Modern businesses understand the value of data and its security.
They’re devoted to creating secure software and web applications. Many organizations train developers to write secure code and spread awareness about data security. But vulnerabilities still appear.
Despite developing secure applications, errors occur. Such errors or security gaps cause high-impact data breaches, undermining business reputation with sizable financial losses.
Regardless, you can’t blame developers for these vulnerabilities and gaps. They have a lot on their plates with urgent releases and other priorities and can make potential mistakes. To identify and avoid security breaches, you need to test applications. It’s better to do this early in the software development lifecycle (SDLC) using Static Application Security Testing (SAST) software. It helps detect vulnerabilities in the source code and allows developers to remediate them early.
What is SAST?
Static Application Security Testing (SAST) methodology analyzes an application’s source code to spot vulnerabilities. It’s conducted in the early stages of the software development lifecycle, allowing developers to mitigate security risks in the code.
SAST doesn’t require a fully-functional application to test. It provides a cost-effective way to fix issues and gives real-time feedback to developers, helping them mitigate vulnerabilities before moving on to the next stage in SDLC.
SAST is a white box security testing method that makes the framework, files, and source code available and accessible. It examines the source code to find vulnerabilities like SQL injection and other Open Web Application Security Project (OWASP) top ten vulnerabilities.
Why is SAST important?
SAST examines source code, files, and the underlying framework with the highest precision. These scans are configured based on a predetermined set of rules to find and fix errors in the code.
SAST tools pinpoint the exact vulnerable line or file, making it easy for software developers to fix these vulnerabilities. These tools also offer a brief description of the issue and a measure of its severity. SAST software scales well as businesses grow and allows the team to eventually save money.
Pinpointing the exact location of error may not be a big deal, but from a developer’s perspective, it saves a lot of time. Developers spend time finding the exact location of the issue, and SAST tools empower them with quick and easy detection. It helps businesses scale and secure sensitive data against cyber attacks, and automate checks to identify security weaknesses.
Want to learn more about Static Application Security Testing (SAST) Software? Explore Static Application Security Testing (SAST) products.
SAST vs. DAST
It’s a dilemma for organizations to choose a method for application security testing, whether SAST or DAST. Simply put, SAST and dynamic application security testing (DAST) provide better security when paired together. Both have their unique purposes and use cases.
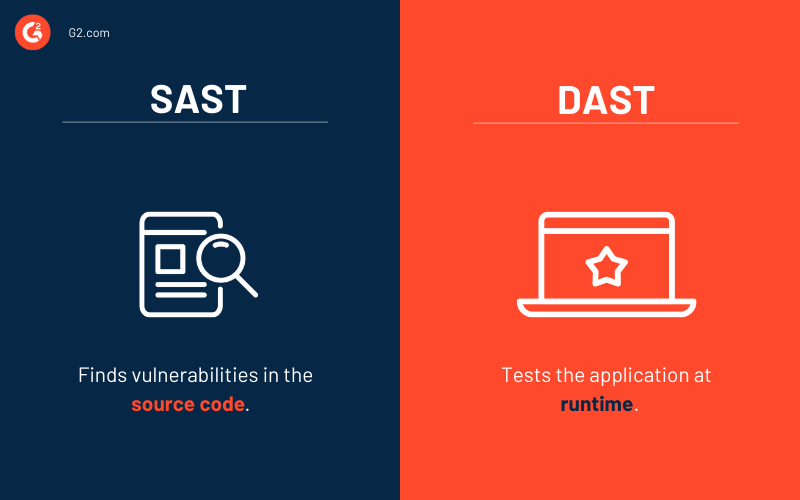
Dynamic application security testing (DAST) tests the application at runtime. It’s a black-box testing method that examines the program to identify ways malicious hackers could exploit it.
DAST needs a functional application to perform security testing. It resembles a real-world hacking attempt and is comparatively expensive as remediating a vulnerability found during DAST requires software developers to reassess the application.
Top 5 DAST tools include:
*These are the five leading dynamic application security testing software from G2’s Fall 2021 Grid® Report.
Both SAST and DAST help ensure application security. Challenges posed by one are often addressed by the other.
Key differences between SAST and DAST
The differences in SAST and DAST determine the most favorable approach depending on the situation and environment. Organizations generally adopt both for comprehensive security testing.
|
Area of difference |
SAST |
DAST |
|
Prerequisites |
Requires source code and analyzes it to detect vulnerabilities. |
Requires a fully-functional application to detect and remediate vulnerabilities. |
|
Time |
Helps stakeholders identify vulnerabilities in the early stages of software development. |
Finds vulnerabilities after the software development lifecycle is complete. |
|
Cost |
Is less expensive since vulnerabilities are detected in the early stages of SDLC before the application goes into QA. |
Is more expensive since vulnerabilities are detected at the end of SDLC, and remediation gets pushed. |
|
Detection |
Can’t find run-time issues since it analyzes the source code. |
Can detect run-time issues as it analyzes a fully-functioning application. |
|
Compatibility |
Supports web applications, services, and thick clients. |
Doesn’t support other software types. |
|
Approach |
Follows white box security testing (developer approach) that tests the application inside out. |
Follows black-box security testing (hacker approach) that tests the application outside in. |
SAST challenges
Businesses may face some challenges while adopting SAST or DAST. These inform the stakeholders of the most appropriate approach based on their unique use case.
SAST relies on static source code to detect vulnerabilities. It can identify certain vulnerabilities but turn a blind eye to other issues that can be exploited during run time.
SAST can sometimes produce ambiguous results based on predefined rules. This may contribute to a false positive or negative error.
Benefits of using SAST and DAST together
SAST and DAST together provide enhanced security and a range of benefits. SAST tools scan each line of the source code to detect vulnerabilities. They determine the exact location of the issue and help developers easily find and remediate the weak spots.
DAST, on the other hand, handles complex parts of application security. DAST tools scan interconnected elements outside source code during run time to spot vulnerabilities. This helps DevOps teams know about misconfigurations in an application’s environment and threats outside the code. DAST complements SAST with an external application framework, effective for comprehensive application security.
How to choose a SAST tool
Consider various parameters while selecting a SAST software best suited for your needs. When comparing SAST software, you can use a selection criterion that includes:
- Compatibility: Check whether the SAST tool supports your programming language and the underlying framework in software development.
- Detection: Make sure the SAST software finds at least the OWASP top 10 vulnerabilities mentioned above.
- Accuracy: Measure the rate of false positives and negatives to determine the accuracy of the SAST tool you’re considering.
- Integration: Verify that the SAST tool works fine with an integrated development environment (IDE) and other tools in your DevOps pipeline.
- Scalability: Ensure the SAST program scales for larger projects and supports more developers in the future.
Moreover, check if the tool you’re considering is easy to set up, use, and fits your budget. You can read software reviews submitted by actual users on G2 to further inform your purchasing decision.
Static Application Security Testing software
Static Application Security Testing (SAST) software analyzes an application’s source code and allows developers to remediate vulnerabilities without executing the code, helping them fix issues before deployment.
To qualify for inclusion in the Static Application Security Testing (SAST) category, a product must:
- Identify vulnerabilities by testing applications
- Run static test without executing the code
- Detect relative exploits and vulnerabilities
*These are the five leading Static Application Security Testing software from G2’s Fall 2021 Grid® Report.
1. GitHub
GitHub is a popular software development and internet hosting platform among developers. It helps detect the source code vulnerabilities and enables developers to fix them early.
What users like:
“The good thing is it works on Windows, Linux, Mac, etc. It provides a free trial, code permission, debugging tool, bug tracking, code security, milestone tracking, version control, and much more. It provides support for almost all popular languages. It is an open-source project, and even large enterprises use it. Its ability to commit and collaborate on the code is very easy and provides fast output.”
- GitHub Review, Ankit S.
What users dislike:
“Since the projects do not have online compilation features, it is not possible to know whether the wrong source code was sent or not without downloading the source codes and trying them.”
- GitHub Review, Şükrü O.
2. GitLab
GitLab is a DevOps platform that combines developing, securing, and operating software in a single application. It helps reduce development process costs, improve cycle time from weeks to minutes, and decrease time to market while enhancing developer productivity.
What users like:
“GitLab is an excellent medium for cloning a repository on a web portal. You can create any number of project repositories here and control its permissions. The tool serves as an excellent DevOps platform and provides the ability to upload a snippet immediately. The uploaded file (s) can be accessed by any number of individuals within the team and could be modified if needed. GitLab also contains the option to raise and track issues. The CI/CD feature provides features and pipelines, editors, jobs, and schedules to automate the integrations.”
- GitLab Review, Giridhar P.
What users dislike:
“Suppose we are merging a feature branch to develop. And many members of the Team had contributed their code in the particular feature branch. During the merge and review phase, we can see the changes between the two branches. It would be great if we can see the name of the person as well when we hover over the changes which are highlighted in the green color. It does help if we are reviewing as a team. We can clarify the changes at that moment instead of going back and looking at who added the changes in which commit.”
- GitLab Review, Debnita G.
3. Coverity
Coverity provides broad security and quality audits for many languages, frameworks, and commonly used infrastructure as code platforms and file formats. It seamlessly integrates automated security testing into your continuous integration and deployment (CI/CD) pipelines and supports your existing development tools and workflows.
What users like:
“Being able to cluster the Coverity server was very helpful. We had 3 development centers around the world, and with clustering, we were able to lessen the impact on the remote developers as well as consolidate the issue ids. This allowed us to have centralized reporting regarding the status of projects.”
- Coverity Review, Matt B.
What users dislike:
“This is compiler-level analysis, so for 50 million lines of code it takes time. The results are worth it.”
- Coverity Review, Glenn D.
4. Snyk
Snyk automatically finds and fixes vulnerabilities in your code, open-source dependencies, containers, and infrastructure as code. It supports many programming languages and effortlessly integrates with your tools, pipelines, and workflows.
What users like:
“Snyk is invaluable for scanning freshly baked and older images for vulnerabilities. When you think a newly installed app has got you covered: think again. Snyk will find those log time still unpatched vulnerabilities in apps and libraries that your distro won't or hasn't found out yet.”
- Snyk Review, Aryan B.
What users dislike:
“The way the different projects are grouped and presented in the UI could be improved (especially if you have a lot of them and are using multiple features, it can get confusing quickly). It can also be troublesome to find how to use a specific feature, as the documentation is often hard to navigate.”
- Snyk Review, Jean-Alexandre B.
5. Appknox
Appknox is an automated mobile application security solution that helps businesses and developers detect and resolve security issues. It offers flexible deployment models and a variety of engagement approaches that crystallize your security requirements.
What users like:
“The team took care of all our needs for web, mobile web, and native apps. Furthermore, not many companies out there can do scans and pen tests for SDKs. Appknox does it all. From the initial scan to the mitigation approaches and re-scan, they are a one-stop-shop. They also help answer any follow-ups from folks who request more details. This has been very valuable to us.”
- Appknox Review, Amod S.
What users dislike:
“We haven't had any reason for any complaint so far. They are super proactive and always open to feedback.”
- Appknox Review, Piyush R.
Develop secure applications
SAST helps you find source code vulnerabilities in the early stages of SDLC, allowing you to fix them at a lower cost. You can leverage the automation capabilities of SAST tools for a robust vulnerability detection process and develop clean and secure programs.
Learn more about DAST software and how you can use it with SAST tools to develop and deploy secure applications.

Sagar Joshi
Sagar Joshi is a former content marketing specialist at G2 in India. He is an engineer with a keen interest in data analytics and cybersecurity. He writes about topics related to them. You can find him reading books, learning a new language, or playing pool in his free time.