Intelligent automation is making impacts across technology markets. And due to an enormous labor shortage in one of those markets—cybersecurity—automation has become incredibly important.
Companies are encountering hiring difficulties, using underskilled staff, and juggling dozens of tools at once—these struggles have real implications. Underskilled and shorthanded staff are more likely to expose information and use tools improperly; this is on top of the risk, and potential consequences, of leaving security positions open and unattended for months.
One potential solution: specialized system security software. While it doesn’t completely answer the skills gap question, security orchestration, automation, and response (SOAR) platforms are designed to simplify and automate huge amounts of security tasks, making teams leaner, more effective, and more efficient.
What is SOAR?
SOAR Platform
In essence, a SOAR platform is an automation engine connected to every security tool running on a network or in an environment. SOAR becomes the center of a security operations team, as it manages and automates remediation activities while providing visibility across networks, cloud environments, and on-premises resources.
Companies integrate SOAR platforms with existing security solutions, where teams define and establish specific operational logic and security policies. The platform then uses contextual information from a company’s security information and event management (SIEM) tool to identify anomalies and malfunctions. SOAR platforms also integrate with firewall software, incident response tools, CASB software, and pretty much any other security tool available to businesses.
SOAR vs. SIEM: More than a SIEM complement
Businesses use security event information and information management (SIEM) solutions to collect and store information about endpoints, networks, and other IT assets. Teams typically do this by placing an agent on each device to gather data and monitor activity. This information is used to identify abnormal activity, security incidents, and any other kind of attack.
SOAR takes the next operational step. After integrating the SOAR solution with an SIEM and processing its stored information, the SOAR tool can integrate with additional security tools to automate workflow tasks. For example, SOAR users will typically add an incident response tool to the platform to automate remediation as incidents arise. They may also integrate security or vulnerability analysis tools to add contextual information to risk engines. There are endless possibilities, but they all revolve around the logic set by security teams and the operations they wish to automate. For example, triggers can be set to automatically isolate a device if malware is detected. Systems can continuously scan for anomalies and automate investigation and remediation once discovered.
SOAR is not a replacement for SIEM solutions; in reality, SIEM powers SOAR. The SIEM provides all the contextual data and security information necessary to train the SOAR platform to identify anomalies and automate their remediation.
What’s driving SOAR adoption?
There are numerous benefits to this emerging technology, first described in 2017. While specific SOAR products boast varying features, commonalities among their benefits include increased efficiency and visibility for security operations teams—through both integration and automation.
Operational Efficiency
Put simply, automation makes employees' jobs easier. SOAR platforms allow teams to set priorities and build a workflow for security events that require minimal human effort. Teams establish operational norms through logic and policies, which SOAR products constantly compare and reference to detect anomalies. If detection and remediation are automated, teams have more time to find the root cause of an issue and prevent it from happening again. Additionally, in the event of a major security incident, these products can instantly alert teams for a quick response.
Response Efficacy
The earlier security teams can detect an issue, the easier they can resolve it. Legacy systems may have the capability to alert one individual of an event, send an email to another for investigation, and ping another for remediation. SOAR solutions allow simple issues to be detected and remediated automatically. Other, more complex issues can be investigated using integrated tools and aggregated forensic information collected by SIEM software. Once the information is analyzed, investigation teams can present the data to incident response staff before they’re even aware of the incident, drastically reducing the time spent from discovery to remediation.
Risk Reduction
Risk reduction is achieved with SOAR by simplifying the incident and vulnerability prioritization process. Vulnerability management is one of the biggest processes SOAR can impact. Companies may have hundreds of configurations to examine, but risk-based, intelligent prioritization helps companies tackle issues with the biggest impact through identifying critical resources potentially impacted by major issues. Simple issues can be remediated automatically (or saved for later) while security teams address the problems facing business-critical systems.
News in the SOAR market
Though SOAR technology has only been around a few years, the space is already expected to surpass $2 billion by 2025, expanding at 16% CAGR during the period, according to KBV Research.
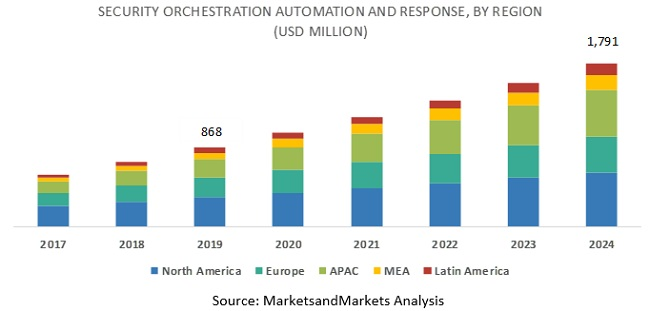
Image Courtesy: MarketsandMarkets
That activity came in many forms.
Some of it came in the form of new products from major players in the security world. And while a number of SIEM vendors have emerged organically, buy-in from tech giants like Rapid7 and FireEye in the last few years have given the market credibility.
Acquisitions added legitimacy to the market as well. In the last few years, SOAR-related startups have been devoured by security vendors:
- In addition to launching its SOAR platform InsightConnect in 2018, Rapid7 has bolstered its tech with the acquisition of three SOAR-related startups: NetFort, tCell, and Komand.
- Splunk acquired VictorOPs and Phantom in 2019 to build out Splunk Enterprise Security and automate security operations through Splunk Phantom Security Orchestration.
- Palo Alto Networks acquired Demisto, a Leader in G2’s SOAR category, and Fortinet bought Cybersponse in 2019.
The list goes on. Acquisitions may steal the headlines, but SOAR providers partnering with tech, consulting, and finance institutions drove lots of market growth. Most of these have come in two forms: enterprise cloud services case studies and agreements with managed services providers (MSP).
LogRythm began a partnership with Dell EMC in 2016 to integrate solutions while adding security automation and analytics to Dell EMC’s products. The next year, ThreatConnect started collaborating with CenturyLink; Rapid7 partnered with Microsoft; and Demisto worked with AWS; all added security automation to their products and services.
Splunk started the MSP partnerships in 2016 while working with Accenture to automate security for Accenture’s application services. LogRythm followed suit in 2017 to do the same for Deloitte. Since then, a number of other consulting, insurance, and services providers, have partnered with SOAR solution providers to expand the functionality of their products or outsource parts of their services.
The future of security operations
These security trends will continue through 2020 and beyond.
For the enterprise, this means more collaborative work between security vendors and services providers to improve security automation for their businesses and customers.
For security teams, the biggest impact will be an easier job: achieving automation and visibility, running security solutions in unison, and developing response workflows. This empowers security teams to identify and prioritize issues based on their own unique goals or needs. Moreover, they can waste less time on minor issues and score risks accordingly to optimize the impact of each second they spend working.
This should impact a substantial amount of enterprise security teams. By 2022, nearly one-third of enterprise organizations will be staffed by five or more security professionals. That number will skyrocket from 5% today, according to Gartner.
Future security teams powered by SOAR will be better equipped than ever to analyze risks, discover security issues, and quickly remediate threats.
Want to learn more about Vulnerability Management Software? Explore Vulnerability Management products.

Aaron Walker
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.