Ever wondered where all your emails, social media posts, photos, or even the Netflix movie you're watching are stored? The simple answer is the cloud.
Today, we store everything on the cloud, from personal files to critical enterprise business data. The email you just checked now? That tweet you posted this morning? The playlist your bestie sent you? They’re all in the cloud. As data grows exponentially, cloud storage usage is also expanding. Businesses are quickly adopting multiple cloud storage and hybrid cloud storage for the speed, scale, and flexibility they offer.
But the rapid cloud storage adoption also opens pandora’s box of securing the data on the cloud. A G2 survey found that nearly a quarter of hybrid cloud storage users consider security a major pain point. Misconfigurations, data loss, and regulatory compliance, the list of security challenges is long and evolving.
24%
consider security, compliance, and DDoS prevention as major pain points of hybrid cloud storage
Source: G2 Survey
Companies are looking for additional help through cloud security software as new threats proliferate cloud storage.
What is cloud storage security?
Cloud storage security includes a set of policies, technologies, tools, and practices to protect data stored in cloud storage systems from leaks, cyberattacks, unauthorized access, and other threats.
Cloud storage security is fundamental for cloud data protection that includes data accessibility, data privacy, and data integrity. Protecting cloud storage involves fortifying cloud storage infrastructure, shielding networks, and endpoints, securing cloud data in rest and motion, and monitoring for vulnerabilities and risks.
But before we dive into the evolving cloud storage risks and how to mitigate them, let’s take a look at the basics of cloud storage. This is important because some cloud storage vulnerabilities stem from some of its best features.
Want to learn more about Cloud Security Software? Explore Cloud Security products.
What is secure cloud storage?
Cloud storage is a cloud computing service model where digital data is stored, managed, and backed up across multiple remote servers of a cloud provider that can be accessed through the internet or private network.
How does cloud storage work?
Businesses buy cloud storage from third-party vendors who own and operate data centers with massive servers in offsite locations. The cloud storage provider hosts, maintains, and manages data centers and makes data accessible to companies through the internet.
There are three types of cloud storage models: public, private, and hybrid.
Public cloud storage: This cloud storage is hosted and managed by third-party cloud storage providers who share the storage resources with multiple customers. Google Cloud, Amazon Web Services, Microsoft Azure, and IBM Cloud are some of the popular public cloud storage providers.
Private cloud storage: This type of cloud storage service is owned, hosted, and operated by an organization or bought from an external cloud storage provider exclusively for its use. There is no sharing of storage resources here.
Hybrid cloud storage: This cloud storage combines and allows data sharing between both public and private cloud storage. Organizations using private and public cloud storage leverage hybrid cloud storage services to use them both with seamless interoperability.
.png)
Why use cloud storage?
Cloud storage eliminates the need for businesses to buy and manage on-premise data centers of their own. It has five significant features that differ from traditional data centers:
- Scalability and elasticity
- On-demand service
- Resource sharing
- Accessibility
- Pay-as-you-go model
Enterprises scale their cloud storage capacity as the data volumes increase or dial down capacity if volume decreases. So, rather than spending on building and maintaining a storage network, companies pay for the storage capacity they use while the provider maintains it for them.
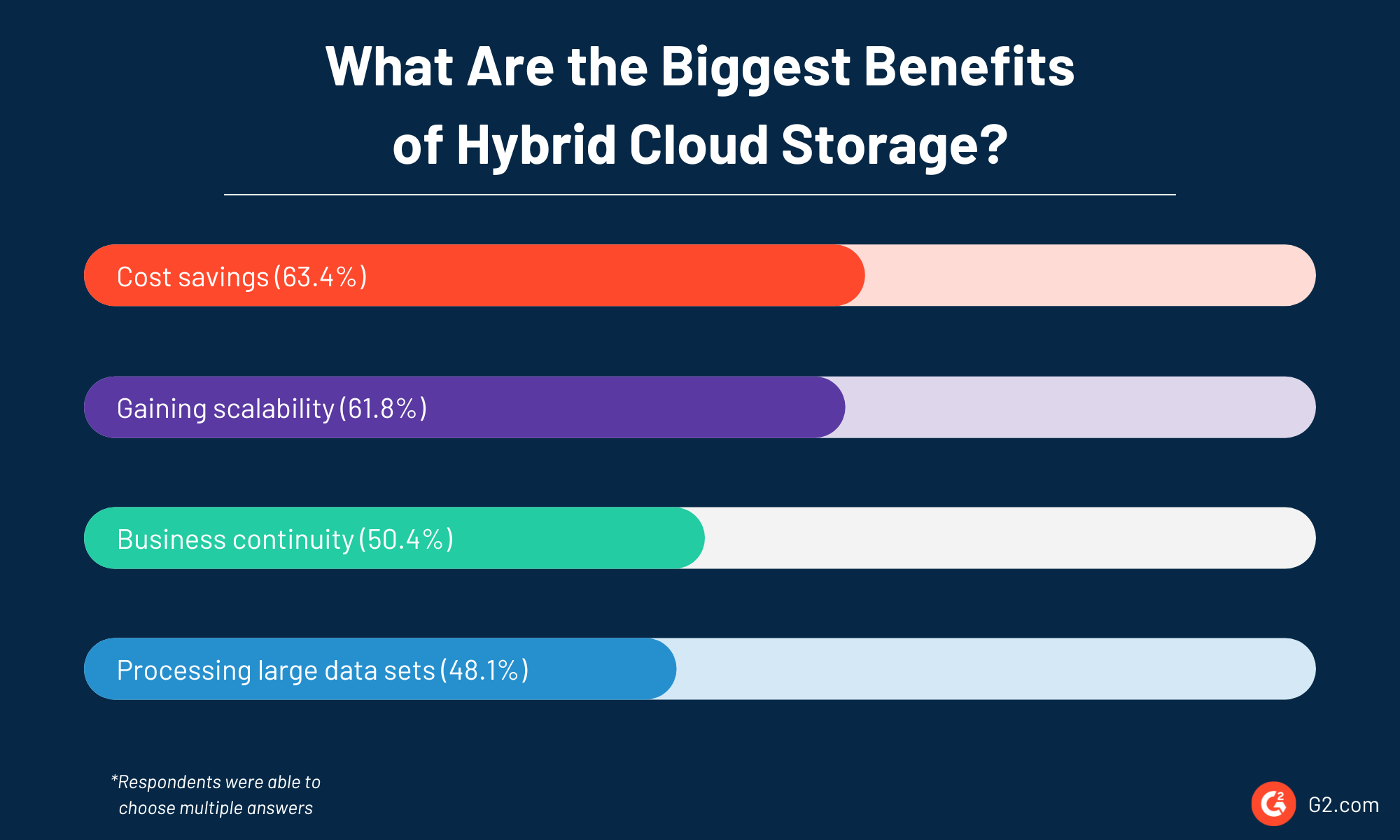
More than half of hybrid cloud storage users benefit from the cost savings (63.4%), scalability (61.8%), and business continuity (50.4%) it offers, according to a G2 survey.
Vendors also store multiple copies of the same data on different servers and if needed, in different locations. So, even in case of any disruption from short-term hardware failures, network or power outages, or a natural disaster, the cloud offers uninterrupted service and business continuity.
The ability to process massive data at scale using cloud storage makes it essential as more companies look to use big data for artificial intelligence (AI), machine learning (ML), and predictive analytics. In fact, this capability is considered one of the biggest benefits by 48% of hybrid cloud storage users.
Many cloud vendors like Google Cloud, Microsoft Azure, AWS, and IBM cloud also provide complementary services that collect, manage, secure, and analyze data at a large scale. But cloud storage has a unique problem.
Security - the special cloud problem
Cloud storage vendors host, manage and maintain the servers and associated infrastructure on behalf of their users. They also safeguard the cloud infrastructure with several security features like:
- Physical security for data centers.
- User access control management.
- Firewalls and intrusion detection systems.
- Continuous monitoring and security testing.
- Multiple data backups for disaster recovery.
But there are two lingering questions about this relationship: where does the provider’s responsibility for cloud security end? Where does the buyer’s responsibility for cloud security begin?
This is where the shared responsibility model of cloud security comes in.
What is the shared responsibility model?
In an on-premise data center, the company owns the complete tech stack; there’s no question of who is responsible for security. But when the company transfers data to the cloud, some security responsibilities shift to cloud service providers (CSPs), and some rest with the users. The shared responsibility model dictates which security tasks the cloud provider handles and which tasks the company takes care of.
The responsibilities vary depending on whether the cloud service model is software as a service (SaaS), platform as a service (PaaS), or infrastructure as a service (IaaS).
%20(600%20%C3%97%20400px)%20(1).png)
For example, cloud storage vendors, who provide IaaS, take care of the underlying cloud infrastructure, both physical and virtualized. The users take care of data security and the protection of applications, virtualized networks, operating systems, and user access.
In simple terms, the cloud storage providers are responsible for the security of the cloud, itself, and the users are responsible for the security of the content in the cloud.
In line with this, cloud storage vendors have different security measures in place to safeguard their cloud infrastructure. Their dedicated cybersecurity team provides constant security updates, auto-patch, and built-in firewalls and backups. It also continuously audits, tests, and monitors for any vulnerability or cybersecurity risks. G2 survey found security to be one of the most important features for customers using hybrid cloud storage solutions.
However, cloud users often misunderstand the shared responsibility model. They assume the CSP is responsible for the security of the cloud and the data stored there. As a result, users leave their data and assets unprotected on the cloud, making them vulnerable to attacks.
Cloud storage vulnerabilities and risks
Cloud storage has several vulnerabilities and your protective measures will only be effective when you identify these issues and frame your security strategies accordingly.
Some cloud storage vulnerabilities come from some of its great features. Here are some of the common vulnerabilities of cloud storage facilities that raise security concerns.
Lack of physical control
Users place their data in the remote servers of cloud storage providers. Since securing the physical infrastructure falls on the vendor, users lose control over this component. They have to rely on the service provider to ensure there’s no data leakage. This raises security concerns and issues related to data privacy and integrity. True, cloud storage providers offer security controls, but when you’re operating in a zero-trust environment, users need to take additional precautions.
Case in point: U.S apparel retailer Bonobos lost seventy gigabytes of customer data in 2021 due to a breach in a backup hosted by a third-party cloud service. Bonobos had to notify the service provider to secure their customer data.
Multi-tenancy
Like tenants who share apartments in a building, companies share cloud resources with other organizations. Cloud multi-tenancy provides better use of resources and saves costs for businesses. On the flip side, however, weak tenant separation or vulnerability in the shared cloud environment compromises multiple tenants. A flaw in a single shared application or a misconfiguration of a single user’s system can lead to a chain of cyber attacks on multiple cloud users.
Case in point: in January, a research by Ocra found that attackers could bypass tenant separation and access sensitive credentials and data of multiple customers in a public cloud data platform. The vulnerability allowed data access and the execution of codes on customers’ machines, compromising the entire system.
System vulnerabilities
Cloud storage also has bugs or other system vulnerabilities that get discovered now and then. Attackers may exploit them to access data, compromise data integrity, and privacy, and potentially disrupt service.
Case in point: in 2021, a cybersecurity research team from Wiz found a system vulnerability in a widely used database service of Microsoft Azure which allowed access to thousands of customer databases, including those of Fortune 500 companies. Subsequently, researchers found five other vulnerabilities that were later patched up.
Four main categories of system vulnerabilities:
- Zero-day vulnerabilities are newly discovered vulnerabilities that have no security patch.
- Missing security patches occur when new vulnerabilities are found as new patches are released, resulting in missing security patches that hackers can exploit.
- Configuration-based vulnerabilities come about when there are simple errors in the cloud's default settings, like weak encryption.
- Weak or default credentials or the absence of solid authentication can result in easy access for attackers.
Apart from vulnerabilities in cloud storage systems, there are other threats from external actors and insiders that result in breaches and security incidents. Let’s look at the top eight cloud storage risks.
Misconfigured cloud
Misconfiguration is the leading and most common cause of data breaches in cloud storage. It’s a vulnerability hiding in plain sight.
When companies don’t configure their cloud storage properly, they leave the door wide open for anyone to exploit. They either misconfigure the system when migrating to the cloud or make unapproved changes to settings post-deployment, resulting in major security incidents.
Today, cloud attackers use automation to detect misconfigurations and other vulnerabilities. Once in, they smash and grab the data they need. Some causes of misconfiguration are:
- Lack of awareness of cloud platform security policies.
- The complexity of multi-cloud deployments.
- Lack of visibility into the entire cloud environment.
- Shadow IT or unauthorized deployment on the cloud.
- Unchanged default credentials and settings.
- Lack of skills and resources in the security team.
Case in point: numerous companies have lost millions of customer data through data breaches due to their misconfigured AWS S3 bucket storage. These kinds of attacks can lead to ransom demands, non-compliance fines, revenue loss, and bad PR.
Common misconfigurations include:
- Excessive cloud access permissions.
- Leaving default credentials and configuration settings unchanged.
- Publicly accessible storage elements.
- Disabled standard security controls.
- Unencrypted cloud storage.
- Unsecured keys/password management.
- Missing security updates or patches.
Insecure APIs and interfaces
Application programming interfaces (APIs) are common these days. Cloud vendors usually expose their APIs to users so that they can interact with their cloud technologies. Cloud APIs are often the front door to cloud service, enabling applications and databases to work together seamlessly. However, when left unprotected, APIs are gateways for attacks. From misconfiguration to excessive data exposure, API loopholes create unwanted data exposure.
Case in point: in January 2021, a security researcher at Pen Test Partners found a bug in Peloton's API that allowed anyone to scrape users’ private information right off Peloton’s cloud server. Companies like John Deere, Experian, and Clubhouse have also suffered from leaky APIs.
Insecure third-party apps
Just like with APIs, companies increasingly rely on third-party apps and resources. Risks exist in each one of these products or services. Any vulnerability in such third-party apps can cause significant damage to cloud users.
Case in point: in December 2020, Microsoft ascertained that hackers compromised the Solarwind Orion platform to endanger the target customers’ cloud resources.
Poor identity and access management (IAM)
An insufficient IAM is like giving your house key to thieves. In the cloud, it leaves your servers and other tenants open to attack and account hijacks. Poor IAM can be slower in provisioning or de-provisioning privileged cloud access or undermanaged password, but these make it easier for malicious insiders and hackers to hijack your account.
Case in point: in September, an 18-year-old got into the internal systems of Uber, including its cloud systems, by stealing an employee’s password and tricking the employee into approving the push notification for multi-factor authentication (MFA).
Accidental data exposure and leaks
The cloud makes data and applications accessible from anywhere on any device. But this increases the risk of data becoming unintentionally exposed or shared.
As companies move to hybrid and multi-cloud environments, security teams struggle to keep track of different cloud resources and configure them properly. They lack visibility, making it difficult for them to identify any accidental exposures or data leaks and they end up with misconfigurations. Such databases are goldmines for hackers.
Case in point: A cybersecurity team from SafetyDetectives found an unsecured AWS cloud storage server exposing over 1 million files on the internet, including sensitive data of airport employees across Colombia and Peru.
DDoS attacks
Distributed denial of service (DDoS) attacks are one of the most significant security concerns for businesses moving to the cloud. DDoS don’t result in a data breach, but they can prevent users from accessing the cloud services, bringing operations to a halt.
The attackers use compromised devices or bots to flood target cloud servers with traffic. The cloud provider scales cloud resources to deal with incoming requests, be it memory, disc space, processing power, or network bandwidth. This exhausts the resources and slows service to legitimate users. In extreme cases, it causes cloud outages.
DDoS is more concerning today because hackers are using cloud services to launch attacks. In addition, there’s also a rise in ransom requests to companies, with hackers holding a company’s data “hostage,” until their demands are met. While cloud storage providers use advanced mitigation techniques to defend against DDoS attacks, the issue remains concerning.
Case in point: in December 2021, Flexbooker faced a widespread outage to its core application because of a DDoS attack on its AWS server. The DDoS attack also resulted in a data breach exposing nearly 3.7 million customer records.
Hackers, Organized Crime, and APTs
Hackers, organized crime groups, and advanced persistent threats (APT) pose a significant risk to the cloud. While these attackers have different motives, they all aim to get into vulnerable systems and exploit them for their own gain. And what’s more attractive to them than the cloud that’s directly accessible via the internet?
Moreover, users often leave their sensitive data on the cloud unsecured, and an attack on one user means a higher probability of attacking other users in the same cloud. From account hijacking through phishing and social engineering tactics to malware and advanced penetration, they use all techniques at their disposal.
Case in point: the Solarwind breach was done by a nation-state-backed APT group to gain access to target users’ cloud resources.
Compliance and regulatory risks
Many regions today have data protection, data sovereignty, and data localization laws, like General Data Protection Rules (GDPR). The rules stipulate where and how businesses can store, process, and use the personal data of their users. Businesses face heavy fines and penalties if they fail to comply with these rules.
Case in point: In July 2022, Russia fined Apple, Zoom, Whatsapp, Snap, and many other companies for allegedly refusing to store the personal data of its citizens within Russia. South Korea fined Microsoft for failing to protect users' personal data in 2021.
Malicious insider
We’ve focused a great deal on the external threat to cloud storage security. But sometimes, the call is coming from inside the house. The malicious actor is an insider who has access to and knows the ins and outs of a company’s IT system. The insider could be a former or current employee, contractor, or business partner who deliberately abuses their access and credentials to cause damage. Enterprises lose millions due to malicious insider attacks.
Case in point: a Pfizer employee who had a job offer from another company allegedly downloaded over 10,000 company files, including sensitive information on vaccine trials and new drugs, and uploaded them to a Google Drive account. While the company caught the employee, it's not always the case.
The need to secure your cloud storage
As enterprises move to cloud storage, the footprint of companies' sensitive data expands, and so do the organizational risks. The potential for data loss, data breaches, security incidents, and compliance failures increases.
Cloud security lapses can be fatal in an age where data privacy is of utmost importance for businesses. But not a day goes by without news of data loss, malware attacks, ransomware, and other cyberattacks. Cloud-based storage and cloud databases are one of the top targets of attack.
These incidents carry a high cost for enterprises - a reputation hit, loss of business due to system downtime, loss of sensitive data, and fines for failed audits and compliance violations. Companies need to have a security architecture that encompasses cloud and on-premise environments. Security is no longer an afterthought.
Six steps to secure a cloud storage
Reading about the risks and vulnerabilities of cloud security storage may give you jitters, but fear not. Here are six practical steps to secure your cloud, regardless of where you are in your cloud journey.
1. Understand the shared responsibility model
Begin with reading the shared responsibility model of your cloud storage provider. Ask the following questions:
- Which security controls are your responsibility?
- Which security controls are part of the cloud offering?
- Which default security controls are inherited?
To decide the security controls you need to implement, consider the following factors:
- Your regulatory obligations
- Your company's security standards and risk management plan
- The security requirements of your customers and your vendors
Create a security plan that encompasses your cloud security responsibilities. Most importantly, review service level agreements (SLA) with your cloud service provider. This is the only way to know the type of service your cloud storage provider offers and what kind of recourse exists in case of any incidents.
2. Leverage access control
In the cloud, identity is the new border. A robust IAM prevents unauthorized access to your cloud storage. Your IAM should include policies and processes for account management, identity governance, authentication, and access control. Review your current identity processes and update them appropriately for cloud usage.
Best practices to secure user access:
- Use a single identity provider.
- Enable single sign-on (SS0) and two-factor authentication (2FA).
- Plan your use of cloud service accounts.
- Provide users only the least privileged access.
- Protect your super-admin accounts.
- Regularly review and remove unused users, permissions, roles, credentials, and policies.
- Monitor user access and activities for anomalies.
- Train employees on acceptable usage and best security practices to avoid any inadvertent errors that result in lasting damage
3. Secure network and endpoints
Securing the network and endpoints from which users access the cloud is crucial as you move beyond your on-premise perimeter to the cloud.
Use virtual private networks (VPN) to connect between on-premise and cloud environments. Enable web application firewalls and monitor network traffic and firewall usage. Firewalls provide DDoS protection as well as prevent unauthorized access and man-in-the-middle attacks.
A dedicated private connection and virtual private cloud that some cloud providers offer might be of use if you have business-critical resources.
4. Enable cloud data protection
Protecting cloud data is critical and data encryption can be one of the ways. Commercial cloud storage services offer encryption. Use them or create your own encryption keys that a third-party vendor provides. Ensure your encryption is end-to-end, which means it shields your data in rest, motion, and when in use. Even if attackers get their hands on your data, it will be gibberish with end-to-end encryption. But make sure you have a proper key management plan in place. If the key is lost, your data will be gibberish to you!
Keep checking user access logs and their activities to identify unauthorized changes and inappropriate access.
You can also use software that scans for malware or viruses in your data before you upload them to cloud storage.
5. Maintain visibility
You can’t protect what you can’t see. Using different cloud services and hybrid clouds creates blindspots that escape security teams. Moreover, shadow IT is common in enterprises. A G2 survey of B2B software buyers found that 56% of employees use software that isn’t vetted by the security team.
Leverage software like cloud access security brokers (CASB) and cloud security posture management (CSPM) to maintain visibility of your cloud infrastructure and control shadow IT usage.
6. Monitor, detect, and mitigate
Centralize your monitoring. Actively hunt for security misconfigurations in networks, virtual machines, storage buckets, and applications. Be proactive when it comes to updating security patches from cloud service providers. Design a risk management plan limiting the effects on the rest of your system in case of a security compromise.
In addition, employ threat detection software to identify any high risks such as malware or DDoS. Keep reviewing your IAM and data security policies. You can’t just set it and forget it.
Most importantly, ensure your security architecture is based on the zero-trust principle and always verify the security controls they give you. Similarly, keep a check on your security architecture. Engage a third-party vendor to search for vulnerabilities if need be. Remember, every element is a threat until you verify it.
Types of cloud security solutions
Different cloud security solutions improve your cloud data protection and strengthen cloud security architecture. You can use a combination of these tools based on your needs and make your organization a secure cloud company.
Identity and access management (IAM)
Identity and access management (IAM) software only allows authorized and authenticated users based on predetermined policies. Apart from IAM, there are other solutions, like single sign-on (SSO), and multi-factor authentication (MFA), that serve the same purpose.
Cloud data security software
Cloud data security software protects information stored in the cloud and transferred through the cloud. Businesses use cloud data security software to:
- Encrypt or mask data stored in the cloud.
- Identify sensitive data.
- Control access to sensitive data.
- Monitor user behavior and access for deviations.
API security tools
API security tools protect data traveling through a company’s network via API. Businesses use API tools to
- Facilitate the documentation of connected APIs.
- Monitor APIs for security issues and abnormalities.
- Test and enforce security policies for API connection.
Data loss prevention software
The data loss prevention (DLP) tool secures control of sensitive business information and guarantees compliance. Companies use data loss prevention (DLP) software to protect sensitive data from loss, leaks, and breaches. It also:
- Understands data usage.
- Maintains customer trust.
- Meets business partner compliance.
- Complies with governmental regulations.
Cloud access security broker
Cloud access security broker software provides a secure connection between cloud users and cloud service. They offer a combination of tools to enforce security policies, including:
- Single sign-on (SSO)
- User analytics
- Cloud gap analytics
- Anomaly detection
- Cloud registry
- Mobile device management (MDM)
- Access control
- Data encryption
Cloud security posture management
Most suited for hybrid cloud environments, cloud security posture management monitors cloud services and infrastructure to detect and fix misconfigurations or incorrectly enforced policies. CSPM is used to:
- Monitor security policies and configurations across the cloud.
- Visualize cloud infrastructure in a single pane of glass view.
- Look out for other issues relating to cloud compliance and other potential security gaps.
Businesses can use a combination of these tools or leverage an all-encompassing CSPM or CASB to secure the cloud storage and the entire cloud environment.
It’s not as cloudy as it seems.
Today, it's not a question of whether the cloud is secure. Rather, it’s about whether businesses are using the cloud securely to shield themselves from cyber threats. Adopt security practices with the cloud security software solutions mentioned above. Keep your business on the cloud safe and secure. After all, the cloud is the future.
Read our latest survey and learn why companies are adopting hybrid cloud storage.

Soundarya Jayaraman
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.

.png)
