Whether it involves critical business documents or confidential client data, no one wants their company's sensitive information to fall into the wrong hands.
As network security professionals, you understand the importance of implementing best practices in data handling. Rather than relying on hope when hitting "send," you can use Secure File Transfer Protocol (SFTP).
What is a secure file transfer protocol?
A secure file transfer protocol is a network protocol for transferring, accessing, and managing files between machines over an encrypted connection.
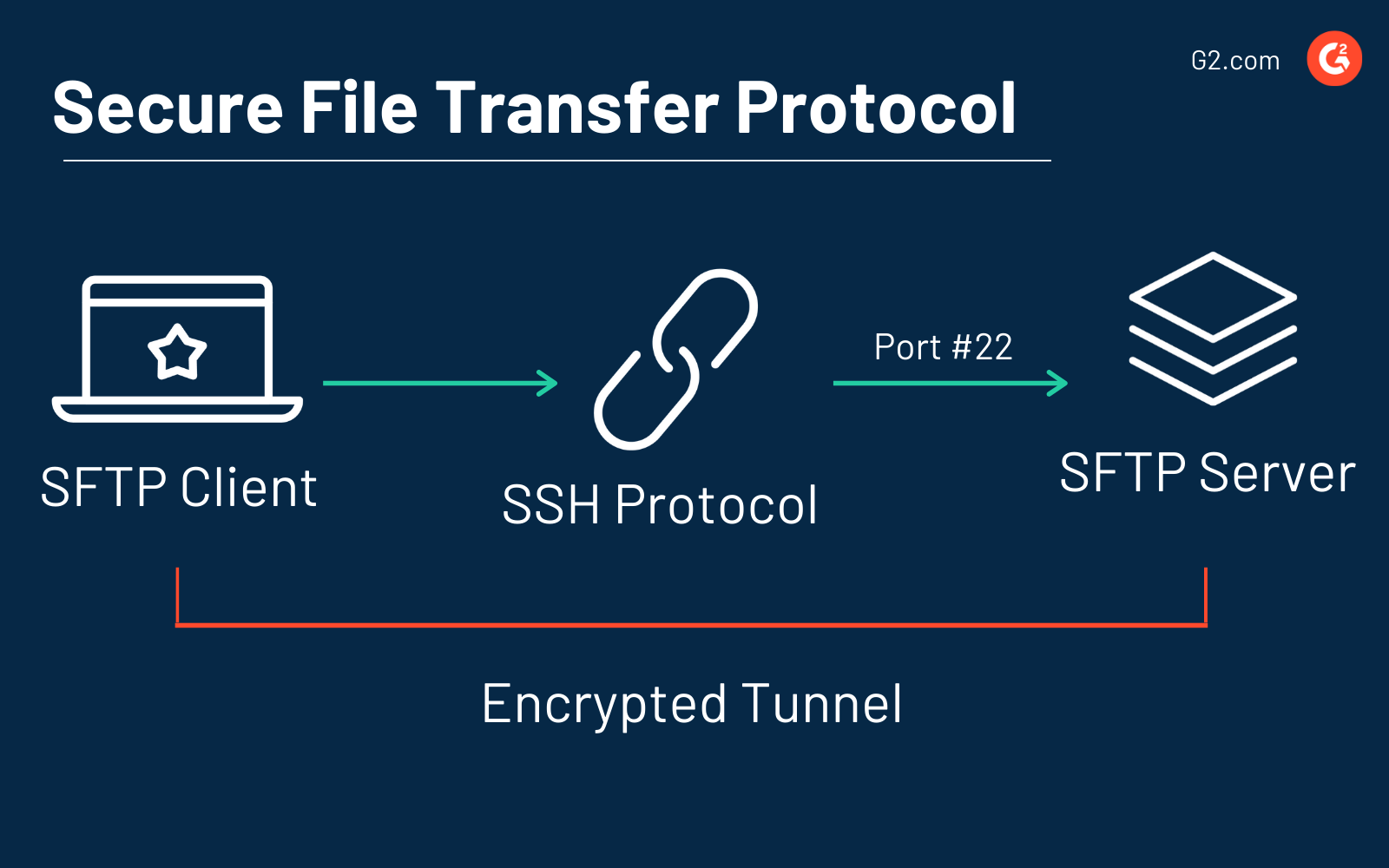
SFTP builds on File Transfer Protocol (FTP) software, uses the secure shell (SSH) protocol to transfer files, and requires the client to be authenticated by the server for enhanced security elements.
No matter what kind of file sharing is taking place, to ensure that all passwords and sensitive information are kept secure, SFTP commands and data are encrypted so that nothing is exposed to the network in plain text.
Understanding network protocols
First things first, a protocol is a set of rules and guidelines that must be followed when communicating data. These rules are broken down for each step in the process before communication between two or more computers or servers.
In order for the networks to successfully transmit data, they must follow the rules within the protocol.
- SSH Protocol: It creates a protected connection between a remote server and a computer and utilizes a public key encryption method to provide secure user authentication and encrypted communications across the Internet.
Note: The Internet Engineering Task Force (IETF) developed the Secure Shell Protocol (SSH) in 2006 to replace older shell protocols that weren’t as secure.
- SFTP: Designed to be an extension of SSH to provide secure file transfer capabilities.
- FTP: Provides users with a way to move files from a local computer to a website’s server. FTP isn’t secure and is often a target of malicious cyber attacks.
SFTP and SSH work together to send encrypted data connections between the client and the server to allow passwords and other sensitive information to be transferred securely over the network.
Want to learn more about File Transfer Protocol (FTP) Software? Explore File Transfer Protocol (FTP) products.
SFTP vs. FTP
FTP doesn’t offer a secure channel to transfer files between hosts. Any data transmitted over this protocol can be easily intercepted and read by malicious actors. In contrast, SFTP uses strong encryption protocols, such as SSH, to create a secure connection between the client and server. This ensures that all data, including login credentials, commands, and file contents, are protected.
The authentication methods differ significantly between the two protocols. FTP typically uses username and password authentication, which can be vulnerable to attacks such as brute force or credential theft.
On the other hand, SFTP supports multiple authentication methods, including public key authentication. This significantly enhances security, as it requires the client to possess a private key that corresponds to a public key stored on the server, making unauthorized access much more challenging.
While SFTP could be slower, FTP might offer faster transfer speeds due to its simplicity. This difference in speed arises from the added security measures that SFTP employs. The encryption and decryption processes involved in securing the data can introduce latency, especially when transferring large files or in environments with limited bandwidth.
How does SFTP work?
When you need a secure server-to-server file transfer between you and your business partners, a secure file transfer protocol is what you need.
While it may sound complicated, it’s relatively straightforward. SFTP works with SSH to establish encryption algorithms to securely move data to the server to keep files unreadable during the entire process.
It then uses authentication to prevent unauthorized file access so nothing ever falls into the wrong hands, providing businesses with a higher level of file transfer protection.
It’s also important to note that SFTP runs on Port 22, but it can be assigned to whatever port number you choose.
Tip: Port numbers identify both the senders and receivers of information to and from the server.
SFTP is also a packet-based protocol, not a text-based protocol. This means it’s easier to process because it’s so compact, and it's faster than other protocols.
Source: LinkedIn
Before you can use an SFTP, you need both an SFTP client and a server.
An SFTP client is the necessary software that allows you to connect to the server. It also allows you to upload files to be stored on the server and download files that are already being stored.
An SFTP server is where files are stored and where you can connect and retrieve them. The server provides its services so users can store and transfer data safely. It uses the SSH file transfer protocol to keep the connection secure. A software vendor may store software updates on their SFTP server so that customers can download secure files with an SFTP client.
When you’re interested in connecting to an SFTP server, you’ll need to establish a password authentication or a public/private key for authentication.
Using keys means creating a pair of public and private keys, with the public key stored in the SFTP server. The client with the private key will verify that the keys match upon login with the server.
Once verification occurs, the SFTP client will gain access to the system. A password or phrase can also be added to the private to take security even further. Since FTP gives anyone the ability to read passwords, commands, and file contents in plain text, it’s not a feasible solution for corporate files and data.
Examples of SFTP commands
- sftp> put -- Upload a file
- sftp> get -- Download a file
- sftp> cd -- Change the active directory path
- sftp> pwd -- Display the remote working directory
- sftp> rm -- Delete a file on the remote host
What is SFTP used for?
Unlike FTP, SFTP encrypts both commands and data, preventing sensitive information from being intercepted during transmission. Its robust security features make it the preferred choice for businesses that require strict data protection measures.
One of the main uses is to comply with the standards of the federal Health Insurance Portability and Accountability Act (HIPAA), which governs protected health information. So, any healthcare business or organization must use SFTP to secure all types of data and reduce the risk of violations that could lead to hefty fines and reputational damage.
SFTP is also used to comply with data protection standards. Depending on the type of files and data, the General Data Protection Regulation (GDPR) may require this type of security to be met before the transfer.
By employing strong encryption techniques, SFTP safeguards against data breaches that could lead to identity theft or financial loss. This level of protection is essential for organizations that handle confidential information, such as financial records or personally identifiable information.
SFTP can complement a Virtual Private Network (VPN). VPNs create a secure, encrypted online connection, acting as a protective tunnel for data being transmitted over the internet. By combining SFTP with a VPN, organizations can enhance their data transfer security even further. This dual-layered approach ensures that data not only travels securely over the internet but is also protected from potential threats within the network.
Advantages of using SFTP
There are many reasons why businesses choose to implement secure file transfer protocols into their strategies:
- Speed: The servers used with SFTP can easily support large file transfers, as well as transferring multiple files at once. Because of this, you’ll save time when moving data from one server to another.
- Security: Thanks to encryption, public key authentication, and data security, SFTP can preserve the confidentiality and integrity of your data. There’s added peace of mind in knowing that data is also checked to make sure it’s coming from a trusted source and that customers and sources are verified before a connection is established.
- Manageable: Using SFTP gives you the ability to easily manage your server using a web interface or an SFTP client.
- Firewalls: SFTP and firewalls go hand in hand. Data, commands, and sensitive information are all sent over a single connection to Port 22. This port is, by default, enabled with firewalls with their own pre-set security parameters.
- Metadata: Users of SFTP are able to access metadata of their files, like data, time, size, permissions, and other information, ensuring that all documents are easier to find.
Disadvantages of using SFTP
Because no technology is going to be perfect, secure file transfer protocol does come with a few disadvantages:
- Because SSH has so many protection features, the keys are harder to manage and validate.
- Can be harder to configure properly without support from software providers.
- SFTP configuration standards may lead to compatibility issues between software titles and different vendors. It’s good to feel secure
When it comes to secure data transfer for your business, SFTP is the standard you should consider. No matter the industry or the file type, SFTP will keep all information encrypted and secure in its transfer to the appropriate server without sacrificing compliance.
Best practices for using SFTP
- Use descriptive filenames and organize files into logical folder structures to make it easier to locate and access files while reducing errors.
- Consider network bandwidth and concurrent transfer limits. Optimizing these parameters can maximize transfer speeds and efficiency.
- Implement robust network monitoring and logging mechanisms to track SFTP activities and detect anomalies.
- Regularly back up your SFTP server and its associated data to mitigate data loss risks.
- Seamlessly integrate SFTP into various workflows, such as automated processes, business file transfers, and cloud storage solutions.
Rest easy, you're protected!
When it comes to secure data transfer for your business, SFTP is the standard you should consider. No matter the industry or the file type, SFTP will keep all information encrypted and secure in its transfer to the appropriate server without sacrificing compliance.
Learn more about web application firewalls to further enhance your understanding of secure data transmission.
This article was originally published in 2020. It has been updated with new information.

Mara Calvello
Mara Calvello is a Content and Communications Manager at G2. She received her Bachelor of Arts degree from Elmhurst College (now Elmhurst University). Mara writes customer marketing content, while also focusing on social media and communications for G2. She previously wrote content to support our G2 Tea newsletter, as well as categories on artificial intelligence, natural language understanding (NLU), AI code generation, synthetic data, and more. In her spare time, she's out exploring with her rescue dog Zeke or enjoying a good book.