Whether you are a hospital, private clinic, ancillary health care services provider, or health-related business, as long as you handle medical and patient data, you must adhere to HIPAA guidelines.
Compliance and regulatory adherence is unavoidable, especially in the age of telemedicine and effective, consumer-facing health applications. Those guidelines set the standards that affect the types of software and devices that are used by medical staff, who on those devices to provide medical care as well as store sensitive patient information. These professionals rely on software (like EHRs and data backup) to keep those records safe.
What is HIPAA compliance?
HIPAA (Health Insurance Portability and Accountability Act) is a piece of enacted U.S. legislation that protects health data. HIPAA sets standards for data privacy, including security provisions that determine when, between whom, and what types of medical information can be shared.
Health care compliance software facilitates the deployment, implementation, training and monitoring necessary to follow relevant policies and procedures. Being HIPAA-compliant means that a health care organization should be able to provide documentation that it has implemented all of the rules that HIPAA has defined. This applies to software vendors as well; if a vendor has created a HIPAA-compliant solution, then that solution must be able to support those rules. HIPAA’s rules standardize the transmission and storage of patient data and other forms of protected health information (PHI).
When it comes down to it, maintaining HIPAA compliance helps hospitals, practices, ancillary care providers and other health care businesses provide better patient care, ensure patient safety, improve their reputation, and minimize and reduce unnecessary financial outcomes.
What makes HIPAA compliance so difficult?
The consequences of failing to deploy and maintain effective HIPAA compliance measures have been made very clear in the past few years. Semi-related is also the issue of hospitals and medical offices using outdated technology and solutions that make it difficult to comply with health care compliance as a whole.
Data breaches that expose patients’ health information en masse, and ransomware attacks that seriously jeopardize health care organizations’ ability to provide services, are two of the most recent examples of outdated technology causing issues. Putting aside the monetary damage that failure to comply brings to a health care organization, the impact that these events have on its reputation is even more concerning.
Don’t think that your organization needs to comply with HIPAA? Four types of health care businesses must be aware of and adhere to HIPAA regulation: health plans, health care clearinghouses, health care providers, and business associates. (Failure to realize that your business is noncompliant or that such regulation even exists can no longer be used as a reasonable defense should your business be fined.)
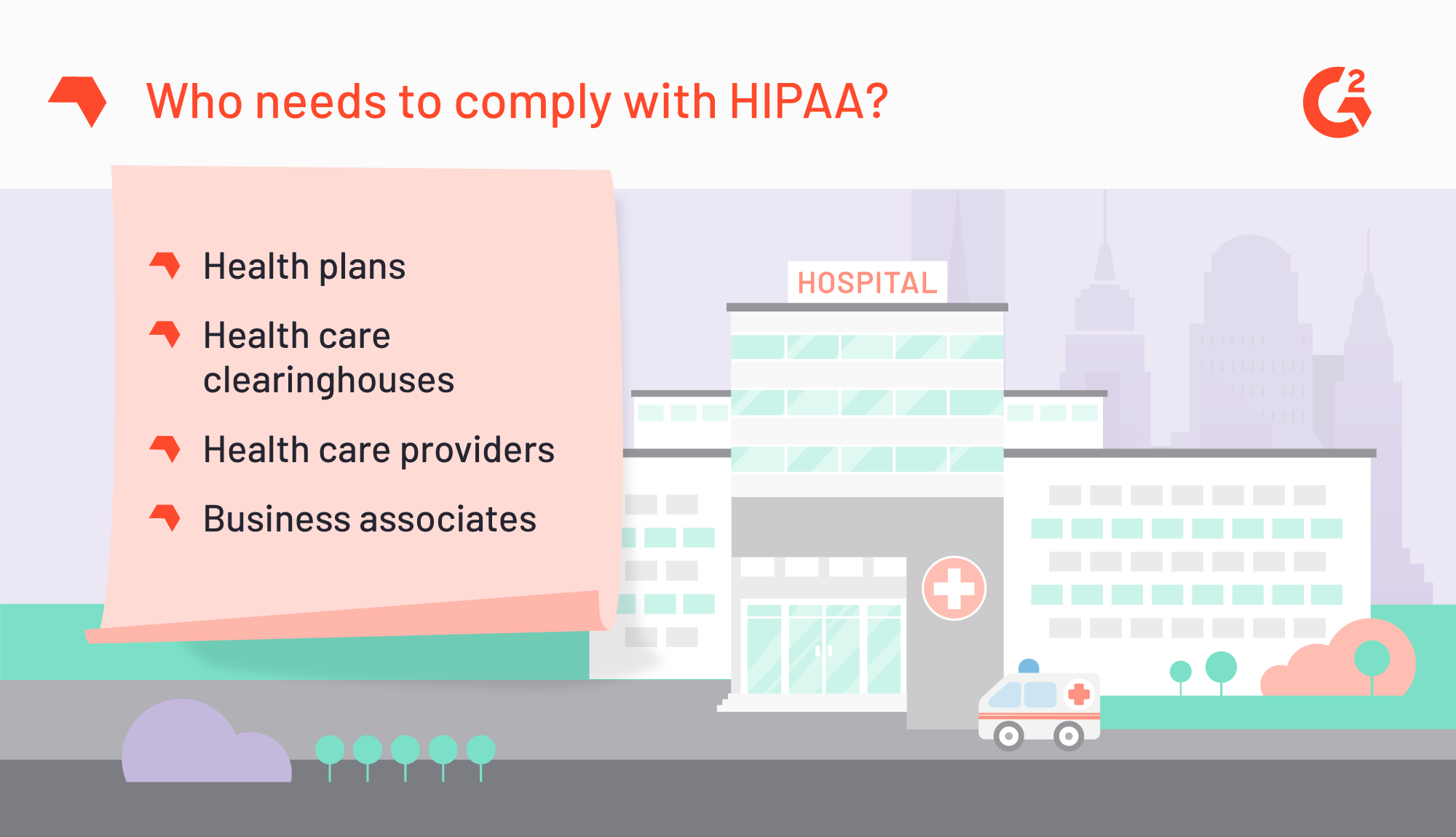
Any company that falls within those four types regularly collects, processes, and stores patient medical and financial data. Already overwhelmed with massive amounts of data, any one of those businesses can inadvertently compromise patient data or the health care network without the help of a HIPAA-specific compliance software or consulting agency.
However, just because a health care organization or business has decided to take serious strides toward HIPAA compliance doesn’t mean it’s an easy process. And so, we have compiled a checklist that you can use to transform your organization into one that’s deliberately and resolutely compliant.
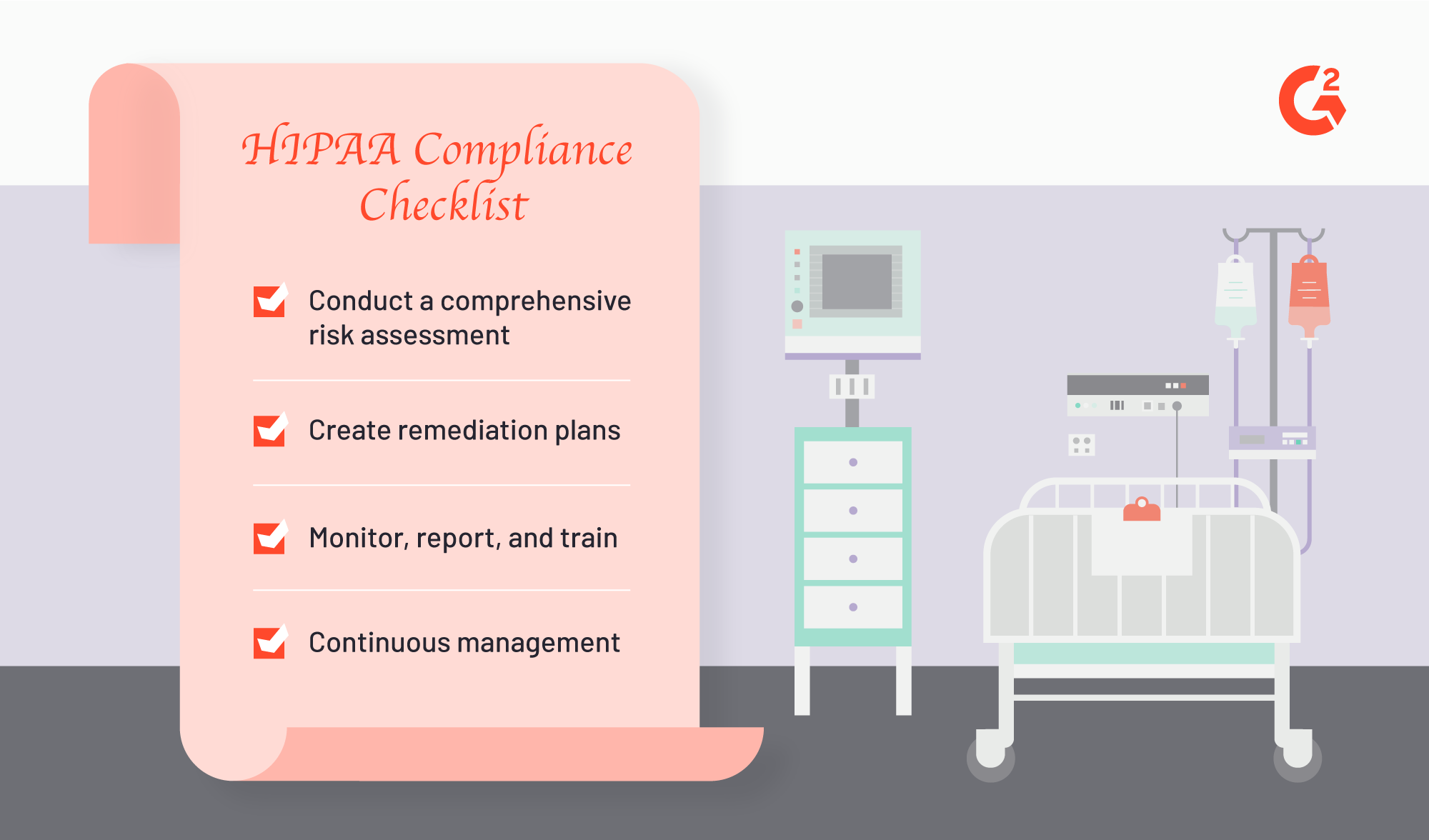
HIPAA Compliance Checklist
There are four components of this checklist:
- Conduct a comprehensive risk assessment of your organization — First things first, you must understand how HIPAA applies to your specific practice, facility or business. You do this by conducting a risk assessment to understand weaknesses, potential vulnerabilities and any gaps in existing measures. You can conduct regular self-audits or you can hire a consulting agency to audit your organization. The end goal is to identify which elements of HIPAA you are at risk of noncompliance.
- Remediation — Once you have identified the gaps and risks in compliance, you must create plans to make sure those issues are addressed. Something of note: Remediation plans cannot be generic. The plans must be tailored to the different HIPAA rules that exist; policies and procedures vary whether you’re adhering to the HIPAA Privacy Rule, the HIPAA Security Rule or the HIPAA Breach Notification Rule. (We will discuss those different rules and safeguards further down below.)
- Monitor, report and train — HIPAA compliance solutions offer automated compliance reporting, which is helpful for tasks like identifying, tracking, investigating and reporting incidents. The different HIPAA rules require either administrative, physical or technical safeguards, all of which are made much easier with tools that automate the monitoring and reporting responsibilities. Additionally, health care compliance of any kind is effective only if every single staff member and employee participates. Training is crucial and essential for ensuring that your hard-prepped compliance efforts are maintained.
- Continuous management — Documentation is necessary to prove your organization is keeping up with compliance efforts. Organizations like the Centers for Medicare & Medicaid Services (CMS), the ONC (Office of the National Coordinator for Health Information Technology), and the HHS (U.S. Department of Health and Human Services) regularly audit health care providers and business associates to make sure they remain in compliance, year after year. In addition, continually managing and evaluating risk will help keep your safeguards in tip-top shape.
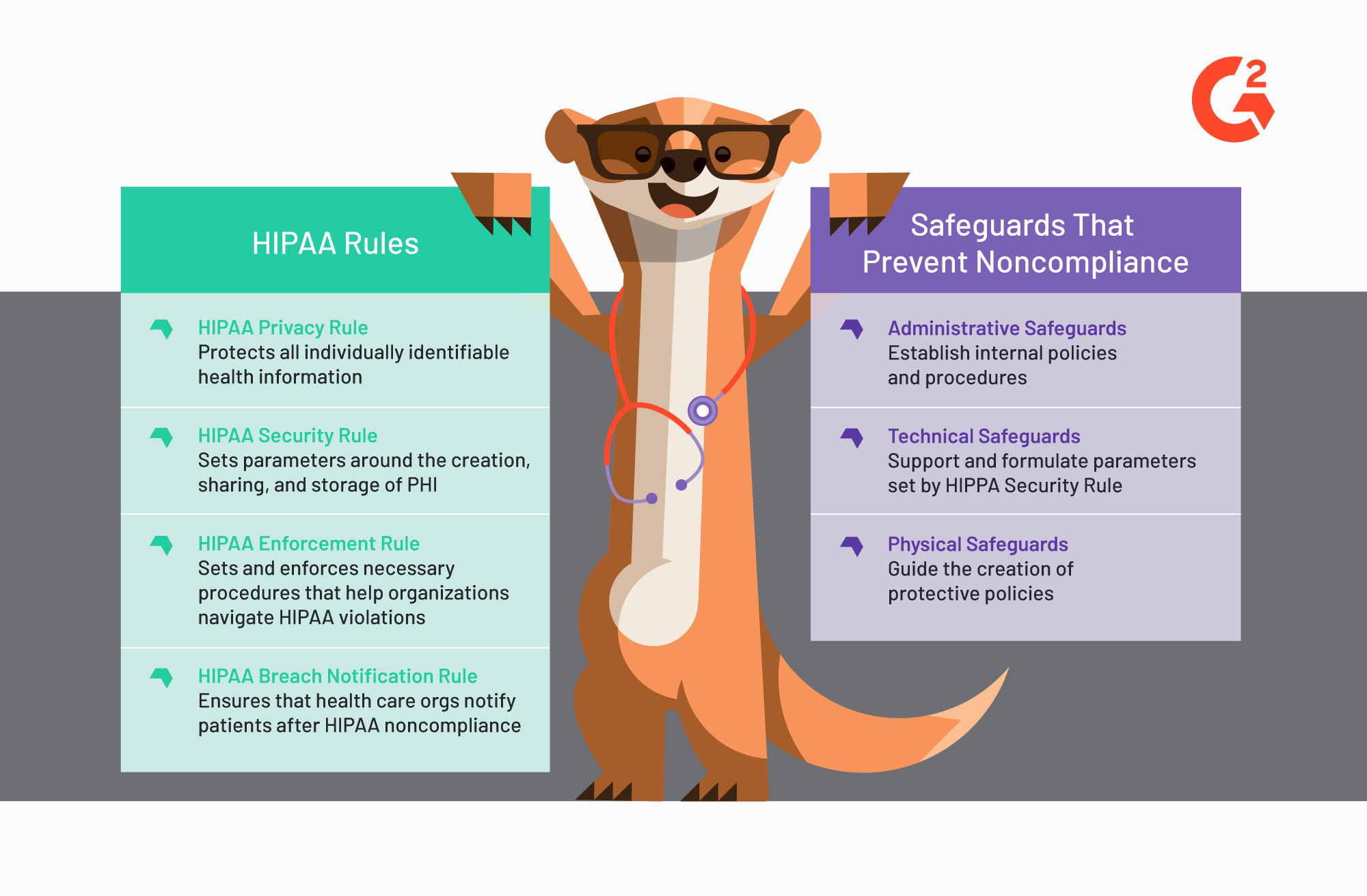
Rules to follow (always)
There are four rules of HIPAA that health care organizations follow, regardless of business type. The Privacy and Security Rules are to be complied with at all times. They come with three safeguards. The Enforcement and Breach Notification Rules establish frameworks post-incidents.
- HIPAA Privacy Rule — The Privacy Rule protects all individually identifiable health information that is shared with or stored by organizations or businesses. The Privacy Rule safeguards protected health information (PHI), both electronically (ePHI) and paper-based, as well as gives patients rights over the access and sharing of their own personal health information. The types of organizations that take extra care of the Privacy Rule are: health care providers, health care insurance clearinghouses, and any business that leverages patient data.
- HIPAA Security Rule — The Security Rule protects individuals’ ePHI; the rule specifically sets parameters around the creation, sharing and storage of such health information. Maintaining confidentiality while also regulating access to that data are crucial aspects that the Security Rule makes sure health care organizations have. The Security Rule helps organizations identify security gaps that can then be addressed via various safeguards tailored to the differing standards of the organizations.
Safeguards
Safeguards exist to prevent the unauthorized or illegal sharing of PHI, regardless of whether that sharing was done intentionally or unintentionally. Ultimately, these safeguards exist to protect patient information, but they are also meant to protect the health care organization from compromising their compliance efforts.
- Administrative safeguards — Administrative safeguards help establish internal policies and procedures via security management processes, security awareness training, and contingency planning. Medical staff and employees should be able to refer to those policies so they reduce any inadvertent violations of patient confidentiality. Documentation is key to implementing effective administrative safeguards; so is easy access of that documentation by employees.
- Technical safeguards — Technical safeguards help formulate the HIPAA Security Rule via access control, audit control and entity authentication. With technical safeguards, health care organizations can ensure the security and integrity of ePHIs. Additionally, technical safeguards monitor user access to ePHI storage systems.
- Physical safeguards — Physical safeguards like controls ordering facility access and device and media usage help guide the creation of the policies that protect the electronic systems that house ePHIs. With physical safeguards, both health care facility and employees can understand and prevent potential threats and unauthorized actions that will jeopardize the maintenance of patient confidentiality.
Rules to follow post-incident
- HIPAA Enforcement Rule — The Enforcement Rule sets and enforces the procedures that must be followed once a possible HIPAA violation is determined. The Enforcement Rule provides the procedures that help health care organizations navigate the fines and penalties that may befall them should that violation require consequence post-investigation. The Enforcement Rule is only set in motion once the Health and Human Services department decides to investigate your organization.
- HIPAA Breach Notification Rule — The Breach Notification Rule makes sure that health care organizations notify patients after PHIs are compromised. A PHI breach should only happen if your organization is in noncompliance of the HIPAA Privacy Rule, e.g., you have failed to secure your patients’ information.
Equipping your health care facility with the tools and resources to maintain HIPAA compliance is a difficult but necessary measure. Employing solutions like HIPAA-compliant messaging systems can protect the hospital or medical practice from accidentally opening themselves up to liability when all they’re doing is emailing their patient confirmation about an upcoming appointment. Organizations must consider the pros and cons of maintaining patient security and confidentiality versus keeping up with technology that empowers patients to have regular access to their own health care information. With mobile apps like Apple Health Records and diabetes managers or glucose trackers creating what is essentially new EHR and medical technology, the line between sharing and providing access to patient health data, versus adhering to medical release laws, has become blurred.
Quer aprender mais sobre Software de Credenciamento de Cuidados de Saúde? Explore os produtos de Credenciamento em Cuidados de Saúde.
How to meet HIPAA compliance
So now that you know the different components that go into HIPAA compliance, how do you go about meeting it?
Here are four rules that will help you create and check-off a HIPAA compliance checklist:
- Standardize clinical documentation and communication — Coding is crucial for medical professionals to document and transmit patient notes. Specific code sets exist to streamline charting, unify health care communication, and encode transmissions. Some common examples of medical codes include: NDC (National Drug Codes) for drug identification and distribution; ICD-10-CM (International Classification of Diseases, Tenth Revision, Clinical Modification) for symptoms diagnosing; and HCPCS (Healthcare Common Procedure Coding System/CPT (Current Procedural Terminology) for medical billing. Most EHRs automate encoding formatting. Make sure that your facility is up to speed in coding best practices.
- NPI registration — NPI (National Provider Identifier) is a 10-digit number used by health plans, health care providers, and health care clearinghouses to verify and validate financial transactions. HIPAA mandates the usage of unique NPIs when transmitting health care data, so your practice must get and use NPIs to differentiate itself from other similarly named practitioners.
- Patient privacy best practices — Develop privacy procedures for your facility, and designate either a point person to keep an eye on their implementation or create an easily accessible database of those policies. Maintain a record of your facility’s PHI, particularly the authorized use and disclosure PHI scenarios, and make sure that your organization requires both continuous training on those privacy procedures and regular risk assessments on the integrity of your security safeguards.
- Contingency planning — Your health care organization should be prepared to deal with any incidents or breaches that violate HIPAA. Regardless of whether your practice actually violates HIPAA, it’s best to establish procedures that align with the HIPAA Enforcement and Breach Notification Rules. The more prepared your organization is, the more equipped it will be when it comes to investigations.
Last things of note
- Have you distributed documented compliance policies and procedures to all medical staff?
- Has every staff member gone through HIPAA compliance training? Is such training material easily accessible for future reference?
- Have you identified all unique variables that must still be in compliance with HIPAA?
- What system do you have in place to handle data breaches and security incidents?
Keep in mind that HIPAA compliance software does exist. HIPAA compliance software equips users with the ability to run audits and risk assessments so that organizations can effectively plan, disseminate and maintain remediation plans via policies, procedures, and necessary employee training.
Most effective HIPAA compliance solutions provide ongoing breach or incident management modules, which helps the tracking, documenting and reporting of any data or IT breaches. Additionally, HIPAA compliance consulting groups exist to lift the assessment and training burden off of your administrators’ shoulders, allowing your facility to leverage the experience and knowledge base of HIPAA experts.
|
Check out the Healthcare Compliance category on G2 for a listing of solutions designed to track, identify, and mitigate risk in any health care organization.
|

Jasmine Lee
Jasmine is a former Senior Market Research Analyst at G2. Prior to G2, she worked in the nonprofit sector and contributed to a handful of online entertainment and pop culture publications.
