Many people and companies handle your personal information.
But the vast majority of them would never use it in ways that could have severe consequences. They’ll usually have your back first. However, others may collect and store your information without your knowledge – whether they copy keystrokes while you write a research paper or they steal your credit card information from a major brand like Target.
These hostile individuals use programs such as spyware to record and store user activity. To help prevent this, people use antivirus software to detect and remove spyware, as it can ultimately compromise users’ online privacy.
What is spyware?
Spyware is software that tracks your activity on a computer or mobile device, gathers and records information, and then transmits that information to another party.
Spyware is used for many purposes, but it’s almost always malicious. It can take screenshots of your computer screen, video recordings of you using your webcam, and even audio recordings via your microphone.
Sometimes it collects information from your hard drive, like documents opened and websites visited. Spyware may gather your email addresses, passwords for websites or apps, credit card numbers, bank account information, and other sensitive data such as your Wi-Fi password. For example, law enforcement authorities can use spyware to locate criminals, while scammers may use it to take advantage of unsuspecting users who don’t know any better.
Because spyware does not require consent before collecting information, it’s often considered a privacy invasion. Many people think that spyware is malware because so many malicious programs are designed to collect sensitive information the same way: silently, invisibly, and without the user’s knowledge or consent.
Types of spyware
Before you take a deep dive into the types of spyware, take a look at three significant categories out there:
- Hardware-based spyware tracks activity using a physical device installed on your laptop or desktop. The most common type of hardware-based spyware is a camera hidden in the frame of a laptop.
- Software-based spyware is an application installed on your device that records everything you do. Most people don't know about this type because it's well-hidden.
- Web trackers are sneaky packages that websites put into their code to track user activity.
There are several types of spyware and each one used for a different purpose. Below is a rundown of some of the most common types:
Password stealers
Passwords stealers steal your login details from various websites and may try to get your credit card numbers when you’re shopping online. Password stealers are a type of trojan installed to steal passwords from popular web browsers and programs such as Internet Explorer, Google Chrome, Opera, and Mozilla Firefox.
These malicious programs hide in other programs and often go undetected. They may operate on a computer as a simple bit of code or take on the appearance of a program that the user might reasonably install. Password stealers may also download other malware onto the computer without the user's knowledge.
Signs that your computer may be compromised with a password stealer:
- Strange error messages when using websites and apps
- The inability to log in to certain sites
- Downloads from websites you did not initiate
- Unusual pop-ups and advertisements appearing on your screen
Banking trojans
Banking trojans allow hackers to take control of your online bank account, steal money directly from it, or alter your balance so you don’t realize the difference. These can be hard to detect because they often appear as customized versions of antivirus software that may not be easily detected as fake.
Infostealers
Infostealers work by collecting information from your computer – they gather all sorts of stuff, including financial documents and personal photos. They can also send this information back to whoever installed the spyware in the first place.
Infostealers use phishing emails to get you to click on links that contain hidden malware. When you open an infected file, the malware will begin to infect your computer with spyware that can record your keyboard inputs, passwords, credit card numbers, bank account information, and other personal information without your knowledge.
Keyloggers
Keyloggers are essentially a hacker’s search engine for your computer - these programs record everything you type on your keyboard, including usernames and passwords for services like email and online banking.
Keyloggers collect information about a computer's activity, including keystrokes, websites visited, search history, email discussions, chatroom dialogue, and system credentials. These programs can monitor employee activity on work computers or keep an eye on childrens’ internet activity.
Adware
Adware is software that displays advertisements to generate revenue for its operators. Some security professionals view it as the forerunner of modern-day unwanted programs. Malicious adware uses underhanded methods to disguise itself as legitimate or piggyback on another program to trick you into installing it on your computer, tablet, or mobile device.
Adware is more of a pesky nuisance than a harmful malware threat to your cybersecurity. If the adware authors sell your browsing behavior and information to third parties, they can use it to target you with more customized advertisements.
Mobile spyware
Mobile spyware is designed to monitor and record the end users’ actions on a mobile device without their knowledge or permission. Once downloaded, mobile spyware eavesdrops on conversations held on or near the smartphone. It can also access data stored on or transmitted by the device, including call logs, text messages, global positioning system (GPS) location information, and photos.
Want to learn more about Antivirus Software? Explore Antivirus products.
Examples of spyware
Although some spyware is innocuous and simply does things like track a user’s web browsing habits, others are built specifically for malicious purposes.
CoolWebSearch
One of the most widely-known malware that features spyware capabilities is CoolWebSearch (CWS). This malware was created in 2006 and is widely available on the internet, infecting nearly 10 million computers worldwide.
CWS steals sensitive information from users, including passwords and bank account details. It affects computers in almost 100 countries and comes preloaded with other kinds of malicious software.
Hawkeye
Researchers at Kaspersky labs discovered Hawkeye in 2012. It steals sensitive information from Android-based mobile devices. The developers behind this program use fake security certificates to bypass Google Play’s security mechanisms, allowing them to install the malicious software without users knowing it exists on their devices.
Hawkeye gathers phone numbers, text messages, and records of calls made or received on the infected device. It then sends this data back to its creators.
Agent Tesla
Agent Tesla (AT) is one of the more complex and difficult-to-detect pieces of spyware available to hackers. AT typically enters a machine as a trojan or malicious program disguised as something else. Once in the device, AT activates as a remote access tool (RAT), which means it can not only steal your data but also control your system entirely.
Pegasus
Pegasus is spyware developed by NSO Group, an Israeli cyber-arms company. It targets mobile phones and other devices running most versions of Apple's iOS and Google's Android operating system. Pegasus can exploit vulnerabilities, including zero-day exploits.
As of 2018, Pegasus can read text messages, track calls, collect passwords, track location, access the target device's microphone and camera, and harvest information from apps. The spyware gets its name from Pegasus, the winged horse of Greek mythology that carried Zeus to Earth.
How does spyware work?
If you get a notification from your operating system saying that data has been sent to an unknown third party, you’ve encountered spyware. Strictly speaking, spyware is software that can make its way onto your device without your knowledge via an app install package, file attachment, or malicious website.
Spyware can get on your device in several ways:
- Downloading a free app that contains a virus
- Clicking on the wrong link when browsing
- Purchasing a phone or computer that already has it
Bad actors can embed spyware into devices’ firmware. This means that even if the operating system is reset to factory settings, it will be there and work. Governments or large corporations usually use this type of spyware to gain insights into their employees’ actions, but individuals can also use it to watch their significant others or employees.
Spyware can also take over your screen. For instance, it might pop up and ask if you want to accept a video call from a friend who isn’t currently online.
How to detect spyware
Spyware is a common problem for laptop and computer users and can be difficult to detect. However, there are some signs you might be infected.
- Laptop or computer slows down: If your computer has suddenly been running incredibly slow or freezing, or if any programs or apps have been acting unusually, your computer may be infected with spyware. It tends to slow down or crash computers by using processing power and memory.
- Random websites open on the browser: If you're sure that no one else has access to your computer and you notice that something looks a little off, there's no harm in looking at your web browser's history and cookies to see what nefarious sites might be lurking. Many times, these programs leave themselves logged into social media sites so that they can continue to track your habits and information, even when they aren't actively running.
You won’t find spyware in prominent places like the Apple App Store or Google Play. Instead, it can be found on less reputable app stores where developers do not take the time to check that their apps are secure.
Mobile users don't realize they're using spyware until they notice something wrong with their phone. Here are some spyware warning signs:
- The battery is rapidly draining and not lasting more than a few hours
- The screen is randomly dimming and brightening
- The phone is making odd noises even when it's not in use
- The background display changed from the normal image to a picture of a sunset, beach, or something similar
How to remove spyware
In the best-case scenario, you never have to deal with spyware. But if you're here, that likely isn't the case.
However, there are several steps you can take to minimize the damage spyware can cause.
- Look at your system and make sure it’s clean of any infections – active spyware, viruses, and other malware. If there's anything left on your system, it could create further problems down the line.
- Communicate with your financial institutions to warn them of potential fraudulent activity. This might seem like an unnecessary step, but people often only find out about a breach when they start seeing odd credit card charges or their bank account is drained completely.
- Contact law enforcement. You are legally required to report any frauds that happen in your area, so don't try to handle this on your own or ignore it. It's better to let the professionals handle it than risk losing money in the long run.
- Get yourself a robust cybersecurity program with a reputation for malware removal. This will help ensure you never have to deal with something like this again – or at least not for a long time.
If your phone falls victim to spyware infection, there are ways you can remove it. First, go to Settings, then tap Apps. Then tap the Downloaded tab. Next, find the app that doesn't belong or looks suspicious and tap Uninstall.
In case that doesn’t work, go back to the main Settings menu and tap Apps again. Then press Force Stop, followed by Uninstall Updates. Finally, go back to the Downloaded tab and uninstall all other apps that don't need to be on your phone. If these steps don't remove the malware, then factory resetting your device will remove any lingering infection.
How to protect yourself from spyware
Be careful about downloading free apps. If an app seems too good to be true, then it probably is.
Before you download an app, read reviews and ensure that other users have not complained about spam email or spam calls – a clear sign of spyware. The best way to protect yourself against spyware is to always have up-to-date spyware removal software on your computer and phone.
Attackers usually distribute spyware through malicious links and attachments in phishing emails. Be cautious when opening links and attachments in emails and social media messages from unknown or suspicious sources.
Spyware can be tough to avoid, especially if you're not really sure what it is or how it's used. Below are some steps you can take to protect yourself.
Be cautious when consenting to cookies
When you visit a new website, you’ll often encounter a pop-up asking if you want to accept cookies from the site. Cookies are tiny files that websites can drop onto your computer and track your browsing activity. This allows them to build a detailed history of where you go on the internet, what you buy, and who you talk to.
Cookies follow your movements online so that websites know who you are and can customize their content for you in the future.
Install an anti-tracking browser extension
Anti-tracking browser extensions prevent websites from tracking your activity and sharing your data without your knowledge. These extensions aren't just for people who want to protect themselves from spyware - they're also good for anyone who wants better privacy online.
You can even use anti-tracking browser extensions on public computers to keep others from collecting the information you enter into a form on a website.
Use multi-factor authentication
Multi-factor authentication uses three or more authentication methods to verify user identity. For example, you might use a password as one factor, a fingerprint as another factor, and location as a third factor. This keeps user accounts secure when user passwords get compromised due to spyware infection.
Update software
Software companies often release patches after they uncover vulnerabilities that can expose your computer to hackers or other bad actors who want to steal your information. Ensure all of your software is up-to-date with the latest security patches so that hackers can't exploit known vulnerabilities.
This will help protect you against any potential breaches or attacks that could allow third parties access to any of your sensitive information.
Spyware vs. ransomware
Spyware collects information about users without their knowledge and installs itself without their consent. Many people accidentally install spyware when they download a free program or open an email attachment.
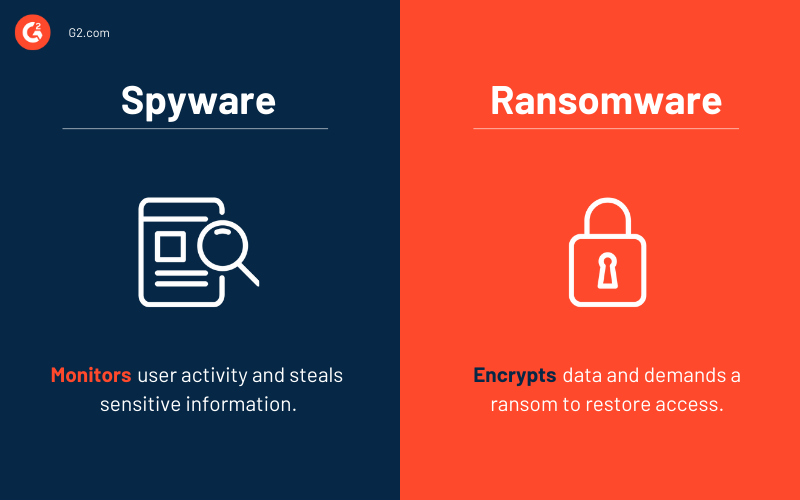
Ransomware is also installed without the users' knowledge, but it encrypts your files and locks them. This means you can't get access to them unless you pay the hackers a ransom, which is usually a few hundred or thousand dollars, depending on the severity of the attack. Sometimes the ransom is much steeper – some hackers even ask for millions of dollars.
Don’t let it spy with its little eye
Spyware is dangerous for consumers' privacy but even worse for businesses. Spyware can steal a company's precious information and rob them of its competitive advantage.
The best way to avoid this problem is to follow reputable sites when downloading software. Only install programs that professional review sites have thoroughly examined, and always read the terms of service when installing applications.
Learn more about malware removal to maintain a robust security posture.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.