Everyone wants to keep their information safe.
In today’s internet age, keeping all of your private information secure and away from hackers takes serious effort. Your personal information seems to be public domain. All of your data, login details, and private information are at risk now more than ever. On top of that, there are plenty of email scams floating around the web that can trick you into coughing up your sensitive information.
Phishing and spear phishing are two of the most common types of cyberattacks. For the sake of this article, we’ll need to define the latter.
What is spear phishing?
Spear phishing is an email scam targeted towards an individual, a business, or an organization to steal personal data such as financial information or account credentials.
No matter if your data is personal or business-related, keeping a ‘better safe than sorry’ mindset is the best way to protect yourself and your business. When it comes to data security, it’s important to be proactive before you have to be reactive. Implementing a thorough cyber security plan is a great example of saving yourself before any attacks can occur.
Spear phishing vs. phishing
The terms phishing and spear phishing are often used interchangeably, but this is incorrect. There is a difference between the two, even though it’s slight. The reason why these two terms are mixed up so often is because both of their purposes are to acquire sensitive information from users.
To be clear, even though the two terms are different, spear phishing is technically a subset of phishing. You could call a spear phishing attack a phishing attack but not the other way around.
Phishing attacks
Phishing is a broader term that encapsulates any attempt to scam victims into giving out their sensitive information. It usually doesn’t take a lot of expertise to execute a huge phishing campaign. Most phishing attacks are one-and-done ordeals, hoping to fool you into giving up information like your credit card data or usernames and passwords. They go after a large number of low-yield targets and are typically less damaging than spear phishing attacks.
Phishing attacks are not personalized to a specific user. Rather, the attacker will send out an email to a mass amount of people at the same time. Phishing attacks can have a couple of different goals. Attackers can be after personal information like social security numbers or bank details to commit identity theft. They may aim to mine business data to gain access to confidential accounts and credentials. Lastly, they can use malware or viruses to corrupt your computer and steal your personal data.
¿Quieres aprender más sobre Software antivirus? Explora los productos de Antivirus.
Spear phishing attacks
Spear phishing, on the other hand, is a phishing method that targets a specific individual, company, or group of employees within that company. Unlike phishing attacks, spear phishing attacks require much more thought and time to achieve. They require highly advanced hacking skills and in-depth details on the targeted victim(s).
Attackers aim to gather as much personal information about their victims as possible in order to make their message appear more convincing. This is why it takes much more time to craft a spear phishing email. The more information an attacker can dig up on the victim, the more convincing they can be in the spear phishing message.
Did you know: 71.4% of targeted attacks and data breaches involved the use of spear-phishing emails?
From this single statistic alone, it’s clear that email users are the main target as well as the weakest link when it comes to information technology security.

These messages are written to specifically address the individual victim and no one else. The attacker disguises themselves as a trustworthy entity, often someone the victim knows personally, in an attempt to boost their chances of procuring personal information from the victim. This technique is usually after more confidential data like business processes, personal identity information, company secrets, or the company’s financial details.
Although phishing attacks began in the mid-1990s as Nigerian prince scams, over time they have evolved into incredibly detailed and targeted campaigns that are highly effective and challenging to stop.
One way to protect yourself is to implement data loss prevention (DLP) software. This software is used to secure control and ensure compliance of sensitive business information. A key component of DLP solutions is distribution control, which ensures users do not send private information outside of corporate business networks.
How does spear phishing work?
Spear phishing usually targets enterprises, as a large majority of their data is available online which can be mined easily and without suspicion. Attackers can browse the company website and find their jargon, their partnerships, events they attend, and the software they use. On the other hand, attackers can find more personal details like a victim’s location, job responsibilities, and their colleagues by looking at their social profiles.
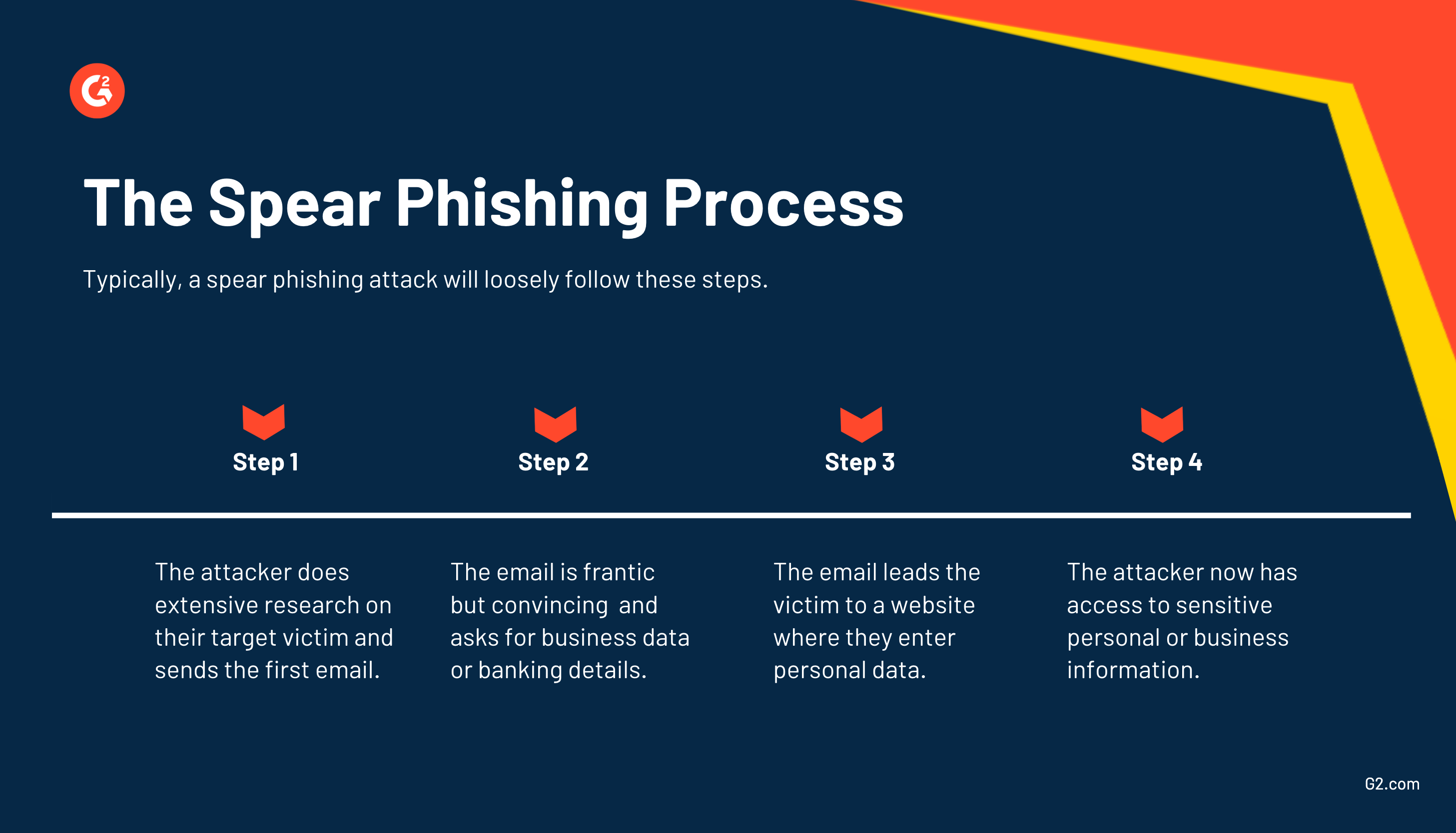
The spear phishing process
No matter if the attacker is out to steal someone’s identity or trying to gain access to business data, they collect as much information about their victim to be as deceiving as possible. After doing the research, the attacker can sprinkle the message with specific names, terms, or places to make it more convincing. Spear phishing is so successful because it feels familiar.
A spear phishing email will be sent from a familiar and trusted source like Google or PayPal. If an attacker discovers that their victim regularly uses PayPal to send money to friends and family, they can disguise themself as a PayPal bot and ask them to change their password. An unknowing victim won’t think twice about it and suddenly, their credit card details are compromised.
To start, spear phishing attackers usually target people who willingly share personal information on the internet. Just from browsing a social profile, attackers may be able to find someone’s email address, geographic location, their entire network of professional connections, and any posts about recent purchases they made. With these details, attackers can act as a friend or a familiar brand the victim trusts and craft a personalized email that sounds and looks eerily authentic.
Additionally, to increase the chance of getting information from the victim, these messages will often have urgent explanations on why they need this information. Targeted victims may be encouraged to click on a malicious attachment or click on a dummy link that leads them to a spoofed website where they may be asked to enter passwords, usernames, account numbers, or PINs. These websites can also contain malware that will infiltrate the victim’s computer as soon as they click the link.
An attacker acting as a friend may fool a victim by asking for social passwords (Ex: their Facebook password) to gain access to certain photos or videos. In reality, when given the password, the attacker will use it (and variations of it) to attempt to log into other websites that contain sensitive information such as credit card numbers or health records. Once these attackers have one password, it is infinitely easier to access other websites and accounts or even create an entirely new identity with their victim’s information.
The process typically goes like this: An email is received, appearing to be from a trustworthy source. The message is frantic, requesting that you send back personal information or even banking account details. Because the attacker did their research and included information like colleagues’ names or a frequently visited location, the receiver will believe the message is from a trusted individual. If all goes to plan, the message directs the victim to a falsified website crawling with malware. The attacker is in and now has access to sensitive company data.
You may think you’re smart enough to detect which emails are legit and which are bait, but you can never be too safe. It’s important to brush up on the ways you can easily spot a spear phishing email.
What is whaling?
When dealing with spear phishing emails, you may do a bit of research and come across the term ‘whaling’. Spear phishing attacks that target high-level executives, politicians, or celebrities are commonly referred to as whaling attacks. These emails most often involve the attacker impersonating a CEO (or another important executive) with the goal of using that high title to convince the victim to share confidential information, discuss company secrets, or make payments without question.
Whaling attackers will masquerade themselves with an executive’s title, position, or phone number which can all be found on social media accounts, press releases, or the company website.
A whaling experiment was conducted that targeted CEOs alone. When all was said and done, a whopping three-quarters of them were fooled by the simulated messages.
Other terms that you should know include smishing and vishing.
- Smishing: attacks sent over text messaging
- Vishing: attacks conducted through phone calls
4 ways to identify spear phishing emails
Although spear phishing emails are extremely targeted and convincing, there are a few key factors that will set them apart from your normal run-of-the-mill email.
1. Incorrect email address
The most obvious red flag is an incorrect email address (or one that is close to a familiar address, but still different). The trick here is that email addresses can be spoofed easily or may not be noticeably different without super close inspection. Normally, the email will have a typographical error or one misplaced letter/number that doesn’t stick out at first glance. For example, instead of a lowercase “L”, an attacker may use an uppercase “i”.
2. A sense of urgency
Another common red flag in spear phishing emails is a sense of urgency. The sender may need instant access to a company account claiming something along the lines of “I’ll need access to (x) account by 11 am today. If you could send the login details over, I’d really appreciate it.”
This sense of urgency is often paired with the desire to break company rules. The sender may want to gain access to company software and forget all normal policies and procedures.
3. They instill fear
Attackers may take a more evil route and instill fear into the heart of their victim by using emotive language. They can act as a C-level executive and tell you they need credentials to a certain account or money for a business expense, and if you don’t comply, you’re letting them down.
4. Unfamiliar terminology
Many companies have common terminology or lingo they use internally. Whether it’s a common phrase across one department or the term employees use to address upper management, company lingo is highly personal and typically only used at that company alone.
A handy way to determine if you’ve received a spear phishing email is if this lingo is missing when it would normally be there. Of course, not every business email will contain customized terminology, but if your department always uses the term “account statement” and the sender uses “financial statement” instead, it doesn’t hurt to be cautious and double-check with the sender.
Another example of this is when you receive a company-wide email from the CEO. If they always sign off with “All the best” and they suddenly use “Cheers”, it should trigger alarm bells.
Spear phishing examples
An attacker could be after one person (like a CEO) or after an entire company. There are a handful of tactics that spear phishing uses and some of the most common include CEO impersonation and the inclusion of a malicious link. The first spear phishing example we’ll look at is a CEO fraud email.
CEO fraud
This employee received an email from an attacker pretending to be their CEO. Often these emails are designed to trick employees into handing over data or other sensitive information. The fear the employee has of angering someone higher up in the company is what makes this scam so effective.
The professional tone and subject line of this email could fool any unsuspecting employee. If they’re not careful, the employee would have sent it to their manager or even the CFO and furthered the problem. This is why educating your team about phishing emails is so important.
Malicious email link
Most phishing emails contain a malicious link. In this example, an employee received an email from an attacker posing as someone from their company’s IT department. The attacker did thorough research and was able to dig up which services they use and how to best impersonate “Amy Lee”.
At first glance, the email address seems legit and the tone of the message is rather professional. The attacker tells the employee that the company will be transferring data from one program to another. If they clicked on the link, the employee would be directed to a fake website where they’d be prompted to create an account and enter personal information.
At the end of the day, the best way to prevent attackers from gaining access to your sensitive information is to refrain from clicking on any links within emails.
How to avoid spear phishing
No matter if you’re an associate or the chief financial officer, spear phishing attackers can choose you as their next victim to gain access to your personal data or your company’s sensitive information. Here are some top tips to defend yourself and your company against spear phishing attacks:
Be cautious before clicking
- Hold back from clicking on links or downloading attachments from unknown emails.
- To be safe, always check the sender’s email to confirm you’re speaking to someone you trust.
- Be cautious of emails (from colleagues or strangers) that use an urgent tone. If you want to confirm the email is from the correct person, call or message them on another social network to verify the message’s validity.
- Encourage all employees to report any potential phishing or spear phishing emails so that your team can stop attacks in their tracks.
- Never send out personal information (especially financial or confidential) via email. If you are sent an email asking for this info, save yourself the risk and go straight to the source to verify the message is real.
Prepare yourself beforehand
- Enlist the help of two-factor authentication. By doing so, you’ll help secure logins to sensitive applications by demanding users enter two pieces of data instead of one. This is usually the normal password and a code that is sent to the user’s phone or computer. When you use 2FA, even if an employee’s password is compromised, it won’t be of any use to the attacker without the second code that will only be sent to the employee.
If you’re looking for extra protection against potential hackers, frequently backing up your data is your best bet. Backup software offers protection for business data by storing data in case of user error, corrupt files, or physical disasters. Take a look at the top backup software tools and find the best fit for your company’s needs. - Have smart passwords. Every password you create (especially for business accounts) should be completely different from the others. Attackers can crack the code much easier if all of your logins are variations of one password.
Related: A little freaked out? Rethinking all of those passwords from high school? Discover how to create a strong password and rest easy tonight.
- Send a message to the company about the dangers of phishing emails. Additionally, you can hold a session that explains what should and should not be shared online to keep the company as protected as possible.
- Implement a data loss prevention tool for your company.
- Install hosted email security and anti-spam protection to set the first line of defense.
Don't take the bait
The first line of defense to protect yourself against scammers and hackers is to educate yourself on the best practices in cyber security. If you’re a C-level executive, it’s especially important for you to recognize the warning signs, and quickly. Your safety relies on your dedication to doing your own research.
If your business is targeted, it can take months, even years to recover from a cyber attack. Now that you’ve read up on what spear phishing is, you’ve seen a couple of examples, and you’ve discovered how you can best protect yourself, you’re well equipped to prevent any future attacks.
Want to learn more? Discover the best practices you can use to boost your company’s data security.

Alexa Drake
Alexa is a former content associate at G2. Born and raised in Chicago, she went to Columbia College Chicago and entered the world of all things event marketing and social media. In her free time, she likes being outside with her dog, creating playlists, and dabbling in Illustrator. (she/her/hers)