Forensik ist eine so gefragte Fähigkeit, und dank zahlreicher Krimiserien bin ich überzeugt, dass es einfache Arbeit ist. Vielleicht kannst du das nachvollziehen?
Wir alle wissen, dass die Realität – ganz anders – ist, besonders wenn wir in die Welt der digitalen Ermittlungen eintauchen.
Die traditionelle forensische Wissenschaft untersucht und analysiert geschickt physische Beweise im Bereich von Verbrechen und Vorfällen, aber digitale Forensik ist wie die Suche nach der Nadel im Heuhaufen. Das Aufdecken von Beweisen und Erkenntnissen erfordert ein spezialisiertes Set von Werkzeugen und Techniken. Netzwerkforensik, die Wissenschaft der Untersuchung von Aktivitäten in den weit verzweigten Netzwerken, entstand, um diesen Anforderungen gerecht zu werden.
Was ist Netzwerkforensik?
Netzwerkforensik ist ein Zweig der digitalen oder Computerforensik. Sie überwacht und analysiert den Netzwerkverkehr, Ereignisse, Protokolle und Kommunikationsmuster nach Cybersecurity-Vorfällen, um Informationen zu sammeln, rechtliche Beweise zu sichern und Eindringlinge zu identifizieren.
Experten für digitale Forensik verlassen sich auf Netzwerkforensik, um Ereignisse zu rekonstruieren, die Absicht zu verstehen und präventive Maßnahmen in Gang zu setzen, um zukünftige Vorfälle zu vermeiden. Lösungen wie digitale Forensik-Software und Netzwerkverkehrsanalyse (NTA) Tools für Netzwerkforensik-Untersuchungen erleichtern die Arbeit.
Die Bedeutung der Netzwerkforensik
Kürzlich wurde ein ehemaliger Apple-Mitarbeiter für schuldig befunden, die Geschäftsgeheimnisse des iPhone-Herstellers gestohlen zu haben, Tage vor seinem Rücktritt aus dem Unternehmen. Wie wurde er erwischt? Seine Computernetzwerkaktivität hat ihn verraten.
Mehrere Sicherheitstools schützen vor Cyberangriffen. Aber wenn ein Angriff oder Sicherheitsvorfall bereits passiert ist, bleibt nur die Verbesserung der Reaktions- und Milderungsstrategien.
Man muss eine Ursachenanalyse der Angriffe durchführen, herausfinden, ob der Sicherheitsvorfall unter Kontrolle ist oder nicht, und ob alle vom Angriff betroffenen Systeme gefunden wurden. Denken Sie daran: Heutige Cyberangriffe betreffen mehrere Geräte in einem Netzwerk.
Nach einem Angriff sammelt die Computer- oder digitale Forensik alle elektronischen Beweise des Sicherheitsvorfalls. Sie konzentriert sich auf Datenwiederherstellung und Dateisystemanalyse. Allerdings offenbart die Festplatte heute nur einen kleinen Teil der Geschichte in der Internetwelt. Computerforensik allein reicht nicht aus, da Hacker möglicherweise alle Protokolldateien auf einem kompromittierten Host löschen können.
Die einzigen Beweise, die für die forensische Analyse verfügbar sind, könnten im Netzwerk liegen, und in diesem Fall ist die Netzwerkforensik am hilfreichsten. Schließlich sind Netzwerke das grundlegende Mittel zum Austausch von Informationen und Kommunikation für jede Einzelperson, jedes Unternehmen und jede Organisation.
2,2 Milliarden Dollar
ist der geschätzte Umsatz des globalen Marktes für Netzwerkforensik bis 2027.
Quelle: Markets and Markets
Netzwerkforensik untersucht alle Arten von Angriffen, indem sie eingehende und ausgehende Verkehrsmuster analysiert. Sie stellt jede Transaktion wieder her – E-Mails, Sofortnachrichten, Dateitransfers – und rekonstruiert den Austausch. Diese Informationen führen zur Quelle des Angriffs. Ermittler können dann ein vollständiges Bild des Cybersecurity-Vorfalls mithilfe netzwerkbasierter Beweise zusammensetzen.
Netzwerkforensik ist besonders hilfreich, wenn der Angriff im Gange ist und man die Hacker nicht darauf aufmerksam machen möchte, dass man ihnen auf der Spur ist.
Wer nutzt Netzwerkforensik?
Organisationen, die Netzwerkforensik-Tools für Verkehrs- und Datenanalyse verwenden, sind unter anderem:
- Strafverfolgungsbehörden
- Militär und Regierungsbehörden
- Unternehmen und Betriebe
- Akademische und Forschungseinrichtungen
- Cybersecurity-Unternehmen
Möchten Sie mehr über Digitale Forensik-Software erfahren? Erkunden Sie Digitale Forensik Produkte.
Computer- und Netzwerkforensik
Bis jetzt haben Sie vielleicht begonnen zu verstehen, dass Computerforensik sich von Netzwerkforensik unterscheidet. Aber hier ist eine kurze Zusammenfassung, um sicherzustellen, dass Sie auf dem neuesten Stand sind.
Digitale oder Computerforensik beinhaltet die Untersuchung und Analyse von ruhenden Daten. Sie umfasst die sorgfältige Untersuchung und Analyse digitaler Geräte, um bei Ermittlungen zu helfen, die von Cybermobbing bis zu Datenverletzungen reichen.
Netzwerkforensik ist ein Zweig der Computerforensik, der sich mit Daten in Bewegung befasst und mit flüchtigen und dynamischen Informationen umgeht. Sie spielt eine entscheidende Rolle dabei, uns zu helfen, die Interaktionen und Aktivitäten zu verstehen, die zwischen Geräten in einem Netzwerk stattfinden.
Schlüsselanwendungen der Netzwerkforensik
Von der Stärkung der Cybersecurity-Position bis zur Sammlung digitaler Beweise, hier ist, wie verschiedene Organisationen Netzwerkforensik nutzen.
- Cybersecurity-Operationen: Netzwerkforensik hilft Sicherheitsteams, effektiv zu reagieren, um Bedrohungen durch Eindringlinge, Malware oder unbefugten Zugriff zu mindern.
- Vorfallreaktion: Vorfallreaktionsteams wenden Netzwerkforensik an, um den Umfang, die Auswirkungen und die Eintrittspunkte von Angriffen zu verstehen. Ihre Arbeit erleichtert die schnelle Eindämmung und Wiederherstellung in Echtzeit.
- Rechtliche Ermittlungen: Strafverfolgungsbehörden und private Ermittler nutzen Netzwerkforensik, um Netzwerkaktivitäten und Kommunikationsmuster in Fällen von Cyberkriminalität, Datenverletzungen und Online-Betrug zu analysieren.
- Insider-Bedrohung-Erkennung: Durch die Überwachung von Netzwerkaktivitäten auf ungewöhnliche oder unbefugte Handlungen von Mitarbeitern oder Auftragnehmern identifiziert die Netzwerkforensik Insider-Bedrohungen.
- Netzwerkleistungsoptimierung: Über die Sicherheit hinaus können Netzwerkadministratoren Netzwerkforensik nutzen, um Leistungsprobleme zu analysieren, Engpässe zu identifizieren und die Datenübertragung zu optimieren.
- Forschung und Entwicklung: Forscher erkunden Netzwerkforensik-Untersuchungen, um ihre Techniken zur Erkennung und Verhinderung von Cyberbedrohungen zu verbessern. Dies trägt zur sich entwickelnden Landschaft der Cybersecurity-Lösungen bei.
- Aus den Anwendungsfällen können Sie sehen, dass Netzwerkforensik eine Erweiterung der Netzwerksicherheit ist, die traditionell die Erkennung und Verhinderung von Netzwerkangriffen betont.
Wie funktioniert Netzwerkforensik
Schwere Cyberangriffe wie Ransomware oder Lieferkettenangriffe beginnen oft mit einem einzigen Fall von unbefugtem Zugriff auf das Zielsystem. Von diesem einzigen Einstiegspunkt aus bewegen sich Hacker durch verschiedene Geräte wie Router, Firewalls, Hubs und Switches in und aus dem System. Netzwerkforensik identifiziert und analysiert all diese netzwerkbasierten Beweise, um zu verstehen, was passiert ist.
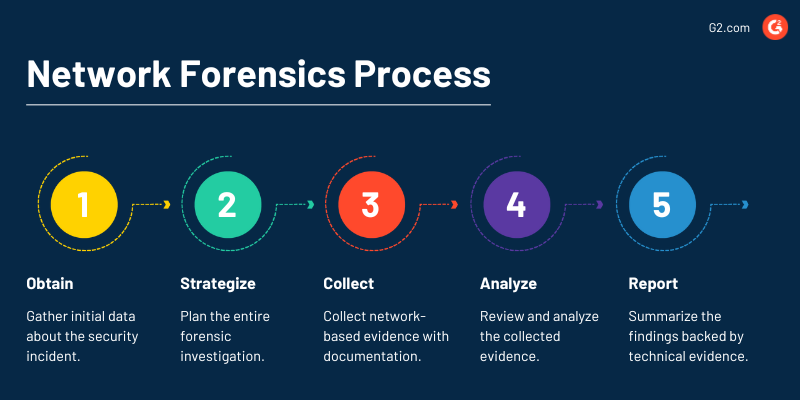
Netzwerkforensik-Prozess
Die fünf wichtigsten Schritte zur Netzwerkforensik-Untersuchung sind:
- Erhalten
- Strategisieren
- Sammeln
- Analysieren
- Berichten
Oder OSCAR. Dieses Framework, das auch in der digitalen Forensik verwendet wird, gewährleistet genaue und aussagekräftige Ergebnisse.
1. Informationen erhalten
Netzwerkforensik-Ermittler sammeln erste Informationen über den Vorfall und die betreffende Netzwerkumgebung. Dazu gehören Details zum Datum und zur Uhrzeit des Vorfalls, beteiligte Personen, Systeme und Endpunkte sowie ergriffene Maßnahmen. Diese Daten zeigen ihnen wichtige Details über den Vorfall.
2. Strategisieren
Dieser Schritt beinhaltet die Planung der gesamten forensischen Untersuchung, da Netzwerkdaten flüchtig sind und sich in ihrer Natur unterscheiden. Fachleute behalten die folgenden Punkte im Auge, während sie ihren Prozess entwickeln:
- Ziele der Untersuchung
- Zeitplan
- Quelle und Stärke der Beweise
- Benötigte Ressourcen und Personal
- Zeitpunkt der Updates
Strategisieren hilft, die Richtung der Untersuchung zu bestimmen und zu priorisieren, welche Beweise zuerst gesammelt werden müssen.
3. Beweise sammeln
Das Sammeln von Beweisen umfasst die Dokumentation aller Systeme, die zugegriffen und verwendet werden, das Erfassen und Speichern von Netzwerkdatenströmen auf Festplatten und das Sammeln von Protokollen von Firewalls und Servern. Die Dokumentation muss die Zeit, die Quelle der Beweise, die Erfassungsmethode und die beteiligten Ermittler enthalten.
Quellen für die Netzwerkforensik-Analyse
Eine Untersuchung erfordert oft das Sammeln von Beweisen aus verschiedenen Quellen, um zu verstehen, was passiert ist. Hier sind einige gängige Quellen, in denen Sie während einer Untersuchung Netzwerkdaten finden können:
- Netzwerkverkehrsdaten umfassen die Informationen, die zwischen Netzwerkgeräten ausgetauscht werden. Tools wie Paketaufnahmelösungen, Paket-Sniffer oder Netzwerküberwachungssysteme zeichnen die Daten auf.
- Protokolle von Routern und Switches verfolgen die Kommunikation zwischen Netzwerksegmenten.
- Proxy-Netzwerkserver-Protokolle überwachen Benutzeranfragen und -antworten, um Details über besuchte Websites, Zugriffszeiten und Benutzeraktivitäten bereitzustellen.
- Firewall-Protokolle zeichnen versuchte Verbindungen, erlaubten oder verweigerten Verkehr und Regelverletzungen auf.
- Intrusion Detection and Prevention Systems (IDPS) Alarme werden generiert, wenn sie verdächtige oder bösartige Aktivitäten erkennen.
- Domain Name System (DNS)-Protokolle enthalten Domain-Abfragen, Internetprotokoll (IP)-Adressen und von Benutzern besuchte Websites.
- E-Mail-Server-Protokolle speichern Daten über eingehenden und ausgehenden E-Mail-Verkehr, einschließlich Absender- und Empfängeradressen und Zeitstempel.
- Authentifizierungsprotokolle führen Aufzeichnungen über erfolgreiche und fehlgeschlagene Anmeldeversuche, um Benutzeraktivitäten und potenziellen unbefugten Zugriff nachzuverfolgen.
- Server-Protokolle von Datenbanken, Anwendungen und Webservern liefern Informationen über Benutzeranfragen, Transaktionen und Aktivitäten.
- Protokolle von drahtlosen Zugangspunkten dokumentieren drahtlose Geräte, die sich mit dem Netzwerk verbinden. Diese Aktion ist Teil der drahtlosen Forensik, einem Zweig der Netzwerkforensik.
4. Beweise analysieren
Diese Kernphase überprüft die Beweise mithilfe mehrerer manueller und automatisierter forensischer Techniken, um Datensätze von verschiedenen Netzwerkgeräten zu korrelieren. Die Analyse beginnt typischerweise mit einigen ersten Hinweisen wie:
- Alarme von Intrusion Detection Systems
- Auffällige Muster, die Anzeichen von Angriffen wie Denial of Service oder Vireninfektionen zeigen
- Protokollanomalien
- Abweichungen von Baselines des normalen Netzwerkverhaltens wie ungewöhnliche Verkehrsmuster oder unerwartete Netzwerkprotokolle oder Portfehler oder anderes abnormales Netzwerkverhalten
Die Korrelation all dieser Daten erstellt eine Zeitleiste der Ereignisse und entwickelt Arbeitstheorien darüber, wie der Angriff stattgefunden hat. Die Analyse kann zur weiteren Sammlung von Beweisen aus zusätzlichen Quellen führen.
5. Berichterstattung
Die Netzwerkforensik-Ermittler fassen ihre Ergebnisse basierend auf den technischen Beweisen zusammen, die sie gesammelt und analysiert haben. Der Bericht sollte einfach sein, damit auch Laien ihn verstehen können.
Methoden zur Netzwertdatensammlung in der Netzwerkforensik
Die Netzwertdatensammlung ist ein grundlegender Schritt im Netzwerkforensik-Prozess. Die Sammlung erfolgt durch zwei Methoden.
1. Catch it as you can-Methode
Der "Catch it as you can"-Ansatz erfasst und analysiert den Netzwerkverkehr, während er einen bestimmten Punkt im Netzwerk durchläuft, alles auf einmal, d.h. im Batch-Modus. Diese Methode erfordert eine große Menge an Speicherplatz, um die Menge der eingehenden Daten für die Analyse zu bewältigen.
2. Stop-look-listen-Methode
Bei diesem Ansatz werden Netzwerkpakete rudimentär im Speicher analysiert, und nur ausgewählte Netzwerkdaten, die für eine weitere Analyse als wertvoll erachtet werden, werden aufgezeichnet. Dadurch wird nicht so viel Speicher benötigt.
Best Practices beim Sammeln netzwerkbasierter Beweise
- Minimieren Sie Interaktionen mit dem Netzwerk, um eine Veränderung der Beweise zu verhindern.
- Sammeln Sie Daten passiv, wann immer möglich, und vermeiden Sie Änderungen, die laufende Aktivitäten beeinflussen könnten.
- Verwenden Sie Industriestandard-Tools für die Beweissammlung, um Genauigkeit zu gewährleisten.
- Machen Sie Kopien aller Beweise und erzeugen Sie kryptografische Hashes zu deren Verifizierung.
- Arbeiten Sie an Kopien der Beweise anstelle der Originale.
- Führen Sie eine Beweiskette, indem Sie alle Schritte der Beweishandhabung dokumentieren.
Herausforderungen in der Netzwerkforensik
Die anfängliche und wichtigste Herausforderung bei der Netzwerkforensik dreht sich um die Vorbereitung der Infrastruktur für die Untersuchung. Sie sollte sicherstellen, dass die erforderlichen Daten für eine vollständige Untersuchung vorhanden sind. Es ist jedoch keine leichte Aufgabe, und Ermittler stehen vor zahlreichen Herausforderungen bei ihrer Arbeit.
- Datenvolumen und Speicher: Da Netzwerke große Datenmengen erzeugen, stellen Speicherung und Verwaltung Probleme dar. Effiziente Speicherlösungen sind notwendig, um relevante Daten für die Analyse zu behalten, während die Speicherkapazitäten nicht überlastet werden.
- Verschlüsselung: Internetverbindungen sind oft mit Transport Layer Security (TLS) und Secure Socket Layer (SSL) Verschlüsselungen geschützt. Während Verschlüsselung vorteilhaft für den Schutz von Daten ist, macht verschlüsselter Verkehr aus forensischer Sicht die Analyse ohne Entschlüsselungsschlüssel schwierig.
- Datenintegrität: Bei der Integrität der gesammelten Daten darf es keine Kompromisse geben. Wenn jemand die gesammelten Daten manipuliert oder beschädigt, könnte das Ergebnis der Netzwerkforensik-Analyse negativ beeinflusst werden.
- Datenschutzbedenken: Ein Gleichgewicht zwischen effektiver Forensik und dem Respektieren der Privatsphäre der Benutzer zu finden, wird kompliziert, wenn gesammelte Daten private oder sensible Informationen enthalten. Die Situation erfordert eine ordnungsgemäße Handhabung und starke Zugangskontrollmaßnahmen.
- Ressourcenbeschränkungen: Der Umgang mit begrenzten Ressourcen ist eine große Herausforderung in der Netzwerkforensik, da es viele Menschen, Computerleistung und Zeit erfordert, um Daten aus verschiedenen Quellen zu aggregieren und zu analysieren.
Netzwerkforensik-Tools
Verwenden Sie das richtige Set von Netzwerkforensik-Tools, um die genannten Herausforderungen zu mindern. Diese fünf Software-Tools decken verschiedene Aspekte der Netzwerk-Infrastruktur ab und helfen beim forensischen Prozess.
1. Netzwerkverkehrsanalyse-Software
Moderne NTA-Tools konzentrieren sich auf die Analyse von Netzwerkverkehrsmustern und Paketen, indem sie Daten wie Quell- und Ziel-IP-Adressen, Ports, Verkehrsprotokolle und Verkehrsvolumen sammeln und analysieren. IT- und Sicherheitsteams verwenden sie, um Netzwerksicherheitsbedrohungen zu identifizieren, den Datenfluss zu überwachen und forensische Untersuchungen durchzuführen.
Top 5 NTA-Tools
- IBM Security QRadar SIEM
- Check Point Next Generation Firewalls (NGFWs)
- Progress WhatsUp Gold
- Arista NDR
- FortiAnalyzer
2. Netzwerküberwachungssoftware
Netzwerküberwachungssoftware zeigt Ihnen Ihr gesamtes Netzwerk und behandelt verschiedene Aspekte von Netzwerkomponenten, Geräten und Verkehr. Während Netzwerküberwachungstools hauptsächlich für die Echtzeitverfolgung, Analyse und Optimierung von Netzwerkaktivitäten verwendet werden, erzeugen sie auch eine Fülle von Werten für forensische Untersuchungen nach Sicherheitsvorfällen oder -verletzungen.
Top 5 Netzwerküberwachungssoftware-Plattformen
* Oben sind die fünf führenden Netzwerküberwachungslösungen aus dem G2 Fall 2024 Grid® Report.3. IDPS
Intrusion Detection and Prevention Software ist ein wichtiger Bestandteil der Netzwerkforensik und -sicherheit. IDPS kann helfen, unbefugten Zugriff auf Netzwerke und Systeme zu erkennen und zu verhindern. Es funktioniert, indem es Netzwerkpakete, Systemprotokolle und andere Datenquellen analysiert, um Anzeichen von bösartigen Aktivitäten oder Richtlinienverletzungen zu identifizieren.
Top 5 IDPS-Lösungen
- Palo Alto Networks Threat Prevention
- Palo Alto Networks Next-Generation Firewall
- Hybrid Cloud Security
- Blumira Automated Detection & Response
- AlienVault USM (von AT&T Cybersecurity)
* Oben sind die fünf führenden IDPS-Lösungen aus dem G2 Fall 2024 Grid® Report.
4. Digitale Forensik-Software
Digitale Forensik-Software ist darauf ausgelegt, digitale Beweise von Computern, mobilen Geräten, Speichermedien und Netzwerken zu sammeln, zu analysieren und zu interpretieren. Während ihr Hauptfokus auf der Analyse digitaler Artefakte liegt, spielt sie auch eine Rolle in der Netzwerkforensik.
Beachten Sie, dass die hier erwähnten spezialisierten netzwerkbezogenen Forensik-Tools fortschrittlichere Funktionen bieten, die auf Netzwerkforensik-Untersuchungen zugeschnitten sind.
Top 5 digitale Forensik-Software
- IBM Security QRadar SIEM
- Belkasoft
- Microsoft Purview Audit
- Magnet Forensics
- SentinelOne Singularity RemoteOps Forensics
* Oben sind die fünf führenden digitalen Forensik-Lösungen aus dem G2 Fall 2024 Grid® Report.
5. Security Information and Event Management (SIEM)-Systeme
SIEM-Systeme bieten zentrale Sichtbarkeit, Ereigniskorrelation und erweiterte Analysefähigkeiten. Sie helfen Organisationen, potenzielle Schwachstellen und Sicherheitsvorfälle zu untersuchen und darauf zu reagieren. Viele SIEM-Lösungen integrieren sich mit anderen Netzwerkforensik-Tools, um umfassende Sicherheits- und Untersuchungskapazitäten zu bieten.
Top 5 SIEM-Lösungen
- Microsoft Sentinel
- IBM Security QRadar SIEM
- Splunk Enterprise Security
- Splunk Enterprise
- AlienVault USM (von AT&T Cybersecurity)
* Oben sind die fünf führenden SIEM-Lösungen aus dem G2 Fall 2024 Grid® Report.
Die hier erwähnten Tools, wie NTA-Software, digitale Forensik-Plattformen, IDPS und SIEM-Lösungen, bieten einzigartige Fähigkeiten, die sich innerhalb einer umfassenden Netzwerkforensik-Untersuchung ergänzen. Berücksichtigen Sie die Bedürfnisse, Ziele und Ressourcen Ihrer Organisation, um zu entscheiden, welche Kombination von Tools am besten zu Ihrer Untersuchungsstrategie passt.
"Berücksichtigen Sie, dass verschiedene Tools unterschiedliche Arten und Größen von Artefakten sammeln und analysieren. Je nachdem, wie viele Daten Sie speichern können und was Sie in großem Maßstab analysieren können, könnten Sie es vorziehen, Tools zu verwenden, um vollständige Paketaufnahmen, nur Segmente von Netzwerkverbindungen oder nur Netzwerkmetadaten zu speichern", sagt Giorgio Perticone, der beratende Analyst für Bedrohungserkennung und -reaktion bei Vectra AI.
"Diese Entscheidung kann Ihre forensischen Fähigkeiten drastisch verändern und sollte sorgfältig im Voraus getroffen werden", fügt Perticone hinzu.
Karriere in der Netzwerkforensik
Mit der zunehmenden Bedeutung der Netzwerkforensik steigt auch die Nachfrage nach Cybersecurity- und IT-Fachleuten, die in diesem Bereich qualifiziert sind, von großen Unternehmen, Strafverfolgungsbehörden und Cybersecurity-Firmen.
Eine schnelle Suche auf LinkedIn nach "Netzwerkforensik"-Karrieren liefert Tausende von Jobs allein in den Vereinigten Staaten, mit Titeln wie:
- Analyst für Computernetzwerkverteidigung
- Analyst für digitale Netzwerkausbeutung
- Ermittler für Cyberreaktionen
- Ermittlungs- und Forensikanalyst
- Analyst für Bedrohungsinformationen
- Sicherheitsanalyst
Sicherheits- und Netzwerkanalysten benötigen mindestens einen Bachelor-Abschluss in Informatik, Cybersecurity oder einem verwandten Bereich. Netzwerkanalysten müssen auch mit Netzwerkprotokollen und Verkehrsanalyse vertraut sein und sich mit Tools wie Paketanalysatoren und Protokollanalyse-Software wohlfühlen.
Bereit für die Jagd?
Jede Organisation, die digitale Forensik als Teil ihrer Sicherheitsstrategie in Betracht zieht, sollte den mächtigen Zweig der Netzwerkforensik nutzen, um ihre Verteidigung zu stärken. Indem sie dies tun, können Organisationen im anhaltenden Kampf gegen sich entwickelnde Cyberbedrohungen einen Schritt voraus bleiben.
Neugierig, mehr zu erfahren? Tauchen Sie in diesen Artikel über Netzwerkverkehrsanalyse und wie sie die Netzwerksicherheit stärkt.
Dieser Artikel wurde ursprünglich 2023 veröffentlicht. Er wurde mit neuen Informationen aktualisiert.

Soundarya Jayaraman
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.
.png)