Ransomware is a major threat that impacts both home and business users alike.
What is ransomware?
Ransomware is a type of malware that blocks user access to data and demands a ransom payment to unlock it. It can also be used as an instrument to threaten a user to publish their sensitive files or information.
With a temporary or permanent loss of data and information, ransomware impacts your capital and business' reputation. It's essential to safeguard your assets from a ransomware attack before it's too late to realize the consequences it might have.
First, you have to examine your security framework for flaws that could invite a malicious ransomware program, monitor every log to recognize any emerging ransomware threat and employ the best cybersecurity practices to put up a strong defense.
Software like SIEM software, anti-virus solutions, vulnerability assessment tools, email anti-spam software help combat ransomware.
What is a ransomware attack?
Emanating from its roots in crypto virology (the study of cryptography used in designing malicious software), ransomware encrypts victims' files on a hard drive and demands payment to decrypt them. Some malware programs are simple, like scareware, which a knowledgeable person can easily overcome and gain access to their data. However many ransomware programs leverage techniques such as cryptoviral extortion, where files' decryption becomes complicated without the decryption key.
Hackers generally use trojans, disguised malware as genuine files, to carry out a ransomware infection. You'll have to be cautious while downloading a file that came as a legitimate attachment in your email or clicking a link that takes you to a fake website, as it can easily be a social engineering attack like phishing. Trojans can also be deployed through a vulnerability in the network service.
In the present cybersecurity landscape, hackers are developing strains of AI-powered malware that hide the conditions required to unlock the files while deploying untraceable malicious software in your machine.
Considering the downtime, loss of data and information, hindrance in functionality, device cost, network cost, ransom demand, and more, a ransomware attack can cause a hefty financial loss to an organization. It's essential to take appropriate preventive measures to protect your network and system from such malware attacks.
Want to learn more about Security Information and Event Management (SIEM) Software? Explore Security Information and Event Management (SIEM) products.
How does ransomware work?
File-encrypting ransomware follows a technique of cryptoviral extortion. The concept was originally invented by Young and Yung at Columbia University. Then, it was presented at the 1996 IEEE Security and Privacy conference.
Here is how the cryptoviral extortion technique of ransomware works:
- An attacker generates a key pair with a corresponding public key. The public key is placed in the malware, which is then released.
- To execute the cryptoviral extortion, the malware generates a random symmetric key to encrypt the victim's data.
- Then, it uses the public key to encrypt the symmetric key. This is called hybrid encryption, where a small asymmetric cipher text and a symmetric cipher text of the victim's data are created.
- It then zeroes the symmetric key and the original plain text data to prevent its recovery.
- In the next step, it displays a message that includes the asymmetric cipher text and steps to pay the ransom.
- The victim sends this asymmetric cipher text and the amount as mentioned in the ransom note via wire transfer, prepaid vouchers, or in cryptocurrency.
- Attackers send the symmetric key after that, and the victim can use it to decipher the original data using it.
In this process, the attacker's private key is never exposed to the victim. As the symmetric key is generated randomly, it cannot be used by other ransomware victims.
When ransomware enters the systems, it runs a payload – a program that carries out malicious actions. The payload locks the system or claims to lock it (like a scareware program). It displays a warning message, claiming you have done illegal activities on your system in some cases.
There are instances where ransomware locks you out of the operating system by modifying the graphical user interface (GUI) in Microsoft Windows or master boot record to prevent rebooting.
Types of ransomware
There are different types of ransomware designed to satiate multiple motives of the attacker. Take a look at the types to identify a ransomware attack if you ever encounter one.
File-encrypting ransomware
File-encrypting ransomware are programs that deploy a payload in your systems, which encrypts your files using techniques such as cryptoviral extortion, among others. When deployed, the malware program runs a payload that locks you out of your system in a typical fashion. These payloads may sometimes display false warning messages from law enforcement agencies, notifying you about illegal activities conducted on your system.
There can be a two-stage payload in some cases, where the victim is tricked into running a script that downloads the main virus into the system. In early versions of the dual-payload ransomware program, a Microsoft 365 document used to contain a script with an attached VBScript Macro, or it was present in the Windows Scripting Facility (WSF) file.
Also, certain strains of file-encrypting ransomware use proxies tied to Tor hidden service, making it difficult to trace the exact location of the cyber criminal.
Non-encrypting ransomware
Non-encrypting ransomware programs aren't a part of encryption tools, but they do restrict access to your files and information. There are instances where users are locked out of their systems, and pornographic images are shown, so the user is prompted to send premium-rate SMS to receive a code to unlock.
The ransomware Winlock followed a similar procedure back in August 2010, managing to extort over $16 million from different end users.
Sometimes the main objective of non-encrypting malware is to frustrate the user into making attempts to close the page. In such cases, users may see a warning message that holds them responsible and accountable for illegal acts conducted on your machine.
Leakware
It is also called extrotionware, doxware and exfiltrationware. Simply put, leakware is the converse of ransomware. In places where the latter restricts access of a user to their information, leakware threatens the user to expose their information out in public. The attackers pressure the victim to pay the ransom to avoid exposure of their sensitive data.
Leakware programs primarily target those users who have third-party information stored in their systems. It includes customer data, financial data, and more. Users who have information like trade secrets or confidential information of a product can also be potential targets of such attacks. The information that is crucial to a user, like their sensitive health data or embarrassing information, also fuels a leakware attack in many cases.
Mobile ransomware
When the popularity of ransomware on computer systems grew, its introduction in mobile phones was unavoidable, as it was rewarding. Attackers primarily targeted Android smartphones to leverage its facility to download and install apps from third-party sources.
In mobile ransomware, a clueless individual downloads an app that is a ransomware program disguised as an APK file. The payload runs a program that displays a blocking or warning message over other applications on your phone. Sometimes, the payload may trick you into providing administrator privileges where the ransomware can delve deeper into your device.
Ransomware can also affect digital cameras by exploiting vulnerabilities in the picture transfer protocol (PTP). Such an attack was presented in August 2019 at Defcon as a proof of concept attack.
Related: Explore mobile data security software to protect mobile devices and their data.
Ransomware as a Service (RaaS)
RaaS fulfills the needs of a hacker to launch a ransomware attack. It’s like a SaaS offering, where some cybercrime organizations take a monthly license fee, whereas others take a commission from the ransom extorted from a victim.
A typical RaaS subscription is charged at around $50 and comes with a ransomware code and a decryption key. It enables low-skilled beginners in hacking to enter the world of cybercrime and test their malicious methods and tactics.
RaaS organizations run their operations in a sophisticated manner on the dark web. Like any typical SaaS business, RaaS has three subscription models: gold, silver, and bronze.
Double and triple extortion ransomware
Double and triple extortion ransomware are advanced and increasingly malicious forms of ransomware attacks that have emerged in recent years.
Double extortion follows the normal ransomware attack pattern by extorting victims into paying a ransom twice.
Triple extortion ransomware takes the extortion tactics one step further by involving a third layer of threat. In addition to encrypting the victim's data and threatening to leak it, attackers also threaten to disrupt the victim's business operations or launch a distributed denial of service (DDoS) attack against their systems if the ransom is not paid.
Top ransomware targets in 2023 by sector
Companies in the following sectors are the most common targets of ransomware attacks based on a Sophos survey.
- Education
- Construction and propery
- Central and federal government
- Media, leisure and entertainment
- Local/state government
- Retail
- Energy, oil and gas and utilities industry
- Distribution and transport services
- Financial services
- Business and professional services
- Healthcare
What is the impact of ransomware?
Almost one-quarter (24%) of incidents involving malware are ransomware.The impact of a ransomware attack can be disastrous. Even if you pay the ransom, there is no surety that you'll get access to your data, which can lead to even more gruesome consequences.
It won't matter if you are from a large or a small organization; a ransomware attack will have an impact on your capital as well as reputation, which is a costly asset in business. It may also cause substantial downtime with an extended recovery period, devastatingly impacting your business.
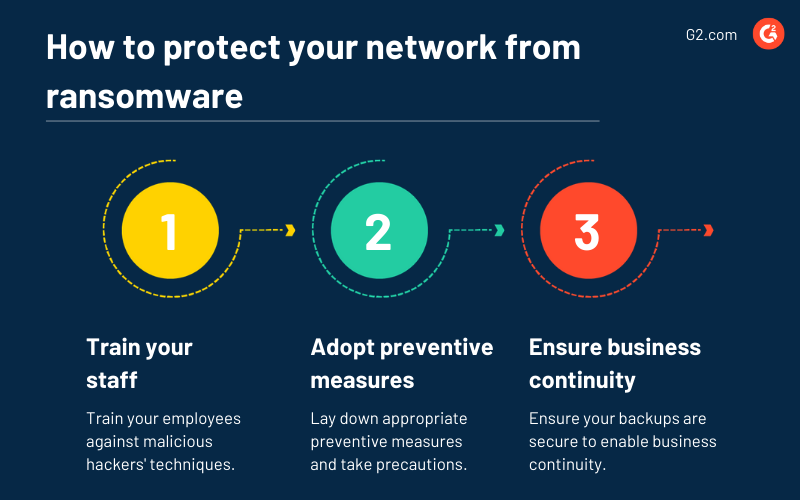
How to protect your network against ransomware
Ransomware is a persistent threat to home and corporate users alike. As it leads to temporary or permanent loss of information to an entity and causes financial and reputational losses, it is essential to have mitigation strategies in place. You should adopt the best practices in the industry focused on prevention and response to a ransomware attack.
Disclaimer: These guidelines are based on recommendations by the US Government. G2 does not offer legal advice. If you have legal questions, consult a licensed attorney.
Train your staff
Employees are perhaps the easiest path for cyber actors to penetrate your security defenses. It's paramount to train your employees against malicious hackers' techniques to inject malware into your networks.
Educate your staff not to fall prey to social engineering attempts that trick them into clicking an unsolicited link or disclosing their passwords. It's advisable to test your team with simulated phishing emails, pretexting, and more.
Adopt preventive measures
The best way to protect your networks from ransomware is to lay down appropriate preventive measures and take precautions. To avoid ransomware injection, the US government recommends the following precautionary measures.
- Implement a training program to spread awareness among your employees and ensure that they are well-educated about ransomware and how it's delivered.
- Authenticate inbound email to prevent email spoofing. Ensure that you have email spam filters to prevent phishing attempts.
- Scan inbound and outbound emails to prevent executable files from reaching the users.
- Block malicious IP addresses by configuring your firewall.
- Consider using a patch management system to patch firmware, software, and operating systems on your computer.
- Perform a regular scan for viruses and malware with antivirus software and anti-malware software.
- Regulate user access privileges effectively. Ensure that no user is granted admin access until it becomes unavoidable. Those who need admin privileges should use them with care and only when required.
- Manage access privileges to files, directories, and shares with the least privileged structure in mind.
- Consider using an office viewer to open MS-office files delivered through email instead of using the full suite. Make sure to disable macro for files transferred via email.
- Prevent execution of a program from common ransomware locations like temporary folders supporting popular internet browsers.
- If Remote Desktop Protocol (RDP) is not being used, consider disabling it.
- Allow execution of programs only from known and trusted sources.
- Use virtualized environments to use operating system environments or certain programs.
- Enable logical and physical separation of networks for different units in your organization while categorizing data based on organizational value.
Ensure business continuity
As ransomware attacks can cause a temporary or permanent loss of data, it's advisable to have a data backup ready. It'll help you ensure business continuity if the unfortunate incident happens.
The US government recommends conducting penetration testing and vulnerability assessment at least once a year.
Ensure your backups are secure and are not connected permanently to the computer or networks they are backing up. There are instances where cloud-based backups might be locked in a ransomware incident, in which the systems and networks back up the information in real-time. These are paramount for incident response and recovery as they help you get up and running to avoid downtime when incidents occur.
Should businesses pay the ransom?
IBM data shows 47 % of ransomware victims have paid a ransom till now in 2023. Governments and cybersecurity experts, however, discourage ransomware victims from paying the money.
Experts note that paying ransom can encourage further ransomware attacks and doesn't guarantee that you will regain access to your data or that your data won't be further exploited or sold on the dark web.
Ransom payment can also be illegal in some cases. For instance, paying ransom to groups from countries like Russia, North Korea or Iran will in violation of U.S. regulations.
Instead, law enforcement agencies encourage reporting such incidents before making payments. Research also notes reporting the cyber threat to law enforcement lessens the total cost associated with a ransomware attack.
Real examples of ransomware attacks
Ransomware attacks have caused havoc for individuals and corporates for ages. Here are a few ransomware attacks to learn from.
Reveton
A ransomware known as Reveton, based on Citadel trojan, spread in 2012 in European countries. Its payload displayed an alarming message from law enforcement agencies, claiming that there have been illegal activities like downloading unlicensed software or child pornography on your machine. The message prompted users to pay a fine using an anonymous prepaid cash service voucher such as a Paysafecard.
To amplify the false illusion, users were shown their IP addresses and recordings from their webcam to prove that they were tracked and the message was actually from a law enforcement agency.
The ransomware trojan used logos of Metropolitan Police Service, Police National E-Crime Unit, and royalty collection society PRS for Music, specifically when it accused the user of downloading illegal music. In 2012, it initially began spreading in European countries, and later on, in August 2012, Reveton's variants were discovered in the United States.
Cryptolocker
Cyptolocker ransomware attack first appeared in September 2013 and infected machines that were using Microsoft Windows operating systems. The ransomware was transmitted as an email attachment that took advantage of Windows OS not showing the file extension and disguising it as a PDF file. As it was file-encrypting ransomware, it showed a message to make a payment in Bitcoin or prepaid vouchers for unlocking the files before a stated deadline.
It's believed that Cryptolocker extorted around $3 million from the victims before getting isolated in May 2014 by Operation Torvar, which took down the Gameover Zeus botnet used for its distribution.
In September 2014, users in Australia were targeted by a ransomware known as Cryptolocker. F, identified by Semantic and unrelated to the original Cryptolocker due to the difference in the operations. The malware trojan was spread through emails disguised as failed parcel delivery notices from Australia post to evade email scanners. The payload was deployed when a user visited a webpage and entered a CAPTCHA code.
CryptoWall
CryptoWall appeared in 2014, where it targeted users with Windows operating systems. One strain of CryptoWall spread through malvertising on the Zedo ad network, targeting several prominent websites. It deployed the payload after redirecting the users to malicious websites and used the browser plugin exploit kit. Barracuda Networks observed that the payload was signed with the digital signature to give a false pretense of authenticity.
CryptoWall 3.0 was distributed through fraudulent emails that deployed the payload by running a malicious code in the JavaScript, disguised as a .jpg file in the email attachment. It also created new instances of explorer.exe and svchost.exe to communicate with the servers and evade detection.
The ransomware deleted volume shadow copy and installed spyware to steal passwords and Bitcoin wallets during encryption. Around 1000 victims contacted the FBI to report CryptoWall infection with an estimated loss of at least $18 million. The latest ransomware strain, CryptoWall 4.0, modified its code to avoid antivirus detection, and it encrypted files and well as the file names.
Fusob
Fusob appeared in 2015 as typical mobile ransomware, which scares users to extort from them. IT displays warning messages to pay a fine for committing illegal activities on your device, or otherwise face legal consequences. The ransomware disguises as a pornographic video player, and tricks users into downloading it.
When downloaded, Fusob checks the language of the mobile device; if it uses any language other than Russian or certain Eastern European languages, it locks the system and demands a ransom to unlock it. The ransomware affected victims in Germany, the UK, and the US.
WannaCry
WannaCry ransomware uses an exploit vector named Eternal Blue, which was allegedly leaked by the US National Security Agency (NSA). It appeared in May 2017 and spread over 150 countries where it demanded a ransom in Bitcoin.
The attacker gave the victims a deadline of seven days, after which if a ransom of $300 wasn't paid, they would delete the encrypted data and files. It affected the British National Health Service (NHS) to the point where 16 hospitals had to cancel patient appointments and scheduled operations.
Petya
Petya ransomware made its appearance in March 2016. It targeted the master boot record by encrypting the NTFS file system. When the system rebooted, Petya blocked it from booting into Windows. In June 2017, a strain of Petya was used to carry out a global cyber attack mainly targeted at Ukraine, but also affected several other countries.
Security experts speculated that the attack was not intended to extort ransom from the user, but to cause disruption. Due to certain design changes, there was no way to unlock it after ransom was paid.
SamSam
In 2016, a new ransomware variant called SamSam emerged, which was aimed at Jboss servers. It exploited vulnerabilities on weak servers using a remote desktop protocol (RDP) brute force attack to guess weak passwords until one is broken.
It targeted healthcare and government agencies, through which the authors extorted around $6 million and caused an estimated loss of over $30 million in damages.
Safeguard your assets from ransomware
Ransomware has caused tremendous damage to institutions and organizations in terms of finance and reputation. You can never predict when and how it may show up at your digital doorstep. The only thing you can do is be aware and prepared – always.
Ready to take the next step? Explore malware analysis tools to isolate and investigate different malware in your system.
This article was originally published in 2020. The content has been updated with new information.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.
