Moderne Unternehmen teilen sich den digitalen Raum miteinander und mit dem Internet, sodass die Möglichkeit von Sicherheitsangriffen oder -verletzungen erheblich zugenommen hat.
Angreifer suchen nach Sicherheitslücken in Ihrem Netzwerk oder System, die ihnen helfen könnten, Zugang zu Ihren sensiblen Informationen zu erlangen. Aufgrund dieser Schwachstellen ist die Cybersicherheit Ihrer Organisation ständig gefährdet. Die Mehrheit der IT-Sicherheitsverletzungen ist finanziell motiviert, da der Wert von Informationen oder geistigem Eigentum auf dem Schwarzmarkt hoch ist.
Daher ist Cybersicherheit von größter Bedeutung, und das Schwachstellenmanagement ist ein Teil des Prozesses, der sie intakt hält.
Definition des Schwachstellenmanagements
Schwachstellenmanagement ist ein Prozess, der einen kontinuierlichen Zyklus von Überwachung, Identifizierung, Bewertung, Behebung und Prävention von Mängeln umfasst, die Ihre IT-Ressourcen Angriffen und unbefugten Änderungen aussetzen könnten.
Fortschrittliche Lösungen wie risikobasiertes Schwachstellenmanagement-Software automatisieren den Prozess der Behebung von Schwachstellen. Diese Tools können Schwachstellen basierend auf Risikofaktoren identifizieren und priorisieren, was sie für Ihre IT-Infrastruktur unverzichtbar macht.
Ein Schwachstellenmanagementprogramm ist unerlässlich, um Ihre IT-Ressourcen vor Bedrohungen zu schützen, die zuschlagen könnten. Es ist die erste Verteidigungslinie gegen die übergreifende Bedrohung durch Black-Hat-Hacker.
Was ist Schwachstellenmanagement?
Betrachten wir das Schwachstellenmanagement anhand der folgenden Analogie: Als Kind gehen Sie zu Ihrem regelmäßigen Gesundheitscheck zum Arzt; der Arzt untersucht Ihre Gesundheit, identifiziert Symptome und Risiken, misst die Schwere und bietet Ihnen eine Behandlung an. Dann bestechen sie Sie mit einem Lutscher und bitten Sie, nach einiger Zeit wiederzukommen. Ähnlich umfasst das Schwachstellenmanagement routinemäßige Überprüfungen, die Bewertung möglicher Risiken, die Bewertung der Risikointensität, vorgeschlagene Behebungen und wiederholte Überprüfungen, um festzustellen, ob die Bedrohung noch vorhanden ist.
Egal wie robust Ihre Cybersicherheit ist, Angreifer können immer durch Fehler im System Zugang erlangen. Das Schwachstellenmanagement stellt sicher, dass diese Fehler behoben und gepatcht werden, bevor ein Cyberangriff erfolgt.
Um Ihrem System einen 100%igen Sicherheitsschutz zu bieten, nutzen Sie Penetrationstests und Schwachstellenmanagement, um Ihre Sicherheitskontrollen zu festigen und Ihre IT-Sicherheit zu verstärken.
Bevor wir tiefer in das Thema eintauchen, beginnen wir zunächst mit den Grundlagen und verstehen, was eine Schwachstelle in der Cybersicherheit bedeutet.
Was ist eine Schwachstelle?
Eine Schwachstelle ist die Möglichkeit eines Risikos oder einer Bedrohung, die die Integrität der im System oder Netzwerk gespeicherten Informationen schädigen, sie verändern oder vom Angreifer für katastrophale Zwecke genutzt werden könnte.
Einfach ausgedrückt ist es die Möglichkeit eines unbefugten Zugriffs, der ein Risiko für das Unternehmen und seine Kunden darstellt. Daher muss es ordnungsgemäß behandelt werden. In dieser Ära, in der Remote-Arbeit im Trend liegt, haben die Vorkommen dieser Schwachstellen sprunghaft zugenommen, da die Schwachstellen im Cloud-Netzwerk anders verwaltet werden als die vor Ort.
Aber bevor wir das im Detail besprechen, identifizieren wir die verschiedenen Arten von Schwachstellen, auf die Sie stoßen könnten.
Arten von Schwachstellen
- Netzwerkschwachstellen: Dies sind die Schwachstellen, die sich über ein Netzwerk von Systemen erstrecken. Dazu gehören Computer, Router, IoT-Geräte und andere, die mit dem Internet und miteinander kommunizieren. (Erfahren Sie mehr über mögliche Herausforderungen für die Sicherheit von IoT-Geräten)
- Systemschwachstellen: Systemschwachstellen sind solche, die exklusiv für eine bestimmte Maschine oder ein IT-Asset sind.
- Anwendungsschwachstellen: Anwendungsschwachstellen sind Fehler in einer Anwendung, die es Angreifern ermöglichen könnten, Böses zu tun. Sie könnten Ihre sensiblen Daten preisgeben und ihnen vollen Zugriff auf Ihr System gewähren.
- Konfigurationsschwachstellen: Dies sind Schwachstellen, die aus Fehlern wie dem Nichtändern von Passwörtern oder der Verwendung von Passwörtern zum Zugriff auf Ihre Sicherheitskameras, Heimgeräte und mehr resultieren. Sie werden meist durch fehlerhafte Konfigurationen verursacht.
Diese Schwachstellen treten aufgrund schlechter Konfiguration und Patch-Management, menschlicher Fehler wie fehlerhafter Code, unveränderter Passwörter, Installation von Apps aus nicht vertrauenswürdigen Quellen und mehr auf. Daher ist der erste Schritt im Schwachstellenmanagement, sie zu vermeiden.
Möchten Sie mehr über Risikobasiertes Schwachstellenmanagement-Software erfahren? Erkunden Sie Risikobasierte Schwachstellenverwaltung Produkte.
Warum brauchen Sie Schwachstellenmanagement?
Da Organisationen langsam auf das Paradigma der Remote-Arbeit umsteigen, ist die Bedrohung für Daten, die vor Ort oder in der Cloud gespeichert sind, höher denn je. Die Welt erlebt zunehmende Fälle von Cybersicherheitsproblemen, was bedeutet, dass Organisationen einen Schwachstellenmanagementprozess haben müssen, um Informationssicherheitsrisiken zu kontrollieren.
Selbst nachdem die Schwachstellen identifiziert wurden, ist es entscheidend zu überprüfen, ob geeignete Behebungen durchgeführt und implementiert wurden. Das Schwachstellenmanagementprogramm berücksichtigt dies. Es stellt sicher, dass sobald die Schwachstelle behoben ist, der Patch als Priorität implementiert wird und das System erneut gescannt wird, um alle Fenster für Hacker zu beseitigen, bevor die Angriffsfläche gepatcht wird.
Schwachstellenmanagement reduziert das Risiko von Cyberangriffen, Datenverletzungen und Ausfallzeiten, schützt letztendlich Ihre Daten, gewährleistet die Einhaltung von Vorschriften und spart Ressourcen.
Erfahren Sie, wie Organisationen Schwachstellenscans mit führenden Patch-Management-Tools kombinieren, um die Risikobelastung zu reduzieren.
Schwachstellenbewertung vs. Schwachstellenmanagement
Menschen verwechseln oft Schwachstellenbewertung und Schwachstellenmanagement und verwenden sie manchmal austauschbar. Aber diese beiden Begriffe sind nicht synonym.
Schwachstellenbewertung ist ein einmaliges Projekt mit einem geplanten Start- und Enddatum. Es ist kein Scan. Hier wird ein externer Sicherheitsberater oder ein Unternehmen die Vermögenswerte Ihrer Organisation prüfen und einen detaillierten Bericht über die Schwachstellen erstellen, denen Sie ausgesetzt sind. Wenn der Abschlussbericht von der externen Behörde erstellt wird, werden Behebungsmaßnahmen vorgeschlagen, der Bericht wird geliefert und der Schwachstellenbewertungsprozess endet.
Schwachstellenmanagement hingegen ist kontinuierlich und kein einmaliger Prozess. Schwachstellenbewertung kann Teil des Schwachstellenmanagementprogramms sein, aber sie sind nicht dasselbe.
Schwachstellenmanagementprozess
Die meisten Organisationen haben einen Prozess zur Verwaltung von Schwachstellen in ihrem Netzwerk, aber es fehlt immer noch an Behebung. Das Ponemon Institute befragte 1.848 IT- und IT-Sicherheitsexperten in Nordamerika, EMEA, APAC und Lateinamerika. In dem Bericht geben die meisten Befragten an, dass ihre Effektivität bei der Priorisierung und Behebung von Schwachstellen und der Sicherung von Anwendungen in der Cloud gering ist.
Dies kann auf verschiedene Gründe oder eine unsachgemäße Implementierung eines Schwachstellenmanagementprozesses zurückzuführen sein. Lassen Sie uns untersuchen, wie ein idealer Schwachstellenprozess aussehen könnte.
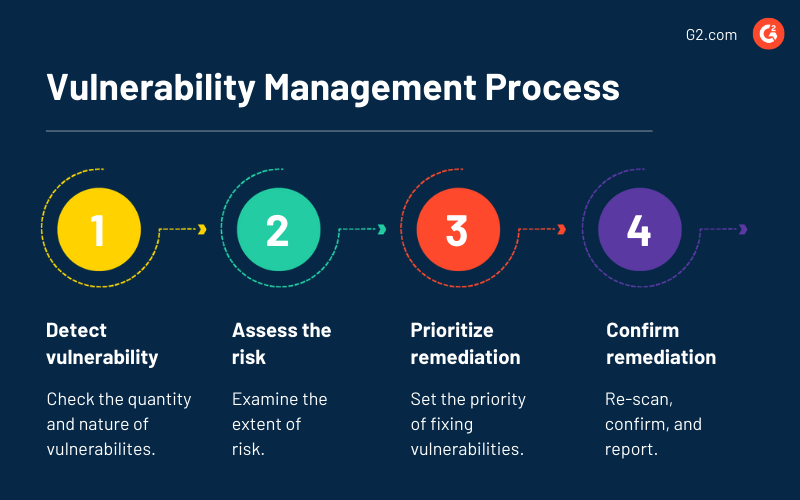
1. Schwachstelle erkennen
Bevor das Internet existierte, war ein Fehler oder Bug im System kein großes Problem. Aber jetzt, da Geräte miteinander und mit dem Internet kommunizieren, haben Sicherheitslücken exponentiell zugenommen.
Der erste Schritt, um Ihr System oder Netzwerk vor Bedrohungen zu schützen, besteht darin, die Anzahl und Art der Schwachstellen zu überprüfen, die es enthält. Dies ist keine einmalige Sache, sondern eher ein kontinuierlicher Ansatz. Sie müssen kontinuierliche Schwachstellenscans durchführen, um neue Schwachstellen zu identifizieren, sobald sie auftreten. Wenn Sie es in großem Maßstab für ein Netzwerk tun müssen, möchten Sie möglicherweise Schwachstellenscan-Tools verwenden, um den Prozess einfacher und überschaubarer zu machen.
Jetzt müssen Sie die Machbarkeit von Netzwerkscans überprüfen. Während Sie Schwachstellenscanner verwenden, sind einige Netzwerkscans relativ schnell und einfach, während andere Ihr System beeinträchtigen können. Aufgrund der Unterschiede in der Rechenleistung müssen Sie sicherstellen, dass Sie das System nicht dauerhaft beeinträchtigen oder Ausfallzeiten verursachen. Es ist ratsam, Schwachstellenmanagement-Tools zu verwenden, die den Umfang von Netzwerkscans informieren. Es wird auch dringend empfohlen, diese Scans außerhalb der Arbeitszeiten durchzuführen, um Ausfallzeiten zu vermeiden.
Jetzt haben Sie die Ergebnisse des Schwachstellenscans zur Verfügung, was tun Sie als nächstes?
2. Risiko bewerten
Risikobewertung und -management sind integrale Bestandteile des Schwachstellenmanagementprozesses, da sie Ihnen helfen, Risiken zu priorisieren. Sie müssen sich um die Risiken kümmern und diese mindern, die eine erhebliche Bedrohung für Ihr System oder Netzwerk darstellen.
Risikobasiertes Schwachstellenmanagement verlagert sich darauf, zuerst mission-kritische Schwachstellen anzugehen. Es gibt jedoch Organisationen, in denen Fachleute dazu neigen, diejenigen mit minimalem Risiko oder Fehlalarmen zu beheben. Fehlalarme sind Schwachstellen, die möglicherweise ein minimales oder kein Risiko für die Netzwerksicherheit darstellen, aber einfacher zu beheben und zu melden sind. Dies liegt hauptsächlich an der Art und Weise, wie Sicherheitsforscher incentiviert werden. Sicherheitsforscher werden nach der Anzahl der von ihnen gelösten Schwachstellen bezahlt.
Stattdessen wäre es angemessen, sie für die Maßnahme der realen Sicherheitsbedrohungen zu entschädigen, die sie minimiert haben.
Wenn Sie nun auf dieser Reise beginnen, haben Sie bereits Scans durchgeführt und einen Bericht erhalten. Es können Tausende von Schwachstellen darin enthalten sein, und Sie fragen sich vielleicht, wo Sie anfangen sollen.
Finden Sie die Ausreißer
Identifizieren Sie ein System, das eine höhere Anzahl von Schwachstellen aufweist. Beginnen Sie damit. Wenn Sie feststellen, dass dieselbe Schwachstelle in mehreren Systemen vorhanden ist, möchten Sie sie möglicherweise zuerst beheben und melden. Sie könnten sogar auf eine Anwendung stoßen, die nicht zu Ihrem System gehört und viele Schwachstellen aufweist. In diesem Fall deinstallieren Sie diese Anwendung aus dem Netzwerk.
Das Angehen der Ausreißer zuerst ist im Allgemeinen eine schnelle und einfache Möglichkeit, einen großen Unterschied zu machen, wenn Sie gerade erst anfangen. Wenn Sie nun wissen, wo Sie anfangen sollen, erstellen Sie eine Liste, wie wir es unten tun werden.
Weisen Sie separate Spalten für den Systemnamen, den Schwachstellennamen, die verantwortliche Partei, das Fälligkeitsdatum, das Datum der Behebung und den Status zu. Es ist besser, ein automatisiertes Schwachstellenmanagementprogramm zu verwenden, aber wenn Sie ein normales Repository pflegen möchten, verwenden Sie Excel, Google Sheets oder ähnliche Tabellenkalkulationstools. Mit den Tracking-Details an Ort und Stelle sind Sie bereit, Ihre gute Arbeit zu zeigen, wenn Ihre Freunde aus der Prüfungsabteilung Sie später besuchen.
Um die identifizierten Schwachstellen nach dem Risikoscore zu priorisieren, können Sie die CVSS (Common Vulnerability Scoring System) Risikoberechnungsformel verwenden und Einblicke erhalten, was und wann sie zu beheben sind. CVSS bietet eine Standardisierung zur Messung der Risiken und weist ihnen einen Risikoscore zwischen 0 und 10 zu, wobei 10 kritisch ist.
Dies wird Ihnen helfen, die Risiken zu mindern, die ernsthaften Schaden an Ihrer IT-Infrastruktur oder der Integrität der Informationen, die Sie besitzen, verursachen können.
3. Behebung priorisieren
Sobald Sie die Risikobewertung und den Risikoscore der Schwachstellen gemessen haben, beginnen Sie, sie zur Behebung zu priorisieren. Ihr nächster Schritt sollte sein, diejenigen mit dem höchsten Risikoniveau zuerst zu beheben, da sie die Sicherheit Ihrer Organisation massiv beeinträchtigen können.
Mit einer gesamten Liste von Schwachstellen möchte niemand in Hunderte von Systemen einloggen und sie einzeln von Hand aktualisieren. Es ist ineffizient und skaliert einfach nicht. Sie können Betriebssystem-Patching auf der grundlegendsten Ebene mit einem Auto-Update-Mechanismus durchführen, der eine Patch-Management-Tool Funktion ist. Sie können auch Konfigurationsmanagement verwenden, um Behebungen gegen einen Teil der Umgebung zu testen und zu sehen, ob sie Probleme verursachen.
Es ermöglicht Ihnen, Sicherheitspatches in Gruppen bereitzustellen, während Sie die Auswirkungen, die sie auf die Umgebung haben können (automatische Neustarts oder Ausfallzeiten), sicherstellen. Eine ideale Plattform ermöglicht es Ihnen, Installationen und Update-Pakete für Software zu erstellen, die nicht standardmäßig verfügbar ist. Diese Funktionalität stellt sicher, dass Sie alle Ihre Anwendungen gepatcht und auf dem neuesten Stand halten können.
4. Behebung bestätigen
Nach dem Scannen und Beheben der Schwachstellen müssen Sie sicherstellen, dass sie verschwunden sind. Mit Ihrem Sicherheitsteam, das zwischen mehreren Problemen und konkurrierenden Prioritäten jongliert, können Behebungsprüfungen in den Hintergrund gedrängt werden, aber Sie müssen verhindern, dass dies geschieht.
Einige Schwachstellen sind komplex und verschwinden nicht einfach, wenn Sie den Patch anwenden. Einige Schwachstellen scheinen eine offensichtliche Lösung zu haben, wie z.B. eine Standard-Webseite, die auf einem Server aktiviert ist. Was wie die offensichtliche Antwort aussieht, ist, die Standardseite zu deaktivieren. Aber wenn es mehrere Instanzen dieser Standardseite auf verschiedenen Ports gibt oder sie von verschiedenen Webserver-Anwendungen verwendet wird, ist die offensichtliche Lösung nicht ganz korrekt.
Einige der prominenten Schwachstellen benötigen möglicherweise mehr als einen Patch, um die Schwachstelle vollständig zu beheben. Der erste Patch zur Behebung des Problems adressiert nur einen Teil der Schwachstelle, und dann erfordert der Folgepatch, dass der erste Patch deinstalliert werden muss, bevor ein neuer installiert werden kann.
Schließlich werden viele Patches installiert, aber sie treten erst nach einem Neustart des Systems in Kraft. Ohne einen Neustart ist die Schwachstelle immer noch vorhanden. Aufgrund all dieser Faktoren müssen Sie einen weiteren Scan durchführen, um zu bestätigen, dass die Schwachstelle vollständig behoben ist. Im Falle von Schwachstellen mit hoher Schwere, die schnell behoben werden, sind dedizierte Scans zur Suche nach möglichen Risiken und Bedrohungen gerechtfertigt.
Wenn Sie Schwachstellen verfolgen und beheben, sollten Sie eine Schwachstelle nicht als behoben betrachten, bis ein Scan bestätigt hat, dass sie nicht mehr vorhanden ist.
Wer ist für das Schwachstellenmanagement verantwortlich?
Beim Aufbau eines Schwachstellenmanagementprogramms in Ihrer Organisation benötigen Sie Experten in verschiedenen Rollen. Offensichtlich wird die Verantwortung für das Schwachstellenmanagement zwischen verschiedenen Personen in der Organisation geteilt. Hier ist, wie Sie die Rollen und Verantwortlichkeiten der Personen definieren können, die mit dem Schwachstellenmanagement betraut sind:
- Sicherheitsbeauftragter: Der Sicherheitsbeauftragte besitzt den gesamten Schwachstellenmanagementprozess und ist für dessen Design und Implementierung verantwortlich.
- Schwachstelleningenieur: Der Schwachstelleningenieur ist verantwortlich für die Einrichtung der Schwachstellenscan-Tools, deren Konfiguration und die Planung verschiedener Schwachstellenscans.
- Asset-Eigentümer: Der Asset-Eigentümer ist verantwortlich für die Verwaltung der IT-Ressourcen, die vom Schwachstellenmanagementprozess gescannt werden. Sie überprüfen, ob die Schwachstellen behoben sind und die damit verbundenen Risiken akzeptiert werden.
- IT-Systemingenieur: Ein IT-Systemingenieur ist verantwortlich für die Implementierung der Behebungsmaßnahmen, die nach der Identifizierung von Schwachstellen vorgeschlagen werden.
Vorteile des Schwachstellenmanagements
Wenn es proaktiv verwaltet wird, kann das Schwachstellenmanagement die Sicherheitslage einer Organisation erheblich verbessern und das Risiko von Cyberbedrohungen reduzieren.
- Verbesserte Sicherheit: Der Hauptvorteil ist eine stärkere Verteidigung gegen Cyberangriffe. Durch die proaktive Identifizierung und Behebung von Schwachstellen machen es Organisationen Angreifern viel schwerer, sich in ihren Systemen festzusetzen.
- IVerbesserte Reaktionen auf Bedrohungen: Schwachstellenmanagement hilft, Bedrohungen basierend auf ihrer Schwere zu priorisieren, sodass IT-Teams sich zuerst auf die kritischsten Probleme konzentrieren können. Diese schnellere Reaktionszeit minimiert potenzielle Schäden durch Angriffe.
-
Erhöhte betriebliche Effizienz: Die Automatisierung von Schwachstellenscans und Patch-Prozessen entlastet das IT-Personal, damit es sich auf andere Sicherheitsaufgaben konzentrieren kann. Darüber hinaus vermeiden Organisationen durch die Verhinderung erfolgreicher Angriffe die Störungen und Kosten, die mit Ausfallzeiten und Datenverletzungen verbunden sind.
-
Erhöhte Sichtbarkeit: Schwachstellenmanagement-Tools bieten umfassende Berichte über die Sicherheitslage eines Unternehmens. Diese verbesserte Sichtbarkeit ermöglicht es IT-Teams, fundierte Entscheidungen über Sicherheitsinvestitionen zu treffen und den Fortschritt im Laufe der Zeit zu verfolgen.
- Einhaltung von Vorschriften: Viele Branchen haben Vorschriften, die Organisationen dazu verpflichten, ein Schwachstellenmanagementprogramm zu haben. Ein starkes Programm hilft, die Einhaltung dieser Vorschriften sicherzustellen und potenzielle Geldstrafen zu vermeiden.
Herausforderungen des Schwachstellenmanagements
Das Schwachstellenmanagement steht vor mehreren Hürden. Organisationen können Schwierigkeiten haben, eine genaue Liste aller Geräte und Bestände zu führen. Wenn es eine überwältigende Anzahl von Schwachstellen gibt, kann die Priorisierung und das Vorhandensein von genügend Personal und Ressourcen, um sie alle zu adressieren, eine Herausforderung sein.
Selbst mit Automatisierung bleibt die genaue Erkennung und Priorisierung von Schwachstellen schwierig, und veraltete Scanmethoden können kritische Bedrohungen übersehen. Der ständige Strom neuer Schwachstellen bedeutet, dass es ein fortwährender Kampf ist, aber mit einem strukturierten Ansatz und den richtigen Tools können Organisationen erhebliche Fortschritte machen.
Sagen Sie teuren IT-Schwachstellen Lebewohl
Sobald Sie ein solides Verständnis dafür haben, wie Schwachstellen identifiziert, bewertet, behoben und bestätigt werden, können Sie mit dem Aufbau Ihres Schwachstellenmanagementprogramms beginnen.
Natürlich ist es kein Einheitsansatz. Ihr Schwachstellenmanagementprogramm kann auf organisatorische Herausforderungen stoßen. Bevor Sie also einen robusten Prozess aufbauen, führen Sie zuerst die Scans durch, um eine Vorstellung davon zu bekommen, wie groß Ihr Problem ist. Verwenden Sie Schwachstellenscanner, wenn Sie eine breite Palette von IT-Ressourcen haben, die Tausende von Schwachstellen liefern können.
Überprüfen Sie, ob Sie spezifische regulatorische Anforderungen haben, die zuerst erfüllt werden müssen. Basierend auf Rollen und Verantwortlichkeiten, Service Level Agreements, Eskalationen und mehr, beginnen Sie mit dem Aufbau Ihres Schwachstellenmanagementprogramms mit den besten verfügbaren Tools.
Möchten Sie Ihre Organisation vollständig vor externen Bedrohungen schützen? Entdecken Sie, wie Penetrationstests Ihnen helfen können, ein unzerbrechliches Sicherheitsframework aufzubauen.
Dieser Artikel wurde ursprünglich im Jahr 2020 veröffentlicht. Er wurde mit neuen Informationen aktualisiert.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.