Security sometimes demands speed.
While encrypting a huge amount of data, you need an encryption method that can process high data volumes without causing a significant impact on network, power, or memory. Symmetric encryption is one such technique that can help you encrypt data faster while providing substantial security.
Organizations generally use encryption software to safeguard their data in use, transit, or at rest. These software work with both symmetric and asymmetric encryption depending on use cases and need.
What is symmetric encryption?
Symmetric encryption is a technique in which both encryption and decryption processes are carried out using a single key. A user encrypting a message with a secret key has to share it with the recipient to carry out decryption.
Unlike asymmetric encryption, which uses a pair of keys, symmetric encryption uses one secret key and has a more straightforward encryption mechanism. Anyone who doesn’t possess the shared secret cannot theoretically decrypt the message encrypted with the secret key. But practically, if a user encrypts information with a mechanism that uses weak encryption algorithms, it can be decoded. Attackers can conduct brute force attacks using systems with high computing power to gain unauthorized access to your information.
Symmetric encryption uses less computational power and is relatively simpler to execute and scale in organizations. The major drawback is that two parties involved in the communication need to exchange a private key, which attackers can intercept.
Symmetric encryption is faster and uses less computational power as compared to public-key cryptography. Therefore, it’s a favorable choice for users who need to carry out bulk encryption. It’s used to encrypt and decrypt databases. Since the private key is available to the database itself, you can use it to encrypt or decrypt large quantities of data.
Before we dive deeper into encryption algorithms and use cases, let’s address a significant challenge users face when using symmetric encryption – key management.
Symmetric encryption and key management
Key management is a challenge that’s not fairly new. Although there are many benefits of symmetric encryption, improper symmetric key management is one issue that prevents its widespread use.
There are many other issues related to key management that people face in implementing symmetric encryption:
- Key exhaustion: When you use the same encryption keys multiple times, there is a chance of information leakage. Attackers can use this information to reconstruct the key. You need to maintain a key hierarchy and ensure proper key rotation to protect your encryption keys from attackers. Implementing an encryption key management system will help you store them while retaining a backup if a key is lost.
- Attribution: Symmetric keys don’t contain embedded metadata that records information like access control or expiry date. ANSI X9-31 standard addresses this issue by attaching the prescribed usage information with the key. However, you'll need a key management system to have complete control over what a key can be used for and when.
- Scalability: Whether there are tens or hundreds of keys, you can manage them manually. But when there is a deployment at scale, arranging effective key rotation and tracking expiration becomes a puzzle.
Managing symmetric key encryption on a large scale can be challenging, especially when you want to ensure robust cybersecurity in a decentralized corporate setup. You’ll need powerful key management software to gain proper visibility and control over enrolled keys. You can start with a free version of key management software and discover how seamless your key management process can become.
Want to learn more about Encryption Software? Explore Encryption products.
How does symmetric encryption work?
Before we dive into the technical process, you should be familiar with a few components involved in the process.
These components of symmetric key encryption are:
- Plaintext: A message that you want to encrypt
- Symmetric encryption algorithm: A mathematical algorithm that converts a message into an unintelligible format
- Secret key: A key that’s used to encrypt or decrypt data
- Ciphertext: An encrypted message that one cannot understand when decrypting it with a secret key
Let’s take an example to understand a symmetric cipher (algorithm). Suppose you have to encrypt a message that says, “We are meeting in the mall.” For instance, let’s use a basic shift encryption algorithm, also known as Caesar cipher. Here, the ciphertext is built by choosing the third letter alphabetically from the given sequence of characters in plaintext.
In our example, “W” in the plaintext will become “Z” of ciphertext, “e” in the plaintext will become “h” in the ciphertext, and so on. This encryption process will be carried out using a secret key, which the recipient will use to decrypt the message.
Therefore, when we use the shift algorithm (with three spaces) to encrypt “We are meeting in the mall,” the ciphertext becomes, “ze duh phhxlqj lq xkh pdoo.” The message recipient can now use the same secret key to convert ciphertext into plaintext.
This is how symmetric encryption works. We used a basic encryption algorithm (cipher) to help you quickly understand the process. The industry’s symmetric encryption algorithms require more complex calculations to create ciphertext and are difficult to predict.
Symmetric encryption use cases
Symmetric encryption is quite popular in many industries and has multiple use cases. In the real world, it’s commonly used in banking, Hypertext Transfer Protocol Secure (HTTPS), and for carrying out encryption of data at rest.
You can find symmetric encryption as one of the vital components in the following sectors:
- Banking: Symmetric encryption is one of the key components of Payment Card Industry (PCI) compliance. It enables businesses to protect data at rest.
- Data storage services: Many services that store data adopt symmetric encryption to protect against intentional or accidental exposure. Services such as Microsoft Azure, Google Suite, and others use symmetric encryption to protect the data.
- Web security through HTTPS: Symmetric encryption is an integral part of website security. Although asymmetric encryption carries out authentication for two parties, the actual encryption process is carried out through symmetric encryption.
Many use cases employ symmetric and asymmetric encryption together to ensure maximum security. They encrypt the data in bulk using symmetric encryption and then encrypt the symmetric encryption key with asymmetric encryption.
Symmetric vs. asymmetric encryption
Both types of encryption, symmetric or asymmetric, have their advantages and disadvantages. Users can choose a particular kind of encryption that best suits their needs or combine both to realize robust security.
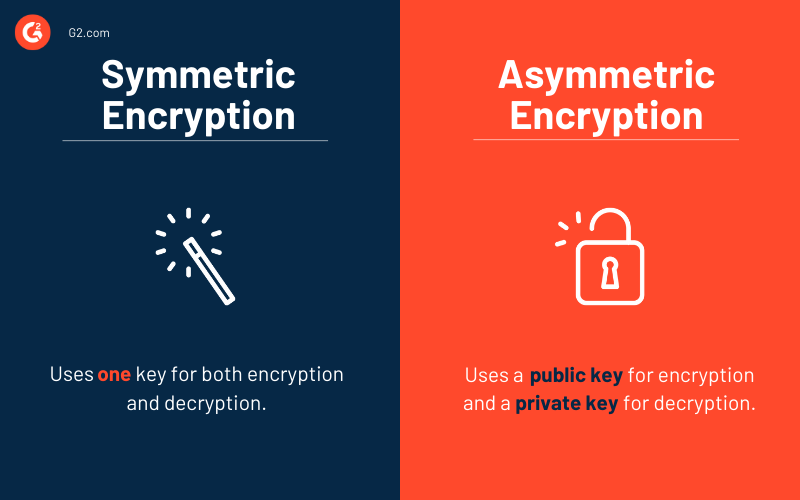
There are various points based on which we can differentiate between symmetric and asymmetric encryption.
|
Areas of differences |
Symmetric encryption |
Asymmetric encryption |
|
Speed |
It’s fast |
It’s comparatively slower |
|
Security |
Offers less security as users have to share the same secret key |
Provides more protection with separate keys for encryption and decryption |
|
Data volume |
Used in transmitting large data volume |
Used in transmitting low data volume. |
|
Consumption of resources |
Works with lesser usage of resources |
Works with high resource consumption |
|
Number of keys |
Uses one key for both symmetric and asymmetric encryption |
Uses two different keys for encryption and decryption. |
|
Key lengths |
128-bit or 256-bit |
RSA 2048-bit or higher |
|
Algorithms |
DES, 3DES, AES, RC4, and more |
RSA, Diffie-Hellman, Elliptic curve cryptography (ECC), and more |
Most significant trade-offs in symmetric and asymmetric encryption
Although asymmetric encryption is an advanced encryption technique, symmetric encryption is still used today because of its benefits. Sometimes, users prefer to adopt symmetric and asymmetric encryption (for example, Secure Socket Layers/Transport Layer Security or mobile chat systems).
While choosing between symmetric and asymmetric encryption, you’ll come across a situation that’ll require you to make a tradeoff between security and speed.
Security
Asymmetric encryption provides better security compared to symmetric encryption. This is because, in symmetric cryptography, you need to share the secret key with a recipient since both encryption and decryption occur using the same key. It opens up opportunities for an attacker to intercept the secret key in transmission and decrypt the message.
Unlike symmetric encryption, asymmetric encryption uses two keys: public key and private key. Here, the recipient of the message generates the key pair. The public key is available to all, but the private key is with the recipient only. Any message encrypted with a public key can only be decrypted by its corresponding private key in the recipient’s custody. Since asymmetric encryption doesn’t require sharing or transmitting keys, the chances of an attacker interfering with them are less, making it a more secure encryption method.
Therefore, in places where you need greater security and speed of encryption isn’t a high priority, asymmetric encryption would be a favorable choice.
Speed
Symmetric encryption is much faster than asymmetric encryption. Symmetric encryption works with lesser key sizes and one secret key, which gives it an upper edge when encryption speed is a priority.
On the contrary, asymmetric cryptography is a slower process and sometimes inefficient as it can cause performance issues in a network. Asymmetric encryption works with large key sizes that can possibly result in higher power consumption and memory issues.
Simply put, if you need to work with large volumes of data and speed is a priority, symmetric-key cryptography would be the favorable choice.
Examples of symmetric encryption
Symmetric encryption uses multiple algorithms based on complexity, computational power, and other factors. These algorithms convert plaintext into ciphertext using a secret key.
Advanced Encryption Standard (AES)
AES belongs to the Rijndael family of block cipher algorithms. It has a fixed block size of 128-bits with varying key sizes of 128, 192, or 256 bits.
Did you know? AES does all its computations in bytes instead of bits. Therefore, a 128-bit plaintext block is treated as 16 bytes.
There are many ways AES encryption is used. You can find its widespread use in processor security, file encryption, wireless security, and various other places. The main reason behind AES’ popularity is the level of protection with a fast computational speed. It provides an effective and efficient form of encryption that’s favorable to governments and businesses worldwide.
The Advanced Encryption Standard is based on a substitution-permutation network. The plaintext goes through a specific number of iterations based on the key size to generate the ciphertext.
How AES works
Let’s dive into the basics to understand how AES works. The symmetric encryption process involves scrambling plaintext into unintelligible information and a key to decrypt the scrambled data. When you enter plaintext into AES, it undergoes four scrambling operations in one round. Based on the encryption key length, the number of rounds will vary.
The number of rounds a scrambling process occurs in AES are:
- 10 rounds for 128-bit AES encryption key
- 12 rounds for 192-bit AES encryption key
- 14 rounds for 256-bit AES encryption key
Simply put, if the plaintext is X, the AES algorithm will produce Y in round one, Z in round two. It’ll scramble the output until it has completed the total number of rounds, producing the final output as ciphertext. Remember that in every round, it runs four scrambling operations.
With the modern computing capabilities, it’d take almost forever for an attacker to crack AES 256 bit encryption.
Data Encryption Standard and Triple Data Encryption Standard
Data Encryption Standard (DES) has played a phenomenal role in the early development of cryptography. It had a short key length of 64 bits, which is insecure now, but it was quite favorable in the recent past (the 1970s).
DES is a block cipher algorithm that uses a 64-bit block size. It takes a fixed-length plaintext string and converts it into a string of ciphertext of the same length, using complex mathematical functions.
Although DES had a 64-bit key length, the encryption algorithm used 56 bits only. The remaining 8 bits acted as check bits. DES encryption didn’t offer sufficient security against brute force attacks and was later superseded by Triple Data Encryption Standard (3DES) and then AES.
3DES was introduced to combat rising instances of brute force attacks on DES. Earlier DES users weren’t in favor of changing the encryption algorithm, considering the high cost and extensive time it’d take to make the transition. 3DES enabled such users to better secure their data without making a complete change in the cipher.
3DES applies DES encryption three times to enhance its strength while using a total key length of 168-bits.
Apart from AES, DES, and 3DES, other popular symmetric encryption algorithms are Twofish, Blowfish, IDEA, RC4, and many others.
Speed vs. security: What’s your choice?
Symmetric encryption is favorable where speed of encryption is a priority, and asymmetric encryption is fit for purposes where security claims a higher priority over speed.
Encrypting a message provides security regardless of what encryption you use, symmetric or asymmetric. It’s just that the level of security (difficulty in cracking the encryption key) can vary.
You can use both symmetric and asymmetric encryption to safeguard the information better. For example, in SSL/TLS, asymmetric encryption is used to verify digital signatures, and the actual encryption process occurs through symmetric encryption.
Learn more about SSL and TLS certificates software and how you can leverage them to ensure robust security and comply with current search engine standards.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.