Technology has made the world a smaller place.
The advent of cloud computing has made access to applications or data virtually instantaneous from anywhere with an internet connection. However, IT departments can find it challenging to ensure that a business's bandwidth capabilities remain operational.
As the number of network services increases, IT organizations struggle to maintain Quality of Service (QoS) standards that ensure sufficient bandwidth to drive business unit initiatives.
To combat this, companies use multiprotocol label switching (MPLS) technology to manage large volumes of data and keep the individual flows separate for optimal security and performance. Together with software-defined wide area network (SD-WAN) software, MPLS is helping organizations mitigate the gaps in their existing network.
What is multiprotocol label switching (MPLS)?
Multiprotocol label switching (MPLS) is a traffic routing mechanism used in telecommunications networks to mold traffic flows when data is sent between network nodes. The term MPLS refers to both the technology and protocol developed explicitly for this purpose.
MPLS allows large service providers to deliver cost-effective Internet Protocol (IP) networking services. It’s one of the least known but most important technologies used in today's telecommunications networks. It was initially invented to improve the performance of existing internet networks by implementing a form of QoS management, which prioritizes each packet sent through a network.
The protocol distinguishes MPLS packets by an extra label attached to the packet's header, which gives information about its path through the network to the destination. MPLS is often used for high-speed data transfer networks that provide redundant paths to carry information between sites, allowing better resilience if part of the route fails.
MPLS is better than traditional IP routing because it transmits data directly to its destination rather than bouncing it all across the Internet before delivering it to its ultimate destination. MPLS is frequently used in carrier networks, private networks, metro optical networks, and more. It helps with resource pooling, congestion control of network traffic, and fast mapping of incoming packets.
MPLS is a standardized technology that uses various networking protocols, most commonly the IP and the transmission control protocol (TCP), to build a virtual circuit from a source to a destination. This allows a network operator to provide a guaranteed level of QoS for a particular application (such as real-time voice or video) over an ordinary "best-effort" packet network.
Virtual private networks (VPNs), traffic engineering (TE), and other applications can all benefit from MPLS.router
Features of MPLS services
Below are key features offered by an MPLS network:
- Scales to quickly add locations and improve bandwidth. This is excellent for organizations undergoing acquisitions or mergers.
- Supports voice over Internet Protocol (VoIP), bandwidth-intensive, and real-time applications.
- Allows traffic to be "engineered" by implementing QoS across the network and class of service (CoS) on routers. The business is in charge of traffic priority for the corporate network.
- Provides any-to-any configuration. If a private network is provided between all your sites, such sites can connect with each other, enhancing overall network performance and dependability.
- Provides a comprehensive, end-to-end service level assurance at the carrier level.
Why do businesses need MPLS?
Businesses value speed and reliability when it comes to the internet. Most companies depend on a reliable high-speed connection to share information with their partners, staff, and customers. With the shift toward software as a service (SaaS) applications, leveraging the power of the internet has empowered businesses to become more agile, flexible, and scalable.
As a result, it has also led to organizations adopting multiple sites across different locations, all connected via some form of wide area network (WAN) connection. This invariably leads to management complexity, increased infrastructural cost, and various similar challenges associated with network failures.
Multiprotocol label switching is a core network infrastructure technology that delivers high-performance business internet services. It increases the speed and efficiency of packets traveling through a network by forwarding them according to the fastest route based on the physical path, not just according to logical paths that may be shorter but involve additional hops.
It's the foundation for effective traffic management in the modern data center. Internet service providers (ISPs) rely on MPLS to offer their customers internet connectivity without any loss of service. For businesses to choose an ISP, the provider must offer MPLS as one of its core capabilities. If your company uses MPLS, you can expect true convergence across all your applications.
Suppose an MPLS provider wishes to connect 20 office local area networks (LANs) to establish a corporate WAN for one of its clients. It may opt to do so by combining circuits from five different underlying carriers with circuits from its core network. MPLS allows the provider to conceal the underlying complexity from the client. The client only sees a single network on which to prioritize traffic as they see fit.
An MPLS network provider can also employ MPLS to build a virtual private LAN service by connecting two locations with only a lengthy ethernet cable — no network address translation, IP address, or carrier hubs visible. As far as their client is concerned, getting data from point A to point B is a matter of one hop.
MPLS also includes a fast reroute function that quickly switches traffic to a different path. If the primary channel becomes problematic, traffic can be redirected to a secondary line, reducing the interruption caused by physical circuit failures.
When to use MPLS?
MPLS could be deployed for real-time applications that require speed and reliability. Two popular examples of such applications are voice calls and video conferencing software. MPLS is sometimes used to establish wide-area networks (WANs). WANs based on MPLS are expensive and hard to scale.
Vous voulez en savoir plus sur Solutions SD-WAN ? Découvrez les produits SD-WAN.
How devices communicate with each other
Imagine a place where no one speaks the same language. It’s unlikely that people would communicate very well with each other. Now imagine a networking infrastructure in which no one system can communicate with another. What a disaster, right?
The funny thing is a lot of data surrounds us at all times. Still, without computers and devices that can communicate, it won't be easy to take advantage of this information.
We have many components of our networks speaking their own language (or protocols), making it challenging to communicate efficiently. The good news is that standards are being developed to support native communication across multiple platforms.
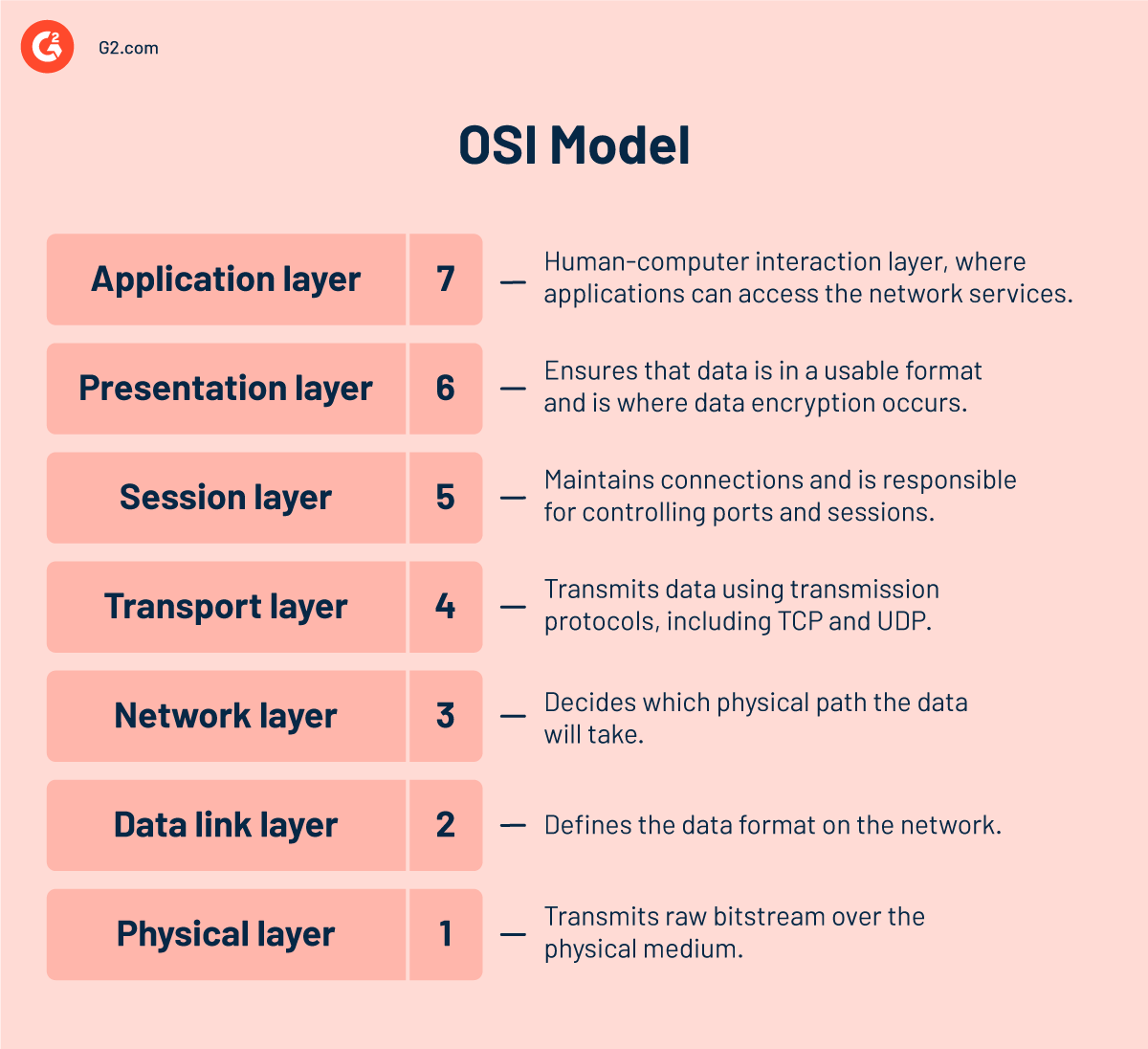
One such standard is the open systems interconnection (OSI) model, which outlines the seven levels computer systems employ to interact via a network.
The OSI model
The International Organization for Standardization (ISO) developed the open systems interconnection (OSI) paradigm, allowing various communication systems to communicate using standard protocols. In simpler terms, the OSI establishes a standard for multiple computer systems to interact with one another.
The OSI Model can be thought of as a universal computer networking language. It's based on the idea of dividing a communication system into seven abstract levels, each of which is layered on top of the previous one. Each layer of the OSI Model is responsible for a certain function and communicates with the layers above and below it.
Although the present internet does not precisely adhere to the OSI Model (instead, it adheres to the simplified TCP/IP paradigm), the OSI Model is still beneficial for debugging network issues.
From top to bottom, the OSI model's seven abstraction levels are as follows:
Layer 7 — application layer
This is the sole layer that interacts directly with user data. End-user applications such as web browsers and email clients employ the application layer. It establishes protocols that enable software to communicate and receive data and present users with helpful information.
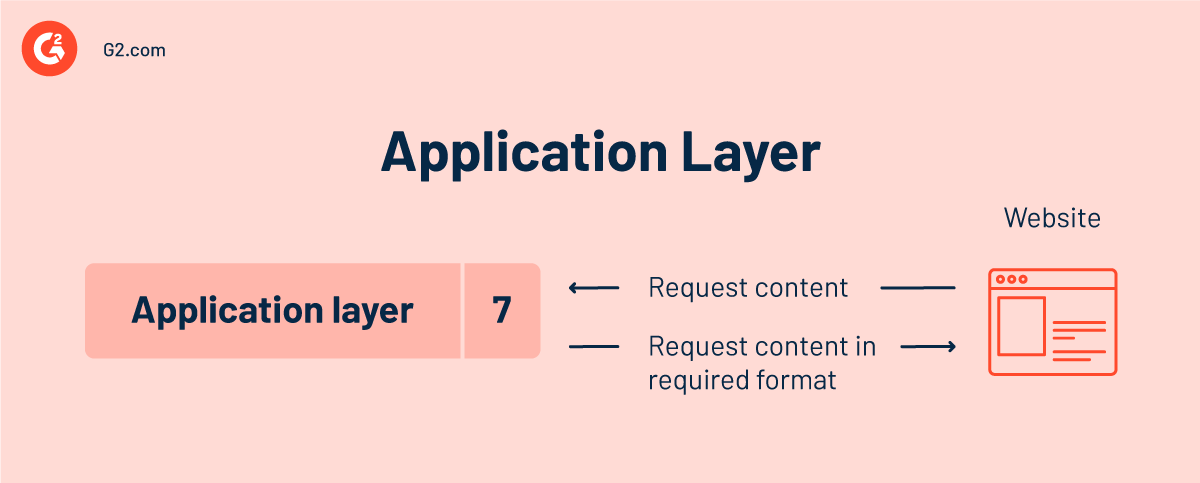
Client software programs are not part of the application layer; instead, the application layer is in charge of the protocols and data manipulation that the software uses to deliver relevant data to the user.
A few examples of application layer protocols are the Hypertext Transfer Protocol (HTTP), Simple Mail Transfer Protocol (SMTP), Post Office Protocol (POP), File Transfer Protocol (FTP), and Domain Name System (DNS).
Layer 6 — presentation layer
The presentation layer is in charge of preparing data for the application layer. It specifies how two or more devices should encode, encrypt, and compress data so that it’s appropriately received on the other end. The presentation layer prepares any information transferred by the application layer for transmission across the session layer.
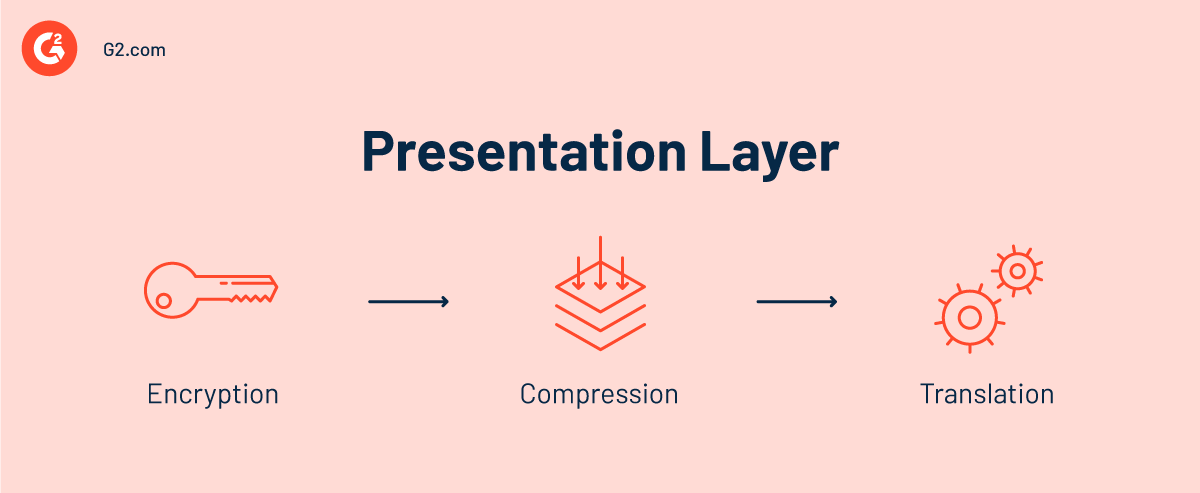
When the devices communicate over an encrypted connection, layer 6 is responsible for adding the encoder at the sender's end and decoding the encoder at the recipient's end to deliver unencoded and readable data to the application layer.
Finally, before the presentation layer is delivered to layer 5, this layer is also responsible for compressing data from the application layer. Reducing the number of data transmitted improves communication speed and efficiency.
Layer 5 — session layer
The session layer establishes communication channels between devices, known as sessions. It's in charge of starting sessions, keeping them open and functional while data is transmitted, and terminating them after communication is complete.
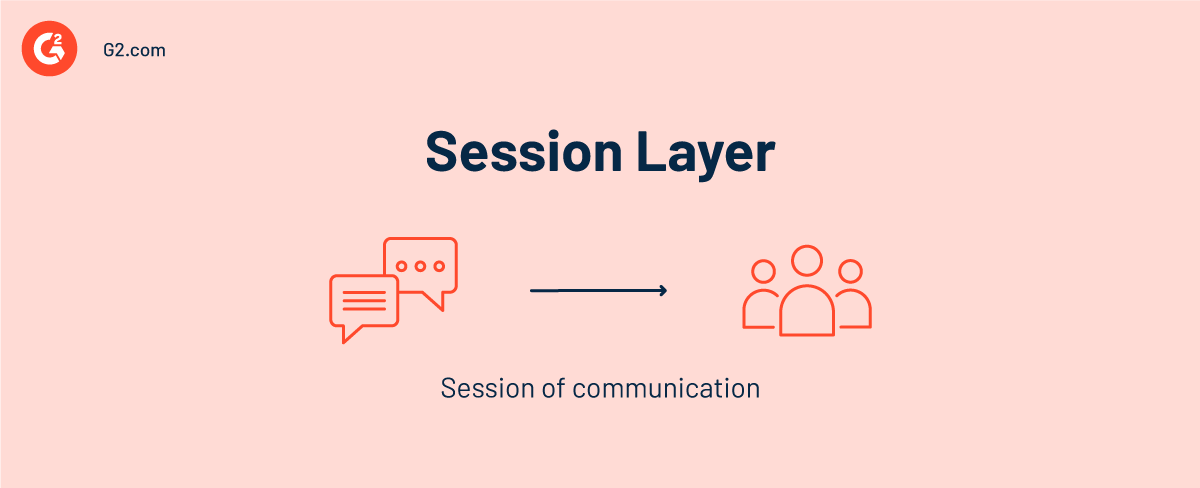
The session layer also syncs data transmission with checkpoints. For instance, if a 100-megabyte file is transmitted, the session layer can establish a checkpoint every 5 megabytes. The session can resume from the last checkpoint when termination or crash occurs following the transmission of 52 megabytes. Only 50 megabytes of additional data must be transmitted.
Layer 4 — transport layer
Layer 4 is in charge of end-to-end communication between two devices. On the transmitting end, the transport layer receives data sent at the session layer and divides it into segments. It reassembles the segments on the receiving end and converts them back into data that the session layer may use.
The transport layer is also in charge of flow control and error control. Flow control finds the best transmission speed to guarantee that a sender with a high-speed connection doesn’t overwhelm a receiver with a slow connection. The transport layer handles error control on the receiving end by checking that the data received is complete and requests a retransmission if it isn't.
Layer 3 — network layer
The network layer is in charge of allowing data flow between two networks. If the two communicating devices are on the same network, the network layer is not needed. The network layer divides segments from the transport layer into smaller pieces called packets on the sender's device, which are then reassembled on the receiving device.
Routing is the process by which the network layer determines the optimal physical path for the data to reach its destination. The network layer employs network addresses (usually IP addresses) to route packets to a target node.
Layer 2 — data link layer
The data link layer is essentially similar to the network layer, except it enables data transmission between two devices on the same network. The data link layer accepts packets from the network layer and divides them into smaller parts known as frames. The data link layer is responsible for flow control and error control in intra-network communication.
This layer is divided into two parts: logical link control (LLC), which identifies network protocols, checks for error, and synchronizes frames, and media access control (MAC), which connects devices and defines authorization to transmit and receive data using MAC addresses.
Layer 1 — physical layer
The foundation layer of the OSI Model is concerned with electrically or optically transporting raw unstructured data bits over the network from the sending device's physical layer to the receiving device's physical layer. This layer is also where the data is transformed into a bitstream, a string of 1s and 0s. Both devices' physical layers must also agree on a signal standard to differentiate the 1s and 0s on both devices.
The physical layer contains physical resources such as network hubs, cabling, repeaters, network adapters, and modems.
Where does MPLS fit in the OSI model?
MPLS is difficult to integrate neatly into OSI architecture. It falls midway between layers 2 and 3. This is because layer 2 devices contain switches, but layer 3 devices include routers. As a result, it's frequently referred to as residing at level 2.5 because it's not a device that enables a data link (layer 2), but it's also not a device like a router (layer 3).
However, because MPLS facilitates data flow like the devices contained in each layer, some opt to give it its own layer, "2.5". It stands "on top of" each node, transferring data packets from one to the next, behaving similarly to a distinct layer in the hierarchy, transporting data from layer 2 to layer 3.
How an MPLS network works
MPLS is not associated with any particular technology; instead, it's an overlay method to improve performance and efficiency.
In traditional IP-based routing, data is transferred through a network in the form of IP packets from one location to another. These packets include the source and destination IP addresses. A packet is routed via multiple intermediate routers, each of which has a routing table. This supplies the packet with the next-hop information before arriving at its destination.
If no route for the packet is discovered in the routing table, the default route is used to send the packet to its destination.
MPLS forwarding differs from IP forwarding in that the forwarding process depends on the label included on the packet instead of IP addresses. This gave rise to the term label switching. MPLS forwarding is multiprotocol because it supports various protocols, including IP, asynchronous transport mode (ATM), and frame relay network protocols.
In MPLS traffic, when a packet joins the network for the first time, it's assigned to a forwarding equivalence class (FEC), which determines how the data packet should be forwarded. This is accomplished by attaching a bit sequence label to the packet. The bit sequence label functions similarly to an address on an envelope, informing the data packet where to travel.
Packets with the same characteristics are assigned the same label and are consequently routed according to the same rules. Each router has a routing table that informs it how to handle those specific packets when the data packet is passed from one router to the next. In this way, data is skipped via short path MPLS labels rather than large network addresses.
When millions of data packets move across the country, some will inevitably experience delays, resulting in latency and poor quality. When data is sent via a more efficient channel and specific set of instructions, the end-user benefits from higher-quality video and audio, as well as faster total transfers.
MPLS labels
One of the many distinguishing features is the usage of MPLS labels. An MPLS header consists of a label, a four-byte (32-bit) identifier that transmits a packet's preset forwarding path in an MPLS network. It's sandwiched between layers 2 and 3 of the OSI paradigm. MPLS labels can also carry information about QoS, such as a packet's priority level.
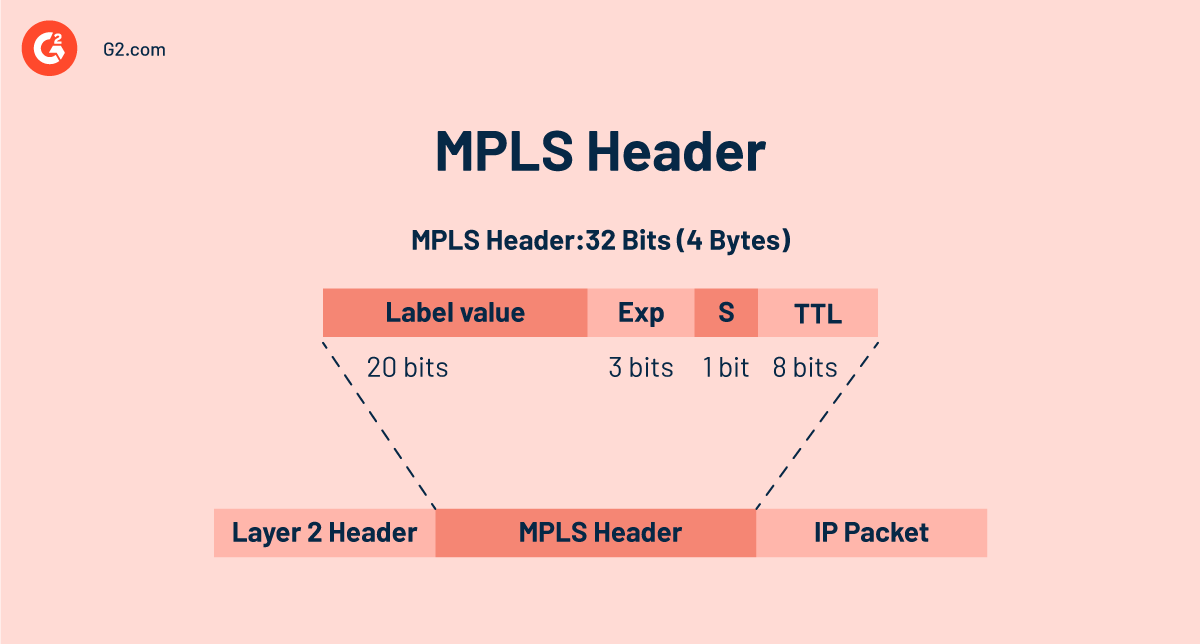
MPLS labels consist of four parts:
- Label value: Because the label field is 20 bits wide, the label may have values ranging from 0 to (2^20) –1, or 1,048,575. The first 16 label values, 0 to 15, are excluded from regular usage since they have a particular significance
- Experimental (Exp): The 3 bits are reserved as experimental bits. They’re used as a measure of QoS.
- Bottom of Stack (BoS): A network packet can contain several MPLS labels layered over each other. A BoS field of 1 bit is used to determine which MPLS label is at the bottom of the stack. The bit is set to 1 only when that label is at the bottom of the stack; otherwise, it's set to 0.
- Time to Live (TTL): The final 8 bits are employed for TTL. It serves the same purpose as the TTL in the IP header. At each hop, its value is simply reduced by one. TTL's duty is to keep the packet from becoming trapped in the network by rejecting it when its value reaches zero.
MPLS routers
The architecture consists of label switch routers (LSRs) to route data packets through the MPLS network. These routers can interpret MPLS labels and receive and send labeled packets.
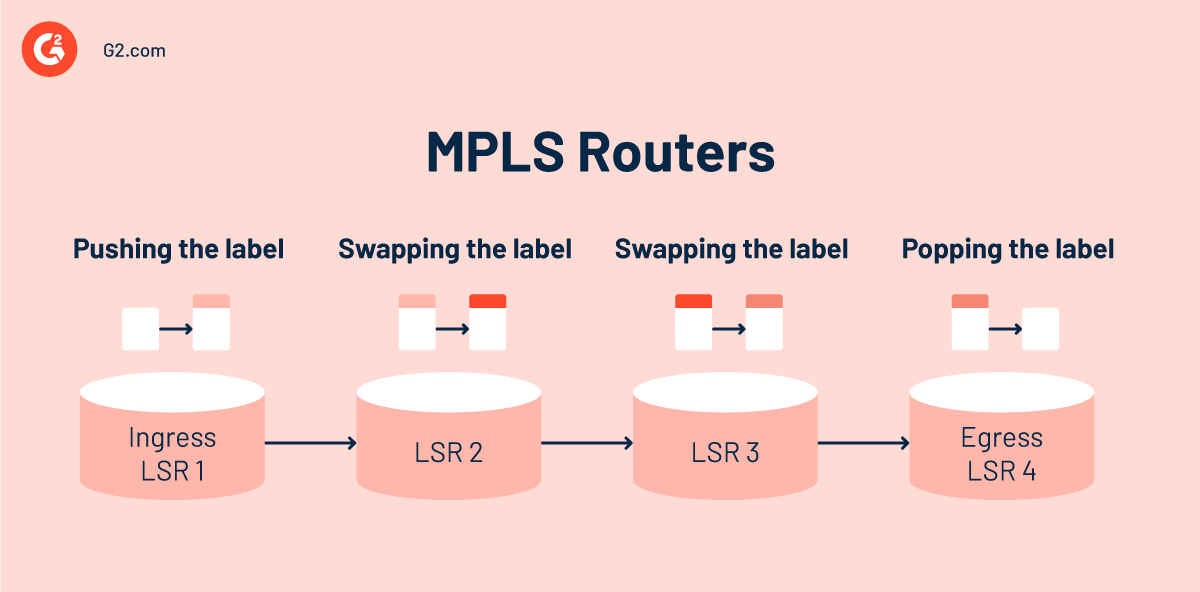
The MPLS network has three types of label switch routers:
- Ingress LSR: These routers are located at the start of the MPLS network. They accept unlabeled IP packets and apply MPLS labels to them. It's also known as the label edge router (LER).
- Egress LSR: Such routers are located at the MPLS network's termination point. They remove the label from the incoming packet and send it as an IP packet.
- Intermediate LSR: These routers are located between ingress and egress LSRs. They receive the tagged packet, swap the label, and forward it to the next hop. These routers are responsible for the MPLS forwarding of data packets.
When a label switch router receives a data packet, it performs one or more of the following actions:
- PUSH: Adds a label to the packet. The ingress router typically performs this action.
- SWAP: Replaces a label in the packet. Intermediate LSRs usually perform this action.
- POP: Removes a label from the packet. The egress router most often performs this action.
What do MPLS routers do with MPLS labels?
MPLS routers use MPLS labels to perform three key functions:- Label switching: Routers use labels to quickly forward packets along predetermined paths without examining the entire packet, enhancing speed and efficiency.
- Traffic engineering: MPLS labels enable routers to manage and monitor network traffic by directing data flows along specific paths, optimizing bandwidth usage, and minimizing congestion.
- Quality of service (QoS): MPLS routers can prioritize traffic based on the assigned labels, ensuring that critical applications receive the necessary bandwidth and low latency for optimal performance.
MPLS forwarding
When a data packet enters an MPLS network, the ingress router applies a label to it. This label relates to a specific path that the packet must take, namely the label switched path (LSP). Different label stacks correlate to different LSPs. The label is disseminated via several protocols, including the tag distribution protocol (TDP), the label distribution protocol (LDP), and the resource reservation protocol (RSVP).
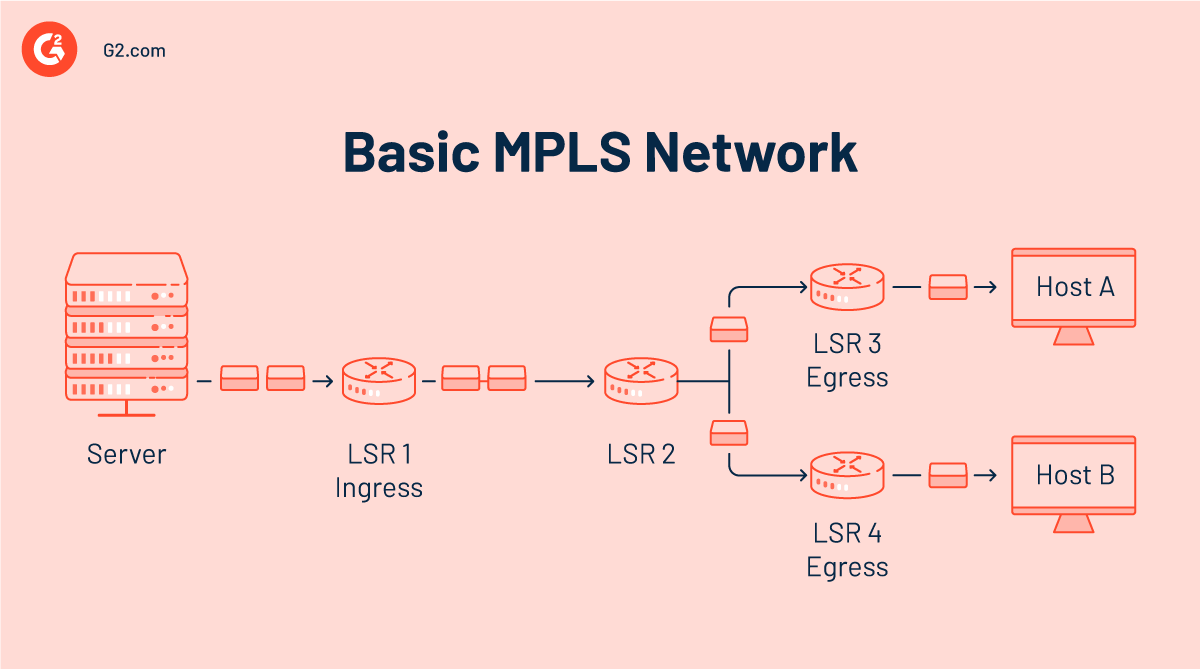
In IP forwarding, each router contains a routing table that commands the system on how the packets are transmitted throughout the network. Similarly, in an MPLS network, each LSR has a label-forwarding information base (LFIB). This information base directs the LSR to switch the label with its equivalent outgoing label, enabling the packet to go over the network.
The key message here is that the router only needs to see the label on top of the incoming packet and is unconcerned with the IP address stored inside the packet, allowing for quicker network routing. The egress LSR pops the packet's label at the conclusion of the LSP, and the data packet is routed as a regular IP packet.
Types of MPLS services
MPLS provides high-speed packet switching, thereby reducing the space and cost of network infrastructure. It has become one of the standard methods of carrying out the core internet protocols such as VoIP, video conferencing, streaming media, and other data in transmission networks.
There are three types of MPLS services:
- Layer 2 point-to-point
- Layer 3 IP/VPN
- Layer 2 virtual private LAN services (VPLS)
Layer 2 point-to-point
Layer 2 point-to-point networking is an inexpensive and more flexible solution to high-bandwidth leased lines. Many retail telecom operators and service providers build their basic network architecture on Ethernet and employ layer 2. This form of transport is protocol-independent, allowing everything that runs on the LAN to be transmitted over the WAN without the need for routers to translate packets up to layer 3.
It's more suitable for organizations that require high bandwidth between a small number of locations.
Layer 3 IP/VPN
Layer 3 IP/VPN solutions are especially suited for large multi-site enterprises, such as retail chains with many low-bandwidth locations or major corporations with global headquarters. They provide the same service guarantees as frame relay or ATM without any permanent virtual circuits (PVCs).
Layer 2 virtual private LAN services (VPLS)
Virtual Private LAN services are becoming increasingly popular for providing Ethernet services. They integrate MPLS and Ethernet, benefiting both customers and carriers. VPLS, also known as transparent Ethernet services, is a newer protocol that operates over MPLS and provides clients with a combination of the benefits of the two network types.
VPLS is popular with TV broadcasters, the financial industry, and media firms due to its simplicity, resilience, and capacity to scale traffic to 10 Gbps.
Benefits of MPLS
Initially, the main advantage of MPLS was that routing lookups were difficult to perform efficiently in software. MPLS substantially reduced latency by reducing these lookups. Although advances in technology have mostly overcome the search problem, MPLS still offers the following benefits:
- Increased performance: MPLS outperforms any previous technology or asynchronous transfer modes, which were meant to accomplish a similar role. ATM first creates virtual circuits between two endpoints, and after the circuit is in place, data is transmitted. This performs well over a public switched telephone network (PSTN) and an integrated services digital network (ISDN), but MPLS performs better with modern IP technology.
- Increased uptime: MPLS increases network uptime due to its mesh topology and Fast Reroute, which allows it to rebound from a mistake in less than 50 milliseconds.
- Improved security: Even though MPLS doesn’t have its own security protocol, it's very similar to a VPN (it's isolated from the public internet). As a result, dangers inherent in the public internet do not affect the system.
- Traffic engineering: MPLS traffic engineering provides fine-grained management over how traffic is routed throughout the network. Thus, the network operator can more efficiently prevent traffic congestion, control line capacity, and prioritize services.
Challenges of MPLS
MPLS is becoming an increasingly popular option for businesses because of its low cost and easy management. It is an attractive alternative to broadband networks, but MPLS services have their limits.
Some of the commonly seen challenges are:
- Vendor dependence: MPLS necessitates the use of a particular carrier to make the system work. If your carrier service falls short of your expectations and you decide to move to another carrier, your MPLS system may be jeopardized, necessitating a redesign, more labor, and lost time.
- Increased cost: MPLS is far more expensive than other technologies, such as broadband. If a company decides to proceed with MPLS, it must conduct a thorough cost assessment to ensure that the advantages outweigh the additional cost.
- Cloud applications: MPLS is solely designed for point-to-point communication. It isn’t ideal for cloud users and doesn’t allow businesses to access their SaaS or cloud applications directly. Just a few cloud services provide this service, but you need to pay a high fee for it.
SD-WAN vs. MPLS
Until recently, the only option to achieve consistent speed and reliable communication between distant business sites was to use pricey MPLS connections despite the availability of low-cost internet services.
Software-defined wide area network (SD-WAN) is reinventing the WAN by establishing a system that dynamically picks the most efficient transport service from a pool of public internet connections and MPLS connections. It offers two primary advantages: cost efficiency and agility.
SD-WAN combines several WAN connections into a single software-defined network (SDN) by utilizing rules, application-aware forwarding, and dynamic link evaluation to pick the best connection for each application. Ultimately, the objective is to provide the appropriate speed and uptime characteristics by leveraging low-cost public internet connections.
SD-WAN and MPLS are sometimes considered different network models, but they aren't directly competing setups; you don't have to choose between the two. SD-WAN is a proven, cost-effective solution for streamlining connections across various endpoints and cloud providers.
If consistency, dependability, and simplicity are essential to you, MPLS could be your best bet. However, if you have more extensive or sophisticated networking requirements, you can combine MPLS and SD-WAN to create a hybrid WAN architecture. The application-aware forwarding benefit of SD-WAN ensures that important traffic, such as VoIP, is routed via your dependable MPLS transport while non-critical traffic is routed over the internet.
Using MPLS and SD-WAN together is a wonderful approach to building your business framework as cloud networking grows and evolves in the near future.
The internet is for the office. MPLS is for business.
MPLS is a very flexible technology that solves a wide range of networking issues. It combines the label-swapping technique associated with virtual circuit networks with IP networks' routing and control protocols to create a network class made for business.
This expands IP networks' capabilities, allowing for more accurate routing management and the provision of various VPN services, among other things.
Learn how software-defined networking (SDN) is changing the way networks are built and operated by reducing cost and increasing functionality.
This article was originally published in 2022. It has been updated with new information.

Keerthi Rangan
Keerthi Rangan is a Senior SEO Specialist with a sharp focus on the IT management software market. Formerly a Content Marketing Specialist at G2, Keerthi crafts content that not only simplifies complex IT concepts but also guides organizations toward transformative software solutions. With a background in Python development, she brings a unique blend of technical expertise and strategic insight to her work. Her interests span network automation, blockchain, infrastructure as code (IaC), SaaS, and beyond—always exploring how technology reshapes businesses and how people work. Keerthi’s approach is thoughtful and driven by a quiet curiosity, always seeking the deeper connections between technology, strategy, and growth.

