As a network administrator undertaking a new project, you know that confusing forward and reverse proxies can lead to suboptimal network configurations.
While both proxy networks sit in the middle of network traffic, their roles are distinct and essential in different contexts.
Forward proxy vs. reverse proxy
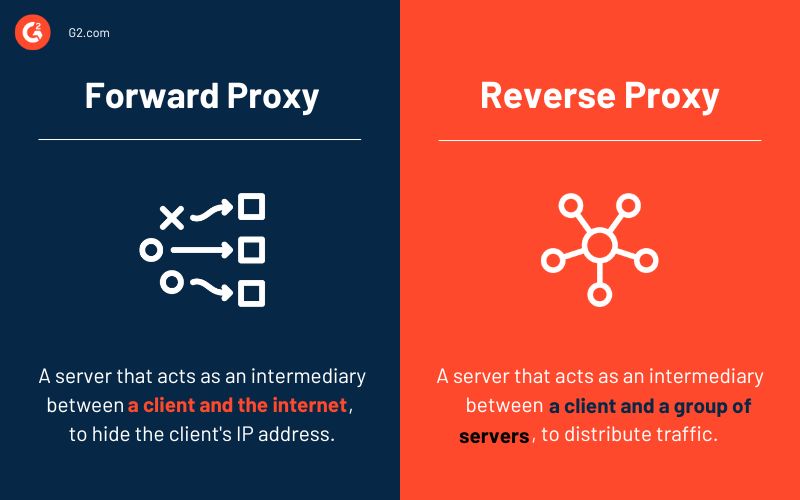
A forward proxy focuses on the client side, regulating access and enhancing security within a network. In contrast, a reverse proxy acts on behalf of servers, managing external requests and providing additional security benefits.
Let's clear up the confusion by dissecting the key differences between forward and reverse proxies.
We'll explore their functionalities, delve into their performance and security benefits, and help you determine the best choice for specific network scenarios. You'll be well-versed in proxy deployment, ensuring your internal network runs smoothly and securely.
What is a forward proxy?
Imagine you are using a web browser to request information from a website. In the traditional model, your request travels directly to the server, which processes it and returns the information to you. With a forward proxy, the process is slightly different.
You, using your web browser, make a request to access a website. The forward proxy server intercepts this request and evaluates it based on pre-set rules, which could involve cybersecurity checks or access control lists.
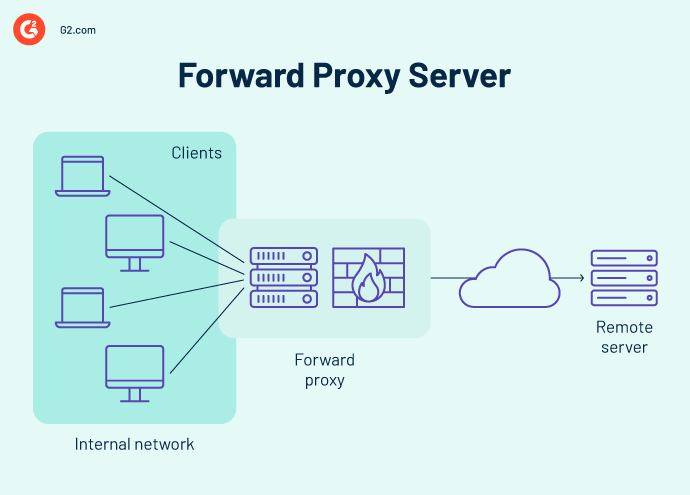
If the request is allowed, the proxy forwards it to the website server using its IP address. The website server processes the request and sends its response back to the proxy server.
The proxy receives the response from the server. It may perform additional actions, such as filtering content or caching frequently accessed data. Finally, the proxy forwards the response back to your device, allowing you to see the website content.
Common use cases of forward proxies
- Caching and content filtering
- Anonymizing web requests
- Bypassing geo-restrictions and network blocks
- Monitoring and controlling internet usage
Want to learn more about Proxy Network Software? Explore Proxy Networks products.
What is a reverse proxy?
In the traditional client-server model, you directly request information from a web server. A reverse proxy changes this dynamic as an intermediary server positioned before one or more web servers.
The reverse proxy sits at the network perimeter, intercepting all incoming requests from clients attempting to access web content. The proxy can implement security measures such as authentication and request filtering based on pre-set rules before forwarding the requests.
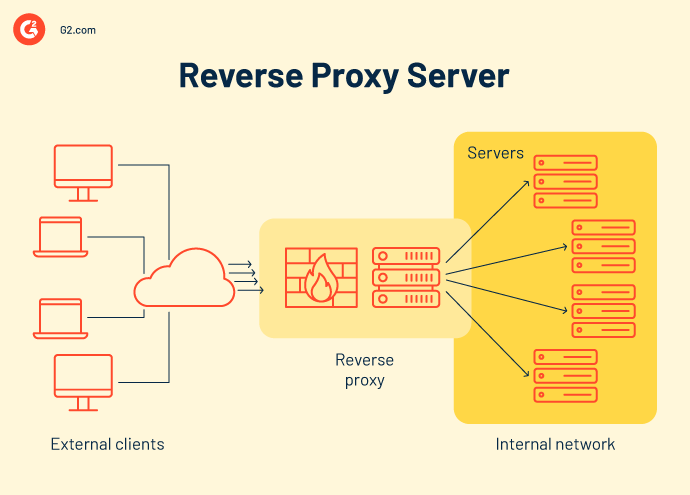
With different reverse proxy servers behind the proxy, it can efficiently distribute incoming requests across these reverse proxy servers based on factors like workload or server specialization. This helps optimize performance and prevent any single server from becoming overloaded. The reverse proxy can cache frequently accessed content, reducing the server load on the origin servers and improving client response times by serving cached content directly.
After performing these potential actions, the reverse proxy forwards the validated request to the most appropriate server behind it. The web server processes the request and generates the response (webpage content), which is then sent back to the reverse proxy.
Finally, the reverse proxy receives the response from the web server and delivers it back to the original client. The client interacts with the website content, unaware of the reverse proxy's involvement.
Common use cases of reverse proxies
- Load balancing
- SSL termination
- Web acceleration (caching static content)
- Protection against distributed denial-of-service (DDoS) attacks.
- Application firewall and security enhancement
- API gateway integration
Differences between a forward proxy and a reverse proxy
Understanding the difference between the two types of proxies is crucial for optimizing network security.
1. Direction of proxying
A forward proxy acts as a middleman between client devices, such as computers and phones, and the internet. Clients direct their requests to the proxy, which then forwards them to the intended server and returns the server's response to the clients.
In contrast, a reverse proxy intervenes when a client requests access to web content. The client communicates with the reverse proxy, oblivious to the actual web server managing the request. The reverse proxy directs the request to the correct server, fetches the response, and returns it to the client.
2. Purpose and functionality
A forward proxy primarily filters content, blocks potentially harmful or unauthorized websites, and enforces access control policies. By anonymizing browsing activities by masking client IP addresses, a forward proxy enhances user privacy.
Note: Forward proxies and virtual private networks (VPN) can be confusing because they mask your IP address. However, they differ significantly in how they achieve this and the level of security they provide.
In contrast, a reverse proxy manages incoming traffic by distributing it across multiple web servers, enhancing responsiveness. It can also handle encryption and decryption tasks, reducing the workload on web servers and ensuring secure communication channels.
3. Placement in the network
A forward proxy is positioned between client devices and a network's internet gateway. It serves as an intermediary that handles client requests before they reach the internet, allowing it to filter content, enforce access controls, and anonymize client IP addresses.
On the other hand, a reverse proxy is placed in front of web servers within a network. It acts as the primary interface for incoming client requests, directing traffic to the appropriate backend servers based on various factors such as load-balancing algorithms or content-specific routing rules.
4. Network topology
A forward proxy is typically configured in two main ways:
- Explicit proxy: When configured as an explicit proxy, each client device must be manually set up to connect to the proxy server directly. In this setup, the client specifies the proxy server's address and port in its network settings. The explicit proxy server then handles all requests and responses between the client and the internet. This method provides more granular control over proxy usage and allows for specific configurations on each client device.
- Transparent proxy: In a transparent proxy setup, the proxy server is integrated into the network infrastructure between the clients and the internet gateway. It automatically intercepts all outgoing client requests without configuring individual client devices. The transparent proxy operates seamlessly in the background, applying security and content filtering policies uniformly across all devices within the network. This centralized approach simplifies management tasks and ensures consistent application of proxy policies without relying on client-side configurations.
In contrast, a reverse proxy is often implemented within a web server or a content delivery network (CDN) software. In a CDN environment, reverse proxies are strategically placed at various locations globally to cache content closer to end users, thereby reducing latency and improving access speeds.
5. Configuration complexity
A forward proxy's setup is straightforward for basic needs such as filtering or anonymization, often requiring just a few settings changes on client devices or the proxy server itself.
However, more complex configurations are necessary when implementing advanced traffic filtering rules, detailed access control lists, and comprehensive security measures.
These configurations might involve specifying which websites or types of content are accessible, setting up authentication requirements, and integrating with other security system designs to monitor and manage internet usage.
On the other hand, a reverse proxy typically involves a more complex setup. Configuring a reverse proxy requires careful planning and implementation of load balancing strategies to evenly distribute incoming traffic across multiple servers.
Additionally, security policies must be established to protect backend servers from direct attacks, including setting up firewalls, TLS/SSL encryption, and other security protocols. Content caching rules must also be defined to improve response times and reduce the load on origin servers by serving frequently accessed content directly from the proxy.
The overall complexity of configuring a reverse proxy increases with the desired functionality, especially in environments requiring high availability, robust security, and efficient content delivery.
6. Impact on performance
A forward proxy can introduce latency, especially if the proxy server is overloaded or far from the client. This delay occurs because all client requests must pass through the proxy before reaching the destination server.
However, forward proxies can also improve performance through caching. By storing copies of frequently accessed content, a forward proxy can quickly serve these cached resources to clients, reducing the need to repeatedly fetch the same data from the internet and thus speeding up response times.
In contrast, a reverse proxy can significantly enhance website responsiveness when properly configured. It reduces the load on the origin servers by caching static content. Clients receive cached responses faster than fetching fresh data from the server, leading to improved overall performance and quicker page load times.
7. Protection against threats
Forward proxies enhance user security by filtering out malicious content and blocking access to potentially harmful websites. These measures protect users from malware infections and phishing attempts.
On the other hand, reverse proxies play a crucial role in protecting web servers from external network threats. By sitting in front of backend servers, reverse proxies act as a protective shield against DDoS attack. They achieve this by hiding the identities of the actual servers handling requests, thereby making it harder for attackers to target and exploit vulnerabilities in the backend infrastructure directly.
Where forward and reverse proxies overlap
Forward and reverse proxies share several key functionalities that enhance security and network management.
Both types of proxies can act as gatekeepers, filtering traffic based on file size and type, allowing only authorized files to pass through. They also enforce access controls, such as restricting access based on user permissions or IP addresses. Additionally, they support port and protocol switching, which helps to obscure access patterns and strengthen security.
Furthermore, the same software can be configured to operate as either a forward or reverse proxy. For instance, widely used servers like Nginx and Apache are frequently deployed as reverse proxies in enterprise setups, yet they are versatile enough to function as forward proxies when configured accordingly
Choosing the right proxy for your needs
Before diving into the specifics, it's crucial to understand what functionality you require.
Imagine you have a remote workforce scattered globally. Due to their physical location, accessing geo-restricted content or company resources can be slow. Here, a forward proxy shines. Placed between your users and the internet, it routes their requests, potentially through a server closer to the target destination. This reduces latency and improves loading times.
In a different scenario, let's say you run a popular e-commerce website. During peak hours, a surge in traffic can overwhelm your web server, causing crashes and frustrating customers. A reverse proxy distributes incoming traffic requests across multiple web servers. This ensures smooth operation and prevents downtime.
Ask yourself:
- What is your purpose for using a proxy? (Anonymity, bypassing geo-restrictions, data scraping, website security, etc.)
- How important is security for your application? (Need for encryption?)
- What level of speed and performance do you require? (Important for tasks like video streaming or real-time gaming)
- Do you need to access content from specific locations or send requests with specific IPs?
Another factor to consider here is cost. Free proxies often have limitations like slow speeds, unreliable connections, and data caps. Paid proxies typically offer better performance, security, and features.
If you just need to unblock a website occasionally and security isn't a major concern, a free proxy might suffice. However, be prepared for slow speeds and potential security risks.
On the other hand, paid proxies are essential for tasks like web scraping, data collection, or streaming video content where speed and reliability are crucial. When dealing with sensitive data or needing consistent performance, paid proxies are a no-brainer.
Once you've made your decision, do your research and compare providers based on features, pricing, and reputation.
Best proxy network software 2024
Whether deploying forward or reverse proxies, choosing the right software is essential to optimize proxy network performance. The top picks for 2025 are:
*These are the five leading proxy network software solutions from G2's Fall 2024 Grid® Report.
Rewriting the rules of online privacy
Forward proxies protect clients accessing the internet by providing security and privacy. Meanwhile, reverse proxies enhance server security and performance. Understanding their roles helps build a robust network architecture that effectively safeguards its users and data.
Forward and reverse proxies work together effectively in network traffic management. As internet threats evolve and user demands increase, these adaptable tools can combine to create a secure and efficient network infrastructure ready to face future challenges.
For an extra layer of defense, consider implementing web application firewalls (WAFs).

Devyani Mehta
Devyani Mehta is a content marketing specialist at G2. She has worked with several SaaS startups in India, which has helped her gain diverse industry experience. At G2, she shares her insights on complex cybersecurity concepts like web application firewalls, RASP, and SSPM. Outside work, she enjoys traveling, cafe hopping, and volunteering in the education sector. Connect with her on LinkedIn.