You have business accounts, therefore you have usernames and passwords...for now.
If you’re like me, you use a password manager to keep track of all these usernames and passwords. I counted mine; I have 184 accounts (that I know of, at least). That is still below average. The average employee manages 191 passwords, according to a 2017 study by LastPass.
Even with stellar password practices, such as using a unique password for every account (who are we kidding though), passwords get hacked. Poor password and authentication practices lead to (even more) phishing attacks on employees and their businesses.
In fact, stolen credentials and phishing were the top cyberattack vectors in 2019, according to a report by Verizon. Additionally, according to the Ponemon Institute’s 2019 report, 44% of respondents have experienced a phishing attack at work (emphasis my own). Even worse, 57% of those respondents who experienced a phishing attack have not changed their password behaviors.

Is securing accounts with only passwords...secure?
Passwords are the most basic type of authentication, but are not sufficient to secure accounts on their own. Why? Because passwords get hacked, and passwords are at the heart of most data breaches.
In the last couple years, cybercrime statistics have reported sobering numbers about hackers’ impact on businesses. For example, according to a 2018 Cisco study, 74% of privacy-immature companies experienced a cyber loss of over $500,000 in the prior year, while only 39% of privacy-mature companies did. Passwords remain a top attack vector for cyber criminals, whether they use known hacked password directories, dictionary hacks, keylogging, or phishing scams to get users’ passwords.
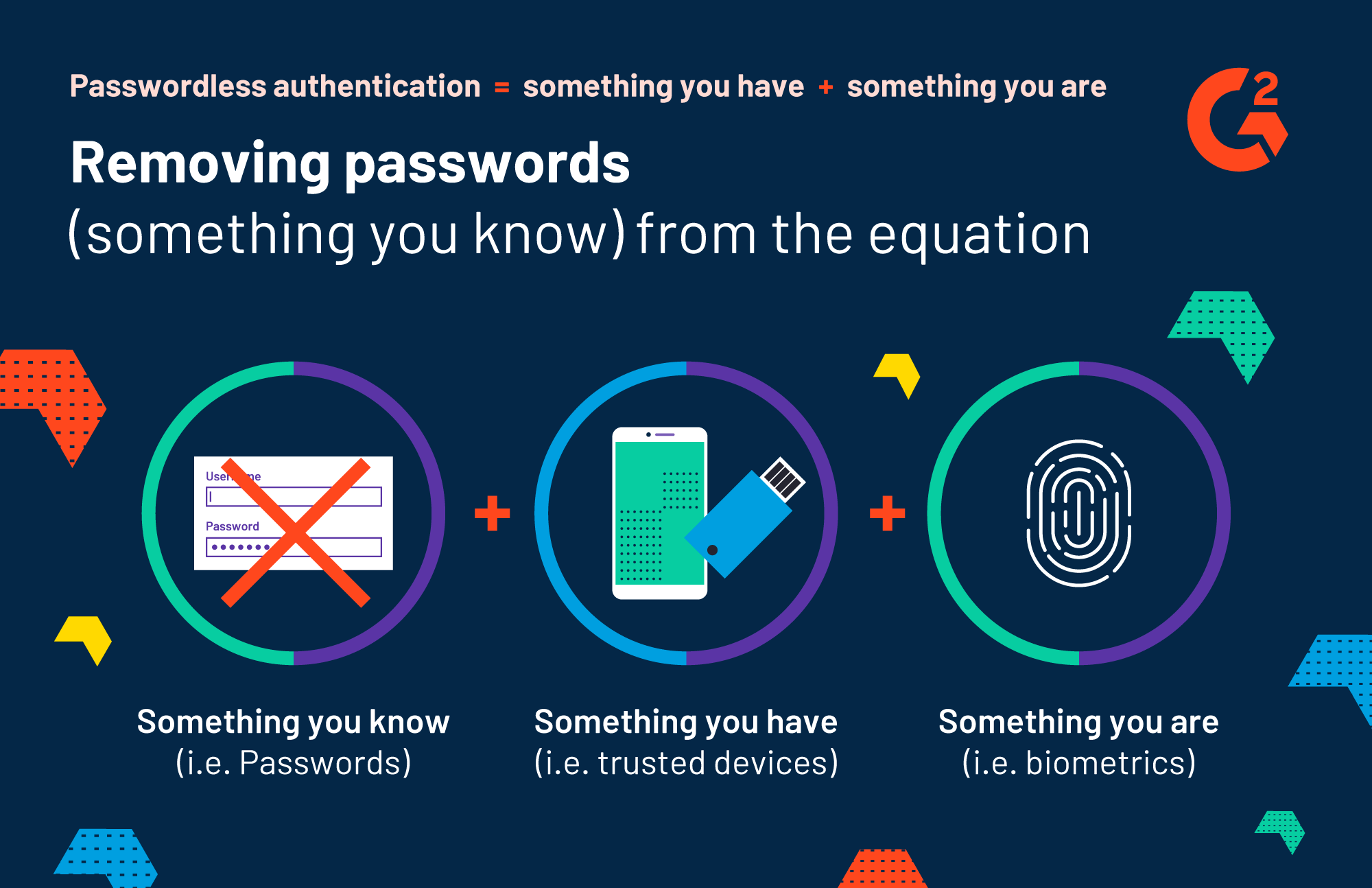
So if passwords are unsecured, can we stop using them? You might be surprised to hear...yes. Yes, we can stop using passwords by using other kinds of authentication. This is known as passwordless authentication.
Below you will find information on different ways users authenticate today and how that contrasts with passwordless authentication. Read more below about real-world use cases, and why companies are going passwordless.
What is authentication?
Authentication is the process of verifying that users are who they say they are. Authentication requires users prove their identity in one or multiple ways before access to an account is granted. Authentication can include a combination of factors such as something you know, something you have, something you are, somewhere you are, when you access an account, or something you do.


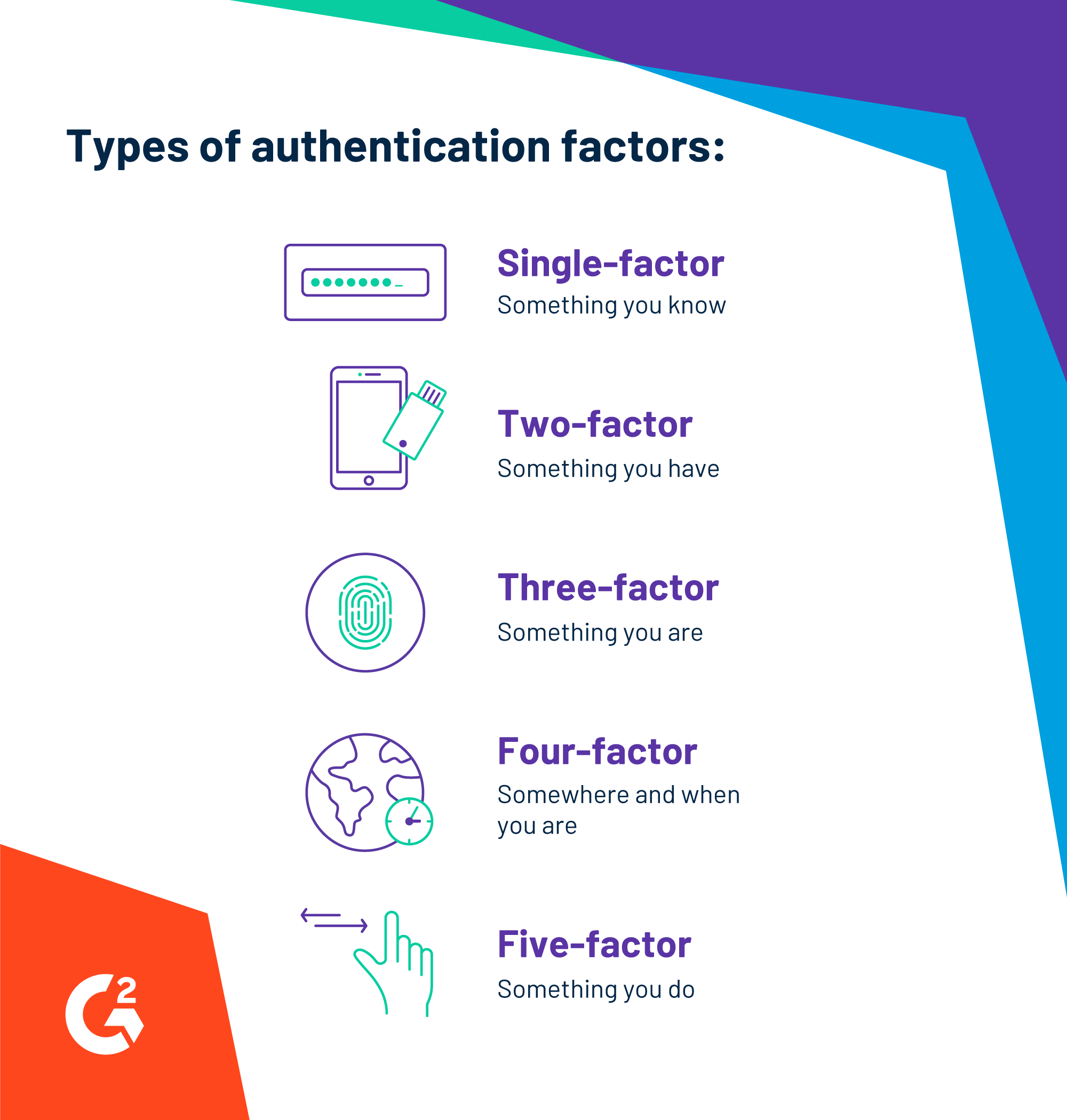
What is passwordless authentication
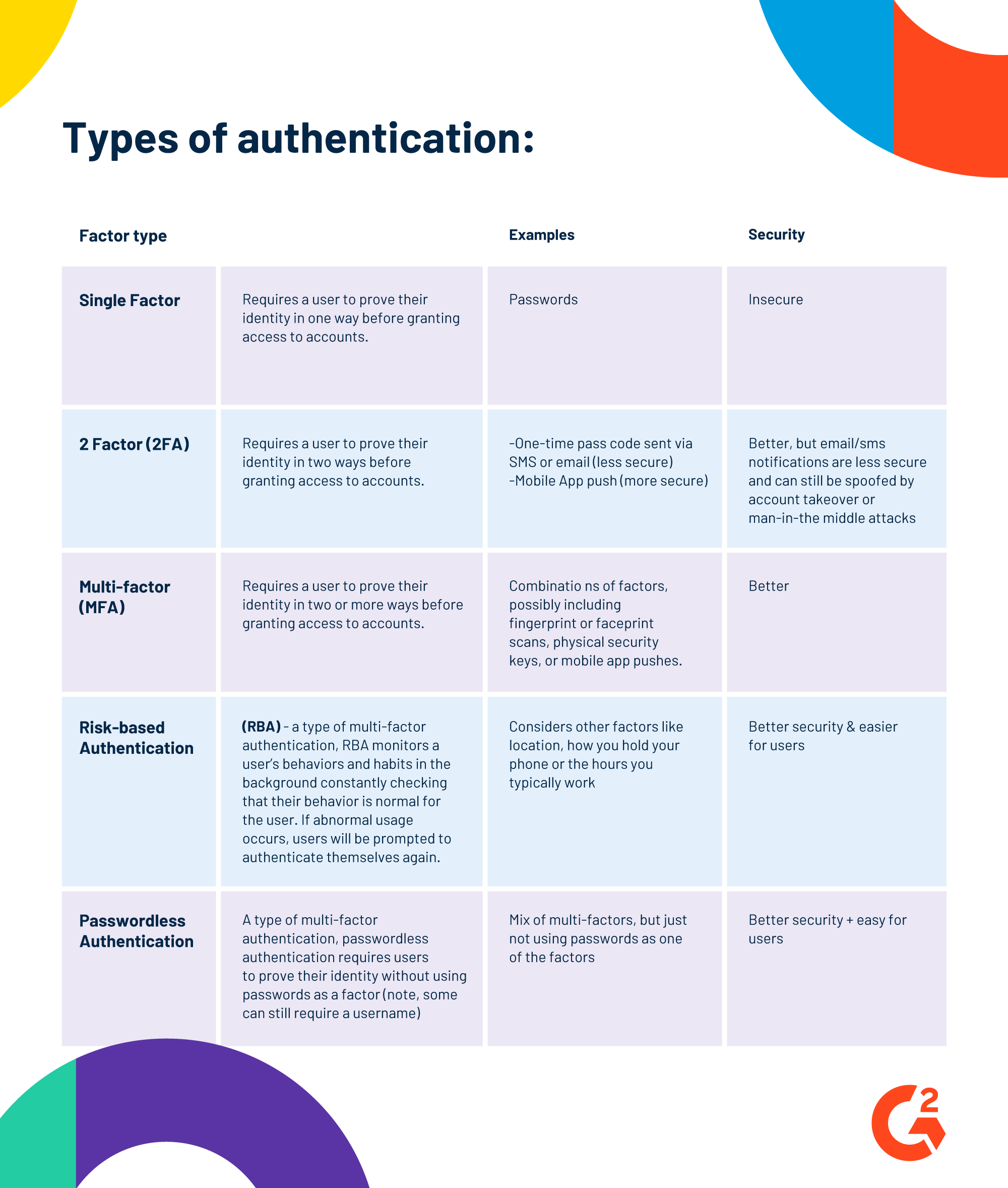
Passwordless authentication is a form of multi-factor authentication (MFA) that relies on authentication factors outside of passwords to grant users access to an account. For example, passwordless authentication eliminates the factor of something a user knows (a password) and instead authenticates a user using something they have (such as a trusted mobile device or a physical security key) and something they are (like their fingerprint or face print).
Passwordless authentication in practice
There are a few common use cases involving employee experiences, customer experience, and high-risk transactions.
Let’s start with common employee use cases. Say an employee comes to work and sits down to her laptop on the company's corporate network. When she types in her username to sign in, she gets a notification to insert her physical security key into her computer’s USB drive. She presses the button on the security key and her laptop is unlocked. No password is typed.
What are physical security keys?
Physical security keys are hardware authentication devices that restrict user authentication to the real world. Physical security keys come in many forms, commonly as USB drives that require users to insert it into their computer or smart cards with near field communication (NFC) functionality that requires the key to be close to the user’s device. Physical security keys support authentication via one-time passwords, public-key encryption and authentication, and FIDO standard protocols.
For a customer use case, the passwordless authentication scenario is similar. Let’s use the example of a hotel customer wishing to change his hotel reservation dates. The customer downloaded the hotel’s mobile app on his mobile phone. When he accesses his hotel account, he types in his username, but not a password. A push notification is then sent to his phone via the mobile app. He authenticates his identity by scanning his fingerprint (the biometric data is stored locally and authenticated on his own device, not on a company’s servers). From there, he can change his hotel reservation. In this scenario, there are no passwords or other knowledge-based challenge questions to answer, such as “What is your mother’s maiden name?” or other questions that can easily be accessed by hackers.
Lastly, there are high-risk transaction use cases, such as transferring large sums of money from a bank. The amount of authentication needed is determined by risk. For example, if a user needs to sign in to an account to check their bank balance from their computer, a push notification to their mobile device secures that customer. However, if a user initiates a large wire transfer, additional authentication might be required. In that case, a user may need to verify the wire transfer on their mobile device and confirm the transaction on their computer. After this, a facial recognition authentication might commence on their mobile phone app. Finally, the bank can release the wire transfer. In this case, no passwords facilitated the transaction. Additionally, there are no unsecured authentication methods—such as SMS or email codes sent to the customer—either.
There are three main ways to store biometric data like fingerprints or faceprints:
- Device-centric storage: stored on a user’s own device like a mobile phone
- Server-centric storage: stored on a company’s centralized servers
- Distributed storage: partial pieces of a user’s biometric data are stored separately on both the end user’s device and a company’s centralized server and merged when a user authenticates
Note that mobile phones, tablets, smartwatches, and similar devices can be registered as trusted devices for authentication purposes. A trusted device could be a user’s primary device like their everyday mobile phone, a secondary backup device like their tablet at home, or a friend’s device with reduced permissions. A user’s trusted devices allow mobile apps to access secrets associated with a device, which identifies the physical hardware and are hard to spoof. The device can allow risk-based authentication policies, such as a user’s geolocation or device posture (how you hold the phone), to be monitored and analyzed for risk as well. Common risk-based authentication policies include group membership, geolocation, mobile device management (MDM), device posture (how you hold the phone), geo-velocity, network reputation, and more.
What are device secrets?
Device secrets, also known as unique device identifiers, are unique codes associated with a specific device, like a mobile phone. For example, Apple codes their devices with a 40-digit code. Note: Device secrets are not a user’s telephone number, which can be transferred to other devices.
Why use passwordless authentication?
There are three main reasons to implement passwordless authentication:
-
- Improve customer experience
- Reduce security risks
- Reduce costs of maintaining passwords
Improved customer experience is a major consideration. When UI/UX designers design digital interfaces, they strive to create a frictionless customer experience where users can intuitively interact with software. Friction is bad for business, as frustrated customers abandon online shopping carts and business transactions. One of the biggest sources of friction? Using a password to sign on, especially if the user can’t remember their password.
Passwordless authentication also reduces security risks. Most cyber hacks today continue to exploit weak or hacked passwords. Methods include using password dictionaries, brute force attacks, dictionary attacks, or social engineering techniques like phishing. C-level executives are at the highest risk. They are nearly twelve times more likely to be the target of social engineering incidents, according to Verizon’s 2019 report. Relying on secure authentication factors—not passwords—reduces these risks.

Lastly, companies use passwordless authentication to reduce cost. Corporate help desk teams are inundated with password-related issues—from password resets to change requests—which are time-intensive, costly exercises. For example, "in a single month in 2017, Microsoft had to reset 686,000 passwords for employees, resulting in support expenses of over $12 million,” according to Verizon’s report. For employees, passwordless authentication reduces the amount of services needed from help desk teams. Registering trusted devices is easy for end users who can utilize self service for device registration and unregistration. Not to mention maximizing employee productivity since fewer users are locked out of accounts.
Why now?
There are many reasons this is the right time for passwordless authentication. There is a security need; developers welcome it; end users are ready for it (and own the devices necessary to achieve it); and the marketplace has adopted standards to allow it; just to name a few.
Getting rid of passwords as a form of authentication is a high-level security need. The number of cyberattacks companies experience won’t decrease. Removing passwords as an attack vector can help protect a company and its employees. Developers like passwordless authentication because they can authenticate end users with simple application programming interfaces (APIs). There is no need to create custom authentication solutions.
End users are ready for passwordless authentication and yearn for the convenience of a passwordless future. According to the Ponemon Institute’s 2019 report, 57% of respondents expressed a preference for passwordless logins that protect their identity, because "managing passwords is inconvenient and cumbersome."
Furthermore, end users have the devices—such as smart phones, smart watches, and other mobile devices—necessary for a passwordless authentication. Users can choose from mobile push options or even biometric authentication on their device using their face or finger to authenticate. Physical security keys are still an option for those who wish to authenticate via other means.
Lastly, the marketplace has adopted the standards to make passwordless authentication mainstream. The embracement of FIDO Alliance (Fast IDentity Online) standards for passwordless authentication—including the FIDO Universal Second Factor (FIDO U2F), FIDO Universal Authentication Framework (FIDO UAF) and FIDO2, which includes the W3C’s Web Authentication (WebAuthn) specification and FIDO Client to Authenticator Protocol (CTAP)—is a driving force to create the ecosystem for the rapid adoption of passwordless authentication among businesses and end users. The FIDO specifications are open and free for global use. Today’s FIDO Alliance members include global tech leaders across payments, telecom, government, and health care industries. This includes tech giants such as Amazon, Alibaba, Facebook, and Google.
| RELATED: What is FIDO? Learn more about the FIDO Alliance here → |
There are some important things to consider when evaluating passwordless authentication providers. Not all providers offer mobile SDK tools to natively embed authentication in a business’ mobile app; this is important for companies who wish to brand their applications to consider. Some providers offer legacy multi-factor solutions, like SMS and email one-time passcodes, which are less secure than other forms of authentication. With this in mind, consider if you’d like to have less secure authentication factors available to your end users for everyday use, just for extreme back-up cases, or not at all. Some providers offer “passwordfree,” not passwordless solutions that still rely on passwords on the backend and merely replay passwords when using an authentication method, such as a biometric. Other things to consider include how a user can authenticate if their device runs out of battery or they are not online. Options would include having a physical security key or scanning a QR code with an offline device.
Passwordless authentication on G2
In the next several weeks, G2 will launch a new category listing passwordless authentication providers. If you currently use a passwordless authentication provider, please consider leaving a review on our site to help future buyers make confident purchasing decisions.
*Disclaimer: I am not a lawyer and am not offering legal advice. If you have legal questions, consult a licensed attorney.
¿Quieres aprender más sobre Software de gestión de identidades? Explora los productos de Gestión de Identidad.

Merry Marwig, CIPP/US
Merry Marwig is a senior research analyst at G2 focused on the privacy and data security software markets. Using G2’s dynamic research based on unbiased user reviews, Merry helps companies best understand what privacy and security products and services are available to protect their core businesses, their data, their people, and ultimately their customers, brand, and reputation. Merry's coverage areas include: data privacy platforms, data subject access requests (DSAR), identity verification, identity and access management, multi-factor authentication, risk-based authentication, confidentiality software, data security, email security, and more.
