Sherlock once said, “It is a capital mistake to theorize before one has data.”
There is no denying that data powers everything we do. It’s a company’s most valuable asset – without it, there could be severe consequences. Any mishandled data could result in loss, theft, or privacy breaches. As a result, companies adapt data lifecycle management (DLM) to secure data from creation to destruction.
Destruction is as important to a business’s data lifecycle management as backup and recovery. Sometimes a business has to securely dispose of its data due to legal or contractual obligations. Data destruction software offers multiple methods to permanently delete information.
What is data lifecycle management?
Data lifecycle management enhances data security and privacy as it moves through the different phases of an IT system, from initial entry to deletion. An efficient DLM system provides structure to an organization’s database and makes it more secure and accessible to those who need it.
By adopting DLM, businesses protect themselves against malicious attacks. DLM supports business growth by providing benefits like risk management, business knowledge, and strategic decision-making.
In a data lifecycle, data is sorted into different phases based on specific criteria and moved along each stage when it fulfills its requirement. The right data will always be available in the right place and at the right time.
Why is data lifecycle management important?
As more and more organizations become data-driven, they need to understand how to manage it securely and productively. The ultimate goal of data management is to retrieve information and turn that information into insights that improve business.
DLM helps organizations maximize the benefits of the data they acquire or generate. Once businesses define how their data is collected, stored, and shared, they defend themselves from potential data breaches and misuse. The input goes through different types of data processing, such as data encryption and transformation, to safeguard the business.
By taking care of data correctly, businesses improve their services by streamlining workflows.
Want to learn more about Data Destruction Software? Explore Data Destruction products.
Data lifecycle management: a brief history
Over the years, the volume of data and the technology for managing data have grown almost parallelly across industries. Storage solutions are much more flexible and less expensive now, with cloud storage reaching limitlessness. But back in the day, things were drastically different.
Companies had to be far more focused on data lifecycles because of limitations on different storage methods. There weren’t many flexible or expanded storage options.
The practice of data management came into existence in the 1980s when random access memory (RAM) was introduced. The invention allowed businesses to segue from mechanical punch cards and magnetic tape storage to databases. The constraints on previous storage methods like hard drives were also lifted.
With machine learning and artificial intelligence, companies have grown increasingly efficient at collecting and analyzing user data. They now have the power to design superior customer experiences, make data-driven decisions, and simplify business processes.
Since companies are creating and working with more and more data, they understand the intention and perks of big data analysis. It has transformed how DLM strategies are developed and targeted in the present landscape.
But with larger data sets, the need for DLM has also become dire as it effectively enhances data security for businesses of all sizes.
What are the three goals of data lifecycle management?
As large volumes of data pour in from every direction, modern businesses need ways to manage it better than ever. Moreover, this data must be handled in a manner that adheres to several regulations while keeping user safety in mind.
The main goals of data lifecycle management are:
- Data security. As mentioned, DLM aims to secure data by creating protocols for every stage it passes through in its lifecycle. DLM prevents unauthorized users from accessing confidential files in your database and creates protection against malware attacks. Your company might benefit from one of these five malware removal tools that keep you safe.
- Data integrity. Your DLM model must retain the original form of all data and track changes to ensure the stored data is reliable and accurate. Plus, the key decision-makers must have full visibility of all versions of this data.
- Data availability. As important as protecting data is, it’s equally necessary to ensure that data is accessible to the right users at the right time without disruptions in the daily workflow.
Data lifecycle management vs. information lifecycle management
Often used interchangeably, data lifecycle management and information lifecycle management (ILM) are not the same concepts.
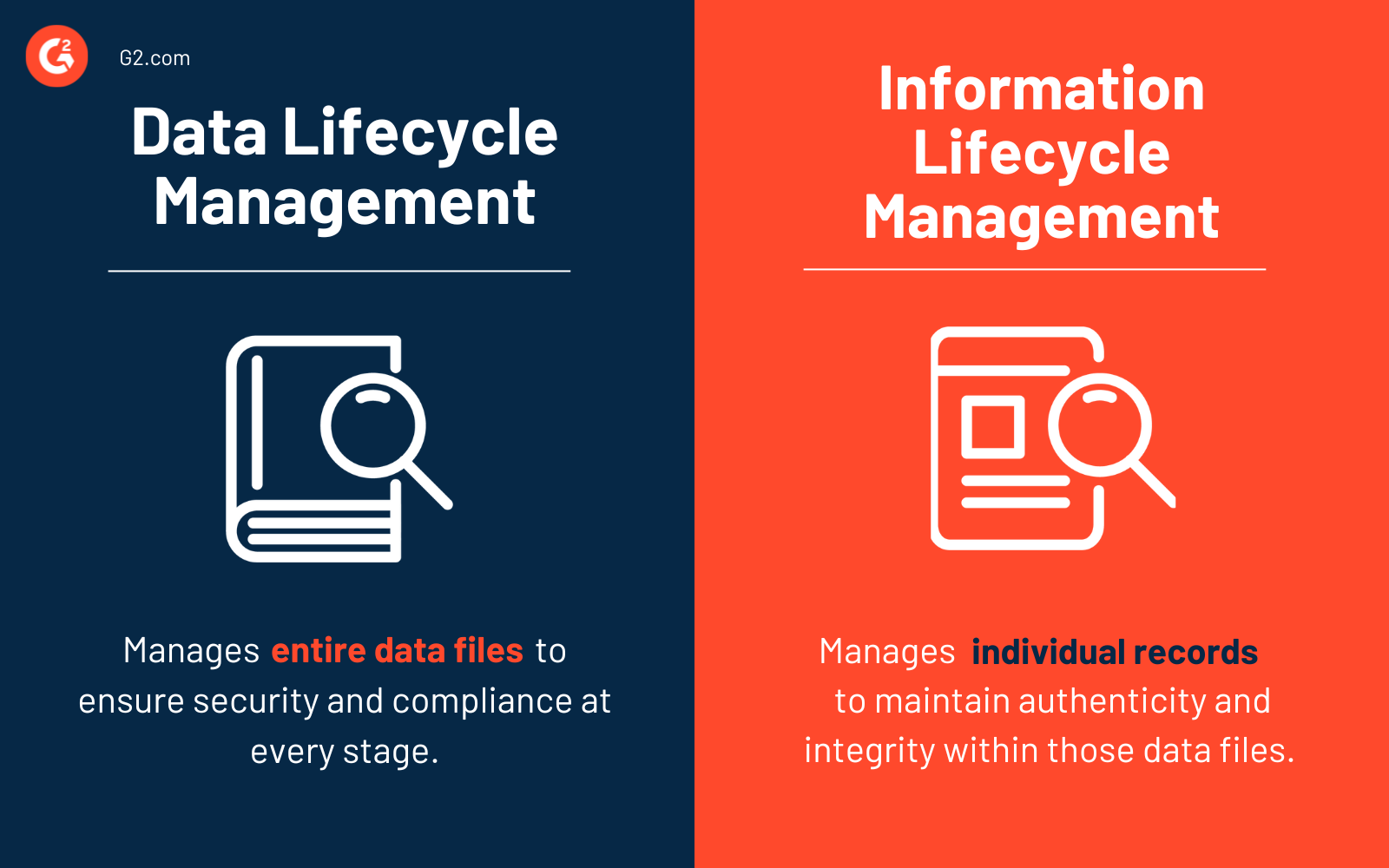
While they are both crucial in determining an organization’s data protection strategy, DLM focuses on the bigger picture, and ILM concentrates on individual pieces of data within a system.
| Attribute | DLM | ILM |
| Type of data | Manages structured and unstructured data | Manages information stemming from organized and structured databases |
| Function | Monitors the movement of data within an organization from creation to deletion | Checks the accuracy and relevance of derived information from data sets |
| Target | Focuses on the privacy and security of complete data files | Focuses on the authenticity and integrity of individual records within complete data files |
| Data journey | Disregards obsolete data and optimizes storage for new files | Archives redundant information and authenticates useful records |
Despite the differences, DLM and ILM are complementary to each other. Without powerful data management solutions, you can’t have an effective information lifecycle management strategy.
What are the five stages of data lifecycle management?
The data lifecycle management framework comprises the different stages of the data in its lifespan. While every business has a distinct way of managing data (depending on the work model and software stack), there are generally five stages in a DLM model.
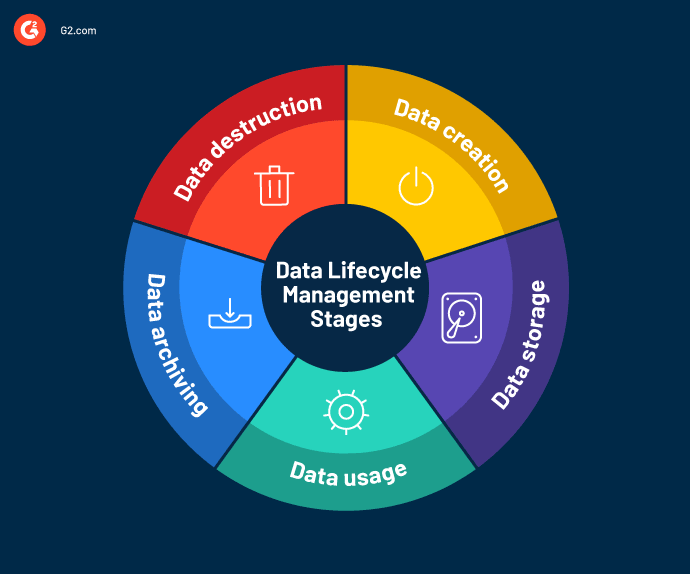
Data creation
The first phase of DLM involves creating and collecting data. Data is manually entered or acquired from an existing source like email, contact form, or website. It can take any form, from images and Word documents to PDF files and structured query language (SQL) databases. However, the addition of new data should be evaluated for both quality and business relevance.
In this stage, it’s advisable to standardize the data input format so it’s accessible and manageable for everyone. Establish rules determining the initial categorization of your records, making it easier to process that data in further stages. Also, always adhere to data privacy regulations when collecting personal data.
Data storage
The second stage concerns protecting and processing data in a manner that aligns with its sensitivity and importance. Modern businesses using cloud servers tend to adopt cloud storage security solutions for flexibility and speed. Structured and unstructured data sets are processed differently.
Once the storage requirements are identified, a business can choose the infrastructure needed to encrypt and reserve sensitive data while ensuring it follows all privacy regulations and policies. This stage also focuses on data redundancy and recovery to maintain a sufficient backup system during emergencies.
Data usage
The stored data is then used, classified, and shared by the organization. This is often considered the most sensitive phase of DLM because the stored data is available to different sets of users. Plan to have an audit system to track all changes to your database.
Since the main goal at this phase is data sharing, you must ensure it’s in the right place and available to all authorized personnel. This requirement is either internal or external, depending on how you use your stored data.
Data archiving
After a certain period, some of your stored data might not be useful. It makes sense to archive it and mark it unnecessary for maintenance or ongoing business operations. Archiving data optimizes your storage system for long-term benefit, ensuring you have access to preserved information in the future.
In addition, data archiving also prevents mishandling of business data and provides the functionality of restoring data for active users when needed.
Data destruction
As powerful as data is, dysfunctional data exposes your business to many risks. So the final stage in DLM, data destruction (also known as data purging), is all about deleting data that no longer serves any purpose, now or in the foreseeable future.
In this stage, companies usually target archived data and figure out methods to dispose of it securely. Most companies use data destruction software to ensure that the deleted data cannot be recovered by any other tool. The destruction process must ensure compliance with data protection regulations.
Hierarchical storage management: choosing the right tier for your data
Cloud access has revolutionized data, but with unlimited storage comes unlimited responsibility. It’s tricky to decide where your data goes.
The concept of hierarchical storage management (HSM) tackles this dilemma flawlessly. HSM works as part of the data archive and backup policy. It minimizes the overall data storage cost by monitoring how a company uses its data and automatically moving it between high-cost and low-cost storage devices.
HSM systems sort company data into three tiers: hot, warm, and cold.
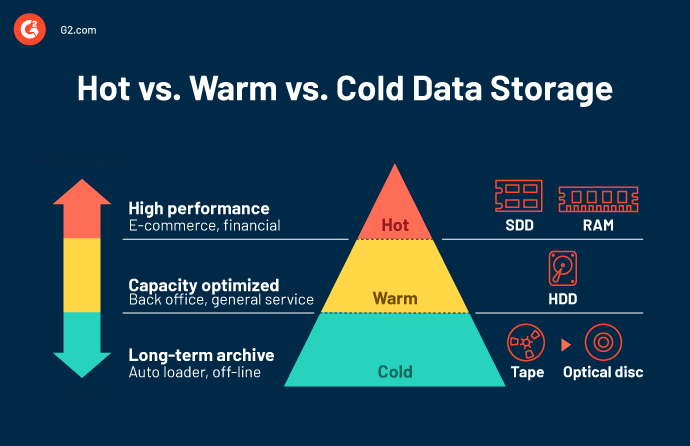
- Hot storage: Data that needs frequent employee access comes under this category. Because of active usage, access to this data set must be quick and frictionless.
- Warm storage: Data that needs less frequent access resides in warm storage. Since it’s not used as actively as hot data, it’s stored at a slightly slower capacity.
- Cold storage: Any data employees rarely use qualifies as cold storage. It includes archived data sets moved to less costly storage located on-premise for compliance purposes.
Data lifecycle management benefits
The benefits of a good data lifecycle management model are many. Aside from saving a company's time and resources, creating a DLM model also results in:
- Improved processes. DLM focuses on maintaining data quality and integrity throughout each stage. This not only fuels overall efficiency but also improves the process by ensuring that businesses maximize the value of their data through increased accuracy and reliability.
- Enhanced security. Data security is the top concern for most entrepreneurs and business leaders. DLM supports organizations as they define how their data is used, stored, and shared, making it the perfect solution to minimize the risk of data breaches and misuse.
- Compliance with regulations. Data retention comes with a set of stringent rules regarding personal data and organizational records. Businesses that set up a solid DLM model handle data with enhanced information security and efficiency, enabling them to stay compliant.
- Higher data accessibility. Since businesses depend highly on data availability for their daily operations, DLM makes data constantly available to authorized users. IT teams tag data as and when created and track it across stages to improve accessibility for all users.
- Cost efficiency. DLM opens up sustainable options for data that might not be useful to an organization. For instance, it can be moved to a less costly storage location or deleted/archived securely to remove maintenance costs.
Data lifecycle management challenges
Just like any other business process, DLM also comes with its unique set of challenges. These include:
- Extracting value. Many companies struggle to simplify big data numbers, failing to identify how they can productively add value to their operations. Understanding big data analytics is crucial for generating actionable insights and getting the most worth out of collected data sets.
- Maintaining consistency. IT teams collect data from multiple sources (both internal and external), making uniformity difficult. Data analysis also becomes a challenge when businesses juggle multiple formats. Therefore, data has to be decrypted into the same format to overcome such issues.
- Simplifying data retrieval. Data retrieval has to be a fairly simple yet authenticated process. But with an overload of data volume, stakeholders might feel lost when figuring out how and where to access files.
Best practices for data lifecycle management
To make the most of the data lifecycle management process, try out these best practices when designing your model.
- Create a centralized repository. It serves as a resource pool for all required data and processes, so users have the means to import information easily. Plus, having a centralized system saves time and adds to operational efficiency.
- Standardize your data model. Data standardization ensures that employees tap into the right data format for their cross-functional uses. It also drives agility, which leads to more informed business decisions.
- Follow data governance. You must follow complex data privacy regulations when managing sensitive data, internally or externally. Compliance with these policies keeps your data organized and protects you from potential legal issues and data attacks.
- Implement a recovery plan. The higher the volume of data, the bigger the risk of data loss or malfunction. Prepare for emergencies by setting up an effective disaster recovery plan. Invest in a reliable database backup solution and eliminate the risk of permanent damage.
- Share your DLM policy. Ensure everyone in the company is on the same page. Defining guidelines speeds up the implementation of the new process and keeps everyone on track with compliance.
- Install automation solutions. Since DLM is vital to daily business, its functions are most effective when easily managed and repeated. And this is only achievable by deploying automation solutions that organize data into different tiers based on the outlined criteria.
In data, we trust.
A functional framework based on DLM shows you your data flow and keeps it secure while you comply with privacy regulations. You have to be able to record, track, and analyze all of your information because as your business grows, so does your data.
Ready to safeguard your company data? Take a look at the best data privacy management software to get comprehensive solutions for handling your privacy policy.

Washija Kazim
Washija Kazim is a Sr. Content Marketing Specialist at G2 focused on creating actionable SaaS content for IT management and infrastructure needs. With a professional degree in business administration, she specializes in subjects like business logic, impact analysis, data lifecycle management, and cryptocurrency. In her spare time, she can be found buried nose-deep in a book, lost in her favorite cinematic world, or planning her next trip to the mountains.
