À mesure que la technologie devient plus avancée, chaque jour apporte de nouvelles façons de travailler, de jouer et d'interagir les uns avec les autres en utilisant nos appareils.
En même temps, les hackers trouvent de nouvelles stratégies pour pirater ces appareils et voler nos informations à des fins personnelles. À cause de cela, comment pouvez-vous être sûr de prendre toutes les précautions nécessaires pour ne pas être victime d'une menace de sécurité ?
Tout se résume à vos efforts en matière de sécurité numérique.
Qu'est-ce que la sécurité numérique ?
La sécurité numérique fait référence aux outils utilisés pour sécuriser votre identité en ligne, vos données, vos actifs et vos appareils.
Ces outils peuvent être tout ce que nous utilisons pour protéger nos données, comme les logiciels de cryptage, les biométries et les services web. D'autres dispositifs de sécurité numérique incluent la carte SIM de votre téléphone et un passeport électronique, car ce sont des outils que nous utilisons pour communiquer et voyager en utilisant notre identité numérique de manière à la fois pratique et sécurisée. Essentiellement, la sécurité numérique est la façon dont vous protégez votre identité en ligne.
Sécurité numérique vs cybersécurité
Il est courant de confondre la sécurité numérique avec la cybersécurité, il est donc important de noter les différences. La sécurité numérique protège votre présence en ligne, comme votre identité, vos données personnelles et divers actifs.
La cybersécurité va un peu plus loin en couvrant plus de terrain. Elle protège des réseaux entiers, des comptes, des composants numériques et des systèmes informatiques, ainsi que toutes les données stockées à l'intérieur.
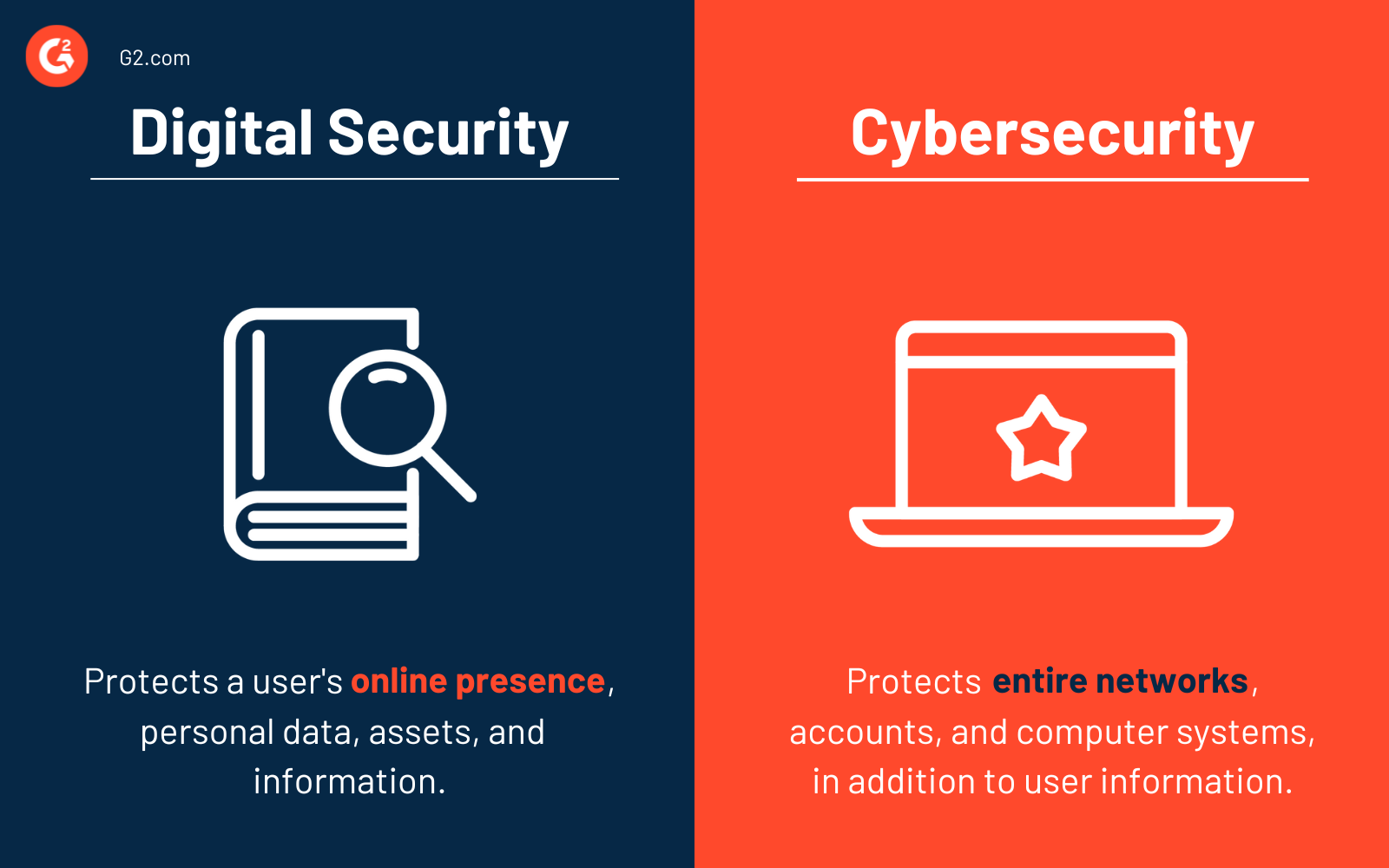
En bref, la sécurité numérique protège les informations, tandis que la cybersécurité protège tous les systèmes, réseaux, infrastructures, et informations.
Quel type de données de sécurité numérique est considéré comme un risque ?
Il existe des informations spécifiques que les hackers de sécurité numérique recherchent pour causer des dommages. Les données les plus à risque sont :
- Données de paiement : Cela inclut tout ce qui concerne les transactions financières, comme les numéros de carte de crédit et de débit, y compris les dates d'expiration et le numéro de vérification de la carte (CVV), les données bancaires en ligne (numéros de compte et de routage), et les numéros d'identification personnelle (PIN).
- Données d'identification : Cela inclut votre nom, adresse, numéro de téléphone, compte email, adresse IP, et numéro de sécurité sociale (SSN). Cela peut également inclure des informations qui localisent votre position. Les données d'identification personnelle sont souvent utilisées pour le vol d'identité et les escroqueries de social engineering. De plus, si un hacker a votre SSN, il peut l'utiliser pour ouvrir des comptes de carte de crédit à votre nom – ruinant votre cote de crédit.
- Données de santé : Cela inclut des informations comme votre historique médical, vos abonnements à l'assurance santé, vos médicaments prescrits, et vos visites chez le médecin et à l'hôpital. Les hackers recherchent ces informations pour déposer de fausses réclamations d'assurance ou revendre des médicaments sur ordonnance.
Les trois piliers de la sécurité numérique
La sécurité numérique repose sur trois piliers principaux. Pour vous en souvenir, pensez à CIA.
1. Confidentialité
Tout d'abord, il est absolument nécessaire de garder vos données et votre identité privées pour éviter une violation de données ou au moins limiter la disponibilité des données à des personnes ou organisations spécifiques.
Tout le monde a des informations qu'il souhaite garder secrètes. Que ce soit vos relevés de compte bancaire, vos numéros de carte de crédit, vos secrets commerciaux, ou même des informations trouvées dans des documents gouvernementaux.
Il existe de nombreuses façons de garder cela confidentiel, de la création d'un mot de passe fort à l'utilisation d'un scanner d'empreintes digitales. Vous pouvez également stocker vos informations via la sécurité du cloud ou investir dans un dispositif de cryptage.
2. Intégrité
L'intégrité garantit que les données que vous gardez confidentielles et sécurisées n'ont pas été modifiées ou corrompues. Vous devez également considérer la source des données. Pouvez-vous être sûr qu'elles proviennent de la bonne personne et que cette personne est bien celle qu'elle prétend être ?
Les hackers ne sont intéressés à voler vos informations que si elles sont correctes. Vous pouvez maximiser l'intégrité de vos données en utilisant des permissions de fichiers, des rôles d'utilisateur et la gestion des accès. Il existe également le contrôle de version pour éviter les modifications incorrectes de vos données. Et, bien sûr, il est toujours dans votre intérêt de sauvegarder toutes vos données et informations sécurisées en cas de corruption.
3. Disponibilité
Enfin, la sécurité numérique doit fonctionner correctement et être opérationnelle à tout moment pour être efficace. Cela se fait en maintenant tout le matériel, en effectuant des réparations matérielles rapidement, et en s'assurant que votre système d'exploitation est exempt de tout bug, ver ou virus.
Connaissez-vous cette mise à jour logicielle ennuyeuse que vous continuez à ignorer en lui disant de "vous rappeler demain" ? Suivre le pilier de la disponibilité signifie qu'il est temps d'installer cette mise à jour, qui peut combler les failles laissées vulnérables aux attaquants.
C'est aussi une bonne idée de tirer le meilleur parti des équipements ou logiciels de sécurité supplémentaires, tels que les pare-feu et les serveurs proxy, pour se protéger contre les temps d'arrêt et les actes malveillants, comme les attaques DDoS.
Méthodes utilisées pour compromettre la sécurité numérique
En ce qui concerne les menaces de sécurité numérique, il existe des méthodes courantes que les hackers exploitent pour mettre la main sur vos données.
- Accès non sécurisé : Les hackers peuvent accéder à vos comptes en ligne et à toutes leurs données en raison de l'utilisation par les utilisateurs de mots de passe faibles ou de leur réutilisation sur plusieurs comptes. Les hackers peuvent également facilement compromettre ces comptes lorsque les utilisateurs n'ont pas configuré l'authentification à deux facteurs.
- Appareils multiples : Ordinateurs portables, smartphones, assistants domestiques et sonnettes intelligentes. Ce ne sont que quelques appareils IoT qui font partie de notre routine quotidienne. Plus il y a d'appareils en usage, plus ils collectent de données, ce qui donne aux hackers accès à plus d'informations sensibles.
- Exposition dangereuse : Pensez à tous les comptes que vous pouvez avoir. Des profils de réseaux sociaux aux services de streaming, ces données permettent aux hackers de se faire une idée de ce que vous faites, qui vous êtes et ce qui vous intéresse. Plus ils sont capables de collecter d'informations, plus il leur est facile de les utiliser à leur avantage.
Comment intensifier vos efforts de sécurité numérique
Que vous soyez un utilisateur régulier ou une personnalité publique, il existe des moyens de renforcer encore plus vos efforts de sécurité numérique.
Couvrez votre webcam
Avez-vous déjà vu des gens taper sur leurs ordinateurs portables dans des cafés ou des aéroports avec du ruban adhésif sur la webcam et vous êtes-vous demandé pourquoi ?
Essentiellement, considérez cela comme une étape de sécurité numérique à haute récompense et faible technologie. Plutôt que de devenir une victime dans cette situation, investissez dans un peu de ruban adhésif de peintre et mettez-le sur la webcam de votre ordinateur portable. Ou, si vous voulez être plus sophistiqué, vous pouvez acheter un cache webcam officiel pour arrêter les hackers dans leur élan.
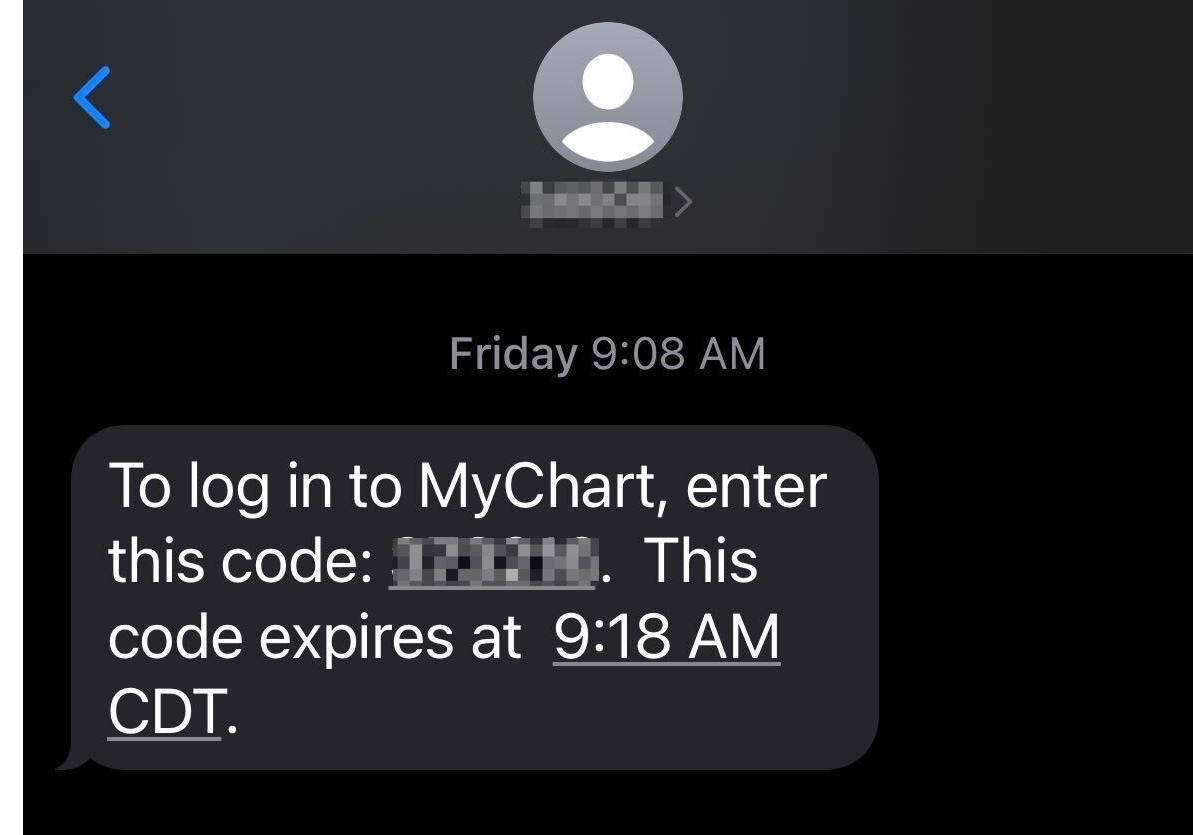
Utilisez l'authentification à deux facteurs
L'authentification à deux facteurs devient de plus en plus courante pour protéger les données et les identités. Cette couche de sécurité supplémentaire est lorsque un site nécessite un mot de passe pour accéder et une autre forme de vérification, comme quelque chose que vous avez.
Un bon exemple est lorsque vous vous connectez à un compte via un mot de passe, puis le compte envoie un code numérique à votre smartphone à taper avant de pouvoir accéder à votre compte. Par exemple, chaque fois que je me connecte à mon portail de soins de santé, l'application m'envoie un code que je saisis avant d'accéder à ces données sensibles.
Appliquez un écran de confidentialité sur les appareils
Quelque chose que nous faisons tous, que nous voulions l'admettre ou non, c'est jeter un coup d'œil à l'ordinateur portable ou au smartphone de la personne à côté de nous lorsque nous sommes en public. Cela se produit lorsque nous sommes dans le train et que nous attendons en ligne, et il devient naturel de regarder l'écran de quelqu'un d'autre de manière décontractée.
Pour empêcher les autres de voir ce qui se trouve sur votre écran, appliquez un écran de confidentialité. Ces couvertures fines rendent votre écran sombre sous certains angles de vue. Lorsque vous utilisez un écran de confidentialité, vous pourrez toujours voir votre écran normalement en regardant droit devant, mais si quelqu'un essaie de regarder en étant assis à côté de vous, il semblera que votre écran est éteint.
Que vous envoyiez un email de travail privé contenant des informations sensibles ou que vous jouiez à un jeu mobile, personne ne le saura.
Il y a un temps et un lieu pour être vulnérable
Tant que cela n'inclut pas votre identité ou vos données. Prenez la sécurité numérique au sérieux et épargnez-vous du temps et de l'argent en évitant d'être piraté. Vous ne savez jamais quand vous pouvez être victime d'une cyberattaque, alors protégez vos données chaque fois que possible.
Renforcez vos efforts de protection de la sécurité numérique en apprenant comment les logiciels d'authentification multi-facteurs peuvent vous apporter encore plus de tranquillité d'esprit.
Cet article a été publié à l'origine en 2019. Il a été mis à jour avec de nouvelles informations.

Mara Calvello
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes content highlighting G2 newsroom events and customer marketing case studies, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.
