Qu'est-ce que le contrôle d'accès ?
Le contrôle d'accès est une stratégie de sécurité qui restreint l'accès physique et virtuel à moins qu'un utilisateur ne soit éligible et que ses informations d'authentification soient valides.
Pour accéder à un bâtiment ou à une zone particulière, un système de contrôle d'accès implique généralement des portails, portes ou barrières verrouillés que les personnes peuvent ouvrir avec des techniques d'authentification d'identité telles que des cartes d'accès à identification par radiofréquence (RFID), des codes PIN, la reconnaissance faciale, les empreintes digitales ou les smartphones.
De même, les organisations peuvent protéger les actifs numériques contre les menaces en ligne et améliorer la cybersécurité en gérant l'authentification des utilisateurs et en mettant en place des contrôles d'accès pertinents pour les utilisateurs. Le logiciel de contrôle d'accès réseau est conçu pour aider à mettre en œuvre des politiques et contrôler l'accès aux réseaux d'entreprise.
La gestion de l'accès comprend la définition et l'application de politiques d'autorisation, d'authentification, de contrôle d'accès basé sur les rôles et de contrôle d'accès basé sur les attributs appropriées.
Types de contrôle d'accès
Quatre types différents de contrôle d'accès sont utilisés pour limiter l'accès à un lieu de travail ou de résidence. Chacun a des avantages et des inconvénients, il est donc crucial de considérer les besoins de sécurité particuliers et de choisir la méthode de contrôle d'accès qui leur convient le mieux.
-
Contrôle d'accès discrétionnaire (DAC) : Un propriétaire d'entreprise peut contrôler combien de personnes peuvent accéder à un lieu particulier avec un système de contrôle d'accès discrétionnaire. Une liste d'utilisateurs autorisés est conservée à chaque point de contrôle d'accès. Le système vérifie les informations d'identification par rapport à la liste chaque fois qu'une carte-clé est glissée ou qu'un code PIN est saisi, puis il accorde ou refuse l'accès.
Les systèmes DAC sont considérés comme les plus adaptables et offrent le plus de tolérances par rapport aux autres méthodes de contrôle d'accès. Ils ont également le niveau de sécurité le plus bas, surtout par rapport aux autres systèmes qui nécessitent un contrôle d'accès. Ici, l'accès est avec une personne qui peut sciemment ou inconsciemment le transmettre à quelqu'un qui ne devrait pas l'utiliser. Les systèmes avec DAC fonctionnent mieux pour les entreprises qui exigent flexibilité et convivialité. -
Contrôle d'accès obligatoire : Les systèmes MAC sont les systèmes de contrôle d'accès les plus sécurisés. Seuls les propriétaires et le personnel de soutien sont éligibles pour utiliser les systèmes. L'administrateur du système détermine tous les paramètres de contrôle d'accès, qui ne peuvent être modifiés ou supprimés sans son consentement.
Un système MAC fonctionne en classifiant tous les utilisateurs et en leur accordant l'accès aux zones selon la programmation du système. Les MAC sont les mesures de contrôle d'accès les plus strictes et les plus sûres, mais aussi les moins flexibles. L'administrateur modifie les listes de sécurité au point d'entrée et l'accès de l'utilisateur spécifique pour changer les autorisations. Les entreprises et les organisations gouvernementales qui exigent les plus hauts niveaux de sécurité utilisent fréquemment les systèmes MAC. - Contrôle d'accès basé sur les rôles : Le RBAC est rapidement en train de dépasser toutes les autres méthodes de contrôle d'accès en popularité. Un système RBAC accorde des autorisations à un titre de poste particulier plutôt que de les attribuer à des utilisateurs spécifiques, comme dans un système MAC. Le temps nécessaire pour configurer l'accès est réduit. Avec 20 vendeurs, deux managers et trois comptables, par exemple, il n'est pas nécessaire de configurer 25 profils de sécurité différents dans le système. Chaque titre de poste nécessite seulement un profil de sécurité. Lorsque les employés sont promus, ils reçoivent des informations d'identification qui correspondent au nouveau rôle.
-
Contrôle d'accès basé sur les règles : Le contrôle d'accès basé sur les règles, qui est distinct de l'autre "RBAC", est souvent utilisé en conjonction avec d'autres types de contrôle d'accès. Dans le contrôle d'accès basé sur les règles, les autorisations d'accès sont basées sur des rôles et des règles spécifiques écrites par l'administrateur pour des rôles distincts.
Par exemple, les employés ne peuvent pas accéder au bureau après les heures de fermeture. Si les heures d'ouverture sont de 9h à 18h, l'entreprise peut établir une directive pour empêcher quiconque d'accéder au système de 18h à 9h.
Avantages du contrôle d'accès
La sécurité est d'une importance capitale pour toute entreprise. Les informations confidentielles d'une entreprise ou les équipements coûteux doivent être protégés pour le succès de l'entreprise. Voici les principaux avantages de la mise en œuvre de systèmes de contrôle d'accès.
- Accès des employés facilité : L'utilisation d'un système de contrôle d'accès permet aux organisations de "définir et oublier" qui a accès à chaque zone de l'entreprise. Les employés peuvent accéder à n'importe quel site dont ils ont besoin en scannant une carte ou en saisissant un code PIN.
- Pas besoin de clés à l'ancienne : Il y a des inconvénients à utiliser des clés conventionnelles. Des clés séparées sont nécessaires pour restreindre l'accès à des sites spécifiques. En plus d'économiser les déplacements des utilisateurs chez le serrurier, un système de contrôle d'accès accélère l'accès aux zones restreintes.
- Pas de visiteurs non autorisés : Les visiteurs peuvent éviter d'être détectés lorsqu'ils visitent une grande entreprise. L'utilisation de systèmes de contrôle d'accès a l'avantage de prévenir les accès non autorisés. Seules les personnes ayant les informations d'identification appropriées peuvent entrer dans la zone car les portes nécessitent une autorisation avant de se déverrouiller.
- Autorisation des employés 24/7 : Un système de contrôle d'accès permet aux employés ayant des horaires variables d'entrer dans le bâtiment quand cela est nécessaire. Les managers n'ont pas à rester tard pour fermer à la fin de la journée ; tout le monde peut arriver tôt sans attendre que quelqu'un déverrouille les portes.
- Données protégées : Les informations client, les dossiers financiers et les informations de santé sont souvent conservés sur des serveurs appartenant à l'entreprise. Seuls les utilisateurs autorisés sont autorisés à accéder aux salles informatiques, aux ordinateurs individuels et aux réseaux grâce à des systèmes de contrôle d'accès qui restreignent ou permettent l'accès.
Contrôle d'accès vs. autorisation
Il est courant de confondre le contrôle d'accès et l'autorisation, mais les deux sont très différents.
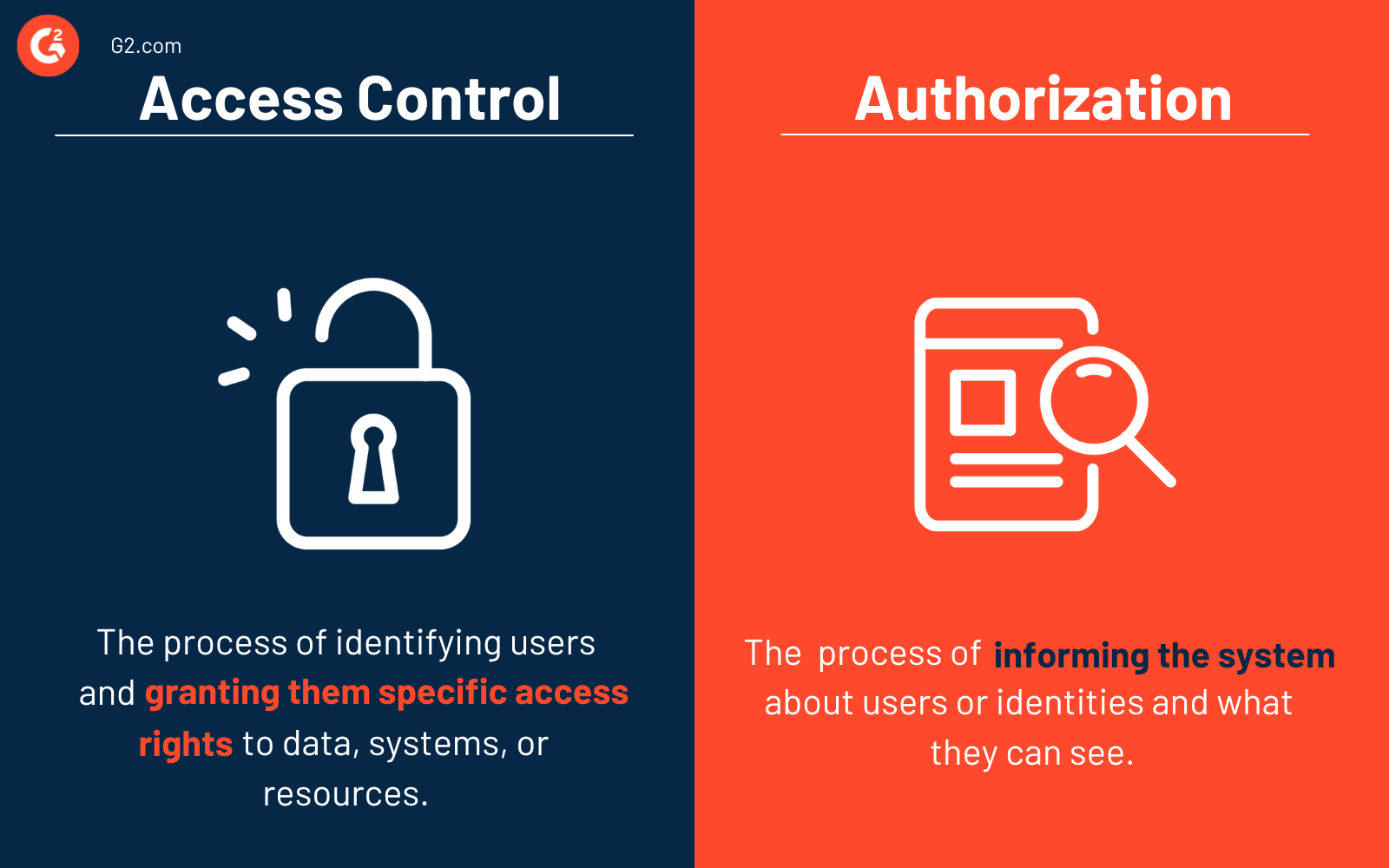
Le processus d'identification des utilisateurs et de leur octroi de droits d'accès spécifiques à des données, systèmes ou ressources est connu sous le nom de contrôle d'accès. Pour gérer la divulgation appropriée des informations, il est crucial de comprendre l'élément de contrôle d'accès. Le contrôle d'accès fait référence au pouvoir d'approuver ou de refuser l'utilisation d'une ressource particulière.
L'autorisation et le contrôle d'accès fonctionnent main dans la main. Le processus d'autorisation informe le système des utilisateurs ou des identités et de ce qu'ils peuvent voir. Le contrôle d'accès déverrouille les actifs pour que les utilisateurs ou les identités puissent effectuer leur travail.
En savoir plus sur l'intelligence des menaces et comment elle aide à se protéger contre les cyberattaques.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.