Spoofing is an art of trickery and deception.
Back in the days of Alexander Graham Bell and his telephone, spoofing meant imitating the true origin of an incoming call. Today, it has a much broader definition and is generally used to describe any attempt at manipulating data.
For example, if you’re communicating via email and you present yourself as someone you’re not, you're engaging in spoofing.
Spoofing attacks often occur through emails. It’s advisable to onboard email anti-spam software to set up defenses against them.
What is spoofing?
Spoofing is a cyber attack that happens when an attacker pretends to be a trusted brand or contact in an attempt to trick a target into revealing sensitive information. Cybercriminals often impersonate well-known brands and website addresses to conduct a spoofing attack.
Spoofing attacks rely on the scammer’s ability to impersonate a trusted authority or a brand. Attackers can choose from various communication channels such as email, phone or text messages to perform spoofing. These attacks include a social engineering element that psychologically manipulates victims by using their greed, fear or lack of technical information.
These con artists can also choose a more technical route such as Domain Name System (DNS) spoofing or Internet Protocol (IP) address spoofing. The complexity of these attacks depends on a hacker's technical expertise and the robustness of an organization’s security posture.
How does spoofing work?
Scammers perform spoofing using two significant elements: spoof and social engineering. A spoof can be an email or text message from a trusted brand or an authoritative person like the CEO or CMO of a company. The social engineering aspect tricks victims into clicking on a link or downloading an attachment that might make a computer system prone to malware or ransomware attacks.
Attackers commonly use email spoofing to access victims' information. They can disguise their emails, impersonate a manager or owner or otherwise trick targets into performing a task that exposes sensitive data.
Content in these emails or the actual task will have a sense of urgency and would nudge human emotions of greed or fear. Imagine getting an email from your company’s CEO asking you to urgently remove a social media post since it’s damaging the business’ reputation.
Usually, your first reaction would be to click on the link and check the specific post. And that’s where they trick you. When you click on the link, you get redirected to a malicious website that can capture your information.
In email spoofing, attackers might register a domain name similar to your company's. For example, 1earn.g2.com. This subdomain might appear similar to learn.g2.com until you notice that the alphabet ‘l’ has been replaced by the number ‘1.’
The primary intention of spoofing is to uncover sensitive information and then use it to conduct a broader cyber attack. Since these attacks are based on deception, it becomes tricky to protect an organization’s network against them.
Spoofing attacks can result in data breaches that can have severe consequences. Organizations should set up proper security defenses with cybersecurity awareness programs to protect themselves against such attacks.
Want to learn more about Email Anti-spam Software? Explore Email Anti-spam products.
Spoofing vs. phishing
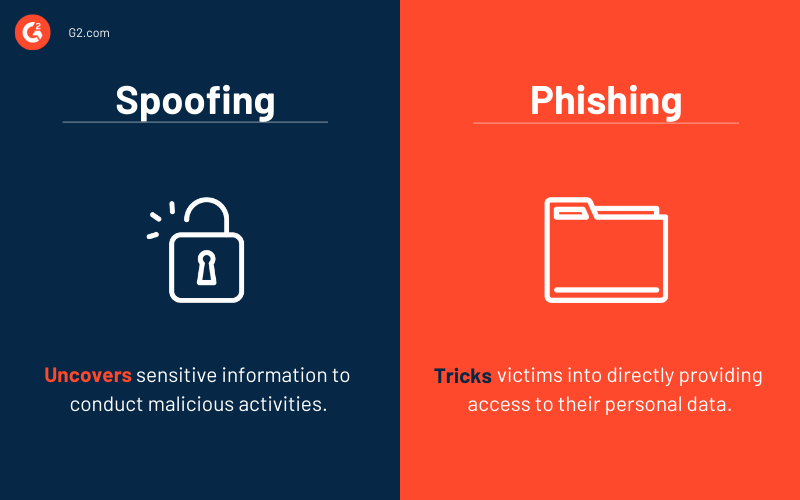
Spoofing and phishing are closely related as they both use an element of disguise and misrepresentation. Spoofing aims to uncover sensitive information to conduct malicious activities, whereas phishing aims to access personal data by tricking users into providing it directly.
Phishing is a common social engineering technique that you probably come across quite often. Phishing emails hold malicious attachments disguised as genuine files. In some cases, they contain links that take you to a malicious website and fool you into revealing sensitive information.
Sometimes, con artists target a small group instead of conducting a phishing attack at scale. They conduct thorough research on the target group to gain their trust and reflect their interests. Such types of phishing attacks are called spear phishing. Spear phishing attacks pose significant threats to organizations as their research helps disguise attackers as genuine employees.
Types of spoofing
Different types of attacks, like email spoofing, IP spoofing or website spoofing, use different channels to target their victims. Almost all of them exploit victims’ trust to access their sensitive information.
Below are some common types of spoofing attacks that hackers use to commit cybercrime.
Email spoofing
You often get emails from trusted websites asking you to click on a link and verify your account. Email account holders are familiar with these communications, and so are malicious hackers. Hackers can write an email asking a targeted user to change their password to maintain access to their account.
Spoofers are usually precise about the email's design and visual aesthetics by keeping it similar to a genuine brand. They try to lure you into their trap by feigning trustworthiness and tricking you into revealing your data.
This is just one common scenario of email spoofing out of many that attackers use to perform these attacks.
What is email spoofing?
Email spoofing is a technique that hackers use to exploit victims’ trust to access personal information by disguising emails as messages coming from any trusted person or brand.
Spoofed emails often encourage victims to transfer money, grant access permissions, deliver a malware payload or sign in to a malicious website disguised as a genuine one.
Tip: Email anti-spam software helps prevent malicious content from being delivered via email. Browse the best software to protect your business against email spoofing.
Below are some common signs of spoofed emails. When you see these, avoid taking any action and report them to your IT department.
- Generic email addresses: Emails coming from addresses at a free service provider, for example, xyzbankname@yahoo.com.
- Requests for personal data: Emails that ask for personal information such as credit card numbers, social security numbers or one-time passwords (OTP).
- Warnings to take urgent actions: Email that demands urgent actions by playing on fear or greed. For example, any message asking you to complete know your customer (KYC) now under threat of fines.
- Inconsistency and spelling errors: Emails where the address doesn’t match the sender’s name or have many typos and spelling mistakes.
- Typosquatting and spelling tricks: Emails that have typos in web addresses or that appear visually similar to genuine ones. For example, Iearn.g2.com and Iearn.g2.com appear similar, but one starts with ‘l’ and the other starts with an uppercase “i”.
IP spoofing
Every device connects to the Internet using an IP address. Any communication between devices or servers happens through data packets that detect your device’s IP address. An attacker can mess with web protocols by changing the IP addresses of their devices, tricking a secure network into letting them in.
What is IP spoofing?
IP spoofing is a technique that attackers use to hide the true source of IP packets to mask their identities or conduct a reflected DDoS attack.
Hackers take a legitimate host’s IP address and modify the packet headers sent from their device so they look like they come from a trusted source. Businesses should avoid falling victim to IP spoofing attacks as they often come as a part of Distributed Denial-of-Service (DDoS) attacks that can take down entire networks.
Tip: Discover how DDoS protection software can stop malicious traffic floods targeted at your network.
IP spoofing attacks can be tricky to detect as they happen in the network layer, i.e., layer 3 of the Open System Interconnection (OSI) model. They don’t leave any external signs.
Although IP spoofing is difficult to detect, it’s not impossible. Businesses can protect themselves from IP spoofing by using network monitoring software and firewalls with packet filtering capabilities. Packet filters detect fraudulent packets and check for inconsistencies in desired IP addresses and packets’ IP addresses.
Below are some ways organizations can protect themselves from IP spoofing attacks:
- Keep an eye out for unusual network activity.
- Use packet filtering systems.
- Verify methods for all remote access.
- Authenticate IP addresses.
- Leverage a network attack blocker.
- Keep at least a few computer resources behind a firewall.
Website spoofing
A spoofed website is a malicious replica of a legitimate website that an attacker creates to steal user credentials. As you enter your login credentials, attackers access them and use them to get into your account on the real website.
What is website spoofing?
Website spoofing is a technique of creating a replica of a trusted website, which can mislead victims and trick them into revealing their sensitive information, such as login credentials. The malicious website uses the same font, color, and themes as the legitimate ones.
Attackers sometimes use a cloaked URL. These URLs redirect a victim through hackers’ systems, allowing the hackers to capture personal information. Often, spoofed websites are used with email spoofing to trick victims into revealing their data.
Below are some common signs to detect spoofed websites:
- The lock symbol in the browser address bar is missing. If you click on the address bar, the URL starts with “HTTP://” instead of “HTTPS://”.
- Improper spelling, grammar, color scheme, or design
- The incomplete or sheer absence of privacy policy or terms and conditions
- None of the usual autofill login credentials are used
Phone spoofing
Many people get calls from a lottery, bank or any other institution asking for bank details and OTP for depositing cash rewards. These calls are likely from scammers who trick targets into exposing bank information to steal money. They often put false information on caller IDs and pave the way to establish trust.
What is phone spoofing?
Phone spoofing, also known as caller ID spoofing, involves scammers falsifying their information on caller IDs to cloak their real identity and pose as a local number. People usually pick up local calls as opposed to ones they don’t recognize.
The phone spoofing technique uses Voice Over Internet Protocol (VoIP) which attackers use to create phone numbers and caller ID of choice. These attackers also dupe people into revealing sensitive information such as their credit card numbers, OTPs or login credentials by disguising themselves as trusted authorities.
Text message spoofing
Attackers can use the short message service (SMS) channel to exploit users’ trust and access their data. You might have witnessed several messages, such as “$XXX by working only N hours!!!,” along with a sign-up link.
These messages often take you to a strange website where you’re asked to enter your information. While some websites just ask you to pay $ABC for registration, some exploit the information you share with them. Such attacks are commonly known as SMS phishing or smishing, and text message spoofing helps attackers hide their real identities behind alphanumeric IDs.
What is text message spoofing?
Text message spoofing happens when the sender of a message hides their identity and misleads users by falsifying sender information and showing alphanumeric characters in place of a real number.
Below are some ways to prevent text message spoofing accompanied by smishing:
- Refrain from clicking on links in an SMS as much as possible, especially the password reset ones, as they’re highly suspicious.
- Remember that financial institutions, telecommunications companies or other service providers don’t ask for sensitive data such as login credentials or OTPs over text.
- Be cautious with lucrative prizes or rewards when they seem too good to be true.
In addition to those discussed above, attackers use a few other methods to conduct a spoofing attack. These techniques are as follows:
- ARP spoofing involves an attacker infiltrating a local area network and intercepting communications between both communicating parties while impersonating them. Address Resolution Protocol ARP allows network communications to reach a specific device on a network. During an ARP spoofing attack, hackers send malicious ARP messages over a local area network (LAN), which link the threat actor’s media access control (MAC) address with a legitimate device’s IP address. With this, attackers disguise themselves as genuine network members and can steal, modify or stop any communication sent toward an IP address.
- DNS spoofing, also known as DNS cache poisoning, directs victims to a malicious website that might harvest their sensitive information. Attackers alter a target website’s DNS records as per their choice, which redirects a victim to a fake website disguised as a real one. These fraudulent websites can steal personal data or install malware into victims’ devices.
- GPS spoofing allows attackers to send false global positioning system (GPS) signals by tricking GPS receivers into broadcasting fake signals. Attackers use this to hack into a car’s GPS and send them to wrong locations. On a bigger magnitude, these attacks can interfere with aircraft and ships’ navigation systems.
- Facial spoofing uses a person’s face and simulates their facial biometrics with a photo or video to steal their identity. Attackers can use stolen biometric data to perform facial recognition spoofing attacks.
How to prevent spoofing
A spoofing attack can expose your company’s sensitive information to hackers who can exploit it in several negative ways. There are more do’s and fewer don'ts you can use to protect your organization against the strands of spoofing.
Do’s
- Adopt 2FA. Two-factor authentication (2FA) requires a user to prove their identity two times before they get access to their accounts. This adds an extra layer of security and makes it harder for hackers to authenticate into online accounts.
- Use better passwords. Strong passwords are difficult to crack. When lower and upper case alphabets assemble beside numbers and special characters, they form a string of characters. When this string grows in size, it becomes harder and harder for attackers to crack it and gain unauthorized access to user accounts. Ensure your password is of considerable length and prides itself on diverse text, digits, and symbols.
- Be alert on social. Use privacy and security settings wisely on social networking sites. Avoid clicking on spam links, and if you have clicked, don’t delay in reporting it.
- Update software. Regularly update your software and tools to patch security vulnerabilities and protect yourself from malware.
- Look out for lousy content quality. Keep an eye out for emails and websites with design inconsistencies or poor grammar and spelling errors. These can be a sign of spoofing attempts.
- Hide IP addresses. When surfing on the Internet, make a habit of hiding your IP address to prevent IP spoofing attacks.
- Install an antivirus program. Use antivirus software to detect threats in real time. This help protect your devices if you click on a malicious link or accidentally download a malware program.
Don’ts
- Don't reveal personal information. Refrain from disclosing your private information on the Internet unless you trust the receiver. Attackers can manipulate legitimate websites to create a fake website and trick you. Be alert while exposing your personal information.
- Don't answer unknown calls. Check who you’re talking to and whether the person is really someone they claim to be. Avoid answering questions that involve your sensitive personal information.
- Don't respond to unrecognized emails. Scammers disguise themselves as someone you trust and send emails encouraging you to click a link or download an attachment. Always verify the identity of the sender and avoid replying to spam emails.
- Don't click on links or download attachments. Double-check whether the message comes from a trusted source before clicking on any links or downloading attachments. Ensure the link doesn’t have any inconsistencies in its web address. If you’re in doubt, it’s better to avoid opening any attachment or link until you verify the sender’s identity.
Tricking people isn’t easy unless they make it easy
Spoofing attacks are based on deception. When you’re alert and careful while browsing the Internet, you can avoid getting tricked into a spoofing attempt. Ensure you have the right set of tools to safeguard against cyber attacks.
Remember, attackers can only exploit your devices if you let them.
Discover the best security products you can add to your arsenal to shield yourself from cyber attacks.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
