What is log analysis?
Log analysis provides visibility into the performance of IT infrastructure and application stacks. It reviews and interprets logs produced by servers, networks, operating systems, and applications.
Logs are time-stamped documentation of a particular computer system. They frequently include time-series data broadcast in real-time by utilizing collectors or archives for subsequent analysis. Log analysis informs users about system performance and may point out potential issues like security lapses or impending hardware breakdown.
Many businesses use log analysis software to effectively document application log files for better analysis.
How to perform a log analysis
Log analysis examines log data produced by computer systems, applications, and network devices to address security, compliance, and system performance issues.
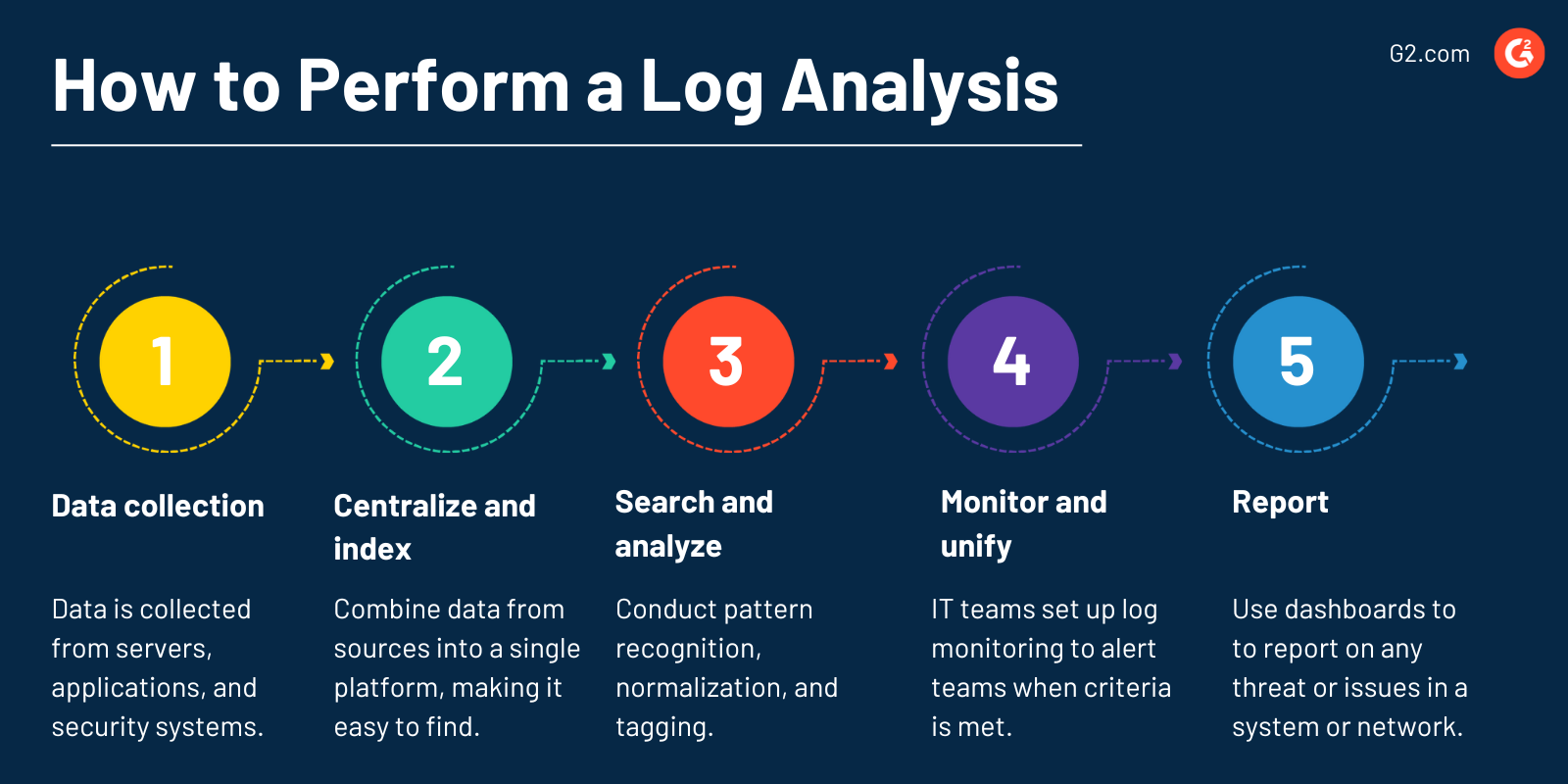
It follows these steps:
- Data collection. IT teams install a collector to gather data from sources like servers, applications, and security systems. Through an active network, log files are broadcast to a log collector or kept in files for subsequent analysis.
- Centralize and index. To make the search and analysis process more efficient, professionals combine data from all log sources into a single platform. Logs become accessible after indexing so security and IT staff can easily find required data.
- Search and analyze. Pattern recognition, normalization, tagging, and correlation analysis help search and analyze logs.
- Monitor and notify. Using machine learning and analytics, IT organizations set up automatic and real-time log monitoring to alert their teams when they meet specific criteria. With the help of automation, many logs across systems and applications can be continuously monitored.
- Report. IT teams utilize personalized reusable dashboards to report on any threat or performance issues in a system or network. Only staff members who need to know can access private security logs and analytics.
Log analysis benefits
Log analysis is a crucial tool for well-maintained, secure computer systems. Organizations can safeguard their systems and guarantee compliance with industry laws by utilizing the insights discovered through log analysis. Here are other ways log analysis benefits businesses.
- Enhanced troubleshooting. Companies that routinely monitor and analyze logs quickly spot problems. They identify issues with sophisticated log analysis tools, considerably reducing the time and expense of the remedy.
- Improved cybersecurity. Organizations can find anomalies, contain threats, and prioritize solutions more rapidly by regularly reviewing and analyzing logs.
- Enhanced client satisfaction. Businesses can ensure all customer-facing tools and programs are fully functional and safe by using log analysis. Enterprises can immediately identify disturbances or prevent problems with consistent and proactive analysis of log events.
- Better system performance. Businesses can find bottlenecks, resource limitations, and other system performance problems. They can then optimize their systems and boost performance by addressing these issues.
- Compliance. Several industry laws demand that businesses monitor and review their IT infrastructure. By providing a record of system activity, log analysis assists organizations in meeting these demands.
- Cost savings. Log analysis helps organizations reduce downtime, lower support costs, and maximize resource utilization, leading to cost savings.
Log analysis techniques
With data in massive volumes, it’s impractical for IT experts to manually maintain and analyze logs across a vast tech environment. A log management system automates key phases in data collection, formatting, and analysis. Below are some techniques IT professionals employ to analyze logs.
- Normalization ensures all of the information in the transaction log is formatted consistently, including IP addresses and timestamps.
- Pattern identification distinguishes between routine events, anomalies, and filters events based on a pattern book.
- Tags and classifications assign keywords to group events to examine related or similar occurrences together.
- Correlational research collects log data from several sources and analyzes it all at once using log analytics.
- Artificial ignorance omits entries that are irrelevant to the functionality or health of the system.
Log analysis applications
Log analysis applications generally fall under three main groups, detailed here:
- Monitoring. Logs help IT professionals track how a product or service is used, mostly for security reasons. Teams can spot harmful usage patterns by looking through the logs.
- Auditing. Logs facilitate audits, especially in the financial sector. For instance, in the case of a supervised exchange that enables users to trade between different currencies, the regulators may request access to the exchange's logs to review the transaction history.
- Debugging. Programmers use relevant logs to detect any threats or defects in a product or service and take necessary measures to fix them.
Log analysis vs. application performance management (APM)
Log analysis and application performance management optimize application performance. However, their purposes are different.
Log analysis focuses on handling the log data. It serves as a prerequisite to broader application performance management.
Application performance management (APM) caters to improving the overall performance of an app. Log analysis supports APM with log data, empowering IT teams to fix any performance issues. This doesn’t mean that the sole purpose of log analysis is to support APM. Log analysis enables organizations to secure sensitive data, prove compliance, and recognize long-term trends, which isn’t feasible using the APM tool as a standalone technology.
Learn more about the best application performance management tools for tracking and monitoring application performance.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.