It takes twenty years to build a reputation and a few minutes of cyber-incident to ruin it. This statement holds true today more than ever before.
Businesses are highly susceptible to cyberattacks, and a single breach can expose sensitive data, operational disruptions, and reputational damage. That's why enterprises must have a strong cybersecurity posture, and an intrusion detection system (IDS) is one of the critical tools for achieving this.
What is an intrusion detection system?
An intrusion detection system (IDS) is a security system that monitors network or system activities to identify and alert on unauthorized access, suspicious behavior, or security breaches in real time, helping protect against cyber threats.
IDS acts as an early warning system, ready to raise the alarm if it finds anything iffy in the system, just like a fire alarm acts when it detects a fire. It is often used with an intrusion prevention system (IPS) designed to actively thwart the threats thrown up by IDS.
Many businesses tap into the strength of IDS and IPS using an intrusion detection and prevention system (IDPS) to detect and proactively defend against cyberattacks.
Why are intrusion detection systems important?
Nowadays, cyber risks are skyrocketing, causing trillions of dollars of damage to businesses.
With the increasing cloud adoption and the rise of a hybrid work culture characterized by practices like "bring-your-own-device" (BYOD) and remote work, the traditional security perimeter is no longer as defined as it once was. It has created millions of attack opportunities. And when hackers see a weakness, they exploit it.
It’s evident from the increasing number of security incidents. In 2022, the global volume of cyber attacks shot up 38%. Ransomware attacks alone rose 13% in the same year, equal to the last five years combined. It’s not whether cybercriminals will attack a business but when.
Such attacks directly consume a company’s resources, leading to increased business costs. The cost includes remediation, lost revenues due to business downtime, ransom payments, and legal and audit fees. The ramifications go beyond these expenses to losing customer trust and reputation.
In this situation, as cliche as it may sound, it’s better to be safe than sorry. IDS comes as a dependable safety net at this critical juncture. It aims to identify different kinds of malware, malicious network traffic, and computer usage as early as possible and notify the security team of any attempt to hack into or disrupt a system.
By catching and flagging intrusions in the first instance, IDS identifies attack attempts on the system long before a successful attack is likely.
IDS protects a range of cyberattacks, including
- Unauthorized access
- Data breaches
- Data exfiltration
- Distributed denial-of-service (DDoS) attacks
- Malware infections
- DNS poisoning
- Malicious traffic and payloads like SQL injection and cross-site scripting (XSS)
- Insider threats
- Policy violations
Today, IDS powered by machine learning (ML) is being deployed for zero-day attack prevention, too.
Quer aprender mais sobre Soluções de Segurança para Data Center? Explore os produtos de Soluções de Segurança para Data Center.
How does an intrusion detection system work
Intrusion is when a person gains or tries to gain access to a system or system resource they are not authorized to. Once in, such intruders can do what they want until detected-steal data, cause business harm by rendering a network, system, or software application unusable, or use it as a means for further intrusions elsewhere.
Either way, the enterprise system is compromised once an intruder is in, and the consequences can be nasty if left as such.
An IDS works to detect such intrusions in the enterprise IT infrastructure by monitoring the network and activities at the endpoint for suspicious patterns. Here’s a simplified version of how it works:
- Data collection: IDS collects data like network traffic from routers, firewalls, and individual system logs from endpoints like servers and workstations.
-
Data analysis: It then analyzes the collected data using different methods like predefined rules, signature-based analysis, and anomaly detection algorithms.
For network data, it compares the collected data against the baseline of normal network behavior and raises alerts when there are deviations from the baseline. Similarly, it tracks changes to settings, critical system configuration, and files in the individual system logs for unauthorized changes. Many IDSs allow security operations center (SOC) analysts to customize and set the baselines for network traffic and system activities via intrusion detection policy. -
Alert generation: If the analysis identifies suspicious or unauthorized activity that violates user-defined rules or default thresholds, IDS logs it as an intrusion event and sends a notification via message or email.
Most IDSs keep records of intrusion events in their dashboards or in a security information and event management (SIEM) tool they are integrated with. - Response and mitigation: Once alerted, system administrators analyze the intrusion events to determine which security actions to take. Some IDSs have denial mechanisms like filtering packets, variable dynamic throttling, disconnecting compromised servers, etc.
For instance, you have a network traffic regulation policy to notify you if the number of transmission control protocol (TCP) connections goes beyond 10% of the total connections to your system in a short time interval. When IDS detects that TCP connections exceed the set threshold, it alerts you with email and message notifications.
Since such an unusual connection request points to a possible DDoS attack, you can throttle the incoming traffic for a specific period and contain it. Once the incident ends, you can analyze the logs to identify where the unusual traffic originated.
Today, there are even cloud-native IDS software to monitor both on-premises and cloud assets as part of cloud security strategy.
Two major intrusion detection methods in IDS
From the working of IDS, it becomes evident that the detection methods employed in IDS play a pivotal role in identifying suspicious activities. Let's now explore the two major intrusion detection methods.
1. Signature-based detection
Signature detection relies on predefined signatures or patterns of known attacks, including viruses, worms, Trojans, and specific attack techniques. It compares network traffic or system behavior against a database of known attack signatures and triggers an alert if there’s a match.
While the signature-based detection method is effective against known threats, it’s ineffective against zero-day vulnerabilities and novel attack techniques.
2. Anomaly-based detection
Also known as behavior-based detection, the anomaly detection technique focuses on identifying deviations from established normal systems or network behavior baselines. The system builds a normal behavior profile by monitoring network activity, system processes, user activities, or other relevant parameters over time. If there’s a significant deviation from the baseline, it triggers an alert.
Anomaly-based detection methods, supported by ML, can be quite effective against zero-day attacks and emerging and new threats. However, it can throw false positives often.
Most IDS and IDPS systems take a hybrid approach called the hybrid intrusion detection method. This method combines signature and anomaly-based methods to detect a broader range of security threats while minimizing error rates.
Five types of intrusion detection system
Based on where they’re placed in a system and what kind of activity they monitor, IDSs are classified into five major types:
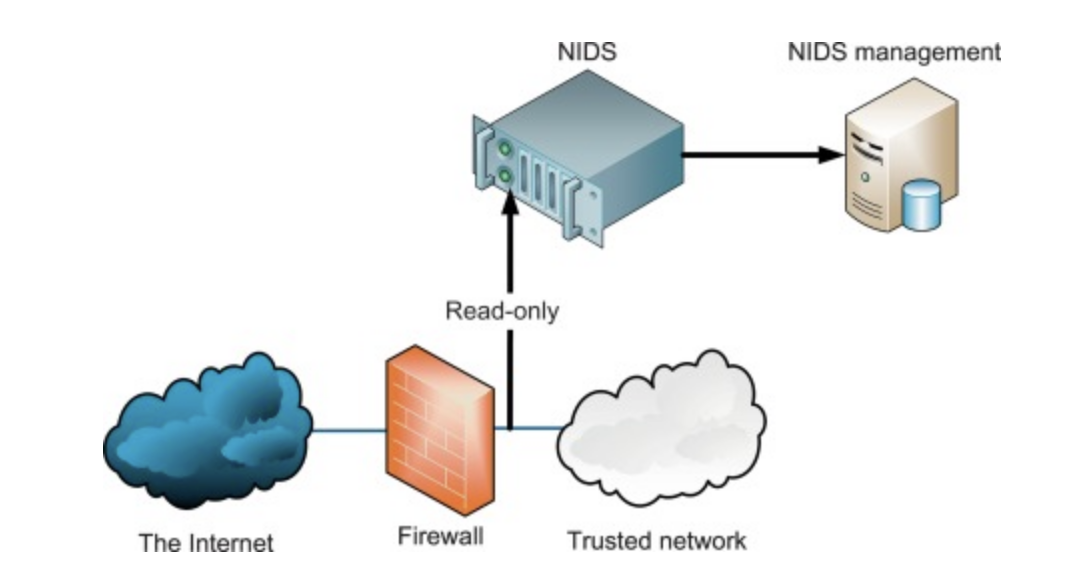
1. Network-based intrusion detection system (NIDS)
NIDS is deployed at strategic points to examine network traffic and packets to and from all devices to find abnormal behaviors, be it on-premises in a data center or the cloud. It is placed “out-of-band,” i.e., traffic doesn’t pass directly through it. Instead, a copy of network packets is sent to it for analysis so that the inspection doesn’t affect legitimate traffic.
Is NIDS a firewall?
NIDS is not a firewall. A firewall actively monitors and filters network traffic. NIDS, on the other hand, passively monitors traffic and alerts if there’s any suspicion of harmful entry.
NIDS is particularly useful because it detects an intrusion before it reaches the internal systems. It has two major variations based on whether the tool uses signature-based and anomaly-based detection methods.
Source: ScienceDirect
2. Host-based intrusion detection system (HIDS)
Like data center security solutions protect servers and endpoints in a data center, HIDS protects servers and endpoints in the entire IT infrastructure. It is installed on individual devices and servers to catch any compromised systems.
HIDS scans activities on the individual device and oversees changes to critical operating system files and system processes. If it notices anything abnormal, like repeated failed login attempts, changes to the system Registry, or installation of a backdoor, it tips off security administrators.
Simple consumer versions of HIDS monitor individual systems, and complex enterprise versions allow for centralized monitoring and management of network systems.
Source: GeeksforGeeks
3. Protocol-based intrusion detection system (PIDS)
PIDS is deployed in web servers to monitor the protocols used to connect devices to the web servers. Typically, PIDS checks on the most commonly used hypertext transfer protocol (HTTP) and HTTPS connections to catch protocol-level anomalies.
4. Application protocol-based intrusion detection system (APIDS)
APIDS is a specific IDS placed between the web server and the database management system of web applications. It monitors connections to structured query language (SQL) databases for threats like SQL injections.
Note that APIDS and PIDS cannot work as a standalone solution to find all intrusions and act complementary to NIDS and HIDS.
5. Hybrid intrusion detection system
Like the hybrid intrusion detection method, this system combines two or more types of IDS to create a comprehensive solution. It improves the overall effectiveness and accuracy of IDS.
Benefits of IDS
Deploying IDS offers several benefits to security teams, network administrators, and organizations to respond effectively to cyber threats, minimize risks, and maintain the integrity of their IT infrastructure. It helps:
- Identify security threats and attacks in real time, allowing for swift incident response.
- Minimize network or system downtime and associated financial losses.
- Collect valuable data for post-incident forensics, helping organizations understand how an attack occurred.
- Meet regulatory and compliance requirements by monitoring and reporting on security events.
- Strengthen the overall security posture of an organization.
Challenges of IDS
While effective in detecting potential threats, IDS is not without its limitations. Here are some common challenges associated with IDS:
- False positives and false negatives: IDS solutions are prone to generate false positives, i.e., alerts triggered for benign network traffic. The false alarms lead to unnecessary investigation. On the other hand, false negatives occur when an IDS fails to detect an actual security breach, potentially leaving the entire network vulnerable.
- Lack of context: IDS may generate alerts without detailed information about the motive or potential consequences due to a lack of understanding of the intent and impact of detected events.
- Limitations of signature-based detection: As mentioned before, signature-based IDS struggle to identify new and evolving threats as they won’t have the signature patterns in their database.
- Evasion techniques: Hackers using advanced evasion techniques like DNS spoofing, encryption, and decoy threats on purpose to distract the security team is one of the major challenges of IDS. Such false alarms can cause operator fatigue and divert security teams from actual attacks.
Some of these challenges, like false alarms, can be overcome by fine-tuning the security and IDS policies to suit the organization’s needs on when it needs to be alerted. However, it takes time and effort to get it right.
IDS vs. IPS: What’s the difference, and which one do you need?
Often, security teams wrangle their mind on whether they need IDS or IPS as part of their security architecture. Understand the distinctions between them to make informed decisions on what you need.
IDS is deployed to passively monitor the network and system to detect and alert about intrusions. The security teams need to investigate the alert and decide if it requires further action.
IPS is deployed in line to actively prevent intrusion by taking immediate action against any suspicious activity. It goes a step ahead of IDS as it actively mitigates threats.
Here are their key differences in terms of purpose, functionality, and their impact on network infrastructure.
| Intrusion detection system (IDS) | Intrusion prevention system (IPS) | |
| Purpose | Monitor network and system for security incidents and unauthorized access attempts. | Monitor network and system for security incidents and unauthorized access attempts, but also take immediate action to block or mitigate identified threats. |
| Functionality | Passive monitoring. Generates alerts or notifications when malicious activity is detected. | Active monitoring. Takes immediate action, like shutting down systems, blocking traffic, or dropping connections in real time. |
| Impact on network performance | Minimal impact on network performance since it operates in a passive mode. | Has a higher impact on network performance due to the active blocking and threat mitigation. |
IDS and IPS can be deployed as a standalone solution or as part of a larger security framework.
If your primary goal is to get network visibility and monitor network traffic, then IDS is suitable. But, if your security requirement is immediate threat mitigation, IPS is the best option. Also, if your business supports critical infrastructure like financial systems and operates in sectors with strict security requirements, it's better to go with IPS.
Most organizations, however, implement both solutions using IDPS in a layered security approach since it provides more comprehensive network and system protection. Let’s explore a bit more about IDPS.
IDPS: The all-in-one solution
While firewalls and other security solutions provide the foundation for network and system security, IDPS is the additional line of defense that takes care of threats that slip past preliminary defense.
IDPS informs IT administrators and security staff of anomalies and attacks on IT infrastructure and provides preemptive intrusion prevention capabilities.
A quick checklist of features to consider when selecting IDPS software
Based on G2 data, our users focus on the following popular features when picking an IDPS tool:
- Incident alerts
- Workload protection
- Activity monitoring
- Automation
The most common industries using IDPS software based on the summary of reviews on G2 are information technology and services, the computer and network security industry, computer software services and financial services, and banking.
Top 5 intrusion detection and prevention (IDPS) systems
- Trend Micro Hybrid Cloud Security
- Trend Micro TippingPoint
- ExtraHop
- AlienVault USM (from AT&T Cybersecurity)
-
Palo Alto VM-Series
*Above are the top five leading IDPS software from G2’s Fall 2023 Grid® Report.
Detect and defeat
IDS is a must-have for network and IT infrastructure security in the age of rising cyber threats. It empowers security teams and network and system administrators to strengthen the organization’s security posture and safeguard critical digital assets.
Let IDS be your sentinel and gain the upper hand in the ongoing battle against cybercriminals.
Now that you have been alerted about IDS, explore our in-depth guide on incident response to ensure you're prepared to combat threats effectively.

Soundarya Jayaraman
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.