What is access control?
Access control is a security strategy that restricts physical and virtual access unless a user is eligible and their authentication credentials are valid.
To gain access to a building or particular area, an access control system typically entails locked gates, doors, or barriers that people can open with identity authentication techniques like radio frequency identification (RFID) access cards, PIN codes, face recognition, fingerprints, or smartphones.
Similarly, organizations can protect digital assets against online threats and improve cybersecurity by managing user authentication and placing relevant user access controls. Network access control software is designed to help implement policies and control access to corporate networks.
Setting and enforcing appropriate user authorization, authentication, role-based access control policies, and attribute-based access control policies are all part of managing access.
Types of access control
Four different types of access control are used to limit access to a place of employment or residence. Each has advantages and disadvantages, so it's crucial to consider the particular security requirements and select the access control method that best suits them.
-
Discretionary Access Control (DAC): A business owner can control how many people can access a particular location with a discretionary access control system. A list of authorized users is kept at each access control point. The system checks the credentials against the list each time a keycard is swiped or a PIN is entered, and then it either grants or denies access.
DAC systems are thought to be the most adaptable and provide the most allowances compared to other access control methods. It also has the lowest level of security, especially when compared to other systems that require access control. Here, the access is with one person who may knowingly or unknowingly hand it over to someone who shouldn’t use it. Systems with DAC work best for businesses that demand flexibility and usability. -
Mandatory Access Control: MAC systems are the most secure access control. Only owners and support staff are eligible to use the systems. The system administrator determines all access control settings, which cannot be altered or removed without their consent.
A MAC system functions by classifying all users and granting them access to areas per the system's programming. MACs are the most stringent and safe access control measures but also the least flexible. The administrator modifies the security lists at the entry point and the specific user's access to change permissions. Companies and government organizations that demand the highest levels of security frequently use MAC systems. - Role-Based Access Control: RBAC is quickly overtaking all other access control methods in popularity. An RBAC system grants permissions to a particular job title rather than issuing them to specific users, as in a MAC system. The amount of time required to set up access is reduced. With 20 salespeople, two managers, and three accountants, for instance, there is no need to set up 25 different security profiles in the system. Each job title requires only one security profile. When employees get promoted, they receive credentials that fit the new role.
-
Rule-Based Access Control: Rule-based access control, which is distinct from the other "RBAC," is frequently used in conjunction with other types of access control. In rule-based access control, access permissions are based on roles and specific rules written by the administrator for distinct roles.
For example, employees cannot access the office after closing hours. If operating hours are from 9 am to 6 pm, the company can set a guideline to prevent anyone from accessing the system from 6 pm to 9 am.
Benefits of access control
Security is of utmost importance to any business. A company’s confidential information or expensive equipment must be safeguarded for the company’s success. The following are the key advantages of implementing access control systems.
- Easier employee access: The use of an access control system enables organizations to "set and forget" who has access to each area of the company. Employees can access any site they require by scanning a card or entering a PIN.
- No need for old-fashioned keys: There are cons to using conventional keys. Separate keys are necessary to restrict access to specific sites. In addition to saving users' trips to the locksmith, an access control system speeds up access to restricted areas.
- No unauthorized visitors: Visitors can avoid detection when they visit a large corporation. Using access control systems has the advantage of preventing unauthorized access. Only those with proper credentials can enter the area because doors require authorization before they unlock.
- 24/7 employee permission: An access control system enables employees with varying shifts to enter the building whenever necessary. Managers don't have to stay late to lock up at the end of the day; everyone can arrive early without waiting for someone to unlock the doors.
- Protected data: Client information, financial records, and health information are frequently kept on company-owned servers. Only authorized users are permitted access to IT rooms, individual computers, and networks thanks to access control systems that restrict or permit access.
Access control vs. authorization
It's common to confuse access control and authorization, but the two are very different.
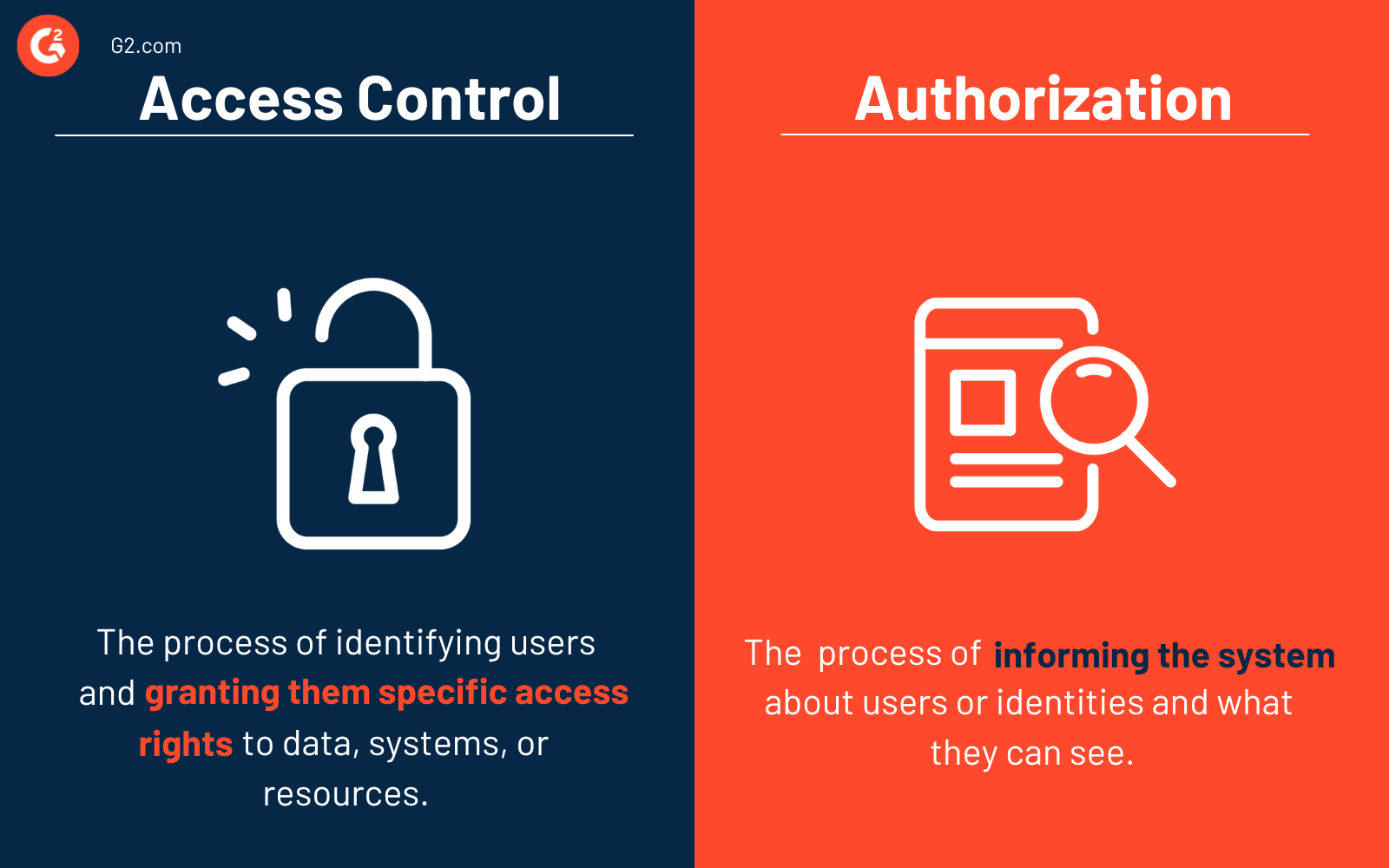
The process of identifying users and granting them specific access rights to data, systems, or resources is known as access control. To handle proper disclosure of information, it’s crucial to comprehend the element of access control. Access control refers to the power to approve or deny the use of a particular resource.
Authorization and access control work hand in hand. The authorization process informs the system about users or identities and what they can see. Access control unlocks the assets for users or identities to perform their job.
Learn more about threat intelligence and how it helps to protect against cyber attacks.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.