Unternehmen werden ständig mit sensiblen Kundeninformationen betraut, wie z.B. finanziellen und biometrischen Informationen, und mit persönlichen Daten kommt eine große Verantwortung, die Privatsphäre und Vertraulichkeit zu gewährleisten.
Betreten Sie die Welt des Datenmaskierens, die gut gehütete Technik gegen neugierige Blicke und Sicherheitsbedrohungen.
Was ist Datenmaskierung?
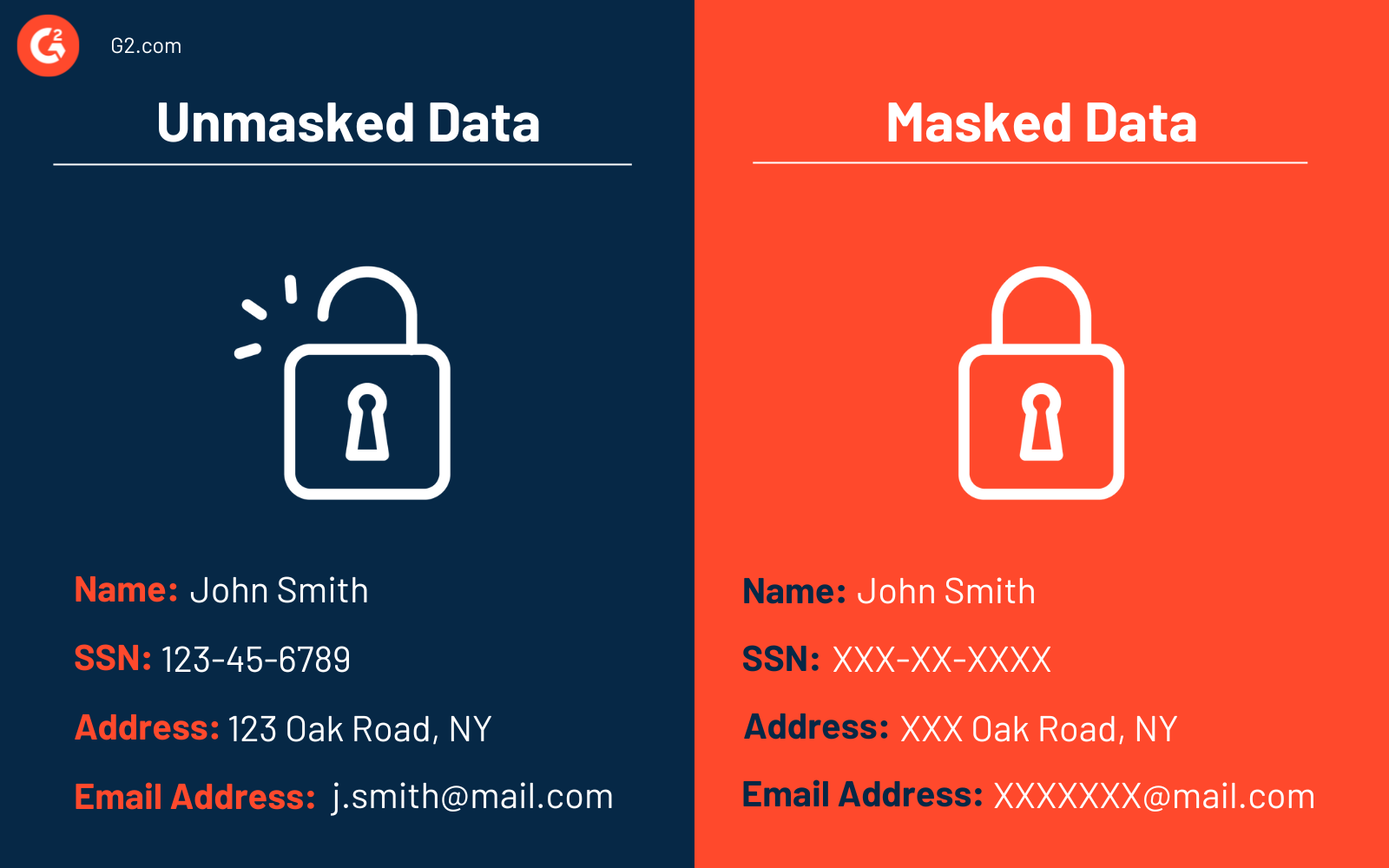
Datenmaskierung bezieht sich auf die Modifizierung oder den Ersatz von ursprünglichen sensiblen Daten, um sie vor unbefugten Augen zu schützen, während ihre Nützlichkeit für autorisierte Benutzer in Produktions- und Testumgebungen erhalten bleibt.
Datenmaskierungssoftware hilft Organisationen, ihre Daten zu schützen. Diese Tools verschlüsseln Daten, bieten konsistente Maskierungsmethoden und ermöglichen das Anlegen und Entfernen von Masken basierend auf spezifischen Regeln.
Warum ist Datenmaskierung wichtig?
Datenmaskierung spielt eine entscheidende Rolle beim Schutz sensibler Informationen vor Sicherheitsrisiken wie Datenverletzungen und Cyberangriffen. Wenn ein Sicherheitsverstoß auftritt, hilft die Datenmaskierung, indem sie sicherstellt, dass die exponierten Daten nicht echt oder sensibel sind, wodurch die Auswirkungen des Verstoßes reduziert werden.
Da die maskierten Daten eine fiktive Darstellung der ursprünglichen Informationen sind, können Angreifer, selbst wenn sie Zugang erhalten, die Daten nicht für böswillige Zwecke wie Identitätsdiebstahl oder Betrug missbrauchen. Dies fügt eine zusätzliche Sicherheitsebene hinzu, die die tatsächlichen sensiblen Daten schützt und potenziellen Schaden durch den Verstoß minimiert.
Möchten Sie mehr über Datenmaskierungssoftware erfahren? Erkunden Sie Datenmaskierung Produkte.
Anwendungsfälle der Datenmaskierung
Datenmaskierung wird in verschiedenen Branchen weit verbreitet eingesetzt, um sensible Informationen zu schützen und gleichzeitig die Nützlichkeit der Daten zu erhalten. Hier sind die wichtigsten Anwendungsfälle:
Einhaltung von Datenschutzbestimmungen
Organisationen verwenden Datenmaskierung, um den Datenschutzgesetzen wie der Datenschutz-Grundverordnung (DSGVO) zu entsprechen. Dies schützt sensible Informationen, einschließlich persönlich identifizierbarer Informationen (PII), Finanzunterlagen, geschützte Gesundheitsinformationen (PHI) und geistiges Eigentum.
Zum Beispiel maskieren Gesundheitsdienstleister Patientendaten, um die Anforderungen des Health Insurance Portability and Accountability Act (HIPAA) zu erfüllen, während sie Informationen für Forschungszwecke teilen.
Sichere Softwareentwicklung und -tests
Datenmaskierung wird in Softwareentwicklungs- und Testumgebungen eingesetzt, um sicherzustellen, dass sensible Informationen nicht offengelegt werden. Softwareentwickler und Tester verwenden maskierte Datensätze, die reale Daten nachahmen, ohne tatsächliche persönliche oder finanzielle Details preiszugeben.
Analytik und Forschung
Datenmaskierung wird von Datenwissenschaftlern und Forschern verwendet, um große Datensätze zu analysieren und gleichzeitig die Privatsphäre zu wahren. Zum Beispiel können Pharmaunternehmen Patientendaten in klinischen Studien maskieren, um die Wirksamkeit von Medikamenten zu untersuchen, ohne die Privatsphäre der Einzelpersonen zu gefährden.
Mitarbeiterschulung
Datenmaskierung wird in Mitarbeiterschulungen angewendet, um realistische Szenarien zu bieten, ohne echte Daten offenzulegen. Organisationen verwenden maskierte Daten, um Mitarbeiter im Umgang mit Kundenanfragen oder bei der Abwicklung von Transaktionen zu schulen.
Zum Beispiel könnte eine Bank maskierte Transaktionsdaten in Schulungsprogrammen verwenden, um Mitarbeitern beizubringen, wie man Betrug erkennt.
Rollenbasierte Zugriffskontrolle
Datenmaskierung wird verwendet, um rollenbasierte Zugriffskontrolle innerhalb von Organisationen durchzusetzen. Mitarbeiter können nur auf die Daten zugreifen, die für ihre Rollen erforderlich sind, wobei sensible Informationen maskiert werden, um unbefugte Einsicht zu verhindern.
Zum Beispiel könnten in einem Krankenhausumfeld Verwaltungspersonal maskierte elektronische Gesundheitsakten von Patienten sehen, während Ärzte Zugang zu vollständigen Informationen haben.
Testdatenmanagement
Datenmaskierung wird verwendet, um schnell sichere Testdaten zu generieren und sicherzustellen, dass Testumgebungen keine sensiblen Informationen offenlegen. Automatisierte Maskierungstools integrieren sich in bestehende Systeme, um qualitativ hochwertige Testdaten zu erzeugen.
Zum Beispiel könnte ein Versicherungsunternehmen maskierte Informationen von Versicherungsnehmern verwenden, um neue Versicherungsanspruchs-Verarbeitungssysteme zu testen, ohne das Risiko einer Datenexposition einzugehen.
Arten der Datenmaskierung
Unternehmen können verschiedene Arten der Datenmaskierung verwenden, um sensible Datensätze zu sichern und zu schützen.
Statische Datenmaskierung (SDM)
Statische Datenmaskierung (SDM) beinhaltet die Anwendung eines festen Satzes von Maskierungsregeln für sensible Daten, bevor sie geteilt oder gespeichert werden. Sie verändert die Daten direkt mit anonymisierten Werten durch Verschlüsselungs- oder Anonymisierungstechniken.
Die gleiche Maskierungsmethode wird für alle Benutzer und Anwendungen verwendet, die auf die Daten zugreifen. SDM ist im Allgemeinen gut für Daten, die unverändert bleiben und wiederholt verwendet werden, wie in einer laufenden Testumgebung.
Dynamische Datenmaskierung (DDM)
Dynamische Datenmaskierung (DDM) beinhaltet die Anwendung von Maskierungstechniken in Echtzeit und die dynamische Veränderung sensibler Daten während der Anwendung oder Ausführung. DDM ist in Produktionssystemen und für Benutzer, wie Tester, die Zugang zu tatsächlichen Daten für Analysen benötigen, weit verbreitet.
Dynamische Daten werden für rollenbasierte Sicherheitszugriffe verwendet. Zum Beispiel fordert ein Benutzer Daten in der Datenbank an, und Maskierungsregeln werden basierend auf den Rollen oder Zugriffsberechtigungen des Benutzers angewendet — autorisierte Benutzer erhalten den ursprünglichen Datensatz, und unautorisierte Benutzer erhalten die maskierten Daten.
Deterministische Datenmaskierung
Deterministische Datenmaskierung beinhaltet das Mapping von Daten, um sicherzustellen, dass ein Wert immer durch einen anderen Wert in der Datenbank ersetzt wird. Zum Beispiel, wenn Sie einen Namen mit „Bob“ maskieren, würde der ursprüngliche Name überall im Datensatz als „Bob“ erscheinen.
Obwohl die deterministische Datenmaskierung bequem ist, ist sie nicht so bequem wie andere Maskierungstypen. Wenn jemand herausfinden könnte, wer „Bob“ im obigen Beispiel ist, könnte er die Informationen dieser Person im gesamten Datensatz identifizieren.
On-the-fly Datenmaskierung
On-the-fly Datenmaskierung maskiert sensible Informationen, während sie zwischen Umgebungen bewegt werden, indem sie im Speicher maskiert werden, anstatt einen veränderten Datensatz im Speicher zu speichern, anstatt ihn separat zu speichern.
Organisationen können diese Technik verwenden, um Daten zu maskieren, während sie zwischen Umgebungen bewegt werden, von der Produktion zur Testumgebung. Diese Technik ist ideal für kontinuierliche Softwareentwicklung oder komplexe Integrationsszenarien, bei denen Teams häufig Daten zwischen Produktions- und Nicht-Produktionsumgebungen übertragen.
Statistische Verschleierung
Die statistische Verschleierungsmethode verändert sensible Daten, während statistische Eigenschaften und Beziehungen innerhalb der Daten erhalten bleiben.
Sie ermöglicht die Anwendung mathematischer Funktionen und Algorithmen auf die Daten für statistische Analysen, sobald sie maskiert sind, indem sichergestellt wird, dass die maskierten Daten ihre ursprünglichen Muster, Korrelationen und die gesamte Verteilung beibehalten.
Datenmaskierungstechniken
Abhängig von Ihrer Datenbank und Ihren Bedürfnissen gibt es verschiedene Techniken zur Maskierung von Daten innerhalb der verschiedenen Arten der Datenmaskierung.
Verschlüsselung
Verschlüsselung kombiniert Verschlüsselung und Datenmaskierung, um sensible Informationen zu schützen. Mit diesem Ansatz können Sie sensible Daten mit kryptografischen Algorithmen verschlüsseln, wodurch sie für alle außer autorisierten Benutzern mit Entschlüsselungsschlüsseln unlesbar werden.
Verschlüsselungsmaskierung bietet hohe Datensicherheit, kann jedoch ein Engpass sein, der die Datenanalyse verlangsamt, da Benutzer Entschlüsselungsschlüssel verwenden müssen, wann immer sie auf die Daten zugreifen möchten.
Top 5 Verschlüsselungssoftware-Tools:
* Dies sind die Top 5 Verschlüsselungssoftware-Tools basierend auf dem G2 Spring 2024 Grid® ReportDurchmischen
Das Durchmischen von Daten ist, was es klingt — das Zufälligmachen von Datenpunkten innerhalb eines gegebenen Datensatzes. Es bewahrt die Beziehung und statistischen Eigenschaften innerhalb des Datensatzes, während einzelne Datensätze unlesbar gemacht werden. Die Datenwerte ändern sich nicht, aber die Reihenfolge, in der sie erscheinen, tut es.
Zum Beispiel, wenn Sie mit einer Datentabelle arbeiten, die Kundennamen und Kreditkartennummern enthält, würde der Ausgabedatensatz aus einer durchmischten Tabelle der tatsächlichen Kundennamen und Kreditkartennummern bestehen, die nicht zusammenpassen.
Substitution
Die Substitution von Datenmaskierung beinhaltet das Ersetzen sensibler Datenpunkte durch ähnliche, aber ersetzte fiktive Daten.
Zum Beispiel, wenn Sie mit Namen arbeiten, könnten Sie echte Namen durch zufällig generierte ersetzen, sodass der Namenswert immer noch wie ein Name aussieht. Dasselbe würde mit Kreditkartennummern funktionieren. Der Ausgabedatensatz würde Kreditkartennummern derselben Zeichenlänge, aber mit zufälligen numerischen Werten anstelle von echten enthalten.
Nulling
Einige Teams verwenden die Nulling-Technik, um Daten unlesbar und unbrauchbar zu machen. Nulling beinhaltet das Anwenden von „Null“-Werten auf Datenkolonnen, sodass unautorisierte Benutzer keine Daten sehen. Während diese Methode Daten schützt, kann sie auch problematisch sein, da diejenigen, die Zugang zu den Daten benötigen, sie wahrscheinlich nicht verwenden können, es sei denn, die „Null“-Werte sind für die Analyse oder den Test völlig irrelevant.
Hashing
Schließlich konvertiert Hashing Datenpunkte in verschleierte, festgelegte Zeichenfolgenwerte. Es wird häufig zum Schutz von Informationen wie Passwörtern verwendet, da die ursprünglichen Informationen nicht benötigt werden, um die Arbeit auszuführen.
Mit anderen Worten, Datenbenutzer müssen die tatsächlichen Passwörter der Einzelpersonen nicht kennen, aber sie müssen eine Funktion testen, die erfordert, dass der Benutzer ein Passwort eingibt oder eines hat.
Herausforderungen bei der Datenmaskierung
Datenmaskierung ist wichtig. Sie bringt jedoch mehrere Herausforderungen mit sich, die angegangen werden müssen, um eine effektive Datensicherheit und -integrität zu gewährleisten. Hier sind einige häufige Probleme, die bei der Datenmaskierung auftreten:
Attributerhaltung
Datenmaskierung muss die gleichen Datentypen und ihre Muster beibehalten. Zum Beispiel, wenn Sie Kundenalter maskieren, sollte der Bereich und die Verteilung der Alter ähnlich bleiben. Wenn dies nicht korrekt durchgeführt wird, kann es die Genauigkeit Ihrer Analyse oder Berichte beeinträchtigen.
Semantische Integrität
Die während der Maskierung erstellten gefälschten Daten sollten immer noch sinnvoll sein. Zum Beispiel, wenn Sie Mitarbeitergehälter maskieren, sollten die neuen Werte immer noch in typische Gehaltsspannen passen. Ebenso sollten maskierte Telefonnummern echt aussehen. Dies hilft sicherzustellen, dass die maskierten Daten immer noch nützlich und realistisch sind.
Beim Maskieren von Daten für Tests ist es wichtig, dass die gefälschten Daten immer noch den Regeln für Dinge wie E-Mail-Formate oder Kreditkartennummern entsprechen. Wenn die Daten nicht diesen Regeln entsprechen, kann dies während der Tests zu Fehlern führen.
Ebenso, wenn die ursprünglichen Daten einzigartig sein müssen, wie Sozialversicherungsnummern, sollten die maskierten Daten ebenfalls einzigartig sein. Wenn die neuen Werte nicht einzigartig sind, kann dies zu Verwirrung oder Fehlern führen.
Referentielle Integrität
Maskierte Daten sollten ihre Beziehungen konsistent halten. Zum Beispiel, wenn Sie den Namen eines Kunden durch einen gefälschten ersetzen, sollte derselbe gefälschte Name überall dort verwendet werden, wo er erscheint. Dies hilft, genaue Verbindungen zwischen Datensätzen aufrechtzuerhalten.
Best Practices für die Datenmaskierung
Um Datenmaskierung richtig zu machen, ist es wichtig, einige Best Practices zu befolgen, die sicherstellen, dass die Daten geschützt bleiben und gleichzeitig nützlich sind. Hier sind einige wichtige Tipps, die Ihnen helfen, Daten effektiv und sicher zu maskieren.
Definieren Sie den Projektumfang
Um eine effektive Datenmaskierung zu implementieren, beginnen Sie damit, festzulegen, welche Informationen geschützt werden müssen, wer autorisiert ist, darauf zuzugreifen, und welche Anwendungen die Daten verwenden und wo sie sich sowohl in Produktions- als auch in Nicht-Produktionsumgebungen befinden.
Erhalten Sie die referentielle Integrität
Referentielle Integrität erfordert, dass alle Daten eines bestimmten Typs konsistent mit demselben Algorithmus maskiert werden. In großen Organisationen ist ein einziges Datenmaskierungstool im gesamten Unternehmen möglicherweise nicht praktikabel aufgrund unterschiedlicher Budgetbeschränkungen, IT-Praktiken und regulatorischer Anforderungen. Stellen Sie daher sicher, dass die Synchronisation von Datenmaskierungstools und -praktiken in der gesamten Organisation erfolgt, um Integrationsprobleme später zu vermeiden.
Schützen Sie Datenmaskierungsalgorithmen
Nur autorisiertes Personal sollte Zugang zu den sensiblen Komponenten des Datenmaskierungsalgorithmus haben. Kenntnisse über wiederholbare Maskierungsalgorithmen könnten zur Rückentwicklung sensibler Informationen führen.
Best Practices umfassen die Durchsetzung der Trennung von Aufgaben, bei der die IT-Sicherheit Methoden und Algorithmen definiert, aber die relevanten Abteilungsdateninhaber spezifische Einstellungen und Datenlisten verwalten.
Organisieren und verfolgen Sie sensible Daten
Unternehmensdaten sind über verschiedene Technologien und Standorte verstreut. Unstrukturierte Daten wie Bilder, PDFs und textbasierte Dateien müssen ebenfalls geschützt werden.
Ersetzen Sie beispielsweise Bilder sensibler Dokumente wie Pässe, Führerscheine und Verträge durch gefälschte Alternativen. Optische Zeichenerkennung (OCR) kann helfen, sensible Inhalte in solchen Dateien zu erkennen und zu maskieren.
Das genaue Auffinden und Klassifizieren sensibler Daten, die geschützt werden müssen, ist entscheidend. Implementieren Sie umfassendes Tracking, um sicherzustellen, dass die richtigen Daten angemessen maskiert werden.
Stellen Sie Compliance und Sicherheit sicher
Der Zugriff auf maskierte Daten sollte den Sicherheitsrichtlinien in Bezug auf Rollen, Standorte und Berechtigungen entsprechen. Überprüfen Sie, ob die Datenmaskierungstechniken mit den Sicherheitsrichtlinien und Vorschriften übereinstimmen.
Bewerten und testen Sie die Datenmaskierung
Bewerten Sie regelmäßig die Wirksamkeit der Datenmaskierungstechniken, um sicherzustellen, dass sie die erforderlichen Sicherheitsniveaus bieten. Führen Sie Tests durch, um zu bestätigen, dass die Abfrageergebnisse aus maskierten Daten mit denen aus den Originaldaten vergleichbar sind, um Konsistenz und Zuverlässigkeit zu gewährleisten.
Top 5 Datenmaskierungssoftware-Tools
Datenmaskierungssoftware-Tools helfen Unternehmen, ihre Daten zu schützen, indem sie sie durch Randomisierung und andere Techniken maskieren. Am wichtigsten ist, dass diese Tools es Unternehmen ermöglichen, ihre Daten weiterhin zu nutzen, sie jedoch für Parteien außerhalb der Organisation unbrauchbar machen.
Um in die Kategorie der Datenmaskierung aufgenommen zu werden, muss ein Produkt:
- Daten verschlüsseln, indem es sie hinter zufälligen Zeichen oder anderen Daten maskiert
- Die Anwendung und Entfernung einer Maske nach Belieben ermöglichen
- Konsistente oder zufällige Maskierung bieten
* Unten sind die fünf führenden Datenmaskierungssoftware-Plattformen aus dem G2 Spring 2024 Grid® Report aufgeführt. Einige Bewertungen können zur Klarheit bearbeitet worden sein.
1. Oracle Data Safe
Oracle Data Safe ist ein einheitliches Kontrollzentrum speziell für Oracle-Datenbanken. Es hilft Benutzern, die Sensibilität ihrer Daten zu verstehen, Sicherheitsrisiken zu bewerten, Daten zur Nutzung zu maskieren und Sicherheits- und Zugriffskontrollen zu überwachen.
Benutzer können Sicherheitsbewertungen, Benutzerbewertungen, Aktivitätsüberwachung, Alarmaktivierung zur Signalisierung ungewöhnlichen Verhaltens, Datenmaskierung mit erhaltener Datenintegrität und SQL-Firewall nutzen.
Was Benutzer am meisten mögen:
„Was mir an Oracle Data Safe am meisten gefällt, ist, dass es sehr hilfreich ist, die Daten automatisch zu auditieren. Es verwaltet die Daten selbst und bietet das beste Sicherheitsniveau. Es hat unserer Organisation geholfen, die Anforderungen des Kunden oder Geschäfts zu erfüllen und ein besseres Ergebnis mit dem klassifizierten Bericht zu liefern.“
- Oracle Data Safe Review, Shivam T.
Was Benutzer nicht mögen:
„Ich fand die Preise auf der höheren Seite, daher muss man es in jedem Projekt, das man verwendet, einsetzen, um eine Skaleneffizienz zu erzielen. Ansonsten fand ich dieses Tool sehr nützlich.“
- Oracle Data Safe Review, Chitrang S.
2. Informatica Dynamic Data Masking
Informatica Dynamic Data Masking kontrolliert unbefugten Zugriff auf Produktionsumgebungen durch Datenanonymisierung. Es maskiert sensible Informationen für Benutzer basierend auf ihren rollenbasierten Zugriffsberechtigungen, die ihre Rolle, ihren Standort und ihre Privilegien umfassen. Darüber hinaus kann es unbefugte Zugriffsversuche alarmieren.
Was Benutzer am meisten mögen:
„Informatica-Datenmaskierung bietet verschiedene Techniken zum Schutz sensibler Daten. Mit Hilfe ihrer formatbewahrenden Technik haben wir die Daten geschützt, ohne das Format zu ändern. Darüber hinaus identifizierte ihre dynamische Datenentdeckungstechnik die meisten sensiblen Datenfelder. Insgesamt kann ich sagen, dass Informatica eine umfassende Lösung mit einer robusten und benutzerfreundlichen Erfahrung bei der Anonymisierung von Daten ist.“
- Informatica Dynamic Data Masking Review, Mayank J.
Was Benutzer nicht mögen:
„Es ist anfangs etwas komplex zu verstehen, und es gibt etwas weniger Dokumentation. Aber sobald man eine kleine Vorstellung hat, ist es sehr einfach und bequem, es für Maskierungs- und andere Sicherheitszwecke zu verwenden.“
- Informatica Dynamic Data Masking Review, Himanshu G.
3. Informatica Data Security Cloud
Informatica Data Security Cloud verwendet Authentifizierungs- und Verschlüsselungsmethoden, um die Datensicherheit in cloud-nativen Umgebungen zu gewährleisten. Es ist Teil der Intelligent Data Management Cloud (IDMC) und wurde entwickelt, um in der Cloud zu laufen.
Was Benutzer am meisten mögen:
„Master-Datenmanagement ist das wertvollste Feature, das ich an Informatica Cloud mag. Wir können Code schreiben, um unsere eigene Logik zu erstellen, um die Qualität zu überprüfen und Datenmaskierung zu verwenden. Das API-Management und die Integration sind gute Konnektoren, die mit der Software bereitgestellt werden.
- Informatica Data Security Cloud Review, Gaurav K.
Was Benutzer nicht mögen:
„Während das Tool viele Optionen und Funktionen für die Datensicherheit bietet, müssen die Personen, die es handhaben, umfangreiche und regelmäßige Schulungen zu DSGVO, Gesetzen, Vorschriften usw. durchlaufen, um die Sicherheit zu verwalten und das Tool in vollem Umfang zu nutzen.“
- Informatica Data Security Cloud Review, Vibha K.
4. Satori Data Security Platform
Satori Data Security Platform ermöglicht selbstgesteuerte Daten- und Analytikkontrollen. Benutzer haben persönliche Datenportale, in denen sie sofortigen Zugriff auf Datensätze erhalten, die für sie basierend auf Zugriffsrichtlinien und -kontrollen relevant sind. Satori anonymisiert Daten dynamisch für eine skalierbare Lösung über mehrere berechtigungsbasierte Profile und Richtlinien hinweg.
Was Benutzer am meisten mögen:
„Satori bietet eine benutzerfreundliche Oberfläche, die es einfach macht, zu implementieren und zu navigieren, robuste Datenmaskierungs- und Sicherheitsfunktionen und schützt sensible Daten. Automatisierte und skalierbare Zugriffskontrolle, die es Organisationen ermöglicht, granulare Kontrolle über den Datenzugriff zu haben, nahtlos in beliebte Software-Tools wie Snowflake und Looker integriert, was den Integrationsprozess vereinfacht.“
- Satori Data Security Platform Review, Vaibhav S.
Was Benutzer nicht mögen:
„Es kann mit fast aller Software integriert werden, insbesondere in der Cloud, was es unverzichtbar macht. Allerdings wird die Leistung etwas langsamer, wenn Tonnen von Terabytes an Daten in das System eingespeist werden, sowohl in Bezug auf die Leistung als auch auf die Zeit, um die Ergebnisse zu erzeugen.“
- Satori Data Security Platform Review, Heena R.
5. Clonetab
Clonetab ist eine Virtualisierungs- und Klonplattform für die Datenbereitstellung. Es bietet fortschrittliches Datenverschleiern (ADS), das sensible Daten vor der Freigabe verschleiert, sowie umfassende Backup- und Datenwiederherstellungslösungen für Oracle e-Business Suite, PeopleSoft und SAP Hana-Datenbanken.
Was Benutzer am meisten mögen:
„Clonetab hilft nicht nur den Administratoren beim Klonen großer VMware, sondern auch beim Klonen von Datenbanken auf granularer Ebene. Die GUI für Clonetab ist so gestaltet, dass es Administratoren leicht fällt, damit zu arbeiten.“
- Clonetab Review, Nikhil N.
Was Benutzer nicht mögen:
„Trotz der besten Plattform für die täglichen Bedürfnisse jedes Unternehmens hat es weniger Community-Unterstützung, was bedeutet, dass diese Plattform vollständig von Support-Mitarbeitern abhängig ist, was zu unbeabsichtigten Verzögerungen führen kann. Wenn wir eine Community-Edition dieser Plattform hätten, wäre es einfach, schnell mit Hilfe der Community zu beheben.“
- Clonetab Review, Mukesh P.
Können Sie die Daten lesen?
Datenmaskierung ist eine effektive Technik zum Schutz persönlicher und vertraulicher Informationen. Unternehmen verwenden Datenmaskierung, um sensible Daten zu sichern und zu schützen, wenn sie zwischen verschiedenen Test-, Produktions- und Entwicklungsumgebungen übertragen werden. Es stehen viele Arten und Techniken der Datenmaskierung zur Verfügung, aus denen Unternehmen wählen können, um die Informationen zu schützen, mit denen sie arbeiten.
Entdecken Sie, wie Datenverlustprävention Ihre sensiblen Informationen schützen kann.

Alyssa Towns
Alyssa Towns works in communications and change management and is a freelance writer for G2. She mainly writes SaaS, productivity, and career-adjacent content. In her spare time, Alyssa is either enjoying a new restaurant with her husband, playing with her Bengal cats Yeti and Yowie, adventuring outdoors, or reading a book from her TBR list.