The return on investment (ROI) is impossible to calculate for cybersecurity solutions. For such solutions, value isn’t found through dollars saved or deals closed; value is found in unobstructed disaster avoidance and a sense of trust for employees, partners, and customers.
Instead of implementing the latest buzzword technology that claims to automate a niche component of security operations, security professionals can improve their security posture by properly training staff, understanding threats, and optimizing existing detection, response, and investigation solutions.
This is more true for some tools than others. Obviously, it’s important to examine empirical security results to ensure the tools under consideration are capable of handling common and advanced threats, specifically in relation to the assets the user aims to secure.
However, for some tools, the crux of success balances between empirical effectiveness and usable effectiveness.
The user: problem and answer
The issue, as always, is the end user. This is not because they’re untrained or unprepared, but because they are not set up for success. Oftentimes, the problem of and the solution to having a good security posture at a company comes down to end users properly using tools. User-centric solutions like cloud, email, and web security, multi-factor authentication (MFA) tools, or even security awareness training programs are heavily reliant on adoption and usability.
Even then, the user is simply a problem if the solution is obtrusive or confusing.
If user adoption is optional, its implementation is going to be less successful. Some percentage of users will not opt for additional protection or verification if posed with the question, but the less intimidating and more easily understood the solution is, the more likely workers are to adopt it.
Not to frame users as the scapegoat, as they are also the heroes of this story.
If these solutions are optional, users are the individuals who choose to update passwords or choose to enact their training and don’t download a suspicious file; only they will follow through with their security training and activate MFA, fulfill continuous authentication requirements, and practice their anti-phishing training drills.
Adoption is a separate factor from empirical security effectiveness, which is a very important factor in deciding which tools a business will adopt. Still, after completing all the demos, gathering information on effectiveness, and allowing cross-functional teams to test the tool, factors beyond efficacy begin to emerge.
As a result, it’s important to view data-driven security acquisition beyond budgetary restrictions and false positive numbers.
Investments: time, money, and training
There are numerous investments a company makes when implementing a new solution, many of which are less obvious than dollar totals. Some of these investments may even have a larger impact on the organization as a whole than the literal cost of the technology.
Time: From research to implementation, time is a huge factor in the software acquisition process. It’s important not to rush the research or implementation of a new solution. Speedy setup might put a tool into action quickly but may also result in misconfigurations, misallocated privileges, and employees misunderstanding its use.
Only 41% of companies reach 100% user adoption for multi-factor authentication (MFA) tools, per G2 reviews as of October 17, 2020.
Research: As the most objectively perceivable investment, money is often the deciding factor in buying decisions, but money is involved in ways beyond the price tag. Companies that fail to dedicate their time to properly and thoroughly researching vendors and products likely won’t adopt the most effective solutions. They also may miss out on a transformative technology that has just hit the market.
Training: Most companies today have some kind of security training, but few have enough. There is already a shortage of skilled security professionals today and forcing security responsibilities onto IT staff and developers without proper training is a recipe for disaster. The same can be said for general employees—without proper training, every employee and their online activity pose a risk to the company and its customers.
ROI: adoption and efficacy
Two things that will surely determine whether or not a solution is considered successful are its usability and effectiveness.
The usability challenge is a double-sided spear. On one end, the company must select the right product and hope employees and everyday users agree it’s intuitive and hop on board. On the other end, is the need for companies to train those employees in an effective manner.
Effectiveness is easier to measure. An effective solution lowers the frequency of infections, false positives, and security incidents in general, but when a solution is not effective, it may be the result of numerous factors from adoption and training to configuration and integration.
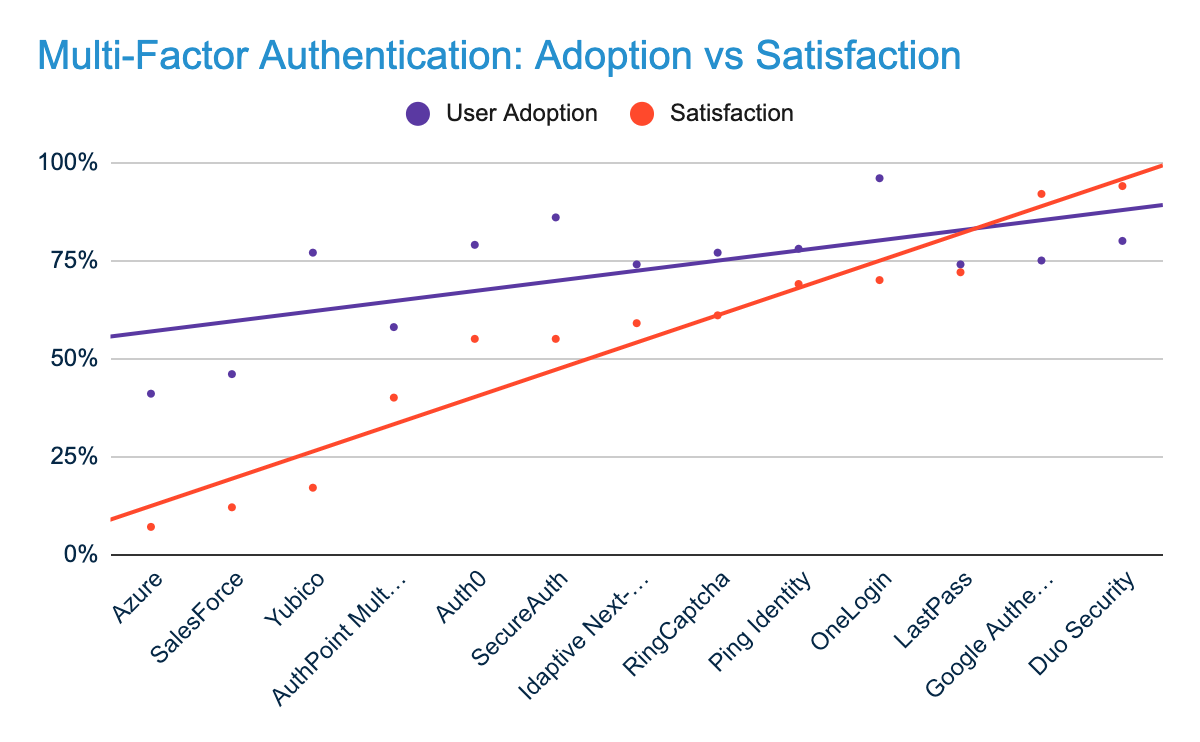 Source: Grid® Report for Multi-Factor Authentication (MFA) | Fall 2020 (Ranked by Satisfaction)
Source: Grid® Report for Multi-Factor Authentication (MFA) | Fall 2020 (Ranked by Satisfaction)
Adoption: If a tool is too clunky or confusing, it’s not adopted. If people aren’t properly trained, it’s not adopted. Furthermore, for the most part, if a tool isn’t required, it’s not adopted.
Mandated, continuous training can help combat low user adoption rates, but only if the training is digestible. Increased adoption will also prevent shadow IT resulting from staff venturing out on their own to find a tool to do the job.
Efficacy: The key question when it comes to efficacy is: “did this make my job easier?” If the answer is yes, the tool is working. If the answer is maybe, a few questions should be asked.
Companies must find out if it’s a single-user or a company-wide issue, review employee training requirements and content, and reevaluate the tool’s empirical effectiveness. A combination of these factors should demonstrate if the issue can be fixed internally or if it’s the solution that needs replacing.
Security ROI is trust and value, not dollars and cents
Happy users are effective users. Companies should not force a solution down workers’ throats because it’s affordable. Employees won’t use the tool if they don’t have to and won’t be efficient if they do. Instead, it is advisable to let end users give their opinions on new tools, and the company must conduct all the demos and consider all the alternatives.
The data that security professionals are responsible for protecting can devastate people and businesses if exposed. So, the goal of an organization or its security team should be more than just avoiding jail time. It should be to empower security professionals to protect the company and its customers by including end users in the decision-making process of selecting the right tool and improving the day-to-day security posture of the company by effectively using security tools.
Want to learn more about Password Managers? Explore Password Managers products.

Aaron Walker
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.
