Managing user identities in an organization is a nightmare for IT teams.
Why wouldn’t it be? Each employee in an organization is likely using a dozen apps every day, deployed on cloud and on-premises infrastructure. Some work from the office, some from home, some on their laptop, and some on their phone.
Until now, a centralized identity and access management (IAM) system has been the traditional workhorse, with a single authority responsible for verifying and controlling user identity and access. System administrators and IAM teams appreciate its simplicity and centralized control.
However, there are growing concerns about potential data breaches. The lack of control over user data and privacy concerns also stand in the way of complete peace of mind.
The call for a more user-centric and privacy-preserving identity management approach has led to the rise of decentralized identity management.
What is the difference between centralized and decentralized identity management?
Centralized IAM stores user data in a single location, offering ease of use but risking breaches. Decentralized IAM lets users store data in their secure digital wallet, giving them control over their data and enhancing security but presenting challenges like interoperability.
Built on top of a blockchain, decentralized identity solutions have become a buzzword in the IAM field as they show potential to make verification easier and give users control of their data.
But what’s the better choice for your organization? Let’s find out. We’ll dive deep into each type of identity management, compare them, and come to a conclusion.
What is centralized identity management?
Centralized identity management involves collecting and storing user identity data in a central database. The users can be employees, customers, partners, or end users of applications, and the data could include identifiers like user names, email addresses, government-issued IDs, biometrics, passwords, and other values linked to the person.
Centralized identity management consolidates all user identification, authentication, and authorization processes into a single system. From a business perspective, IT teams use a single unified database to manage and control user identity and access to resources.
From the end-user perspective, using a central IAM with single sign-on (SSO) simplifies the login process. There’s no need to remember multiple user names and passwords to sign into different tools.
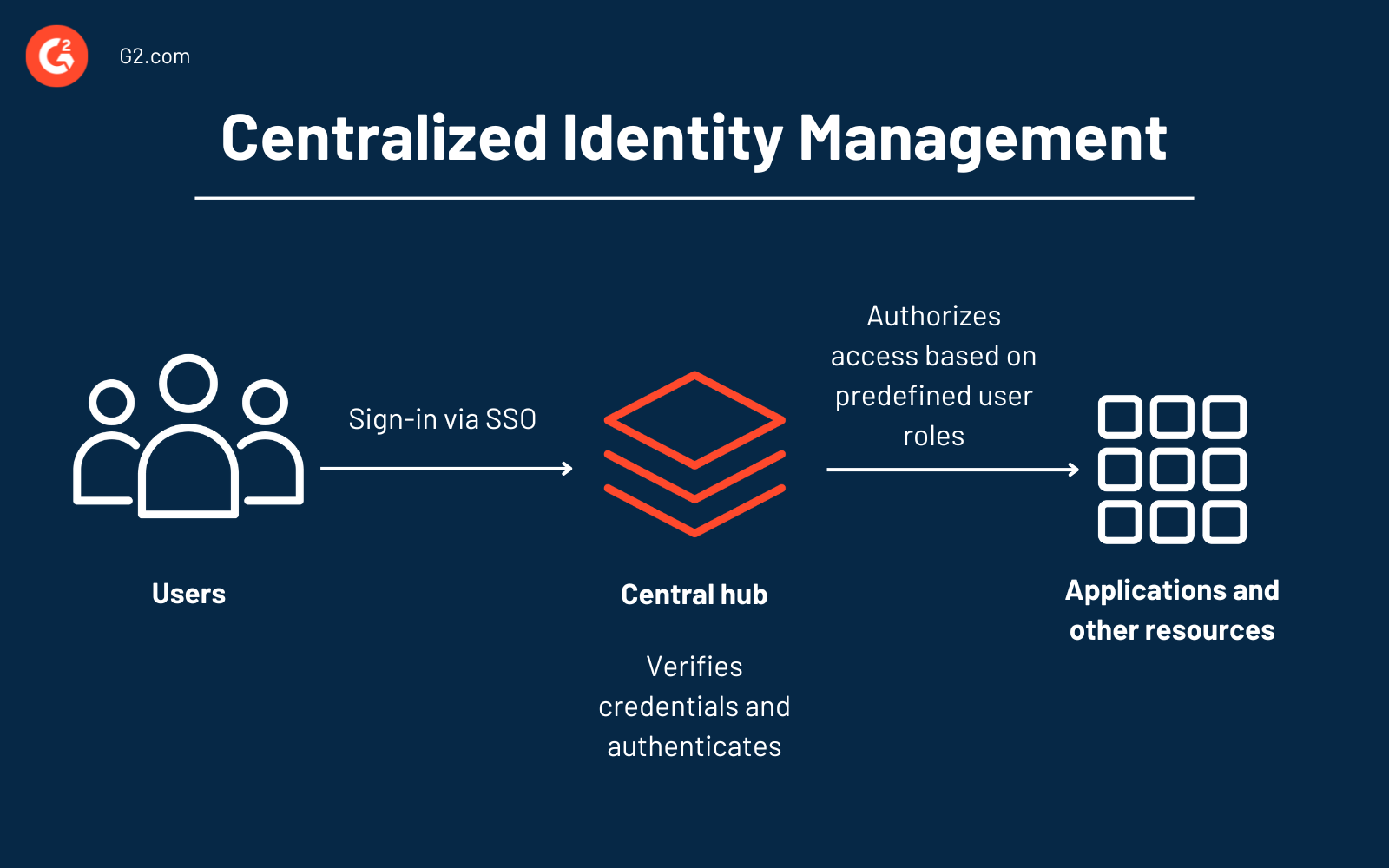
How centralized management works
Most service providers, enterprises, governments, and other organizations use centralized identity systems. Here’s how it works:
1. The core hub
The core of centralized identity management is a central hub that stores all user account details, login credentials, roles, and permissions. This hub can be a database, directory service, or an IAM platform.
IT teams coordinate IAM tasks using this database. The IAM team configures and enforces rules and organization-wide IAM policies for secure sign-ons, access controls, passwords, and user management.
They set up user profiles and groups, create access control lists that define what resources individual and group users can access, integrate internal and third-party applications to SSO, manage the central directory, and audit user access.
2. Authentication
When a user logs in, the central repository verifies the user credentials against its records and grants access if they are valid. Authentication in modern IAM systems typically includes multi-factor authentication (MFA), two-factor authentication (2FA), or even passwordless authentication.
3. Access control
The system determines the user's level of access to different applications based on their role and grants access accordingly.
4. SSO
SSO eliminates the need for repetitive logins to access different software. It uses the pre-built trust between the central IAM system and the applications through common security standards like OAuth 2.0, OpenID Connect, and security assertion markup language (SAML).
Different categories of centralized IAM tools
Based on their deployment models, functionalities, and the specific needs they address, here are the different categories of centralized IAM tools:
- Directory services
- Cloud directory services
- Single sign-on (SSO) solutions
- Cloud-based identity management tools
- Privileged access management (PAM) software
- User provisioning and governance tools
- Biometric authentication systems
Benefits of centralized identity management
Features you see in the best IAM tools, like centralized password management, auditing, workflow automation, and security policy enforcement, provide significant financial and security benefits.
Cost benefits of centralized IAM
- Automates onboarding and offboarding user accounts, saving time and minimizing human error.
- Consolidates and tracks access to and usage of various applications, potentially reducing the need for multiple licenses per user.
- Simplifies compliance management with automated reporting.
- Reduces time spent on administrative tasks related to IAM, freeing the IT team to focus on core functionalities.
Security benefits of centralized IAM
- Strengthens authentication with features like MFA, 2FA, and biometric authentication.
- Enables granular access control where users only access what they need.
- Improves visibility and audit trails of software usage for faster incident detection.
- Reduces risk of privileged account misuse, insider threats, and employee identity theft.
- Enables enterprise-wide security policy enforcement, reducing the risk of vulnerabilities due to inconsistent access control practices.
- Centralizes password management with a strong password policy that applies to the entire organization.
Limitations of centralized identity management
A centralized identity system provides a convenient and controlled approach, but it's not without flaws.
Single point of failure
Critics of centralized IAM often point out that central storage is a prime target for cyber attacks. If compromised, attackers could gain access to a vast amount of user credentials. The data can be stolen, duplicated, or tampered with, leading to widespread access issues and data breaches.
Imagine your email ID and password getting compromised in a breach. Your other applications that depend on the same email ID also get compromised.
For example, a data breach at Ticketmaster in May 2024 exposed the personal data of its 560 million customers in North America, potentially even payment details.
A breach in an IAM platform is even worse and can lead to supply chain attacks.
In 2023, Okta, a leading provider of IAM solutions, experienced a data breach due to stolen employee credentials. This compromised 134 customer accounts, including Cloudflare, BeyondTrust, and 1Password, and hackers even managed to steal data about all of its customers. Fast-forward to February 2024, and Cloudflare, one of the affected companies, reported a cyber attack stemming from the Okta breach.
This showcases how a vulnerability in a single, centralized IAM system can create a domino effect, impacting numerous downstream organizations.
Lack of user control over data
The second major critique of centralized IAM also stems from its centralized architecture. Users have no control over how their data is stored or used within the central repository. This lack of transparency can be unsettling, especially when considering that data might be used for purposes beyond initial consent.
Facebook owner Meta, for instance, was fined over $1 billion by the European Union in 2023 for violating EU data privacy rules by transferring and storing user data from Europe to the United States, where privacy protections are considered weaker.
These limitations highlight the need for user-centric decentralized identity management systems.
Want to learn more about Decentralized Identity Solutions? Explore Decentralized Identity products.
What is decentralized identity management?
Decentralized identity management is an innovative new approach. Users collect identity data and credentials from trusted entities like the government and store them in their digital wallet or local device.
When a service provider requests ID, the user shares it from the wallet without relying on a single central authority.
This way, the user reveals only the information absolutely necessary for the transaction, keeping the rest of their data private. The enterprise doesn’t get to store the data after verification.
How does decentralized identity management work?
Decentralized identity works with the following components:
- A digital wallet that is secured with public key encryption so the user has a public key to share with a service provider and a private key that only they can access. Much like a crypto wallet, except this is used to store user identity data.
- Verifiable credentials (VC), such as an education certificate, birth certificate, driving license, social security ID, or employment experience, from certified issuers like the government, universities, and employers, with their digital signatures, are stored in a digital wallet.
- A decentralized identifier (DID) that points to the digital wallet with credentials and informs service providers how to access the credentials they need.
- Distributed ledger technology (DLT), like blockchain, as the ledger to record the DID.
When interacting with a service (say, renting a car), the user shares the DID that points to their data instead of all personal details. The service looks at the DID on a blockchain. This tells them where to find the user’s VCs and how to verify them.
The service retrieves the specific VC needed (driver's license) and verifies its authenticity using digital signatures from the issuer. Based on successful VC verification, the service grants the user access (rents the car) or denies it if the VC doesn't meet their requirements.
Instead of an organization enrolling a user and verifying and storing the user data, individuals hold it and share it when needed. Trust is shared based on the verified credentials in an immutable ledger to identify, authenticate, and authorize users.
Thus, decentralized identity management flips the script of traditional identity systems.
Benefits of decentralized identity management
Decentralized identity management provides features like distributed identity data, strong cryptography, user-centric design, and tamper-proof credentials. Its potential benefits include:
- Less reliance on managing and securing centralized identity infrastructure.
- Easier verification processes through reusable credentials.
- No central point of failure for attackers to exploit.
- Users share minimal data with each service, limiting potential damage.
- Improved data protection with cryptography reduces the potential for privacy violations.
- Decentralized storage makes it harder to steal complete identities.
Top 5 decentralized identity solutions
*Above are the top 5 decentralized identity solutions based on the G2 Summer 2024 Grid® Report for the software.
Limitations of decentralized identity management
On paper, decentralized management sounds like a game-changer. Users get to call the shots on their digital identity. Breaches become less catastrophic when there's no central vault of user data to crack.
For IT professionals, decentralized identity offers a potentially simpler architecture without hundreds of accounts to manage centrally. But, there are challenges — both technical and non-technical. Let's take a look.
Blockchain limitations
Blockchain technology provides a tamper-proof ledger for DID storage but has scalability issues. Whenever a DID needs to be added to a blockchain, it must be validated, which takes time. Public blockchains, like the ones used for Bitcoin, for example, struggle to process a high volume of transactions, leading to slow transaction times. This can be a significant roadblock for DID adoption, as a large user base would overwhelm the network.
Key storage
Securely storing private keys and verifiable credentials associated with DIDs remains a challenge. Today, most decentralized solutions store such private data in users' devices, such as smartphones, personal computers, or even hardware devices. What will happen if the storage device is lost is still unaddressed.
Interoperability
The biggest question around decentralized identity is the common standard for interoperability. While organizations like the World Wide Web Consortium (W3C) are working on standardizing, it's still a work in progress. Given the scale required, it will certainly take some time and coordination among all stakeholders, such as governments, technology providers, and other organizations.
User adoption
Encouraging users to switch from familiar centralized systems to a new system is often difficult. It depends on many factors, such as knowledge about the new technology, ease of use, cost, and willingness to adopt it. Decentralized identity requires some level of technical expertise that many users lack.
Moving from a legacy system to decentralized management will be difficult for organizations, as much of their functioning depends on a central authority controlling IAM.
Centralized vs. decentralized identity management
The major difference between centralized and decentralized systems stems from the trust relationship that exists between involved parties.
Identity management standards like SAML and OAuth used in centralized IAM rely on bidirectional trust. Here, the parties know and trust each other to share securely and authenticate the user identity.
For example, you log into work-related software using your SSO. Your SSO provider and the application provider already have an agreement that defines how they will communicate and exchange information about you. They trust each other to handle your information securely. This relationship identifies, authenticates, and authorizes you to access resources.
A decentralized system, in contrast, uses a unidirectional model of trust. Here, the verifier of the user identity trusts the issuer of the credentials, but the issuer doesn’t know the verifier and has no relationship with them.
Now, this unidirectional model can be achieved using existing centralized systems, too. But what differentiates decentralized identity management further is the technologies it employs, namely the digital wallet, and advanced cryptographic techniques. These ensure user control over identity data.
The user has an independent relationship with both the issuer and verifier, with the digital wallet acting as a middle ground. Blockchain's tamper-proof nature establishes trust in the identity data. Additionally, advanced encryption sets trust boundaries more securely and offers greater user privacy.
This fundamental distinction in trust relationships shapes the various aspects of centralized and decentralized systems.
|
Aspect |
Centralized identity |
Decentralized identity |
|
Control |
Controlled by central authorities (governments, companies). |
Controlled by individuals. |
|
Data storage |
Centralized databases or servers. |
Distributed across a decentralized network. |
|
Privacy |
Limited control, vulnerable to breaches. |
With enhanced control, users decide on sharing. |
|
Security |
Central points of failure, susceptible to cyberattacks. |
Distributed architecture is resistant to single points of failure, but new security threats might emerge. |
|
Interoperability |
Existing identity management solutions have limited interoperability. |
Interoperability is still in the works as the common standards on decentralized identity are still evolving. |
|
Trust |
Reliance on centralized authorities and intermediaries. |
Built-in trust mechanisms with cryptography. |
|
Regulatory compliance |
Requires compliance efforts for privacy/data protection laws. |
Built-in privacy controls and consent mechanisms can aid compliance. |
|
User experience |
Varied. Simplified with SSO but often involves redundant accounts/passwords. |
Potential for more seamless access with digital wallet. |
Centralized or decentralized: Choosing the right approach
There's no single right answer when it comes to selecting between centralized and decentralized approaches. Both approaches have their strengths and weaknesses, and the ideal choice depends on your specific needs and priorities.
If your organization requires strict oversight and uniform policies, a centralized IAM solution may be better.
74%
of IAM software users come from mid-market and enterprise businesses, according to G2 review data.
Source: G2
However, if you prioritize user privacy and data control and are willing to invest in emerging technology, consider a decentralized IAM approach.
However, remember that implementing and managing decentralized identity solutions can be significantly more complex than implementing established centralized systems. Expertise or additional resources might be necessary, and compatibility with existing partners could become a roadblock.
If you are comfortable with your current IAM, it’s advisable to wait and watch before adopting decentralized identity systems. Monitor the development of standards and user experience.
The most pragmatic approach would be a hybrid model where you integrate elements of decentralized identity with your existing centralized IAM system and test it. Consider pilot programs to test the technology and assess its fit.
Ultimately, the best approach depends on your unique circumstances.
IAM-prove your security
IAM plays a critical role in ensuring that the right individuals have access to the right resources at the right time for the right reasons. Carefully consider your IAM priorities, explore the options available, and select your model to create a secure and empowered digital identity environment for your organization.
Ready for the next step? Explore this free G2 guide on identity governance, which can help you define, manage, and review your IAM policies.

Soundarya Jayaraman
Soundarya Jayaraman is a Content Marketing Specialist at G2, focusing on cybersecurity. Formerly a reporter, Soundarya now covers the evolving cybersecurity landscape, how it affects businesses and individuals, and how technology can help. You can find her extensive writings on cloud security and zero-day attacks. When not writing, you can find her painting or reading.

