Was ist Bedrohungsemulation?
Bedrohungsemulation ist ein proaktiver Ansatz zur Cybersicherheit, bei dem eine reale Bedrohung in einer kontrollierten Umgebung repliziert und simuliert wird, um bestehende Cybersicherheitssysteme zu testen.
Ziel der Bedrohungsemulation ist es, aktuelle Systeme zu bewerten und Schwachstellen zu identifizieren, durch die ein Cyberangriff in das Netzwerk eines Unternehmens eindringen könnte.
Typischerweise werden vergangene bekannte Angriffe als Grundlage für die Bedrohungsemulation verwendet und in Netzwerk-Sandboxing-Software nachgeahmt. Dies ist ein sicherer digitaler Raum, in dem die Bedrohung repliziert und ausgeführt werden kann, ohne die aktiven Geschäftssysteme im Netzwerk zu beeinträchtigen.
Grundelemente der Bedrohungsemulation
Bei der Durchführung eines Bedrohungsemulationstests sollten Teams mehrere Schritte befolgen, um sicherzustellen, dass der Test so genau wie möglich ist. Diese Schritte umfassen:
- Anwendung bekannter Bedrohungsinformationen: Alle Informationen, die das Team über die nachgebildete reale Bedrohung sammeln kann, machen die Simulation wirkungsvoller. Das Sammeln von Daten über alle Bedrohungen, denen ein Unternehmen ausgesetzt sein könnte, sollte ein fortlaufender Prozess sein.
- Identifizierung von Vermögenswerten im System: Während reale Angriffsdatensätze nützlich sind, hatte das Ziel des Angriffs wahrscheinlich andere Vermögenswerte als die, die in der Bedrohungsemulation getestet werden. Zu wissen, welche Vermögenswerte das Unternehmen hat und wie diese in einer Bedrohungsemulation verwendet werden könnten, macht die Ergebnisse erfolgreicher, wenn ein starkes Cybersicherheitsprogramm entwickelt wird, das auf das Unternehmen zugeschnitten ist.
- Bewertung bestehender Cybersicherheitssoftware: Es ist auch wichtig, dass alle Angriffsminderungswerkzeuge, die das Unternehmen bereits hat, wie Antivirensoftware, in den Bedrohungsemulationstest einbezogen werden. Dies ermöglicht es dem Team, die Fähigkeiten der Werkzeuge zu überprüfen und Lücken im System zu identifizieren.
Vorteile der Bedrohungsemulation
Vorbereitet zu sein auf einen möglichen Cyberangriff kann Unternehmen Tausende, wenn nicht Millionen von Dollar sparen. Zwei der größten Vorteile von Bedrohungsemulationen sind:
- Verständnis der Wirksamkeit von Sicherheitsmaßnahmen: Jedes Werkzeug, das das Unternehmen derzeit für die Cybersicherheit hat, sollte regelmäßig überprüft und getestet werden, um sicherzustellen, dass jede Reaktion angemessen ist und wichtige Daten schützt. Zu wissen, dass aktuelle Werkzeuge effektiv sind, oder Schwachstellen im System zu finden und daraufhin Upgrades zu planen, ist die wichtigste Funktion von Emulationstests.
-
Testen der Reaktion des Teams auf einen Angriff: Bei der Bedrohungsemulation geht es darum, zu wissen, ob die Cybersicherheitssysteme des Unternehmens mit einem Angriff umgehen können und dem IT-Team zu vertrauen, mögliche Bedrohungen zu bewältigen. Mit der Bedrohungsemulation sind die Reaktionen des Teams, wie Aufgabenverteilung und Geschwindigkeit, entscheidend, um sie zu bewerten und zu verbessern, falls ein Angriff auftritt.
Best Practices für die Bedrohungsemulation
Jeder Bedrohungsemulationstest sollte so gestaltet sein, dass er dem ursprünglichen Angriff so ähnlich wie möglich ist. Dazu sollten mehrere Best Practices befolgt werden, darunter:
- Wählen Sie Ziele vor dem Testen: Jeder Test sollte messbare Ziele und Vorgaben haben, die klar festgelegt werden, bevor das Testen beginnt. Die meisten Bedrohungsemulationen zielen darauf ab, Schwachstellen im System zu finden, aber Teams können noch spezifischer sein, welche Art von Schwachstellen sie mit jedem Test suchen.
- Arbeiten Sie in einer geeigneten Testumgebung: Die für den Test erstellte Sandbox muss nicht genau den realen Systemen entsprechen, die das Unternehmen betreibt. Je näher die Übereinstimmung jedoch ist, desto relevanter sind die Daten und Erkenntnisse nach Abschluss des Tests.
- Überprüfen und beseitigen Sie Fehlalarme: Bedrohungsemulationstests sollten niemals nur einmal durchgeführt werden. Mehrfaches Durchführen der Tests wird Anomalien oder Fehlalarme aufdecken, die Daten verfälschen können, was für eine größere Genauigkeit unerlässlich ist. Wenn Änderungen an Cybersicherheitssystemen auf der Grundlage dieser Ergebnisse vorgenommen werden, wird dies umso wichtiger.
Bedrohungsemulation vs. Penetrationstests
Obwohl sowohl Bedrohungsemulation als auch Penetrationstests einem Unternehmen, das seine Cybersicherheit testen möchte, zugutekommen, gibt es wichtige Unterschiede zwischen den beiden.
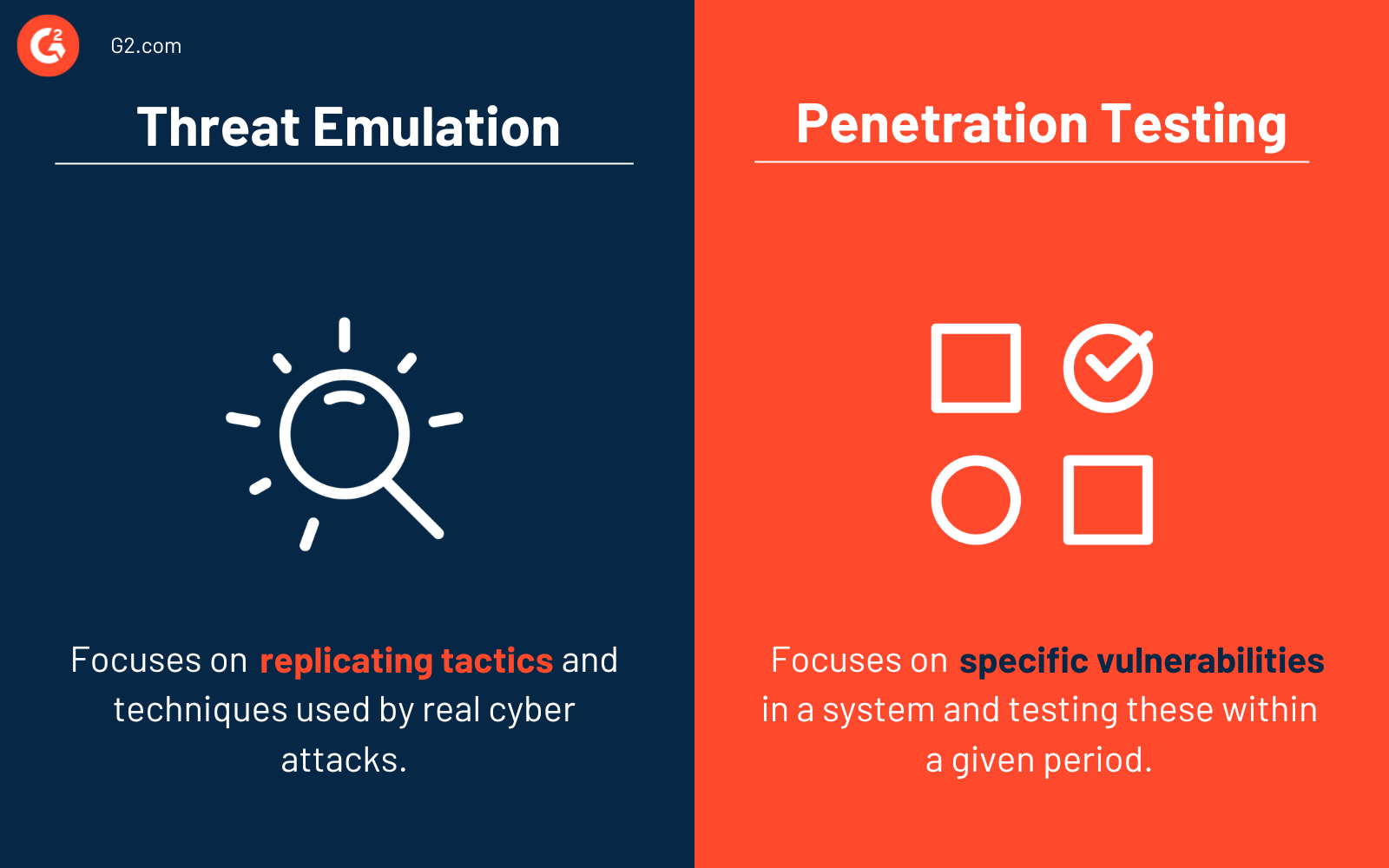
Bedrohungsemulation konzentriert sich hauptsächlich auf die Replikation von Taktiken und Techniken, die bei realen Cyberangriffen verwendet werden.
Penetrationstests konzentrieren sich auf spezifische Schwachstellen in einem System und testen diese innerhalb eines bestimmten Zeitraums. Das Ziel ist es, sich auf eine oder zwei Schwachstellen zu konzentrieren, anstatt auf die Methoden, die zur Ausnutzung dieser Schwachstellen verwendet werden (was die Aufgabe der Bedrohungsemulation ist).
In vielen Fällen können sowohl Bedrohungsemulation als auch Penetrationstests verwendet werden, um einen umfassenderen Cybersicherheitstest zu erstellen.
Überwachen Sie neue Bedrohungen und verstehen Sie, wo die aktuelle Sicherheitsinfrastruktur verbessert werden kann mit Bedrohungsinformationssoftware.

Holly Landis
Holly Landis is a freelance writer for G2. She also specializes in being a digital marketing consultant, focusing in on-page SEO, copy, and content writing. She works with SMEs and creative businesses that want to be more intentional with their digital strategies and grow organically on channels they own. As a Brit now living in the USA, you'll usually find her drinking copious amounts of tea in her cherished Anne Boleyn mug while watching endless reruns of Parks and Rec.