Verwundbarkeitsscanner sind eine entscheidende Verteidigungslinie, die Webanwendungen vor den sich schnell entwickelnden und gefährlichen Cyberbedrohungen schützen. Diese Software bewertet Ihr Netzwerk und Ihre Systeme auf Schwachstellen und berichtet über die damit verbundenen Risiken. Es gibt viele Verwundbarkeitsscanning-Tools in der Branche, aber da die Bedürfnisse jeder Organisation variieren, variiert auch die beste Wahl bei Verwundbarkeitsscannern.
Was ist ein Verwundbarkeitsscanner?
Ein Verwundbarkeitsscanner ist ein Sicherheitstool, das Ihre IT-Ressourcen auf Mängel, Schwächen oder CVEs (Common Vulnerabilities and Exposures) untersucht, die die Cybersicherheit Ihrer Organisation gefährden könnten.
Lassen Sie uns tief in das Thema Verwundbarkeitsscanning eintauchen, um Ihre Prioritäten zu ordnen und Ihnen zu helfen, die beste Lösung für Ihr Team auszuwählen.
Verständnis von Verwundbarkeitsscannern
Verwundbarkeitsscanner helfen Ihnen, Schwächen zu beheben und den Prozess entsprechend ihrem Risikoniveau zu priorisieren. Sobald die Software den Scan abgeschlossen hat, erstellt sie eine Risikobewertung der identifizierten Schwachstellen und schlägt Maßnahmen zur Risikominderung vor.
Wenn Verwundbarkeitsscans regelmäßig mit einem ordnungsgemäßen Verwundbarkeitsmanagement durchgeführt werden, helfen sie, Ihre Organisation vor neuen Bedrohungen zu schützen, die durch häufige Software-Updates entstehen. Außerdem überprüft das Tool eine oder mehrere Verwundbarkeitsdatenbanken, um festzustellen, ob bekannte Schwachstellen vorhanden sind.
Zum Beispiel ist die NVD, die National Vulnerability Database, das US-Regierungs-Repository für standardbasierte Verwundbarkeitsmanagementdaten, die mit dem Security Content Automation Protocol dargestellt werden. Diese Daten ermöglichen die Automatisierung des Verwundbarkeitsmanagements, der Sicherheitsmessung und der Compliance.
Verwundbarkeitsscanner ermöglichen es Organisationen auch, die sich entwickelnden Sicherheitsstandards einzuhalten, indem sie Schwächen überwachen und erkennen, um die Sicherheit von Webanwendungen und Netzwerksicherheit aufrechtzuerhalten. Darüber hinaus ist das Verwundbarkeitsscanning auch einer der ersten Schritte beim Penetrationstesting.
Möchten Sie mehr über Verwundbarkeits-Scanner-Software erfahren? Erkunden Sie Verwundbarkeitsscanner Produkte.
Was ist der Zweck von Verwundbarkeitsscannern?
Der Zweck von Verwundbarkeitsscannern besteht darin, das Sicherheitsframework Ihrer Organisation gegen kontinuierlich sich entwickelnde Bedrohungen zu schützen. So erfüllt ein Verwundbarkeitsscanner seinen Zweck.
- Erkennt Sicherheitsbedrohungen: Kontinuierliche Scans helfen Ihnen bei der Erkennung von Schwachstellen und der Bewältigung neuer Schwachstellen sowohl aus externer als auch aus interner Perspektive.
- Entdeckt nicht identifizierte Geräte: Verwundbarkeitsscanner identifizieren unautorisierte Maschinen, die mit Ihrem Netzwerk verbunden sind. Sie helfen Ihnen, Ihr Netzwerk vor möglichen Bedrohungen zu schützen, die diese Geräte darstellen könnten.
- Überprüft das Netzwerkgeräte-Inventar: Verwundbarkeitsscanner helfen, alle Geräte im Netzwerk mit spezifischen Details wie Gerätetyp, Betriebssystemversion, Hardwarekonfiguration, Patch-Level usw. zu identifizieren.
Welche Arten von Verwundbarkeitsscans gibt es?
Ob Sie ein Open-Source-Verwundbarkeitstool oder einen lizenzierten Sicherheitsscanner gewählt haben, es gibt verschiedene Arten von Verwundbarkeitsscans, die Sie mit ihnen durchführen können. Die Art des Verwundbarkeitsscans hängt vom Umfang, der Umgebung und anderen Faktoren ab.
Man kann sie in folgende Typen einteilen:
Externer Verwundbarkeitsscan vs. interner Verwundbarkeitsscan

Externe Verwundbarkeitsscans helfen Unternehmen, Probleme zu identifizieren und zu beheben, die ihr Netzwerk Angreifern aussetzen. Diese Scans werden von außerhalb des Netzwerks der Organisation durchgeführt und umfassen alle Endpunkte, Webanwendungen, Ports und mehr.
Die Einführung der Cloud hat den Bedarf an externen Verwundbarkeitsscans erhöht, da die Anzahl der Fehlkonfigurationen und unsicheren Datenbanken stark zugenommen hat.
Interne Verwundbarkeitsscans ermöglichen es Ihnen, die Sicherheit von Anwendungen und Systemen, hauptsächlich von innerhalb des Netzwerks Ihres Unternehmens, zu verstärken.
Diese Scans helfen Ihnen, die Sicherheitslücken zu erkennen, die Hacker ausnutzen könnten, sobald sie die äußere Verteidigung durchdrungen haben. Diese Scans helfen auch dabei, die Bedrohung durch Malware oder Insider-Bedrohungen zu identifizieren, die von unzufriedenen Mitarbeitern oder Auftragnehmern ausgehen könnten.
Es gibt Standards wie den Payment Card Industry Data Security Standard (PCI-DSS), der sowohl interne als auch externe Verwundbarkeitsscans vierteljährlich sowie bei neuen Updates, Änderungen der Netzwerktopologie oder Änderungen der Firewall-Regeln vorschreibt. Hier müssen Sie Tools von einem PCI-zugelassenen Scananbieter (ASV) verwenden, der die PCI DSS-Anforderung 11.2.2 erfüllt, um Ihre externen Scans durchzuführen.
Unauthentifizierte Verwundbarkeitsscans vs. authentifizierte Verwundbarkeitsscans

Unauthentifizierte Verwundbarkeitsscans erkunden und erkennen Dienste, die über ein Netzwerk auf einem Computer geöffnet sind, indem sie Pakete an deren offene Ports senden. Sie bestimmen die Version des Betriebssystems, die Softwareversionen hinter den jeweiligen Diensten, offene Dateifreigaben oder andere verfügbare Informationen ohne Authentifizierung.
Danach überprüfen Scanner die Verwundbarkeitsdatenbank und identifizieren Schwachstellen, die wahrscheinlich vorhanden sind.
Authentifizierte Verwundbarkeitsscans sammeln detailliertere Informationen über die Version des Betriebssystems (OS) und der installierten Software, indem sie Anmeldeinformationen verwenden, um umfassende Informationen über die Schwachstellen des Systems zu liefern.
Manchmal ist es möglich, dass einige Programme nicht über das Netzwerk zugänglich sind, aber dennoch Schwachstellen offenlegen, die anderen Angriffsvektoren ausgesetzt sind, wie z.B. das Öffnen bösartiger Webseiten oder bösartig gestalteter Dateien.
Um solche Schwachstellen zu verwalten, setzen einige Verwundbarkeitsbewertungslösungen leichte Softwareagenten auf Computern ein, um ein vollständiges Bild der Cybersicherheitslandschaft einer Organisation zu erhalten.
Umfassende Verwundbarkeitsscans vs. begrenzte Verwundbarkeitsscans
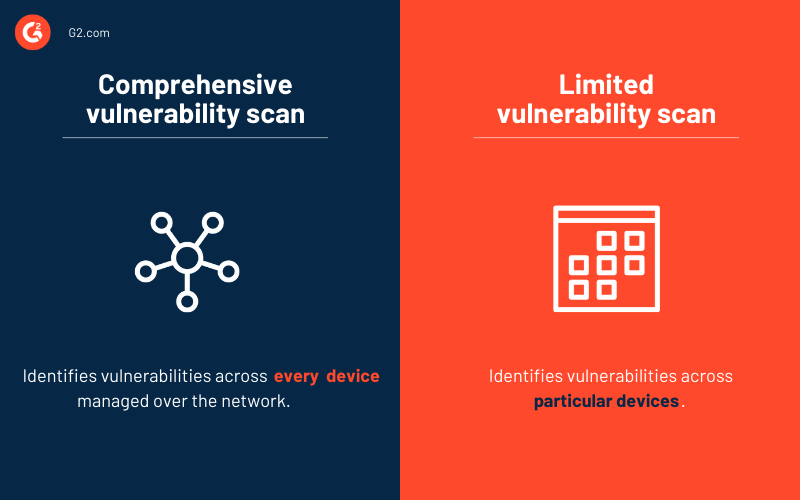
Umfassende Verwundbarkeitsscans erkunden, untersuchen und identifizieren neue Schwachstellen auf jedem im Netzwerk verwalteten Gerät. Dazu gehören Server, Desktops, Laptops, virtuelle Maschinen, Mobiltelefone, Container, Drucker, Firewalls, Switches und mehr.
Hier erhalten Sie einen vollständigen Scanbericht über das installierte Betriebssystem, Benutzerkontoinformationen und offene Ports, unter anderem. Umfassende Verwundbarkeitsscans können viel Bandbreite nutzen, aber der Vorteil ist, dass kein Risiko übersehen wird.
Begrenzte Verwundbarkeitsscans konzentrieren sich hauptsächlich auf bestimmte Geräte wie einen Server, Arbeitsstationen oder Software. Diese Scans werden durchgeführt, um eine hochspezifische Sicherheitslage der Tools zu erhalten und sie besser gegen mögliche Risiken zu schützen.
Wie funktioniert ein Verwundbarkeitsscanner?
Verwundbarkeitsscanner arbeiten mit einem dreistufigen Mechanismus, der auf das Ziel Ihrer Organisation abzielt, die Schwachstellen und die Risiken, die sie darstellen könnten, zu identifizieren. Diese drei Mechanismen ermöglichen es Ihnen gemeinsam, die Cybersicherheit Ihrer Organisation zu schützen.
1. Erkennung
Der erste Schritt des Verwundbarkeitsbewertungstools besteht darin, einen Verwundbarkeitstest durchzuführen, um mögliche Angriffsflächen zu erkennen und zu identifizieren. Es ermöglicht Ihnen, die Sicherheitslücken in Ihrem Netzwerk zu bestimmen und sie zu schließen, bevor Angreifer eindringen können.
2. Klassifizierung
Im zweiten Schritt werden die Schwachstellen klassifiziert, um Administratoren bei der Priorisierung ihrer Maßnahmen zu helfen. Diese Schwachstellen könnten fehlende Updates, Skriptfehler oder Anomalien umfassen, während die Bedrohungen basierend auf Alter und Risikomaßnahme priorisiert werden.
3. Behebung
In der Regel bieten Verwundbarkeitsscanner keine Möglichkeit, identifizierte Schwachstellen automatisch zu beheben. Sie konzentrieren sich mehr auf die Überwachung und Bereitstellung von Details für die Administratoren, um den nächsten Schritt zu unternehmen. Aber einige Scanner beheben Konfigurationsfehler und sparen so den Administratoren Stunden an Arbeit, indem sie mehrere Geräte gleichzeitig erreichen.
Wie führt man einen Verwundbarkeitsscan durch?
Die Durchführung eines Verwundbarkeitsscans erfordert einen standardisierten Satz von wiederholbaren und skalierbaren Prozessen, um den wachsenden Anforderungen Ihrer Organisation gerecht zu werden. Führen Sie die unten genannten Schritte aus, um einen Netzwerkverwundbarkeitsscan in Ihrer Organisation durchzuführen und ein standardisiertes Verfahren festzulegen:
Definieren Sie den Umfang
Es ist wichtig, den Umfang des Verwundbarkeitsscans zu definieren, bevor Sie ihn planen. Sie müssen alle Ressourcen identifizieren, die Teil des Informationssystems Ihrer Organisation sind. Sie können dies mit Ihrem Ressourcenregister tun, das zusätzliche Spalten für Bedrohungen und Schwachstellen enthält, um ein zentrales Repository für Ressourcen, Schwachstellen, Risiken und Behebungsmaßnahmen zu pflegen.
Erstellen Sie ein standardisiertes Verfahren
Um eine klare und strukturierte Methodik des Verwundbarkeitsscans zu erstellen, sollten Sie ein festes Standardverfahren, Richtlinien und einen Maßnahmenplan zur Implementierung haben.
Zuerst benötigen Sie einen offiziellen Verantwortlichen, der für die Ausführung des genannten SOP verantwortlich ist. Denken Sie daran, dass dieses SOP von den höheren Behörden genehmigt werden sollte und den verschiedenen Compliance-Vorgaben wie HIPAA oder PCI-DSS entsprechen sollte, zum Beispiel.
Dieses Standardverfahren würde definieren, wie oft Sie diese Scans durchführen sollten, die Art der Scans, die Verwendung von Softwarelösungen und die Schritte nach Abschluss des Scans.
Identifizieren Sie die benötigte Art des Verwundbarkeitsscans
Bevor Sie direkt mit dem Scannen Ihrer Ressourcen auf Schwachstellen beginnen, müssen Sie feststellen, welche Art von Scan den größten Nutzen bringen würde.
Es gibt vier Arten von Scans, die Sie basierend auf Ihren Bedürfnissen durchführen können.
- Netzwerkverwundbarkeitsscans: Der Umfang von Netzwerkverwundbarkeitsscans umfasst die Hardware und Software, die Teil des Netzwerks sind, ihre Kommunikationskanäle oder Netzwerkausrüstung. Dazu gehören Hubs, Switches, Firewalls, Router, Webserver, Cluster und so weiter.
- Host-basierte Verwundbarkeitsscans: Diese Scans werden oft mit Netzwerkscans verwechselt. In Wirklichkeit identifizieren host-basierte Verwundbarkeitsscans Schwachstellen in den Hosts eines Netzwerks wie Computern, Systemen, Laptops usw. Der Untersuchungsumfang dieser Scans umfasst Konfiguration, Verzeichnisse, Dateisysteme und andere Informationen. Durch diese können Sie die ruhenden Schwachstellen und Fehlkonfigurationen identifizieren, die Angreifer ausnutzen können.
- Drahtlose Verwundbarkeitsscans: Diese Scans umfassen das Erkennen aller drahtlosen Geräte in Ihrem Netzwerk, das Kartieren der Attribute jedes Geräts und das Identifizieren von nicht autorisierten Zugangspunkten im Netzwerk, die Hacker verwenden könnten, um Ihren drahtlosen Datenverkehr abzuhören.
- Anwendungsbasierte Verwundbarkeitsscans: Diese Scans sind Teil des Anwendungssicherheitstests, um Schwächen in einer Webanwendung zu erkennen; basierend auf den Ergebnissen wird ein Anwendungspenetrationstest durchgeführt, um eine robustere Anwendungssicherheit aufzubauen.
Konfigurieren Sie den Verwundbarkeitsscan
Sie können die Konfiguration eines Verwundbarkeitsscans basierend auf den allgemeinen Zielen, die Sie erreichen möchten, und dem beteiligten System anpassen.
Zuerst müssen Sie eine Liste der Ziel-IP-Adressen hinzufügen, auf denen die Kurse in der Verwundbarkeitsscanning-Software gehostet werden. Sie müssen dann den Portbereich auswählen, den Sie scannen möchten, und das Protokoll, das Sie verwenden würden.
Der nächste Schritt definiert die Ziele auf den angegebenen IPs, sei es eine Datenbank, ein Server, ein drahtloses Gerät oder etwas anderes. Damit können Sie Ihren Scan spezifischer gestalten, um genaue Ergebnisse zu erhalten.
Bewerten Sie die mit dem Scan verbundenen Risiken
Die Durchführung eines Verwundbarkeitsscans kann eine erhebliche Belastung für das Ziel darstellen, was dazu führen kann, dass es möglicherweise neu gestartet wird oder Ausfallzeiten erleidet.
Sie sollten Vorsichtsmaßnahmen treffen, während Sie Produktionssysteme und solche, die für den Betrieb der Organisation von entscheidender Bedeutung sind, scannen. Es ist am besten, wenn Sie die Scans außerhalb der Arbeitszeiten durchführen, damit die Auswirkungen auf das Ziel minimal sind und es weniger Möglichkeiten für eine Überlastung gibt.
Verwandt: Erfahren Sie mehr über Lastverteilung, um eine Überlastung Ihres Netzwerks zu vermeiden.
Starten Sie den Verwundbarkeitsscan
Sobald Sie die Konfiguration und Bewertung der Risiken abgeschlossen haben, können Sie den gewünschten Scan ausführen. Die Dauer des Scans hängt von verschiedenen Faktoren ab, wie dem Umfang des Scans, seiner Eindringlichkeit und mehr; es kann Minuten oder Stunden dauern, bis er abgeschlossen ist.
Es gibt drei Phasen eines Verwundbarkeitsscans. Zuerst ist das Scannen, bei dem das Tool die Ziele analysiert und notwendige Informationen sammelt. Dann kommt die Aufzählung, bei der das Tool nach spezifischeren Details wie Ports und Diensten sucht, die diese Ziele ausführen. Schließlich erstellt das Tool eine Karte der Schwachstellen, die vorhanden sind.
Analysieren Sie die Ergebnisse
Verwundbarkeitsscanning-Tools erstellen automatisch eine Prioritätenliste, aber Sie müssen auf falsche Positive oder falsche Negative überprüfen, bevor Sie Schwachstellen zur Behebung priorisieren.
Sie sollten auch den Aufwand berücksichtigen, der erforderlich ist, um die Schwachstelle auszunutzen. Hacker werden diejenigen angreifen, die weniger Schritte erfordern und für sie höhere Gewinne bringen. Ebenso sollten Sie zuerst die Schwachstellen beheben, die öffentlich ausnutzbar sind.
Erstellen Sie einen Behebungsplan
Sobald Sie die Ergebnisse analysiert haben, sollte Ihr Information Security Team mit dem IT-Team zusammenarbeiten, um den Behebungsprozess zu priorisieren.
Es ist am besten, das CVSS (Common Vulnerability Scoring System) zu verwenden, um die Behebungsmaßnahmen zu priorisieren. Dieses standardisierte System hilft Ihnen, die Schwere der Sicherheitsrisiken, die mit der Schwachstelle verbunden sind, auf einer Skala von null bis 10 zu quantifizieren. Insgesamt würde es Ihnen ermöglichen, den Behebungsprozess zu priorisieren und zu beschleunigen.
Sie sollten eine Schwachstelle nicht als behoben betrachten, nachdem sie gepatcht wurde, führen Sie Scans durch, um sicherzustellen, dass sie nicht erneut in den Berichten erscheinen. Einige Schwachstellen können kompliziert sein, und Sie benötigen möglicherweise mehrere Sicherheitspatches, um sie zu beheben.
Top 5 Verwundbarkeitsscanner
Die folgende Liste enthält echte Benutzerbewertungen der besten Verwundbarkeitsscanner auf dem Markt. Um in diese Liste aufgenommen zu werden, muss ein Produkt:
- Eine Datenbank bekannter Schwachstellen pflegen.
- Kontinuierlich Anwendungen auf Schwachstellen scannen.
- Berichte erstellen, die bekannte Schwachstellen und neue Exploits analysieren.
* Unten sind die fünf führenden Verwundbarkeitsscanner aus dem G2 Spring 2024 Grid® Report. Einige Bewertungen können zur Klarheit bearbeitet worden sein.
1. Wiz
Wiz bietet cloud-natives Verwundbarkeitsscanning mit einem Fokus auf automatisiertes Scannen. Die Arbeitslast erfordert keine Agenten oder Sidecar-Container, die bereitgestellt werden müssen. Dies vereinfacht die Bereitstellung und reduziert den Wartungsaufwand.
Rezensenten loben Wiz für seine benutzerfreundliche Oberfläche und die klare Darstellung der Verwundbarkeitsdaten. Seine Fähigkeit, Schwachstellen basierend auf Kontext und potenziellen Auswirkungen zu priorisieren, ermöglicht es Benutzern, sich zuerst auf die kritischsten Probleme zu konzentrieren. Außerdem empfinden Rezensenten, dass Wiz besseren laufenden Produktsupport bietet.
Was Benutzer am meisten mögen:
"Dies ist nützlich, um Anwendungs-Schwachstellen für eine schnelle Behebung aufzuzeigen. Das Tool bietet zentrale Sichtbarkeit und Aufsicht sowie mehrere Bereitstellungsoptionen; auch die Benutzeroberfläche ist einfach zu bedienen und benutzerfreundlich.
Der attraktivste Punkt ist, dass es agentenlos ist. Ich kann ohne Aufwand priorisieren und die Regeln anpassen, um sie an meine Organisation anzupassen."
- Wiz Review, Vaibhav S.
Was Benutzer nicht mögen:
"Wiz veröffentlicht oft neue Funktionen, die "getestet" werden sollen - das kann bedeuten, dass, wenn man den Wert oder Anwendungsfall nicht versteht, sie sich nicht "produktionsreif" anfühlen können. Einige Organisationen könnten davon abgeschreckt werden."
- Wiz Review, Tony C.
2. Nessus
Tenable Nessus ist eine Verwundbarkeitsbewertungslösung, die von Sicherheitsexperten verwendet wird, um zeitpunktbezogene Bewertungen durchzuführen, um Schwachstellen schnell zu identifizieren und zu beheben. Es analysiert und erkennt auch Softwarefehler, fehlende Patches, Malware und Fehlkonfigurationen in verschiedenen Betriebssystemen, Geräten und Anwendungen.
Rezensenten auf G2 heben die robusten Automatisierungsfähigkeiten von Nessus und seine große Bibliothek vorgefertigter Scan-Richtlinien hervor, um verschiedene Sicherheitsanforderungen zu adressieren. Es kann vorgefertigte Verwundbarkeitsscans ohne manuelle Eingriffe durchführen, was Zeit und Ressourcen spart.
Weitere Funktionen umfassen anpassbare Berichterstattung, Echtzeit-Updates und die "Snooze"-Funktionalität für Gruppen. Insgesamt macht es die Verwundbarkeitsbewertung einfach, leicht und intuitiv.
Was Benutzer am meisten mögen:
"Nessus hat eine der größten Bibliotheken von Verwundbarkeits- und Konfigurationsprüfungen, die eine breite Palette von Systemen, Geräten und Anwendungen abdecken. Trotz seines umfassenden Funktionsumfangs ist Nessus für seine benutzerfreundliche Oberfläche bekannt, die Benutzern hilft, schnell loszulegen."
- Tenable Nessus Review, Deepsan V.
Was Benutzer nicht mögen:
"(Nessus) kann teuer sein und eignet sich für größere Organisationen, die hohe Funktionalität und Unterstützung benötigen. Es ist mit einer benutzerfreundlichen Oberfläche gestaltet, erfordert jedoch dennoch Kenntnisse oder Schulungen, um es zu verwenden. Es benötigt mehr Zeit für das Scannen."
- Nessus Review, Lavesh K.
3. Microsoft Defender Vulnerability Management
Microsoft Defender Vulnerability Management ist eine cloudbasierte Verwundbarkeitsmanagementlösung, die von Microsoft als Teil ihrer Endpunkt- und Cloud-Sicherheitsprodukte angeboten wird.
Mit seiner Integration von Microsoft-Bedrohungsinformationen kann es die Wahrscheinlichkeit von Sicherheitsverletzungen vorhersagen und Schwachstellen basierend auf Geschäftskontext und der Bewertung von Geräten priorisieren. Benutzer schätzen die Software dafür, dass sie nicht anspruchsvoll in Bezug auf CPU/Memory ist und bewundern ihre Effizienz und Anpassungsoptionen.
Was Benutzer am meisten mögen:
"Es gibt viele Lösungen auf dem Markt für diesen Zweck, aber nur wenige von ihnen sind so wenig anspruchsvoll für CPU/Memory wie Microsoft Defender Vulnerability Management. Man merkt wirklich nicht, dass es arbeitet, keine Beeinträchtigung der Systemgeschwindigkeit, aber es erledigt die Arbeit perfekt. Die Anpassung ist auch großartig und kann sehr schnell an Ihre Bedürfnisse angepasst werden.."
- Microsoft Defender Vulnerability Management Review, Marko V.
Was Benutzer nicht mögen:
"Das Dashboard kann verwirrend und schwer zu bedienen sein für Erstbenutzer; zusätzliche Schulungen sind erforderlich, um alle Funktionen vollständig nutzen zu können. Die Berichterstattungsfähigkeiten könnten erhöht werden, um umfassendere Informationen über Schwachstellen und deren potenzielle Auswirkungen bereitzustellen. Die Unterstützung für Drittanbieterprodukte ist stark eingeschränkt."
- Microsoft Defender Vulnerability Management Review, Marko V.
4. Orca Security
Orca Security, ähnlich wie Wiz, verfolgt einen agentenlosen Ansatz. Es nutzt Side-Scanning-Technologie, um Ihre Cloud-Umgebung zu scannen, ohne dass Agenten auf Workloads bereitgestellt werden müssen. Es ist speziell für Cloud-Umgebungen entwickelt und versteht die Feinheiten der Cloud-Sicherheit und kann eine breite Palette von Cloud-Ressourcen scannen, einschließlich virtuellen Maschinen, Containern, serverlosen Funktionen und mehr.
Was Benutzer am meisten mögen:
"Agentenloser Ansatz und tiefe Sichtbarkeit. Es erfordert keine Installation von Agenten oder zusätzlicher Software, deshalb benötigen wir nur Minuten, um neue Konten bei Orca zu integrieren. Nach der Integration bietet Orca wirklich umfassende Asset-Erkennung, Verwundbarkeit Scannen und Risikobewertung. Außerdem bin ich beeindruckt von der kontinuierlichen Produktentwicklung von Orca Security und ihrem Engagement, neue Funktionen einzuführen."
- Orca Security Review, Swapnil R.
Was Benutzer nicht mögen:
"Das Überprüfen der Datei, die kompromittiert oder falsch konfiguriert ist, ist schwer im Dashboard zu sehen, und ich bin mir immer noch nicht sicher, ob es Sonarqube oder nur Sonar Query verwendet. Es gibt viele Komponenten, die es schwer verständlich machen."
- Orca Security, Sujeeth J.
5. Tenable Vulnerability Management
Tenable Vulnerability Management ist ein weiteres Produkt von Tenable, das den Kern-Nessus-Scanner in diesem Tool enthält. Es geht einen Schritt weiter als das Verwundbarkeitsscanning zum risikobasierten Verwundbarkeitsmanagement. Das Tool kann vor Ort, in der Cloud oder in einer hybriden Umgebung bereitgestellt werden.
Viele Rezensenten finden Tenable Vulnerability Management wertvoll, um die Einhaltung von Sicherheitsvorschriften sicherzustellen. Seine vorgefertigten Compliance-Prüfungen vereinfachen diesen Prozess. Die detaillierten Berichte der Plattform werden von Benutzern geschätzt.
Was Benutzer am meisten mögen:
" (Ich mag die) Flexibilität des Tools, sowohl für interne als auch externe Scans. (Es) bietet gute Berichtsfähigkeiten (und es ist) einfach, rollenbasierte Zugriffe zu etablieren... (Das) Kundenserviceteam ist großartig."
- Tenable Vulnerability Management Review, Roger N.
Was Benutzer nicht mögen:
"Einige Filter und Kategorien zur Überprüfung Ihrer aktiven Schwachstellen sind im Dashboard versteckt und schwer zu finden. Ich musste einige meiner Fragen direkt mit unserem Sicherheits-Compliance-Ingenieur besprechen, um Unterstützung zu erhalten."
Tenable Vulnerability Management Review, Esteben G.
Stärken Sie jetzt Ihre Cybersicherheit
Die Wahl des besten Verwundbarkeitsscanners für Ihre Organisation ist von entscheidender Bedeutung, da er einen enormen Einfluss auf Ihren Verwundbarkeitsbewertungs- und Verwundbarkeitsmanagementprozess haben würde.
Sie benötigen Software, die die Bedürfnisse Ihrer Organisation ergänzt und Ergebnisse gemäß Ihren Erwartungen liefert. Wählen Sie den besten Verwundbarkeitsscanner aus den oben genannten aus und treffen Sie eine kluge Entscheidung, um die Cybersicherheit Ihrer Organisation vor Bedrohungen und Angriffen zu schützen.
Mehr erfahren? Erfahren Sie mehr über Eindringungserkennungssysteme und wie sie helfen, Eindringlinge in Ihrem Netzwerk zu erkennen.
Dieser Artikel wurde erstmals 2020 veröffentlicht. Er wurde mit neuen Informationen aktualisiert.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.