Not a day goes by without news of another organization getting hit by cyber security threats. It could be your favorite brand going through a data breach. It could be a multinational corporation falling victim to a crippling ransomware attack. It could even be your slightly reckless co-worker opening a suspicious email from our old friend, the Nigerian prince, asking for some money.
These cyber threats are everywhere. They are invisible and silent, but very dangerous. Their impact on people, businesses, and governments is devastating, and they're only getting more sophisticated by the day.
You have to understand the basics of cyber threats to know how to protect yourself and your organization.
What is a cyber threat?
A cyber security threat is any malicious attempt or act that can harm your computer or network, steal information, or disrupt operations. The threats range from simple viruses, malware, and phishing attacks to complex ransomware and supply chain attacks.
Organizations that take cyber threats seriously have a multi-layered security stack to protect their network, data, and operations. They employ network security software, endpoint protection tools, cloud security solutions, and internet of things (IoT) security systems for a robust defense.
To figure out what you should prioritize for your organization’s cyber security, let’s look deeper into the emerging cyber threat landscape. We’ll explore the source, the most common threats, and the emerging ones you should prepare for.
Sources of cyber threats
Today, threat actors with different motivations, skill levels, and methods cause cyber security incidents. The following are the most common sources of cyber threats.
Cybercriminals
Hackers, both individuals and in groups, commit cyber crimes for economic benefit. They resort to malware, ransomware, and phishing scams to extort money or steal private or sensitive information from people and companies.
Casino operator Caesars paid millions of dollars in ransom to cybercrime group Roasted 0ktapus after the hackers managed to infiltrate and disrupt the venue’s systems in September 2023.
According to PWC, hackers and organized crime groups pose the biggest external threats, committing 60% of external frauds against companies.
Nation-states
Nation-states and governments launch cyber attacks by funding hackers and threat groups to further their national interests. The state-sponsored hackers steal sensitive data, gather confidential information, or disrupt another government’s critical infrastructure. Since the groups are well-paid, their operations are often some of the advanced cyber threats.
Since the start of the Ukraine-Russian war, Russian-backed hackers have targeted Ukraine’s critical digital infrastructure.
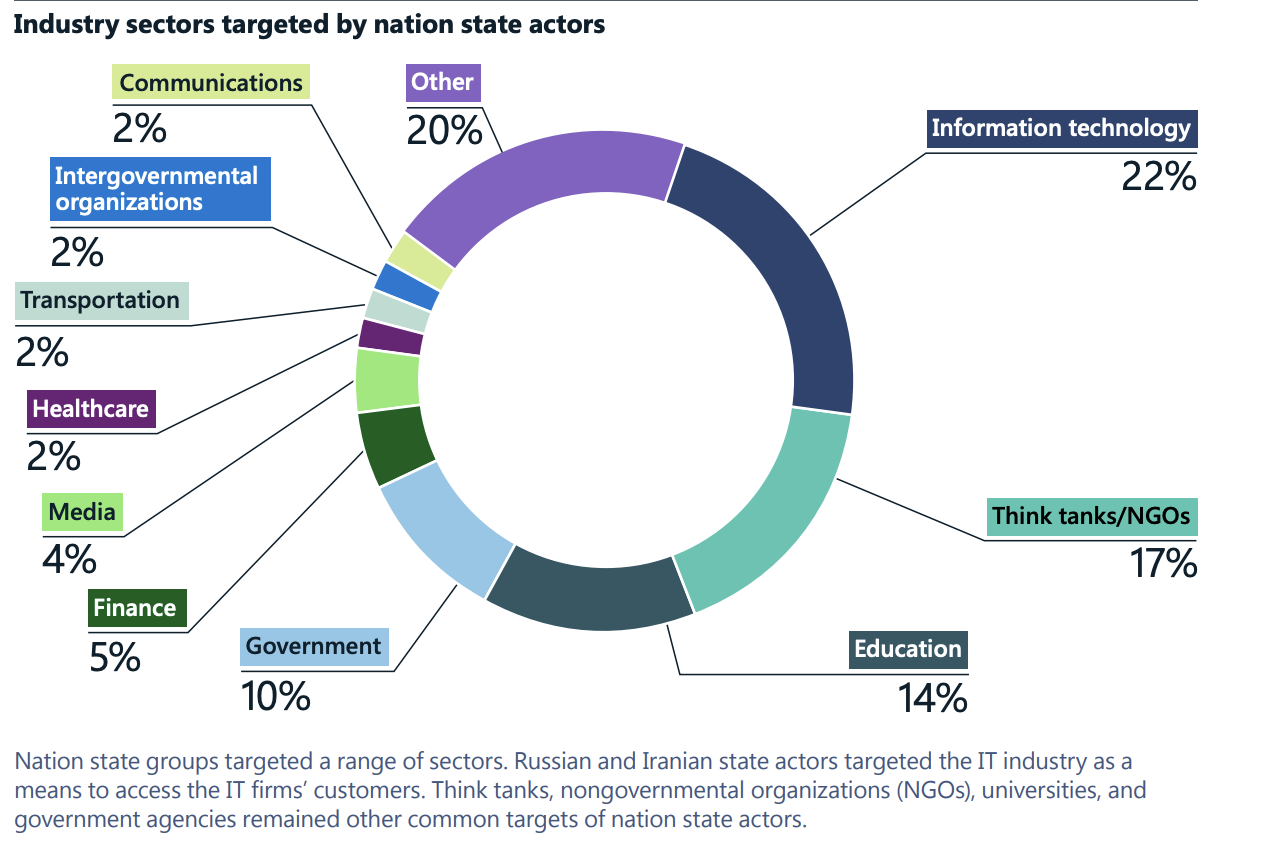
Source: Microsoft Digital Defense Report 2022
Hacktivists
Hacktivists are private citizens who use cyber threats for political or social goals, like uncovering human rights violations or spreading free speech. They use their skills to hack individuals, organizations, or government agencies who stand against their morals. Once the hacktivists get into the proper network, they steal and leak sensitive information or disrupt operations.
Anonymous is a popular hacking collective that has organized some of the biggest cyber-attacks in the early 2010s.
Insider threats
Insider threats come from employees, partners, contractors, vendors, suppliers, or anyone with access to the organization’s resources.
Unlike other sources of cyber threats, not all insider issues have harmful intentions. It can come down to inadvertent, human errors like employees unwittingly installing unauthorized software, falling for a phishing scam, or losing a company-issued device.
For instance, an 18-year-old hacker breached Uber Technologies in 2022 by using social engineering techniques to get authentication credentials from a company contractor.
But malicious insiders do exist. Such turncloak abuse their access privileges to steal data for monetary gain or cause damage to data or applications. Data breaches caused by malicious insiders are more costly at $4.90 million than the average data breach cost of $4.45 million.
Cyberterrorists
Terrorist organizations launch politically or ideologically motivated cyberattacks that threaten or result in violence. Some cyberterrorists are state-sponsored, and others act on their own or on behalf of a non-government group.
Targets of cyber attacks: Who and what do cybercriminals target?
Hackers are often drawn to seemingly vulnerable and valuable targets. They usually prey on
- Individuals
- Businesses of different sizes and different sectors that have valuable data, or cash-rich
- Government and military agencies
- Critical infrastructure like power grids, healthcare, and emergency services
- Educational and research institutions
- Nonprofit organizations (NGOs)
Quer aprender mais sobre Soluções de Segurança para IoT? Explore os produtos de Soluções de Segurança para IoT.
12 types of cyber security threats with real-life examples
Threat actors launch cyberattacks using a variety of tactics to gain unauthorized access to their target systems. Here’s an overview of the different kinds, as well as some real-life examples.
1. Malware
Short for malicious software, malware is any kind of code or software intentionally designed to cause harm to computer systems. Malware can compromise a system’s security and privacy by gaining unauthorized access, stealing, altering, encrypting, or destroying data.
A new malware called DogeRAT that takes control over affected devices was found targeting Android mobile users in India in September 2023.
Malware comes in many forms:
- Viruses are self-replicating malware tools that attach themselves to legitimate files and spread to other files and systems when executed.
- Worms self-replicate exponentially across networks or devices without the need for a host file.
- Rootkits are malicious programs that conceal their presence and get administrator-level access to a computer’s operating system or other assets.
- Trojan horses are disguised as legitimate software tools that spread using social engineering techniques.
- Ransomware is a sophisticated malware platform that encrypts the victim’s data or system. It’s used to demand a ransom in exchange for the decryption key.
- Spyware secretly monitors user activity and transmits sensitive data to hackers without the victim’s knowledge or consent.
- Fileless malware operates in computer memory rather than on a device's hard drive, making it difficult to detect and eradicate.
- Scareware is deceptive software that tricks users into believing their computer is infected or has serious issues, prompting them to purchase fake or unnecessary security software.
- Adware displays unwanted advertisements on web browsers to generate revenue for the adware creators.
- Keylogger secretly records a user's keystrokes to capture sensitive data like login credentials.
- Cryptojacking malware is used to illegally mine cryptocurrencies in a victim’s system.
In 2022 alone, there were 5.5 billion malware attacks, fuelled by cryptojacking malware and malware targeting IoT devices. Beacon, Systembc, hivelocker, Qakbot, and Metaspoilt are some of the most popular malware tools used in 2022.
Related: Learn about anti-malware software that protects you against malware in Windows, iOS, and Android devices.
2. Social engineering attacks
Social engineering attacks use psychological manipulation against people rather than technical weakness in systems. Hackers impersonate people you know or someone from a trustworthy organization to get your trust and make you willingly lower your guard. They invoke fear, greed, urgency, and other emotions to make you divulge credit card details or click on a malicious link.
For instance, identity and access management company Okta found threat actors used social engineering tactics to target several of its customers’ IT service personnel. Hackers made Okta’s clients reset the multi-factor authentication (MFA) of highly privileged users in each company. They then used that privilege to impersonate legit staff and access private applications.
Common social engineering techniques are mentioned here.
- Phishing involves sending deceptive emails or messages designed to trick recipients into revealing confidential data, such as passwords or financial details.
- Baiting makes false promises that pique curiosity or greed to make recipients install malware or share personal information.
- Pretexting manipulates users with a fake scenario to make them divulge important data.
3. Phishing
Imagine you wake up to a distress message from your friend asking you for money urgently via email because they are stuck in Paris after losing their wallet. Except your friend is sleeping peacefully in your guest room. That’s because the person who sent the emergency message isn’t your friend, but a hacker.
We call this phishing, one of the most common social engineering attacks. The cyber threat involves hackers using fraudulent emails, messages, phone calls, or websites to trick users into sharing personal data or taking action that exposes the victim or their organization to cybercrime. Phishing often results in data or monetary loss.
For instance, Tech giants Facebook and Google were swindled for nearly $100 million between 2013 and 2015 via a phishing attack. The fraud impersonated a vendor and emailed fake invoices that seemed so legitimate that both companies paid out.
Phishing causes 16% of all data breaches, making it the most common initial attack vector. Read on for more info about different techniques.
- Spear phishing comprises highly targeted phishing attacks against individuals with privileged access.
- Whaling attacks a company’s senior executives or valuable public figures.
- Business email compromise (BEC) is a type of spear phishing targeting businesses for extremely valuable corporate information or money.
- Voice phishing or vishing happens over phone calls. Thanks to voice-over-internet providers (VoIP) tools, scammers today make millions of vishing attempts.
- SMS phishing, or smishing, refers to phishing via text messages or SMSes.
- Social media phishing happens via social networking sites like Facebook, LinkedIn, Twitter, TikTok, and Instagram.
4. Ransomware
Even though ransomware is a type of malware, it warrants a separate section because of the danger it poses.
Criminals use malware to block access to data. They threaten to keep it locked or publish it unless the victim pays a hefty ransom.
The Colonial Pipeline Company, which is responsible for transporting gas in the Southeastern US, was forced to halt operations after a ransomware attack locked the company’s systems in 2021. The attackers restored the system only after receiving $4.4 million in Bitcoin.
Ransomware attacks gained prominence among crime groups after the highly successful and notorious Wannacry attacks in 2017. Today, the assaults target critical infrastructure, businesses of all sizes, and governments. Hackers are also offering ransomware as a service, lowering barriers to entry for wannabe cybercriminals.
5. Supply chain attacks
Supply chain attacks abuse vulnerabilities in trusted software, application programming interfaces (APIs), and the off-the-shelf services of a company’s software supply chain. Culprits then use this compromised link to plant a backdoor and gain access to the organization's systems.
Once in, they use their access to orchestrate further attacks or move upstream or downstream to steal from other vendors, suppliers, or the organization's customers in the supply chain. A single attack compromises multiple points, making it much more dangerous than other types of cyber threats.
In fact, the SolarWinds hack (2020-2021) – one of the biggest cyberattacks ever – was the result of a supply chain attack. Thieves delivered a backdoor malware as one of SolarWinds’ software updates in Orion’s platform. 18,000 customers, ranging from tech giants like Microsoft to US government agencies were affected by unwittingly downloading the update.
6. Man-in-the-middle attacks (MITM)
In MITM, the attackers eavesdrop on or alter communication between two legitimate parties by inserting themselves in between – or in “the middle” – without being detected. MITM often targets financial app users, software as a service (SaaS) companies, e-commerce sites, and other websites where logging in is required.
Common MITM attack techniques are below.
- Wifi-eavesdropping intercepts all unencrypted traffic on an unsecured Wi-Fi network set up by the hacker in public spaces.
- Email spoofing fakes emails from a legitimate source to trick the receiver and make them share personal details like login credentials.
- Domain name system (DNS) spoofing manipulates responses from DNS servers to send users to untrustworthy sites.
- Internet protocol (IP) spoofing impersonates a trusted IP address to intercept or manipulate network data packets and gain unauthorized entry into a device or network.
- Hypertext transfer protocol secure (HTTPS) spoofing mimics legitimate websites to trick users into visiting them for fraud or phishing.
- Cache poisoning manipulates cache content with harmful data to redirect users to phony websites.
Recently, hackers used a MITM attack to deploy spyware on iOS and Android mobile phones.
7. Distributed denial of service (DDoS) attacks
DDoS attacks, as the name suggests, literally try to deny service. It makes a system resource or a website unavailable to legitimate users by overwhelming it with traffic from multiple points. DDoS is highly disruptive and causes business downtime and monetary loss.
DDoS attacks are also used as a smokescreen to hide more sophisticated cyber attacks happening at the same time, like extortion or data theft. Like ransomware, criminals offer DDoS attacks as a service, with prices ranging from $20 per day to $10,000 per month.
There are three categories for DDoS attacks:
- Volumetric attacks generate massive traffic to an attacked site using techniques like user datagramprotocol (UDP) floods or Internet control message protocol (ICMP) floods.
- Protocol-based attacks impair actual server resources or other in-between network equipment like firewalls or load balancers with synchronize (SYN) flooding or ping of death.
- Application layer attacks overwhelm web servers with a high volume of seemingly legitimate requests, resulting in a server crash.
In June 2023, a threat actor called Anonymous Sudan launched an application layer DDoS attack on Microsoft 365, OneDrive, and Azure services, causing temporary outages.
8. SQLi attacks
Structured query language injection (SQLi) is one of the most common types of code injection attacks that target web applications. Attackers inject malicious code into the SQL query of the targeted app’s database. A successful SQLi attack results in errors in the app, unauthorized access, data breaches, and compromised systems – all of which hackers can use to strike other systems in the network.
For example, the MoveIT supply chain attack was a result of SQL injection vulnerability in the software.
Apart from SQLi, cross-site scripting (XSS) attack and cross-site request forgery (CSRP) are other common threats to web applications.
10. Zero-day exploits
A zero-day exploit abuses zero-day vulnerabilities or unknown security flaws in software, hardware, or firmware. Since the targets often don’t even know about these vulnerabilities, zero-day exploits can go undetected for days before proper investigation and mitigation.
For instance, the WannaCry ransomware attack from 2017 that affected over 200,000 systems in more than 150 countries was launched against the Microsoft Windows operating system using a zero-day exploit called EternalBlue.
Zero-day vulnerabilities are such a menacing cyber threat is that even if a vulnerability is made public for organizations to update their security, it only takes 14 days for criminals to create an exploit in the wild. Until the affected organization patches all of its systems properly, hackers will look for ways to leverage the vulnerabilities. For instance, hackers still scan for the known zero-day vulnerability in Log4j that was disclosed in 2021.
Related: Learn the best practices to prevent zero-day attacks from security experts.
10. IoT vulnerabilities
Threats that come from security flaws in devices like smart TVs, smart thermostats, and security cameras are prime targets for hackers. IoT devices aren’t highly secure by design because of their limited hardware and computational capabilities. Hackers easily exploit the IoT vulnerabilities to gain command, steal data, or make the devices part of a botnet.
An IoT botnet is a network of internet-connected IoT devices that are remotely controlled by attackers. It poses a significant threat as it’s often used for sophisticated and vast DDoS attacks.
1 million
IoT devices engaged in botnet-driven DDoS attacks in 2023, up from just 200,000+ a year ago.
Source: Nokia
To give an example, Mirai botnet, founded in 2016, targeted IoT devices like cameras and routers, turned them into bots, and used them to launch one of the biggest DDoS attacks. It temporarily took down high-profile sites like Netflix, Twitter, and Github.
11. Brute force attacks
A brute force attack is a simple but effective hacking method that cracks passwords, login credentials, and encryption keys. Criminals use computational power to relentlessly try all possible combinations of passwords till the right credentials are found. So, as much as your password “password@123” has billions of combinations to try, hackers can easily guess it in a matter of seconds using a brute-force attack.
Recently, the Akira ransomware gang brute-forced their way into one of Cisco’s VPN services, breached 11 customers, and compromised other systems in their network.
12. Advanced persistent threats (APT)
APTs are particularly vicious cyber threats. Theattacker gains unauthorized access to a computer system and remains undetected for an extended period of time. They operate clandestinely, infiltrating computer systems, conducting espionage and reconnaissance, escalating privileges and permissions, and exfiltrating sensitive data.
APTs require meticulous planning and more resources than a standard cyber threat like SQLi or malware attack. Because of this, they’re often launched by state-sponsored actors or organized crime groups.
China-based APT groups have been targeting European government embassies since December 2022 to get hold of sensitive information related to foreign policies.
How to protect against cyber threats: cybersecurity best practices
No doubt, cyber threats are devastating so let’s talk about what you should do now to protect your organization.
- Implement a cybersecurity policy that outlines your organization's requirements and procedures. This helps you prioritize which security solutions you need to invest in first.
- Educate your employees about cybersecurity best practices so they’re more aware of the risks and the steps to take to protect themselves.
- Use strong passwords with MFA and access control. Limit employee access following the least privilege principle.
- Keep your software and systems up to date. Software updates often include security patches that protect you from weak points. Take advantage of vulnerability management software to verify all components in your software and hardware stack are current.
- Encrypt and backup data. Conceal sensitive data in transit and at rest to protect it from unauthorized access. Use backup software to recover data in case of loss or ransomware attacks.
- Invest in a robust security stack. Allocate resources to build a comprehensive security stack that includes network security software, endpoint protection tools, cloud security solutions, and IoT security systems.
- Monitor your networks and systems for suspicious activity. Intrusion detection systems and network monitoring tools help respond to cyberattacks early. Cyber threat intelligence solutions also help in this case.
- Put an incident response plan in place. This plan should include steps for containing the attack, investigating the incident, and recovering your data.
- Assess third-party vendors’ security practices to prevent supply chain attacks.
- Conduct regular security audits to identify and remediate vulnerabilities and to ensure that your security system is working properly.
12 must-have solutions in your security stack:

3 emerging trends in the cyber threat landscape
While known cyber security threats continue to plague us, the threat landscape is rapidly changing. Let’s take a look at the emerging trends to know what your security teams should keep in mind when strengthening your defense.
1. Rising ransomware and BEC threats
Established threats like ransomware and business email compromises will dominate the list of top cybersecurity threats in the coming years. Why should you care? BEC is the most expensive financial crime being committed today, taking organizations for $2.7 billion in 2022. Ransomware is fast catching up to BEC, with damages expected to cause a loss of $265 billion by 2031.
Attackers are using platforms like BulletProftLink, which sells end-to-end service for BEC, and Locky, and Goliath, which sells ransomware-as a service for industrious scale campaigns.
There’s also the rising trend of dual ransomware attacks, a second ransomware attack on the same victim within 10 days of the first attack using different malware. This, when combined with escalating supply chain attacks and double extortion, makes ransomware much more dangerous.
2. Increasing cloud complexity
Businesses need the cloud for their IT infrastructure these days. However, growing cloud adoption presents unique security challenges due to the complexity of cloud services and the increasing attack surface.
Attackers frequently target cloud services because of the scalable computing resources it offers that can be abused and the valuable data cloud holds. The hackers exploit breached cloud services to launch other large-scale attacks like cryptojacking or DDoS attacks.
Cloud security risks like misconfigurations, insecure third-party services and APIs, and poor access management often lead to data breaches. In fact, in 2022, 82% of information leaks involved data stored in the cloud, according to IBM data. Given the rapid migration, the security issues related to cloud services will increase.
3. Artificial intelligence (AI) and machine learning (ML) threats
By using AI and ML in so many different ways, businesses have unintentionally opened new exploit channels for criminals, particularly those threatening data security.
Threat actors are also causing concern because they’re upping their use of AI to launch cyberattacks. Among other tricks, they’re writing phishing emails with generative tools and turning to AI to automate social engineering scams on mobile phones.
135%
was the increase in social engineering attacks using generative AI tools like ChatGPT between January and February 2023.
Source: Darktrace
Deep fakes for vishing scams, fraudulent websites, disinformation campaigns, deceitful social media profiles, and AI-powered malware – the list of cyber crimes boosted with AI tools grows and grows. AI and ML algorithms also amplify the impact of other cyber threats like brute force and DDoS attacks and help them go undetected by traditional security tools.
On guard always
Cyber threats wreak havoc on individuals, businesses, and governments. They are constantly evolving, getting bigger and better, but we have steps to protect ourselves from their dangers. Embrace the cybersecurity best practices, invest in comprehensive solutions for cyber threat prevention, and stay vigilant. You’ll get the baddies before they get you.
Take the first step toward protecting your business. Explore security software that can help defend your organization.

Soundarya Jayaraman
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.