Vulnerability scanner software is becoming increasingly popular as enterprises want to mitigate attacks from external entities, especially as hybrid and remote work scenarios have increased external endpoints.
Improve patch and security processes with vulnerability scanner software
With increased network traffic to external devices, it has become all the more important to have solutions that monitor company networks for any threats or weaknesses that malicious actors can exploit. This is where vulnerability scanner software becomes an indispensable tool for enterprises.
As hackers become more persistent and clever, the next threat is just around the corner. For example, office files with malware are a common cyber tactic by threat actors, where the attacker exploits an application like Microsoft Office to deliver malware. With vulnerability scanner software, organizations can stay ahead of these attackers who try to find loopholes in cybersecurity updates or patches.
What is Vulnerability Scanner Software?
Vulnerability scanner software monitors applications and networks to identify security vulnerabilities. The software maintains an up-to-date database of previous vulnerabilities and conducts scans to identify potential exploits.
This database helps enterprises test applications and networks against known vulnerabilities and to identify new ones. This tool typically produces reports detailing an application's or network security's state and provides recommendations to remedy identified issues.
Some vulnerability scanners work similarly to dynamic application security testing (DAST) tools but scan tools instead of mimicking attacks or performing penetration tests.
Want to learn more about Vulnerability Scanner Software? Explore Vulnerability Scanner products.
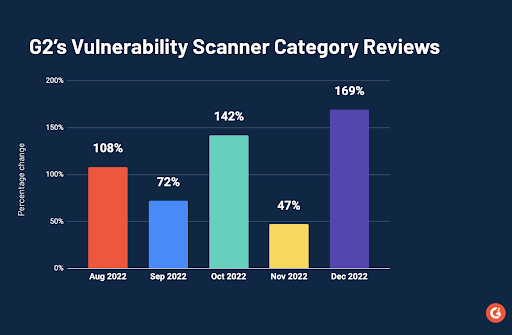
G2 data shows rising interest in the vulnerability scanner software
Visitors to the G2 website validate this increased market interest in vulnerability scanner software. At the end of 2022, G2 witnessed a 169% increase in reviews for the Vulnerability Scanner Software category. This reflects buyers’ increased interest in this category.
According to G2 data for its buyers, the desired capabilities for vulnerability software are:
- The software meets compliance, regulations, and standards relevant to that organization’s industry and business.
- The tool has a user-friendly dashboard that clearly shows risk scores and prioritizes which internal teams should make what efforts.
- The solution can scan and monitor all the systems and infrastructure an organization wants to protect.
Using vulnerability scanner software to combat increasing external threats
As proof that enterprises are experiencing more network traffic with external devices due to hybrid work scenarios, some of G2’s Collaboration & Productivity categories have witnessed significant growth. For example, the Virtual Workplaces subcategory, which includes products that simulate a physical office environment, grew 178% in 2022.
Vulnerability scanner software identifies external threats and vulnerabilities by scanning external systems outside the company's network. In this case of hybrid work scenarios, this would be systems like unsecured home networks or devices such as laptops. External scans can reveal how hackers exploit vulnerabilities and how they commit cybercrimes. For example, external scans give insight into how outside hackers enter an organization’s IT assets and ports and allow users to determine how to deal with these vulnerabilities.
The result is that companies receive insight into how to improve their patch and security processes as well as how to improve their security standards. Several companies can opt for vulnerability scanner software since it can assess threats in real time. Software agents can be installed into each organization’s endpoint and perform deep scans of each, allowing endpoint users to view and monitor each vulnerability it scans and determine whether to patch or fix the vulnerability.
Vulnerability scanning software can also provide web-based scanning for websites. External scanning helps end users focus on the most significant threats and vulnerabilities, and then they can quarantine a breached device until it can be thoroughly investigated.
What are the current challenges with vulnerability scanner software?
Some of the key challenges that buyers of vulnerability scanner software are facing today are:
False positive: The biggest challenge is that vulnerability scanner software can produce false positives and thus slow responses from support.
Scale: Newer vulnerability scanner solutions may not have enough capabilities for a large enterprise. On the flip side, a solution built for large enterprises may be too robust for a medium-sized to smaller business.
On-premises or only cloud-based: Vulnerability scanner software developed only for on-premises may not meet the scanner needs for an organization's cloud applications. At the same time, if it is only cloud-based, it may not be the best choice for organizations that need to scan their entire tech infrastructure.
Price: For some mid-sized companies today, the price of vulnerability scanner software built for large enterprises may be too expensive.
Future of vulnerability scanner software
Not every organization will use vulnerability scanner software in the same way. Some will use it primarily for external threats, while others will use it internally and externally.
A contributing factor to the demand for vulnerability scanner software is that it helps mitigate the growing threat of data breaches that require organizations to meet regulatory standards such as HIPAA, PCI-DSS, and GLBA. And, thanks to the remote and hybrid work trend, the need for the software is unlikely to change anytime soon.
Edited by Shanti S Nair

Sarah Wallace
Sarah is a Research Principal at G2. She has worked as an industry analyst for over 20 years and focuses on cybersecurity for areas such as cloud and networks.
