions of a stateful inspection firewall with antivirus measures. These firewalls can often include cloud management since they focus on simplicity and ease of use.
Threat-focused firewall
A threat-focused firewall includes all of the features and functionality of an NGFW, while also providing advanced threat detection and mediation. These firewalls provide a user with heightened data and can better detect suspicious activity.
If a threat does occur, these firewalls can quickly react to an attack, in addition to decreasing the time from detection to cleaning up a potential mess.
Network address translation firewall
A network address translation firewall makes it possible for multiple devices, with their own network addresses, to connect to the internet using one IP address, keeping individual IP addresses hidden.
By doing so, hackers scanning a network for an IP address to hack won’t be able to capture the necessary details, which will provide greater security against these attacks.
How to enable a firewall on Mac
Using a Mac and unsure if your firewall is enabled? It’s easy to check. Once you open your System Preferences, click Security and Privacy.

From the top panel, click Firewall.
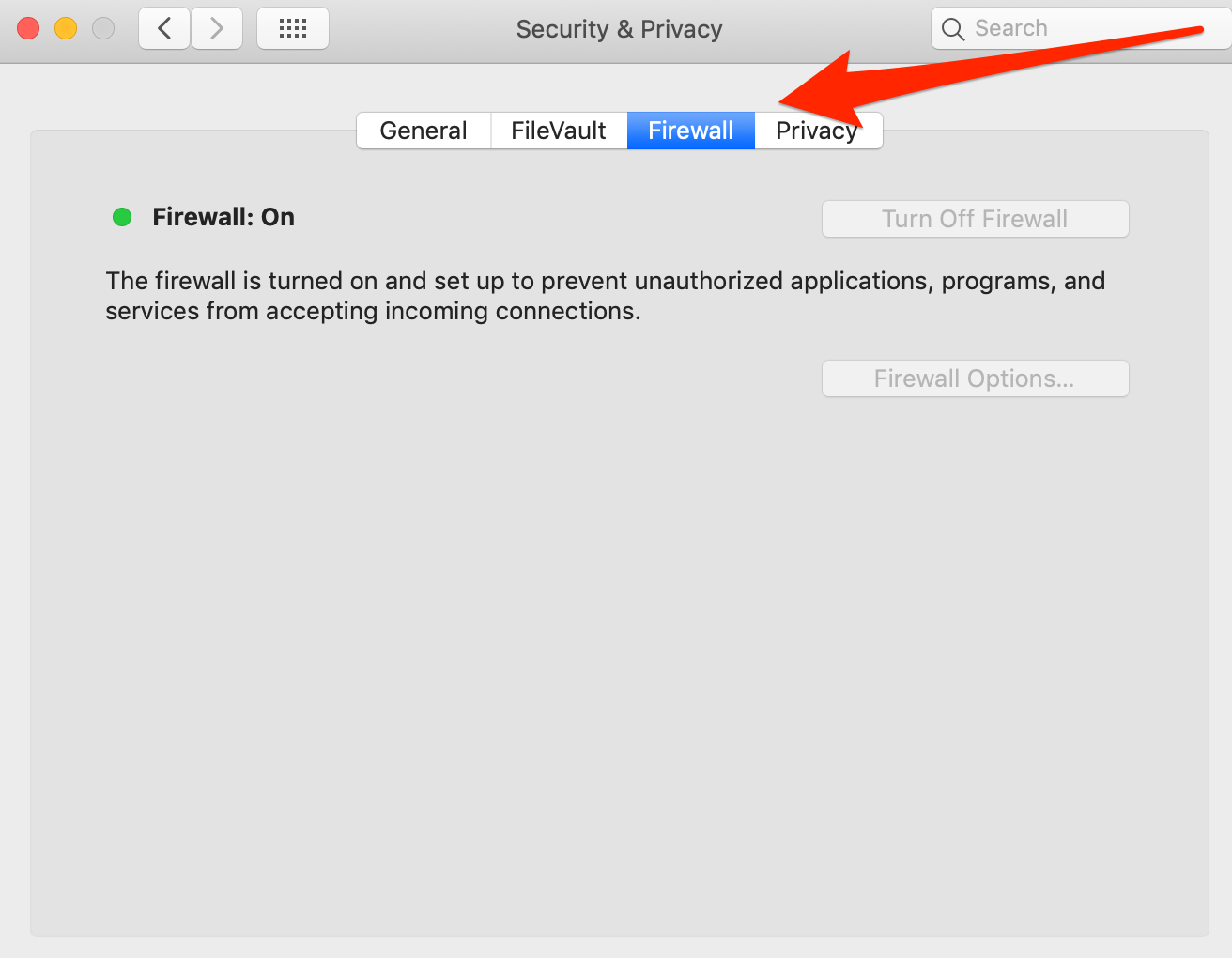
Make sure your firewall is turned on to prevent unauthorized applications, programs, and services from accepting incoming connections.
A wall you can believe in
Some walls make sense, and some don’t. One that does? A firewall to enhance your network security and stop hackers in their tracks. It’s an absolute must that you use a firewall as your first line of defense so your personal information doesn’t fall into the wrong hands.
Interested in learning more about keeping your network secure? Check out everything you need to know about SSL certificates and how to set up a VPN.

Mara Calvello
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes customer marketing content, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.
