Modern applications send and receive an unfathomable amount of data at any given time. This flow of data is powered through application programming interfaces (APIs).
From a hacker’s perspective, APIs are an attack surface often overlooked by security teams.
APIs often play a crucial role in an application’s functionality. Moreover, APIs are not inherently vulnerable if properly configured, and the threat of an attack does not outweigh their value.
As of July 2019, more than 22,000 APIs have been published. Because so many applications rely on APIs, securing online connections can be a crucial component of cloud security operations, especially when working with sensitive data.
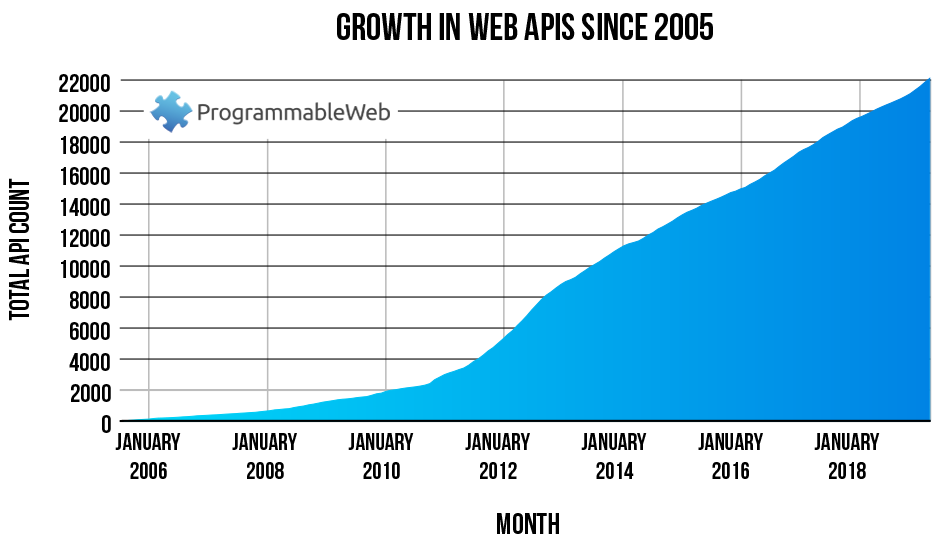 Source: ProgrammableWeb
Source: ProgrammableWeb
What is API security?
First, let’s review what APIs are. APIs control incoming and outgoing server requests while connecting data and other cloud services to applications.
APIs are used to power applications that include anything from finance and pricing data to machine learning libraries and vulnerability scanning services. There’s no argument against their convenience and usability, but there are major concerns regarding their security.
Companies running applications in the cloud and connecting them to additional data sources or cloud services have a number of security challenges in front of them. We’ll dig into them more, but the main issues revolve around network access control (NAC), authentication, standardization, and exposure.
Why is API security important?
As new connections continue to bring more data across global applications, API security becomes more important. Every connection and every application has unique requirements that must be continuously tested to ensure protection.
Unprotected or unknown APIs pose many threats to businesses including breaches, fines, and attacks.
Breaches make headlines. Companies are demonized and scapegoats are cast out for the sake of the business. If poorly secured, APIs can be especially vulnerable to attack.
| RELATED: Learn 8 best practices to boost data security and avoid data breaches, here → |
Companies and their respective security teams must put themselves in the shoes of an attacker to best protect their data. By examining API surfaces from the outside, it’s significantly easier to discover and remediate existing vulnerabilities.
Fines come as a result from breaches. When a company experiences a breach, regulatory bodies and localized ordinances enforce privacy protection and fines depending on the size and scope of a breach, as well as the nature of the exposed data.
Bad press will be the least of a company's worries if a vulnerable API is discovered. Vulnerable APIs are fines waiting to happen, especially if an application or connection exposes sensitive information to the public.
In 2019, Facebook received negative public attention due to the Cambridge Analytica scandal. Facebook allowed access to sensitive data with the third-party application’s use of an API. As a result of this scandal, the Federal Trade Commission fined Facebook $5 billion.
Attacks can be costly in a number of ways. While fines can quickly add up, attacks can be just as expensive. Attacks may prevent an application from functioning or cause a network to crash, but they can also come in the form of literal theft.
| RELATED: Learn how to protect yourself from a cybersecurity attack, here → |
Earlier this year, stolen API keys, along with malware and social engineering attacks, were used to steal millions from Binance, a popular cryptocurrency exchange. Using stolen credentials and vulnerable APIs, the hackers illegally obtained 7,000 Bitcoin worth over $40 million.
API security challenges
APIs are complex and come in many forms. This makes them difficult to protect, but addressing these common security concerns is a good place to start.
Access control and visibility are the two biggest needs when it comes to protecting APIs and applications. Without proper access and authentication measures, any nefarious actor on the web could easily discover an unprotected API and steal data or break into an application.
Organizations must require multi-factor authentication to access APIs and continuously monitor systems for privilege abuse and unauthorized API access. Companies should limit the number of employees that have API access and be sure to revoke credentials when employees leave the company, via their own volition or termination.
Exposing sensitive data is another common issue with API security. Often, companies use APIs to securely transfer sensitive data. Most health care or financial APIs contain some kind of sensitive information.
Access control is key to protecting this data, but must also be encrypted while in transit. End-to-end transport layer encryption (TLS) should always be used, but additional authentication with OAuth or OpenID can improve protection as well.
| RELATED: Read an overview of modern encryption technology, here → |
Shadow API is a term used to describe legacy APIs or other APIs no longer in use. These old or unknown APIs may have outdated security mechanisms or expose data to anyone interacting with it.
They may also be connected to systems without a business knowing. This is why it’s incredibly important to continuously discover API connections and monitor their use.
API security best practices
Keep in mind these security components when designing an API ecosystem to maximize protection.
-
-
Use advanced authentication protocols such as OAuth or OpenID
Advanced authentication protocols provide an additional level of security and user governance. This can make it more difficult for threat actors to misuse credentials and escalate their privileges. These can be implemented leveraging multi-factor authentication or privileged access management solutions. -
Monitor API ecosystems for abnormal behavior and shadow APIs
Abnormal behavior can be detected using a number of solutions, but user and entity behavior analytics (UEBA) seems to be the most promising solution for the future. UEBA products continuously evaluate risk based on user behavior, privileges, location, and a number of additional factors to alert administrators when high-risk users pose a threat. -
Use an API gateway to limit entry points and simplify management
Many integration platforms as a service (iPaaS) are capable of serving as an API gateway. These can funnel integration requests to a single access point, making it more difficult for shadow APIs to connect or for hackers to remain unnoticed. -
Test and scan APIs, applications, and configurations for vulnerabilities
Many vulnerability scanners are capable of examining APIs for threats in source code and discovering misconfigurations. Penetration testing tools are also useful in simulating real-world threats and providing situational context to security tests.
-
Use advanced authentication protocols such as OAuth or OpenID
The evolving API security market
API security solutions are on the rise and it wouldn’t be surprising if a number of new API security startups are purchased by major players in the integration platform (iPaaS) space. These technologies would be a logical addition for any platform focused on managing APIs.
Keep an eye out for newer startups like Appknox, CloudVector, Data Theorem, and Wallarm—more will emerge as demand for solutions grows. It will be interesting to see how the relationship between these companies and the major integration solution providers evolves as API security becomes a mainstream goal for the enterprise.
Want to learn more about Encryption Software? Explore Encryption products.

Aaron Walker
Aaron has been researching security, cloud, and emerging technologies with G2 for more than half a decade. Over that time he's outlined, defined, and maintained a large portion of G2's taxonomy related to cybersecurity, infrastructure, development, and IT management markets. Aaron utilizes his relationships with vendors, subject-matter expertise, and familiarity with G2 data to help buyers and businesses better understand emerging challenges, solutions, and technologies. In his free time, Aaron enjoys photography, design, Chicago sports and lizards.
