In an increasingly data-centric digital world, security can’t be compromised.
Remote access continues to be a savior for IT operations in the post-pandemic landscape. However, despite its many perks, technology doesn’t come without challenges. The biggest challenge is exposure to cyber attacks when interacting with systems over unsecured networks. Secure shell (SSH) has been a game changer in overcoming this problem.
What is SSH?
Secure shell (SSH) is a remote network protocol that allows system administrators to access, control, and modify servers over unsecured networks. It ensures that all communication is encrypted by providing secure access when logging into a remote system to execute commands.
Terminal emulator software comes with automatic SSH file transfer protocol (SFTP) and assists users with secured file access and remote file management.
While SSH was developed for Unix-like operating systems, such as Linux and macOS, it also works on Windows. You only need an SSH client like PuTTy to open SSH connections on your system.
How does SSH work?
Before SSH, there was no secure way of connecting computers remotely.
Let’s say you have a confidential document to share with your colleague. When you pass it over the long chain of contacts connecting you, there is a risk of anyone reading the content inside. The only way to avoid this privacy invasion is if those documents are locked with a unique key that only your colleague can access.
The 3 layers of SSH protocol:
- Transport layer: Secures contact between server and client, provides data encryption and establishes data integrity.
- Authentication layer: Conducts client authentication for the server, confirming the identity of the operating agent.
- Connection layer: Multiplexes SSH tunnel into logical channels after the authentication.
The secure shell protocol operates on a client-server model and uses public key cryptography to verify the client. It provides an encrypted medium to exchange information, regardless of the underlying network infrastructure.
.png)
There are two steps involved in establishing an SSH connection. First, the systems should mutually decide on encryption standards to safeguard future communications. Then, the user must authenticate themselves. If the credentials match, then access is granted.
SSH works with connections like Transmission Control Protocol (TCP) to send over data as packets. Once the connection is established, it uses different SSH encryption algorithms to ensure data privacy and integrity between the client and server.
The information inside these data packets gets decrypted by the server with a message authentication code available only to the server and the client. And that’s how the data gets transferred safely over unsecured networks because SSH encrypts data, not the connection between systems.
Check out my review of the best terminal emulators to find the perfect fit for your SSH sessions, whether you're on Windows, Mac, or Linux.
Want to learn more about Terminal Emulator Software? Explore Terminal Emulator products.
A brief history of SSH
Before SSH, Teletype Network Protocol (Telnet) was used to access and modify files by connecting to computers remotely. In 1995, Tatu Ylönen, a researcher at the Helsinki University of Technology in Finland, designed SSH to replace unsecured protocols like Telnet. SSH ensured that external forces couldn't intercept private data, which was one of Telnet's most significant security threats.
The first version of the secure shell became known as SSH-1 and was soon a popular tool across industries. Soon enough, the Internet Engineering Task Force (IETF) started working on developing a successor to this protocol. In 2006, SSH-2 was introduced with security improvements and became the new standard.
SSH-2 uses different encryption and authentication algorithms. It’s a complete rewrite of the original protocol and incorporates built-in protections against the known challenges of SSH1.
Core SSH features
Generally, SSH is used to establish a secure connection with a remote server. But it’s also used for transferring files securely, forwarding ports, mounting remote directories, redirecting GUI, and proxy arbitrary traffic.
Take a look at some of the core features of SSH.
SSHD
Establishing a connection requires the remote computer to run SSH daemon (SSHD). This program finds and authenticates connection requests. It uses the SSH protocol to encrypt the data exchange between local hosts over unsecured networks.
There’s also a secure shell fingerprint record (SSHFP) that equips the public host key fingerprints to verify the authenticity of the host.
SSH tunneling and port forwarding
The technology of port forwarding or tunneling reroutes unencrypted traffic on a network through an encrypted channel. OpenSSH, a popular open-source SSH server, supports three types of port forwarding: local, remote, and dynamic. It can also implement virtual private networks (VPNs) to access geo-restricted content across firewalls.
SSH keys and agents
Out of the various authentication mechanisms in SSH, the use of keys is the most secure compared to passwords. A key is encrypted for improved security and can be used only after decrypting it by entering a secret passphrase. Plus, SSH keys, combined with an authentication agent, can protect your computer accounts without memorizing any passwords or entering them repeatedly.
Encryption technologies used by SSH
What sets SSH apart is that it uses encryption software technology to transfer information safely. It safeguards all traffic between the client and the server, making it difficult for cyber attackers to access the encrypted data. There are three SSH encryption methods:
1. Symmetrical encryption
In symmetric encryption, a secret key is used to encrypt and decrypt data by the client and server. So, anyone with access to the key can encrypt the shared data. Each key is unique to individual SSH sessions and is generated before the client authentication stage.
This process is highly secure because it’s carried out by a unique key exchange algorithm. Even if an external system accesses the file, it won’t be able to decrypt the information because the key exchange algorithm will be unknown.
2. Asymmetrical encryption
This method differs from symmetric encryption because it uses two SSH keys: private and public. These keys are paired using complex mathematical algorithms and work together to encrypt and decrypt messages.
Anyone can use the public key to encrypt, but only the recipient of the private key can decrypt that message. The mechanism behind encryption and decryption is entirely automated.
3. Hashing
This method is not the same as encryption but is a different form of cryptography used in SSH connections. Hashing is one-way and irreversible, which means it can’t be decrypted.
The hashing algorithm provides a unique hexadecimal value of a fixed length which verifies everything on the file. SSH uses hashing to verify a message’s authenticity, ensuring it hasn’t been tampered with.
Top 5 terminal emulator software
*These are the five leading terminal emulator software from G2’s Fall 2024 Grid® Report.

Importance of SSH keys
The SSH protocol is one of the most secure encryption methods today. It adds more security, strengthens credibility, and offers practical ways to handle sensitive data.
One of the main challenges companies across sectors face is the lack of means to expand security on-premises. With SSH, admins can protect data integrity and the changes made to the server. Through its encryption methods, SSH protocol provides the highest protection from malicious actions like intercepting data or invading servers with confidential information.
SSH keys restrict data access only to the authenticated user, providing more control to a company. This SSH security protocol also controls access to remote machines or servers by blocking unauthorized access to those systems.
SSH vs. SSL vs. SCP
While all three of these mechanisms are used for encrypting and securing connections between systems, there are some key differences.
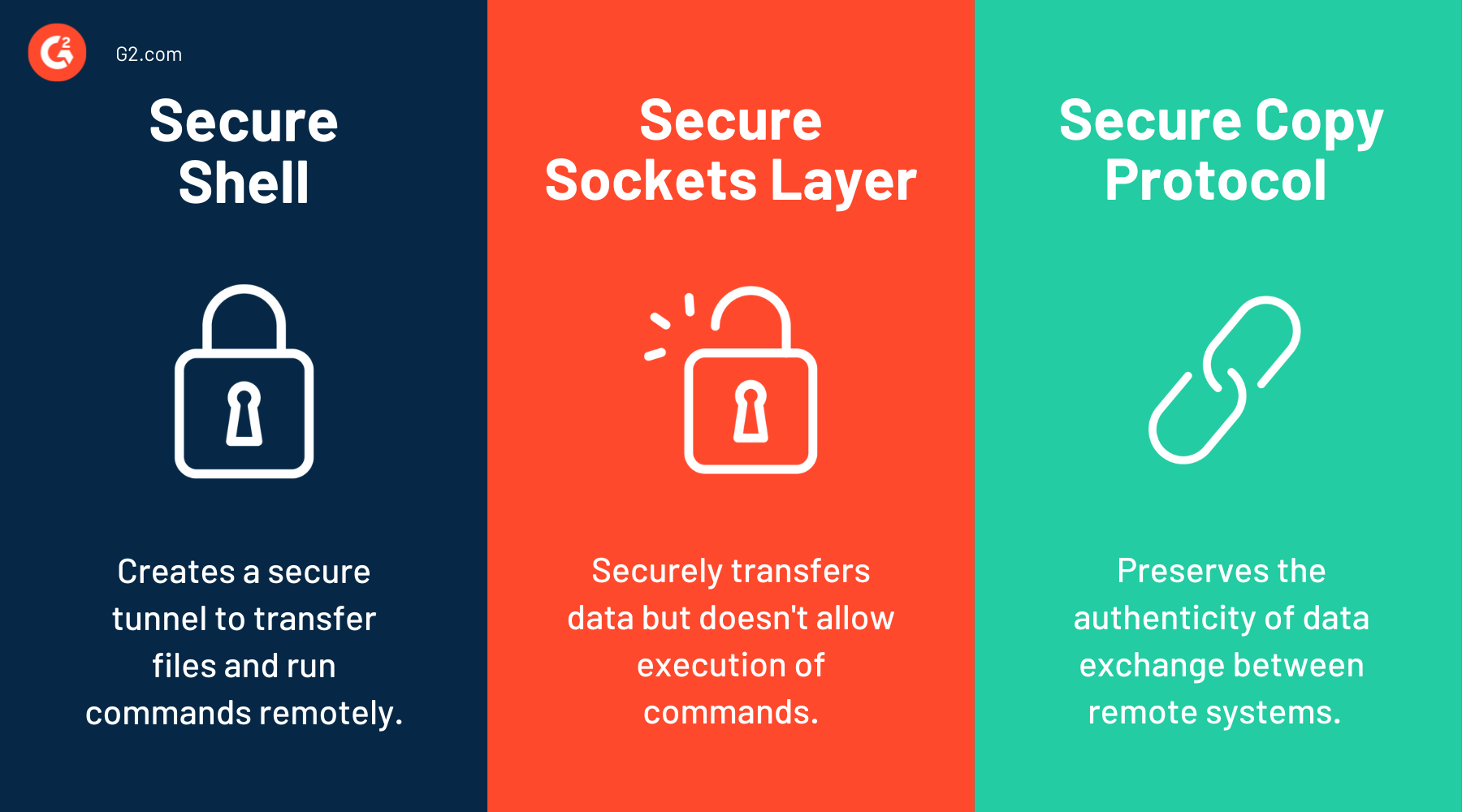
SSH is a cryptographic network protocol. It enables secure file transfer, accessing, and configuring remote systems to run commands securely. Secure sockets layer (SSL) is a security protocol that does not allow you to run commands remotely like SSH.
Secure copy protocol (SCP) is a network protocol that uses SSH secure connection to transfer files. However, SCP is focused on securing the integrity of data exchange and cannot be used to access or control devices remotely like SSH.
Common SSH commands
While SSH commands also have graphical implementations, they are usually performed using terminal emulators or executed as part of a script with command line interfaces (CLI).
Here are some examples of SSH commands and their functionality.
| SSH command | Function |
| ssh-keygen | Creates a new authentication key pair for SSH |
| ssh-copy-id | Used to copy, install, and configure an SSH key |
| ssh-agent | Tracks identity keys and allows logging into a server without reentering passwords |
| ssh-add | Adds a key to the SSH authentication agent and enforces SSO |
| scp | SSH version of rcp (remote copy), copies files from one computer to another |
| sftp | SSH version of File Transfer Protocol (FTP) solutions, copies files from one system to another |
SSH use cases
SSH allows organizations to communicate securely over the internet. It doesn’t come with complications of traditional processes, like Telnet or FTP, and offers easy access through automated mechanisms. System administrators use SSH to:
- Establish communication channels between local machines and remote hosts
- Execute commands on a remote server using a command line interface
- Connect automatically to servers to modify configurations
- Perform remote management tasks like backups, software installation, updates, and troubleshooting
- Provide single sign-on options to access multiple user accounts without passwords
- Create a secure authentication process for database management
- Enable key-based authentication for secure automation
How secure is SSH?
One of the primary questions regarding SSH is, "What security benefit is provided by SSH?" SSH has many security features, highlighting how it safeguards sensitive data, enhances user authentication, and protects against various cyber threats:
- Strong encryption: SSH uses robust encryption algorithms, like AES, to protect data in transit and ensure confidentiality against eavesdropping.
- Public key authentication: It utilizes public key cryptography for authentication, allowing users to connect without transmitting passwords, reducing credential theft risk.
- Session integrity: SSH includes mechanisms to verify that data sent and received has not been altered, protecting against tampering.
- Protection against cyber threats: It safeguards against attacks such as man-in-the-middle attacks, IP spoofing, and data manipulation.
- Access control: SSH allows administrators to manage user access effectively and revoke permissions as needed.
- Widely accepted standards: It utilizes well-established cryptographic practices recognized in the cybersecurity community, enhancing trust in its security.
- Regular updates: Ongoing updates and security patches help protect against emerging threats and maintain a secure environment.
Is SSH safer than VPN?
A virtual private network (VPN) is built over public network infrastructure like the internet. It masks your IP address by encrypting and routing traffic through a remote server. It protects your personal information when accessing public Wi-Fi and ensures that nobody can snoop on your data or track your geolocation by checking your IP address or hostname.
VPN software is easy to use and provides top-notch encryption and privacy protection. At first sight, SSH seems similar to VPN services, but some differences exist.
While both of these technologies add an extra layer of security when surfing the web, SSH functions on systems, while a VPN secures your network. So, between SSH and VPN, the latter offers higher protection and is easier to set up as a business solution.
Benefits and challenges of SSH
Like any other security protocol, SSH is a mixed bag that offers excellent benefits and some challenges. Understanding both factors on a deeper level will help businesses make the most of their SSH protocol implementations.
Benefits of SSH
SSH's superior encryption mechanisms make it the best choice for business applications. Here are some of the main benefits of using SSH.
- Gives secure access without sharing passwords with multiple users
- Executes shell commands on a remote computer
- Streamlines permission management by letting all parties log in as the same user
- Makes remote file management easy for administrators
- Permits access revocation as and when needed
- Protects from cyber attacks like IP source routing, spoofing, and data manipulation
- Allows tunneling of other protocols like FTP and DNS security
- Uses unique key pairs instead of traditional login credentials
Challenges of SSH
While SSH is considered to be an all-rounder in terms of security, it’s known to have some vulnerabilities, such as:
- Violation of security regulations due to unrestricted outbound SSH transactions
- Poor SSH key management can result in key sprawl leading to cyber attacks
- Slow response to high-bandwidth commands over slower SSH networks
- Delay in incident response process gives hackers more time to access confidential data
- Lack of monitoring options for encrypted data due to added difficulty and expenses
- Exposure of SSH ports can serve as a backdoor entrance to malware attacks
SSH best practices
While SSH has established itself as the industry standard for security, it’s only as secure as configurations applied to the server and client. Keeping in mind the best practices of secure shell is fundamental for preventing cybersecurity threats.
Enable two-factor authentication
A system with two-factor authentication enabled requires two different forms of verification to provide access. Since organizations use SSH to build a secure connection to remote systems, enforcing another layer of SSH security is vital to offer complete protection.
System administrators should ensure that users logging into a remote system via SSH authenticate with more than one credential. This practice makes this authentication method more secure than a password, which can be hacked, or a single SSH key.
Disable root user login
The SSH root access can be risky because it gives full access and control over the entire system. Disabling the root user login is needed because it’s on by default, which allows hackers to hunt for credentials easily.
Tip: Admins can change the root user login settings by updating the SSH config file (/etc/ssh/sshd_config) and setting the option “PermitRootLogin” to “no.”
The best way to tackle this is by creating individual logins. This allows control over what each user can access, making it easier to track and audit each activity.
Use SSH certificates for client authentication
SSH key authentication is superior to regular passwords. But when securing a remote login process, you must remember the complexities of SSH key management.
SSH keys are text-based and come with the risk of being copied or hacked. This is why authenticating with SSH certificates is a more powerful option, as it can secure the login process with public keys and provide a certificate to verify the authenticity of each key.
Impose firewall
A firewall not only reviews incoming and outgoing traffic but also monitors the traffic within a network, which helps secure the server. It operates on a set of pre-determined rules and can reduce the chances of cyber attacks.
By configuring your firewall, you can enable packet filtering, which means it can accept or reject data packets and make the best decision to secure your system. You can also filter user access and get alerts on unauthorized access attempts with the right firewall software.
Change the default port number
On Linux systems, SSH’s default server runs on port number 22. When searching for open SSH servers, the default port is the first thing hackers look into.
While it doesn’t necessarily enhance the overall security, changing the default port will secure your server by hiding the SSH port from attacks like brute force. It also hides you from bots searching for open SSH servers to attack and gain access.
It’s not a question of if but when.
There’s a lot of truth in the old saying, “Prevention is better than cure.” Cyber security should not be taken lightly in the current business environment where digital assets hold so much value for a company.
SSH is a powerful tool for IT administrators to protect businesses against unauthorized access and data theft. The right blend of security solutions can help create a robust system free from cyber attack risks.
Check out the best encryption key management software to enforce security policies for your key storage and distribution.
This article was originally published in 2023. It has been updated with new information. robust

Washija Kazim
Washija Kazim is a Sr. Content Marketing Specialist at G2 focused on creating actionable SaaS content for IT management and infrastructure needs. With a professional degree in business administration, she specializes in subjects like business logic, impact analysis, data lifecycle management, and cryptocurrency. In her spare time, she can be found buried nose-deep in a book, lost in her favorite cinematic world, or planning her next trip to the mountains.
