¿Qué es un servidor remoto?
Un servidor remoto conecta a los usuarios con sus sistemas informáticos cuando no están en el mismo lugar. Ayuda a las personas a conectarse al servidor interno de una organización sin estar en la red de área local de la empresa.
Las empresas a menudo utilizan servidores remotos para ahorrar costos. Minimizar los costos de instalación de infraestructuras físicas y su mantenimiento. Debido a la fácil escalabilidad de los servidores remotos, las organizaciones pueden ajustar los recursos del servidor, como las unidades centrales de procesamiento (CPU), la memoria de acceso aleatorio (RAM) y el almacenamiento según sus necesidades.
A muchas empresas les gusta usar software de virtualización de servidores, también conocido como hipervisores, para dividir servidores dedicados en instancias virtuales escalables. Ayuda a optimizar la carga de trabajo y la asignación de recursos.
Tipos de servidores remotos
Cada tipo de servidor proporciona propósitos distintos y ofrece ventajas únicas. A continuación se presentan algunos tipos comunes de servidores remotos.
- El servidor Windows ejecuta el sistema operativo (OS) de Windows. Aunque no es de código abierto, las organizaciones generalmente prefieren los servidores Windows debido a su interfaz fácil de usar y su compatibilidad con numerosas plataformas de software.
- El servidor Linux opera en un sistema operativo Linux, como CentOS o Ubuntu. Debido a su naturaleza de código abierto, los servidores Linux se utilizan ampliamente para la computación en la nube. Linux, Apache, MySQL y Hypertext Preprocessor (PHP) (LAMP). Las aplicaciones de pila LAMP normalmente se alojan en servidores Linux
- El servidor Unix ejecuta una versión de Unix (un sistema operativo desarrollado como una alternativa a Linux). Soporta multitarea y múltiples usuarios. Las instituciones académicas y las empresas lo prefieren.
- Servidores mainframe realizan actividades complicadas que involucran grandes cantidades de datos. Las grandes empresas, incluidas las firmas de telecomunicaciones e instituciones financieras, dependen comúnmente de estos servidores debido a su rendimiento robusto y altamente confiable.
Métodos de acceso a servidores remotos
Comprender los métodos para acceder a servidores remotos es esencial para una gestión efectiva y manejo de datos. A continuación se presentan algunos métodos estándar comunes entre los profesionales.
- Secure shell (SSH) es una forma segura de acceder a la línea de comandos de un servidor. Esto es generalmente para servidores Linux y macOS.
- Protocolo de escritorio remoto (RDP), utilizado principalmente para servidores Windows, proporciona una interfaz gráfica para controlar sistemas de forma remota.
- Protocolo de transferencia de archivos (FTP) mueve archivos entre una máquina local y un servidor. Secure FTP (SFTP) es su versión segura.
- Una red privada virtual (VPN) crea una conexión segura a una red, dando acceso al servidor como si el usuario estuviera en la red local.
- Telnet es un método más antiguo, un poco menos seguro que SSH, utilizado para el acceso a la línea de comandos.
- Paneles de control basados en web proporcionan una interfaz web para gestionar funciones del servidor.
- Computación de red virtual (VNC) ofrece características de compartir escritorio gráficamente. Es similar a RDP, pero se utiliza para diferentes tipos de sistemas.
- Acceso directo a la consola proporciona acceso físico al servidor, generalmente en un centro de datos, con un teclado, ratón y monitor.
Capacidades de los sistemas de gestión de servidores remotos
Un sistema de gestión de servidores remotos proporciona a los usuarios las herramientas para gestionar y administrar servidores de manera eficiente en entornos remotos o distribuidos.
Algunas de las capacidades y características críticas son:
- Gestionar la salud y el rendimiento. Los administradores pueden supervisar la salud y el rendimiento del servidor, incluyendo el monitoreo del uso de la CPU, la utilización de la memoria, el espacio en disco y la actividad de la red.
- Configurar cuentas y seguridad. Los administradores crean, modifican o eliminan cuentas de usuario en servidores remotos, estableciendo permisos y derechos de acceso. Un sistema de gestión de servidores remotos también proporciona herramientas para configurar configuraciones de seguridad como reglas de firewall y cifrado.
- Minimizar vulnerabilidades. El sistema de gestión de servidores remotos asegura que los servidores ejecuten las últimas aplicaciones y parches de seguridad. Esta capacidad reduce las vulnerabilidades, mejora el rendimiento del servidor y apoya el mantenimiento continuo del software.
- Centralizar el control y la automatización. Los equipos gestionan múltiples servidores remotos desde una única consola, simplificando los procedimientos de trabajo y aumentando la eficiencia. Un sistema de gestión de servidores remotos también admite la creación de scripts y la automatización, permitiendo a los administradores automatizar tareas repetitivas y crear scripts de gestión personalizados.
Proceso de implementación de la gestión de servidores remotos
Las organizaciones pueden establecer sistemas de gestión de servidores remotos siguiendo los pasos a continuación.
- Decidir. Considerar las opciones disponibles e identificar los sistemas que mejor apoyen las necesidades de los usuarios.
- Preparar. Configurar la infraestructura para aplicar la solución de gestión remota.
- Desplegar. Instalar y configurar múltiples sistemas utilizando plantillas predefinidas después de completar todos los requisitos previos.
- Integrar. Incluir las herramientas de gestión existentes, procedimientos y flujos de trabajo. Sincronizarlos con la solución de servidor remoto.
- Implementar. Crear cuentas para los usuarios e instruirlos sobre cómo utilizar el sistema después de una implementación exitosa.
Mejores prácticas para la protección de servidores remotos
La protección de servidores remotos es crucial ya que ayuda a mantener la confidencialidad, integridad y disponibilidad de los datos en servidores remotos. Siga estas mejores prácticas para garantizar la seguridad.
- Usar firewalls. Implementar un firewall sólido para filtrar el tráfico de la red. Esto ayuda a bloquear el acceso no autorizado y las amenazas potenciales.
- Aprovechar la autenticación de clave SSH. Usar claves SSH en lugar de contraseñas. Esto añade una capa extra de protección, ya que las claves son más difíciles de descifrar.
- Actualizar regularmente. Mantener actualizado el sistema operativo y el software del servidor. El software desactualizado es vulnerable a los exploits.
- Usar políticas de contraseñas fuertes. Imponer políticas de contraseñas fuertes. Cada usuario debe elegir una contraseña compleja que cambie regularmente.
- Desplegar un sistema de detección y prevención de intrusiones (IDS). Usarlo para monitorear el tráfico de la red en busca de actividades sospechosas. Optimizarlo para alertar al usuario en caso de posibles brechas de seguridad.
- Adoptar un control de acceso estricto. Limitar el número de usuarios con acceso remoto y otorgar solo los permisos necesarios.
- Cifrar datos. Usar el protocolo seguro de transferencia de hipertexto (HTTPS) para cifrar los datos en tránsito.
- Segmentar la red. Segregar el servidor en diferentes segmentos de red para limitar el impacto de cualquier brecha. Usar una zona desmilitarizada (DMZ) para servicios accesibles públicamente.
Servidor remoto vs. servidor local
Es común confundir un servidor remoto con un servidor local, pero los dos tienen diferencias clave.
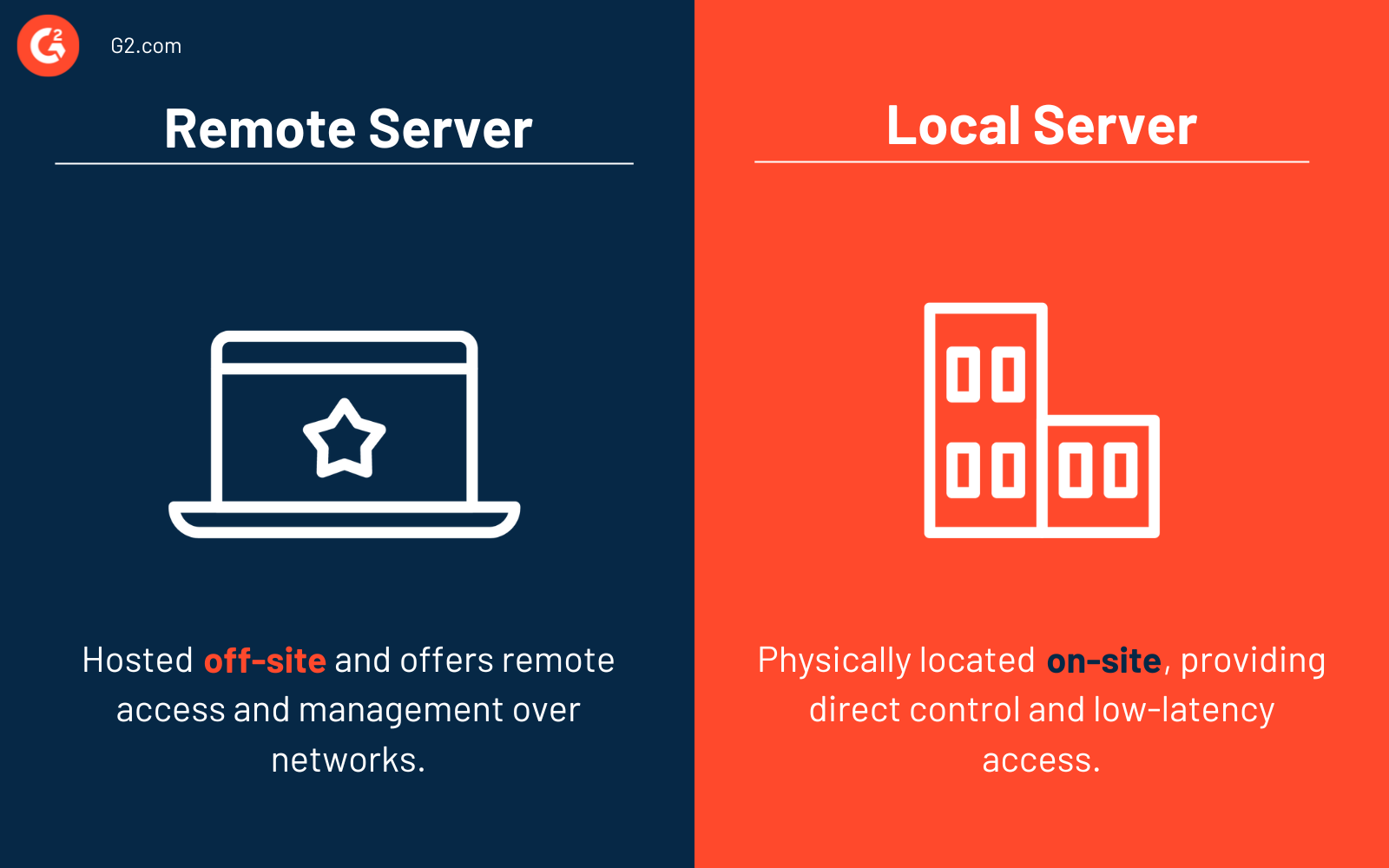
Los servidores remotos están alojados fuera del sitio y ofrecen acceso y gestión remotos a través de redes. Son mantenidos por proveedores externos, ofreciendo escalabilidad y accesibilidad desde cualquier lugar. Sin embargo, implican costos recurrentes y dependencia de proveedores de seguridad.
Los servidores locales están ubicados físicamente en el sitio, para control directo y acceso de baja latencia. Necesitan inversiones en hardware, mantenimiento regular y seguridad.
Aprende más sobre los sistemas de detección de intrusiones (IDS) y comprende por qué son importantes para la seguridad de los servidores remotos.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.